Aws Service Catalog
Hands-On
Demo

In this demo, we will:
- Create IAM roles for Service Catalog
- Create a Service Catalog portfolio
- Create a product using a CloudFormation template
- Add the product to the portfolio
- Grant access to end users
- Test provisioning as an end user
- Review provisioned products and governance
- Clean up resources
Agenda
Step 1: Create IAM Roles for Service Catalog
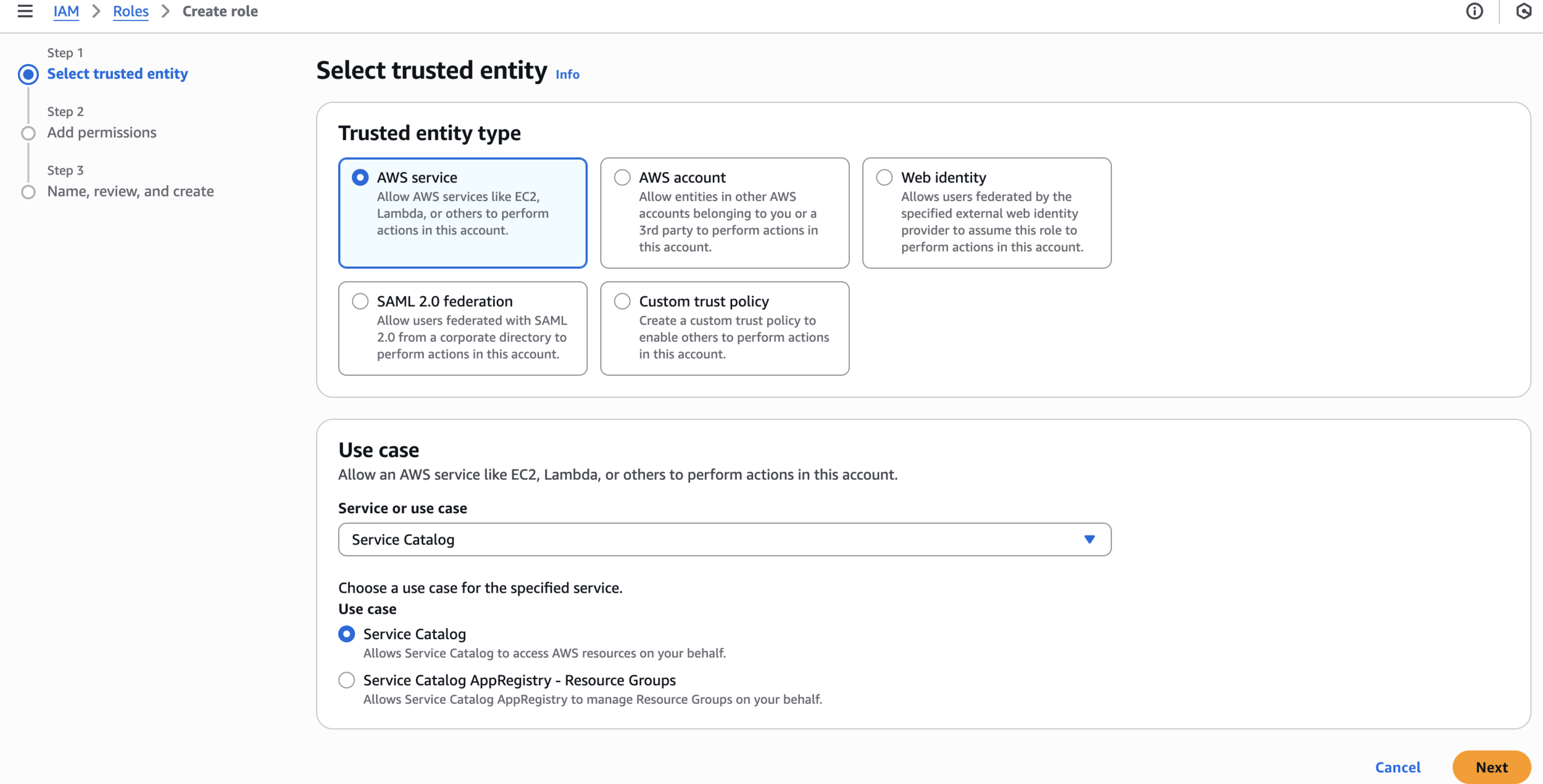
Create role
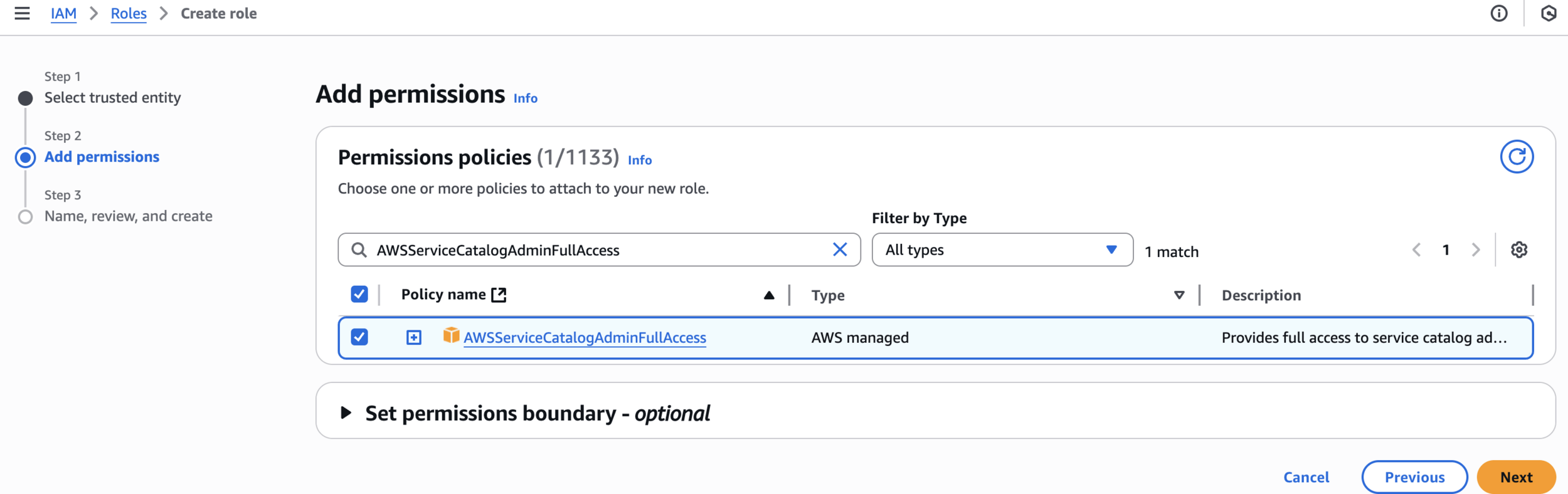
Add permissions
AWSServiceCatalogAdminFullAccess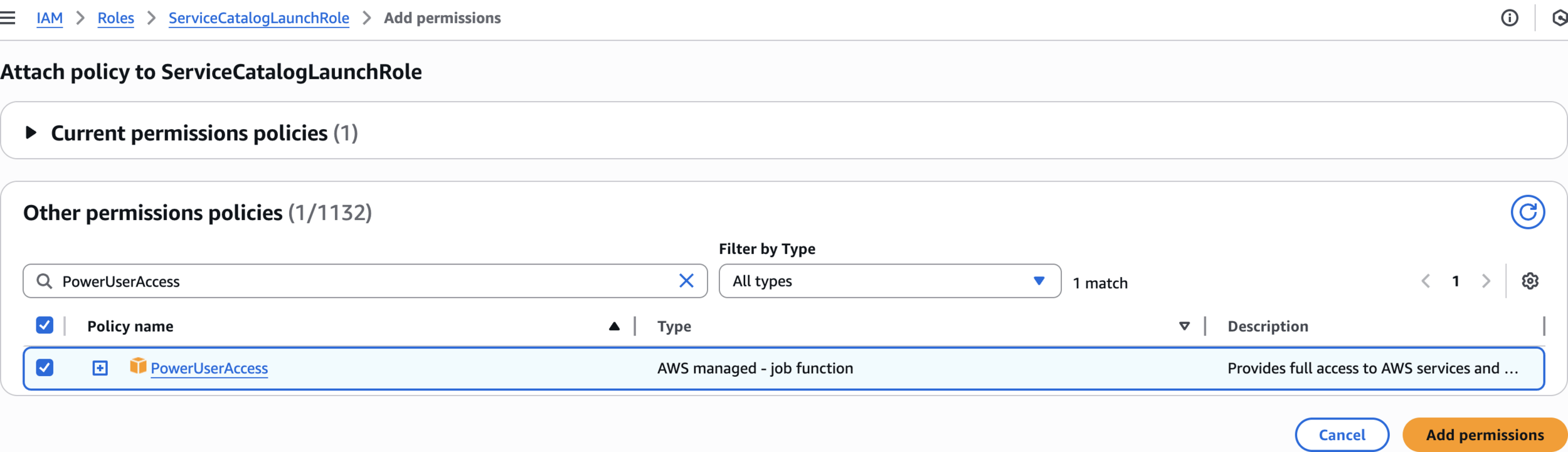
Attach policy to ServiceCatalogLaunchRole
PowerUserAccess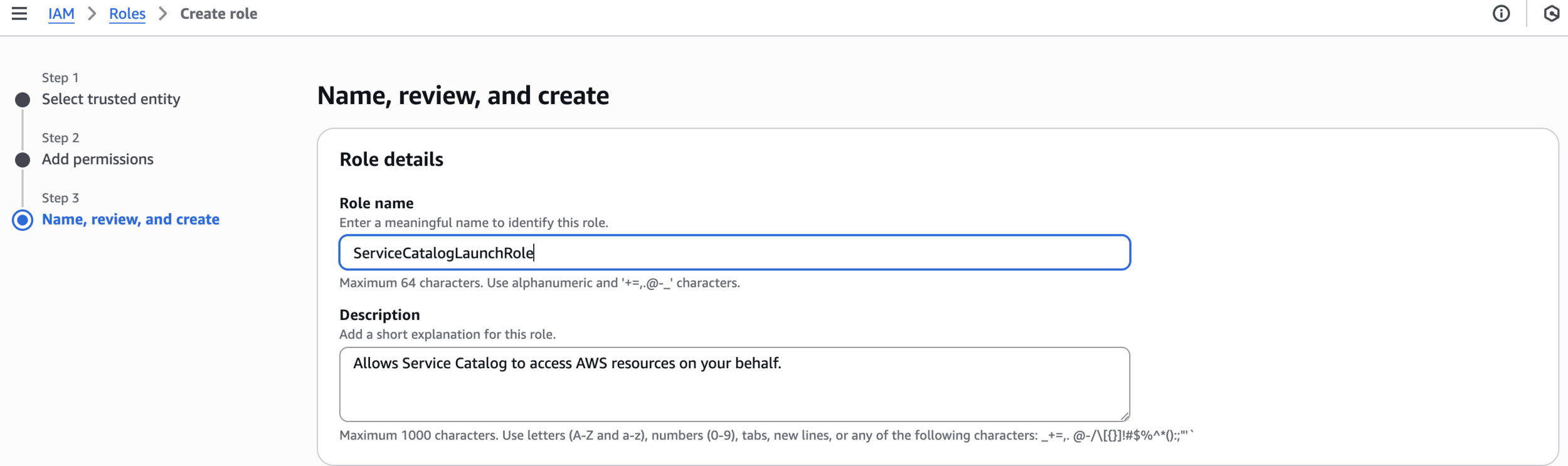
