Kubernetes


Advanced Usage
Network Policy

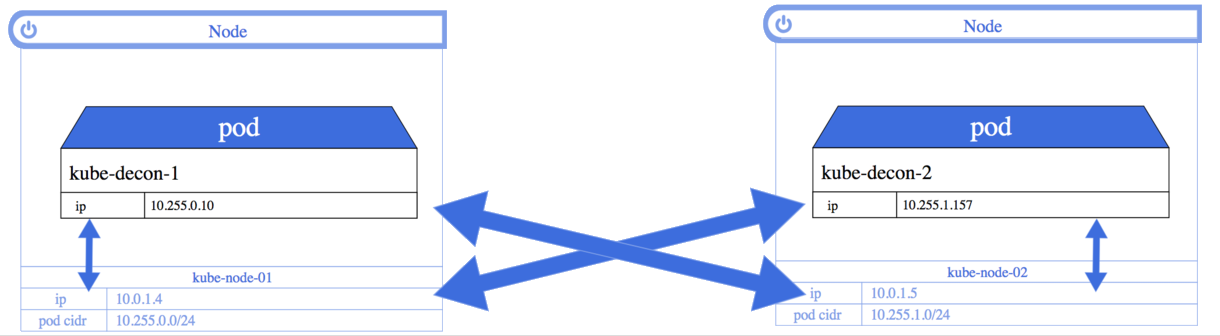
Network Policy


Network Policy

Similar to Firewalls
Deny Ingress / Egress traffic
Use Label Selectors & IP blocks

Init Containers

Advanced Usage
Init Containers

Advanced Usage
apiVersion: v1
kind: Pod
spec:
initContainers:
- name: init-db
image: busybox
command: ['sh', '-c', 'until nslookup db; do sleep 2; done;']
containers:
- name: myapp-container
image: busybox
command: ['sh', '-c', 'echo The app is running! && sleep 3600']
Init Containers

Advanced Usage
POD
Init Containers

Advanced Usage
POD

init-db
Init Containers

Advanced Usage
POD

init-db

Init Containers

Advanced Usage
POD

init-db

Init Containers

Advanced Usage
POD


init-db
Init Containers

Advanced Usage
POD


my-app
Init Containers

Ensure Services are available
Ensure Volumes are populated

Node Affinity
kubectl label nodes \
<node-name> \
<label-key>=<label-value>

Node Affinity
kubectl label nodes \
my-node-1 \
gpu=nvidia-tesla-p100

Node Affinity
requiredDuringSchedulingIgnoredDuringExecution
preferredDuringSchedulingIgnoredDuringExecution
In Pod's spec.affinity.nodeAffinity:

Node Affinity
requiredDuringSchedulingIgnoredDuringExecution
preferredDuringSchedulingIgnoredDuringExecution
HARD RULES
SOFT RULES
In Pod's spec.affinity.nodeAffinity:

Node Selection
kubectl label nodes <node-name> <label-key>=<label-value>
apiVersion: v1
kind: Pod
metadata:
name: nginx
spec:
containers:
- name: nginx
image: nginx
nodeSelector:
disktype: ssd
Recap: Services
Service Type: ClusterIP
10.47.240.1:80
my-app-1h4md
label selection
my-app.my-ns.svc.cluster.local
10.47.242.240:8080
10.47.242.241:8080
10.47.242.242:8080
my-app-j2vek
my-app-xt8lx

Recap: Services
my-app-1h4md.my-app.my-ns.svc.cluster.local
my-app-xt81x.my-app.my-ns.svc.cluster.local
10.47.242.240:8080
10.47.242.241:8080
10.47.242.242:8080
Headless Service
(clusterIP: None)
my-app-1h4md
my-app-j2vek
my-app-xt8lx
my-app-j2vek.my-app.my-ns.svc.cluster.local

Recap: Services
my-app-1h4md.my-app.my-ns.svc.cluster.local
my-app-xt81x.my-app.my-ns.svc.cluster.local
10.47.242.240:8080
10.47.242.241:8080
10.47.242.242:8080
Headless Service
(clusterIP: None)
my-app-1h4md
my-app-j2vek
my-app-xt8lx
my-app-j2vek.my-app.my-ns.svc.cluster.local

StatefulSets
A deployment with extra guarantees:

StatefulSets
A deployment with extra guarantees:
my-app-1h4md
my-app-j2vek
my-app-xt8lx
my-app-2
my-app-1
my-app-0
DEPLOYMENT
STATEFULSET

StatefulSets
A deployment with extra guarantees:
-
Stable, unique network identifiers.

