Building a secure application
Agenda
- Why ?
- Input validation
- Handle sensitive data
- Sessions and permission
- Store data
- CAPTCHA
- Mobile or legacy
- Improvements/Solutions
Why ?
"The reason why security is actually popular in the web area is because it is the last worry of the developers."

Why ?
"Security is an endless cycle that requires permanent awareness and caution on every single aspect of the target's ecosystem."
From the experience that i've ...
Security Issues are more common on new features.
User Input
What is user input ?

GET and POST
What to look for ?
XSS - HTML and Javascript code

What to look for ?
SQL Injection - Code executed in database
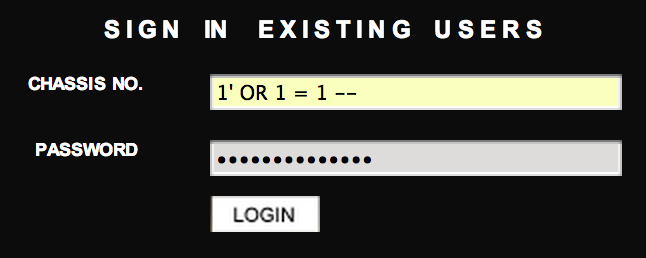
What to look for ?
XXE - External Xml Entity

HTTPS
What to look when use HTTPS ?
-
Valid certificate
- Apply to all pages (force it!)
- Strong protocols and chipher.
- HSTS (HTTP Header)
-
Keep an eye on the technology/software used
(a.k.a. prevent OpenSSL to strike back!)

HTTPS
https://www.ssllabs.com/ssltest/
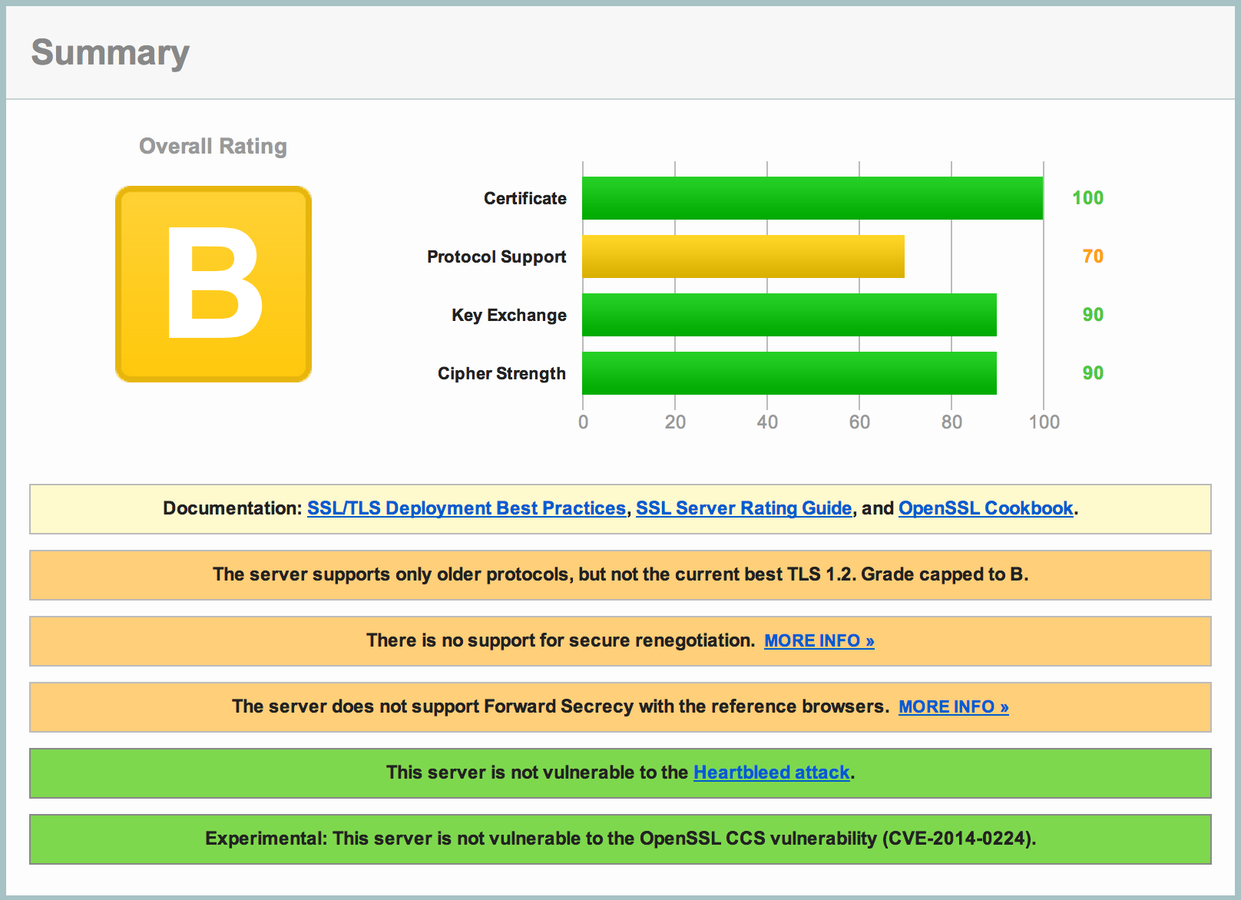
Trust
Don't trust external data.
Always limit the scope of the input:
Number -> [0-9+-,.]
String -> [a-zA-Z0-9]
Test it!
Layers
Create an abstract layer that do the protection for you.
Layers of trust!
Example:
Each object that is passed to the render layer,
will have all values sanitised.
HTTP Request
Example
GET /?gfe_rd=cr&ei=XTPDU_euKsHe7ge1hZGZBg&gws_rd=szl HTTP/1.1
Host: www.google.pt
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:30.0) Gecko/20100101 Firefox/30.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://www.google.pt/xpto
Cookie: PREF=ID=43984f61769e0702:U=a9a6b3d9d72f081c:FF=0:TM=1388671305:LM=1404746416:S=bPDotTFh9f-uCR_7; NID=67=N4EN6p1vKmr2d4q-geUgyKu5Zn6DYmqyd0JPCS5jx02JkswPfnbIVg0AdtW44nX_FCOsTnCbYN--Tu9407zrc1fQHspFGlWnIARYddqYU4v_t8OKFk1KVqFhzr9OZQiv; OGPC=5-7:
Connection: keep-alive
All of this can be forged!
https://en.wikipedia.org/wiki/HTTP_headers
Image