Name, review, and create
ServiceCatalogLaunchRole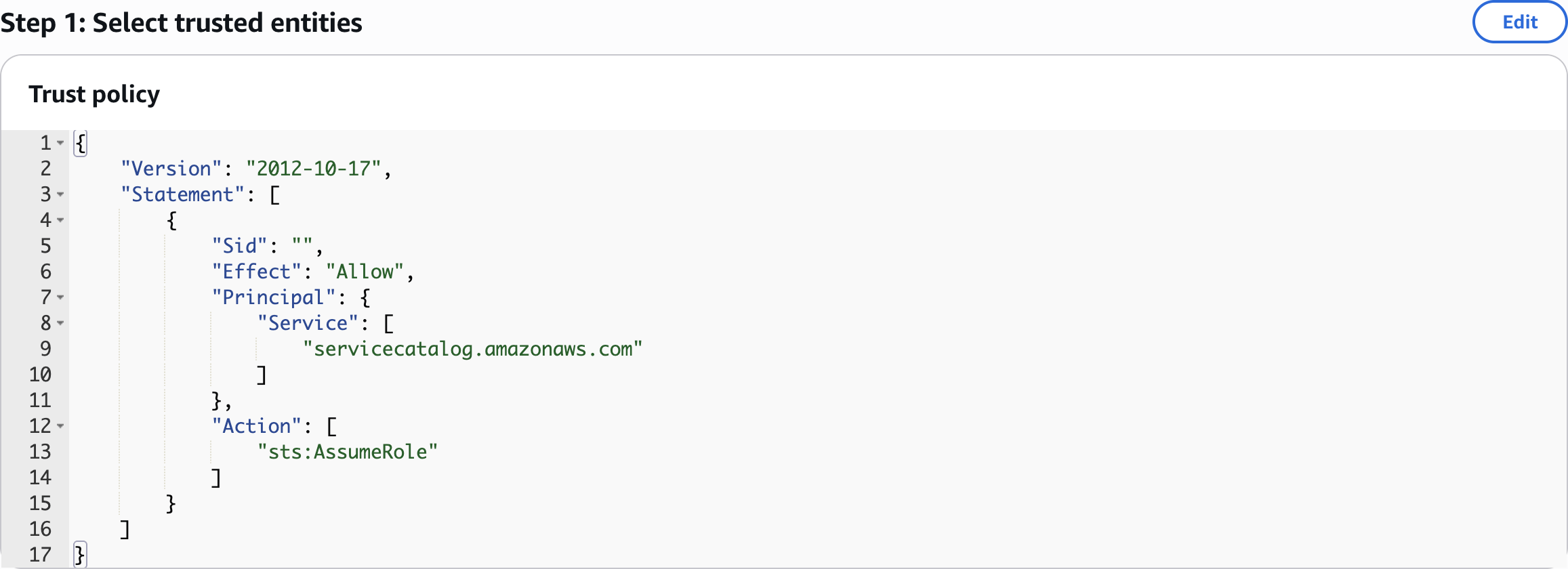
Select trusted entities
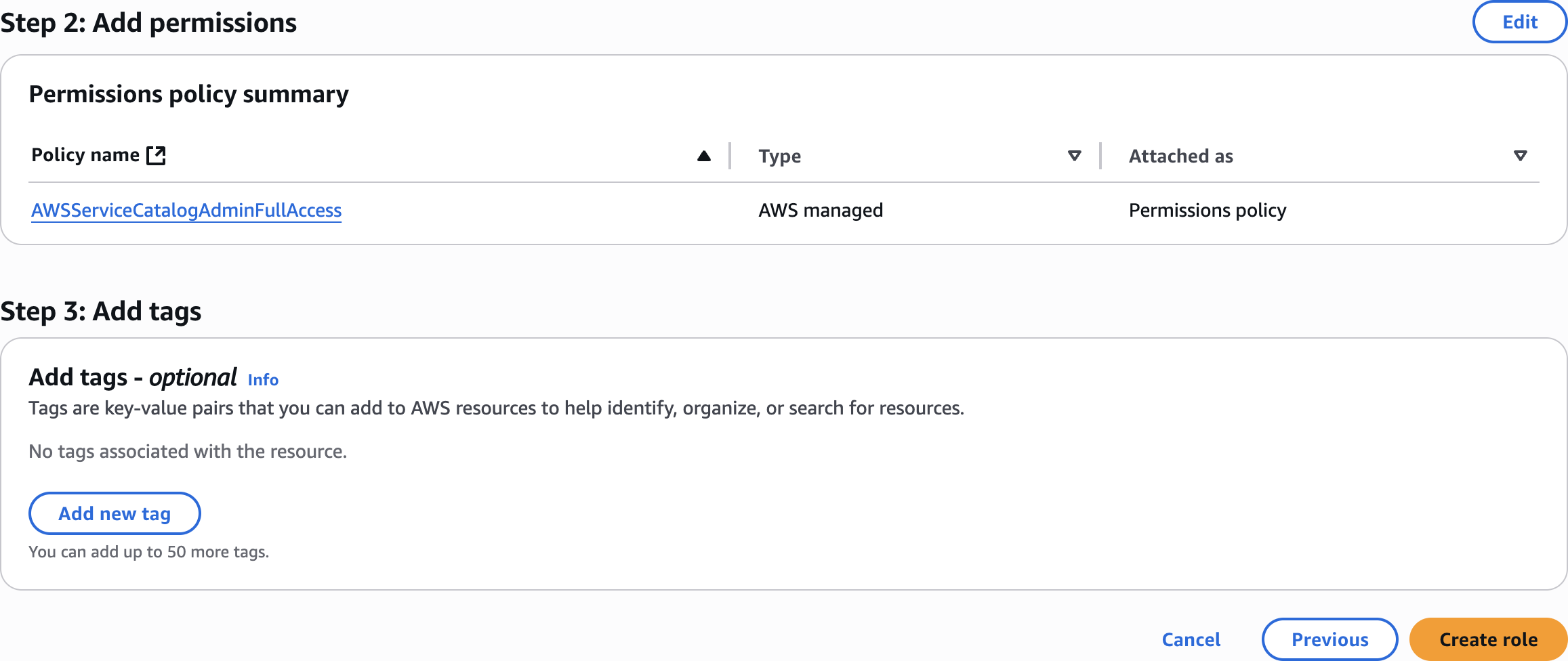
Add permissions
Step 2: Create a Service Catalog Portfolio
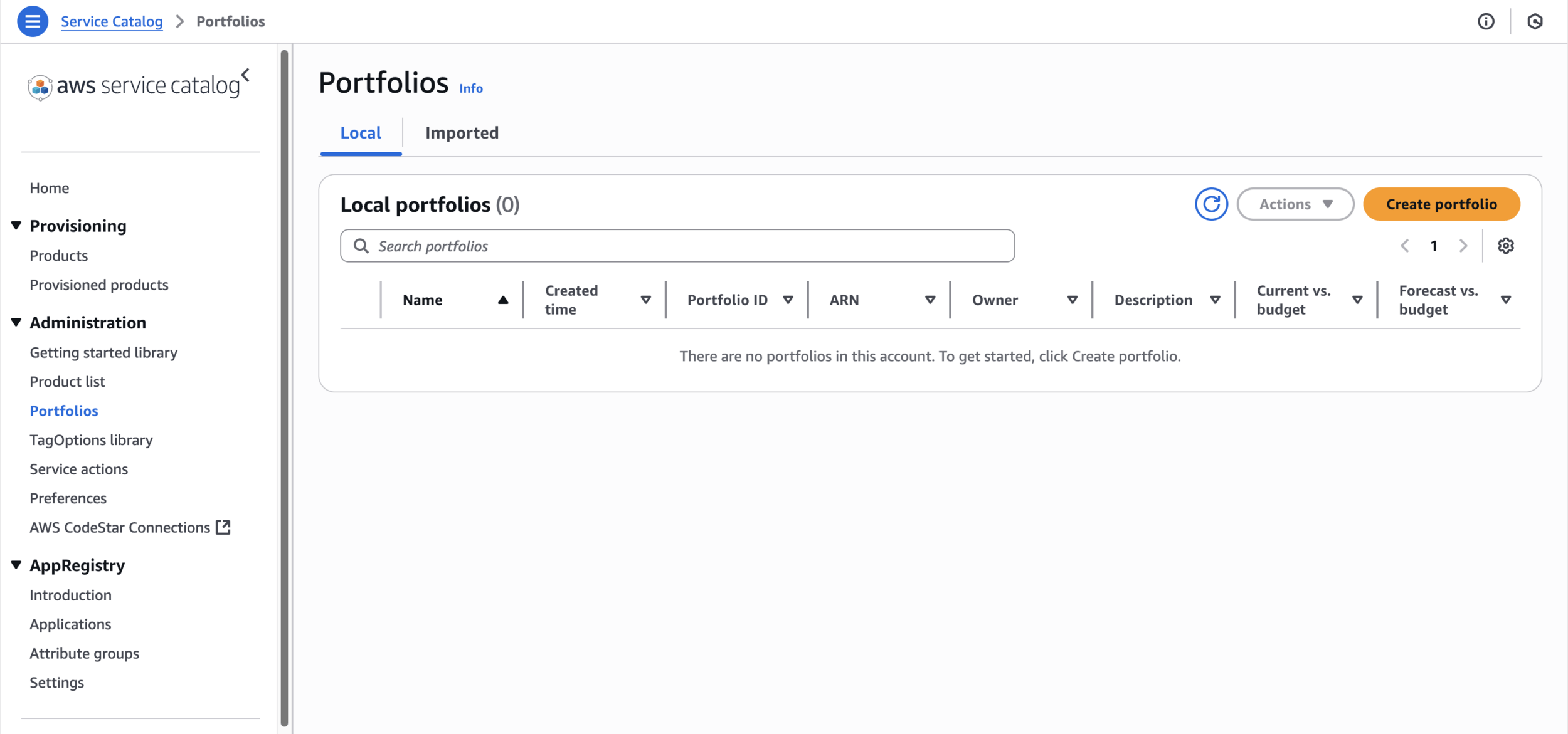
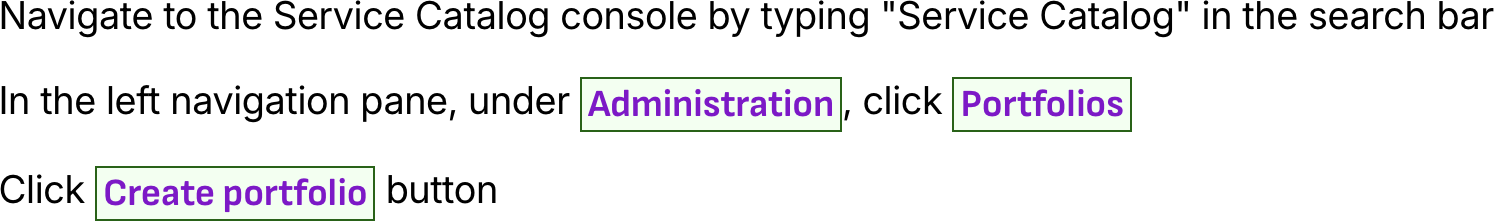
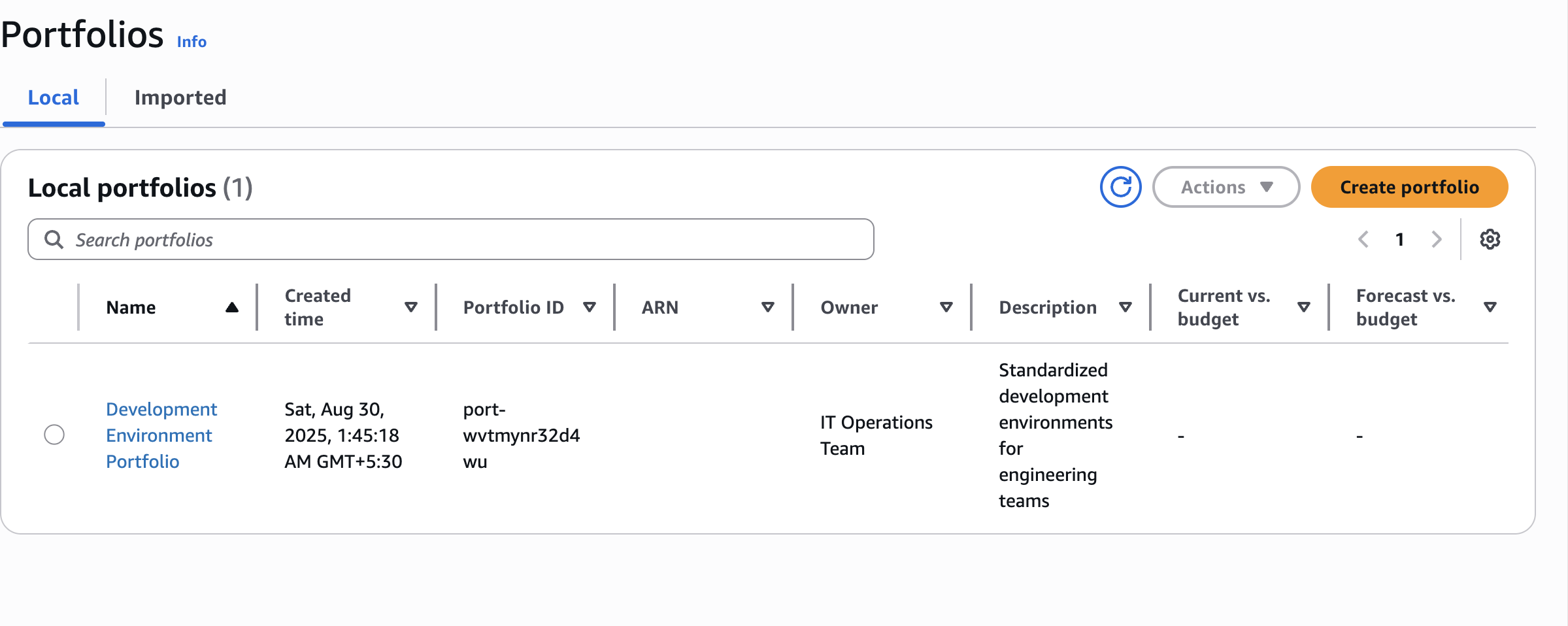