StatefulSets
A deployment with extra guarantees:
-
Stable, unique network identifiers.
my-app-2
my-app-1
STATEFULSET
my-app-0.my-app.my-ns.svc.cluster.local
my-app-2.my-app.my-ns.svc.cluster.local
Headless Service
my-app-1.my-app.my-ns.svc.cluster.local
my-app-0

StatefulSets
A deployment with extra guarantees:
-
Stable, unique network identifiers.
-
Stable, persistent storage.

StatefulSets
A deployment with extra guarantees:
-
Stable, unique network identifiers.
-
Stable, persistent storage.
-
Ordered, graceful deployment and scaling.
-
Ordered, graceful deletion and termination.
-
Ordered, automated rolling updates.

StatefulSets
A deployment with extra guarantees:
-
Stable, unique network identifiers.
-
Stable, persistent storage.
-
Ordered, graceful deployment and scaling.
-
Ordered, graceful deletion and termination.
-
Ordered, automated rolling updates.
my-app-0
my-app-1
my-app-2
Created
Created
Created

Apache Zookeeper
Distributed State Management

Apache Zookeeper
Distributed State Management
/
/Znode1
Value: "foo"
/Znode2
Value: "bar"
/Znode1/subnode
Value: "foo"
/Znode2/hello
Value: "world"
/Znode2/mutex
Value: "locked"

Apache Zookeeper
Distributed State Management
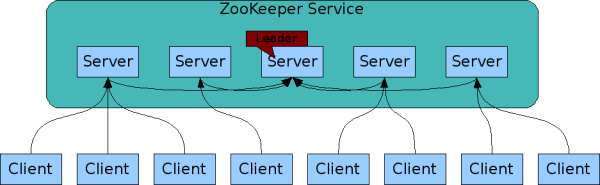

DEMO

POD DISRUPTION BUDGET

POD DISRUPTION BUDGET
my-app-2
my-app-0
my-app-0
apiVersion: policy/v1beta1
kind: PodDisruptionBudget
metadata:
name: zk-pdb
spec:
selector:
matchLabels:
app: zk
maxUnavailable: 2

POD DISRUPTION BUDGET
my-app-2
my-app-0
my-app-0
apiVersion: policy/v1beta1
kind: PodDisruptionBudget
metadata:
name: zk-pdb
spec:
selector:
matchLabels:
app: zk
maxUnavailable: 2

Taints & Tolerations

Taints & Tolerations
Opposite of NodeAffinity

Taints & Tolerations
# To add the NoSchedule taint kubectl taint nodes worker-1 key=value:NoSchedule
# To remove the taint
kubectl taint nodes worker-1 key:NoSchedule-

Taints & Tolerations
# In a PodSpec tolerations: - key: "key" operator: "Equal" value: "value" effect: "NoSchedule"

Taints & Tolerations
# In a PodSpec tolerations: - key: "key" operator: "Equal" value: "value" effect: "NoSchedule"
Effects:
- NoSchedule
- PreferNoSchedule
- NoExecute

Taints & Tolerations
https://kubernetes.io/docs/concepts/configuration/taint-and-toleration/#taint-based-evictions
Builtins
These get applied automatically by NodeController

Taints & Tolerations
https://kubernetes.io/docs/concepts/configuration/taint-and-toleration/#taint-based-evictions
Builtins
These get applied automatically by NodeController

RBAC

RBAC
Role: Single Namespace
ClusterRole: All Namespaces

RBAC
Role: Single Namespace
ClusterRole: All Namespaces
ONLY additive

RBAC
When a resource needs access to other resources
E.G. Operators

RBAC
# Allows User to get all pods
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"]
RoleBinding / ClusterRoleBinding

RoleBinding / ClusterRoleBinding
users:
- name: corey
user:
client-certificate: <xxx>
client-key: <xxx>
Role

RoleBinding / ClusterRoleBinding
users:
- name: corey
user:
client-certificate: <xxx>
client-key: <xxx>
Role
https://github.com/coreos/dex/blob/master/Documentation/kubernetes.md

RoleBinding / ClusterRoleBinding
# This role binding allows "jane" to read pods in the "default" namespace.
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: User
name: jane
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-reader # this must match the name of the Role
apiGroup: rbac.authorization.k8s.io
RoleBinding / ClusterRoleBinding
# This cluster role binding allows anyone in the "manager" group
# to read secrets in any namespace.
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-secrets-global
subjects:
- kind: Group
name: manager
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: secret-reader
apiGroup: rbac.authorization.k8s.io
RoleBinding / ClusterRoleBinding
# This cluster role binding allows anyone in the "manager" group
# to read secrets in any namespace.
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-secrets-global
subjects:
- kind: Group
name: manager
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: secret-reader
apiGroup: rbac.authorization.k8s.io
FIN
K8s Advanced Usage
By Corey Brooks
K8s Advanced Usage
- 665