Image
What can go wrong ?
Filename
EXIF
We should think in the small case first,
then expand with a broader range if need.
Imagine
Your App ..
Your input ..
Can you think outside the box ?
Protection
HTTP Headers
-
Strict-Transport-Security
-
X-Frame-Options
- X-Content-Type-Options
- Content-Security-Policy (CSP)
- X-XSS-Protection
Input Validation
"Never trust any input data from the user and clean it before processing it"
Handle Sensitive Data
Each person data is sensitive.
Enumeration
Handle Sensitive Data
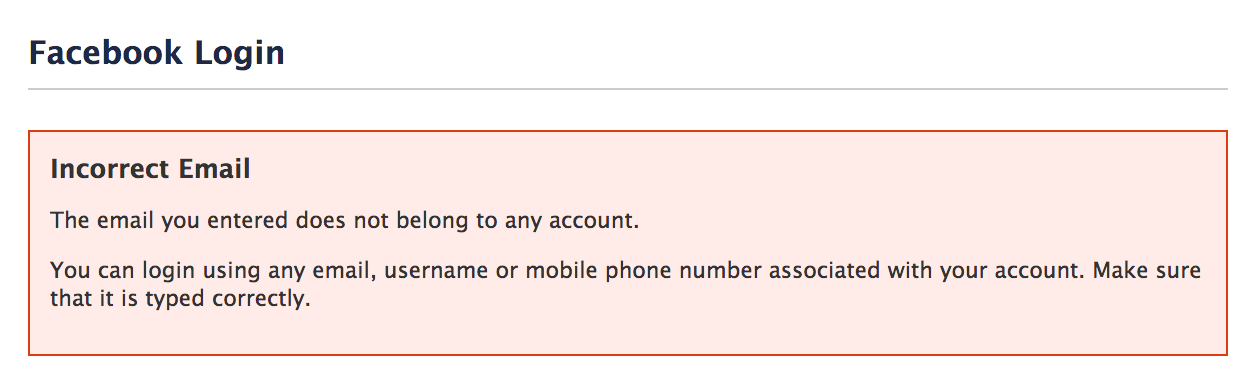
Protect
Count interactions with forms.
Give ambiguous answers.
Log information.
Encrypt password
Rainbow Tables
Security Level
-
Hash
-
Salt + Hash MD5
-
Salt + Slow Hash Algorithm
- Everything up, + new hash on login
Password
Force the use of stronger passwords.
-
Limit the number of failed login attempts.
-
Require strong passwords.
-
Do not limit passwords to a certain length.
-
Allow special characters in passwords.
Two Factor Authentication
6 digits token
Google, Facebook, Dropbox, Betfair, PayPal, ...

... or even multi factor authentication (SMS).
Forgot your password ?
Be careful on the logic for recover passwords.
-
Ask for more information:
- Mobile Number
- Secret question
- ...
- Send token by SMS
- Send recover link by email
Are this enough ?
Session and Permission
A2 - Broken Authentication and Session Management
Implement LOG OUT feature ...
and implement it WELL!
Use a good permission manager ...
to hide ADMIN pages!
SESSION ID on URL ?
Did you allow to introduce the same email ?
Show the same message
For 404, 403 and 500 ...

Store Data
Cookies, Local Storage, ...

Totally UNSAFE!
CSRF
Cross Site Request Forgery

CSRF - Solution
On write actions, only accept POST.
Security Level
-
Token in URL
-
Token per Session
-
Token per Request
Bad Implementation
Change
Be special careful critical parts of the website:
On user edit page

CAPTCHA
Don't even try to create your own CAPTCHA.
Main reasons that CAPTCHA fails:
- Bad implementation
- Simple graphics
http://www.securitytube.net/video/9479
Just use the best ... reCAPTCHA!

Mobile or Legacy
What Mobile and Legacy have in common ?
Hacking Facebook Legacy API
http://stephensclafani.com/2014/07/08/hacking-facebooks-legacy-api-part-1-making-calls-on-behalf-of-any-user/

Reverse
If you learn a lot about protecting your website,
you learn also about how attack others :)
you learn also about how attack others :)
SDLC
"I had no idea we were doing that"
Solutions
Security in SDLC.

Expectations
Always expect the worse and be prepare for that.
Questions ?
References
https://www.linkedin.com/today/post/article/20140429201001-92602781-thinking-security-in-your-app-design-let-s-build-a-recommendation-list
http://alias.io/2010/01/store-passwords-safely-with-php-and-mysql/
https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet
https://www.eff.org/https-everywhere/deploying-https
http://www.itproportal.com/2013/08/06/7-steps-for-building-a-secure-web-application/
Building a secure application
By David Magalhães
Building a secure application
- 526