Portfolios
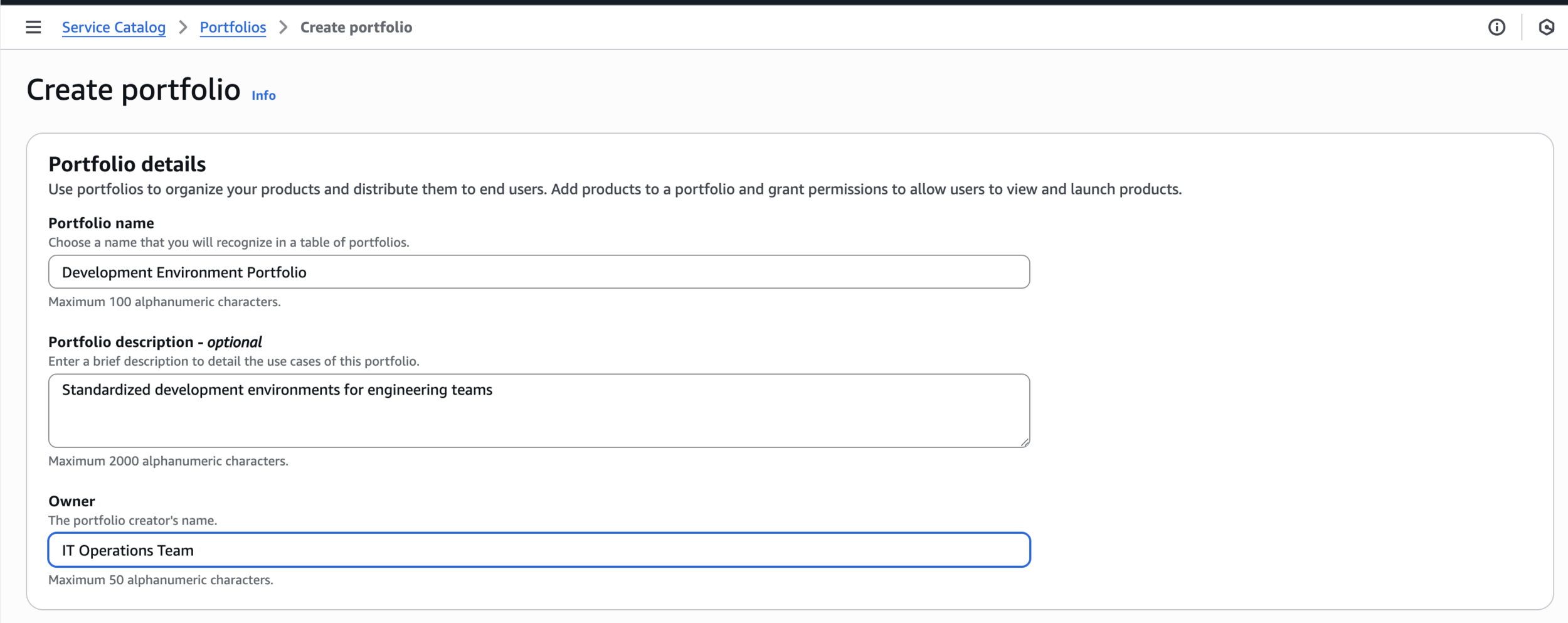
Development Environment PortfolioCreate portfolio
Standardized development environments for engineering teamsIT Operations Team
Manage tags
Step 3: Create a CloudFormation Template for the Product
Create a file named development-ec2-template.yaml with the following content:
development-ec2-template.yamlAWSTemplateFormatVersion: '2010-09-09'
Description: 'Development EC2 Instance - Service Catalog Product'
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: "Instance Configuration"
Parameters:
- InstanceType
- KeyPairName
- Label:
default: "Environment Settings"
Parameters:
- EnvironmentName
ParameterLabels:
InstanceType:
default: "EC2 Instance Type"
KeyPairName:
default: "SSH Key Pair"
EnvironmentName:
default: "Environment Name"
Parameters:
InstanceType:
Type: String
Default: t3.micro
AllowedValues:
- t2.micro
- t2.small
- t3.micro
- t3.small
Description: EC2 instance type for development environment
EnvironmentName:
Type: String
Default: Development
Description: Environment name tag for the instance
MinLength: 1
MaxLength: 50
KeyPairName:
Type: AWS::EC2::KeyPair::KeyName
Description: Name of an existing EC2 KeyPair to enable SSH access
ConstraintDescription: Must be the name of an existing EC2 KeyPair
Mappings:
RegionMap:
us-east-1:
AMI: ami-00ca32bbc84273381 # Amazon Linux 2023
us-west-1:
AMI: ami-0e0ece251c1638797 # Amazon Linux 2023
us-west-2:
AMI: ami-002829755fa238bfa # Amazon Linux 2023
us-east-2:
AMI: ami-024e6efaf93d85776 # Amazon Linux 2023
eu-west-1:
AMI: ami-0b9fd8b55a6e3c9d5 # Amazon Linux 2023
eu-central-1:
AMI: ami-0669b163befffbdfc # Amazon Linux 2023
ap-southeast-1:
AMI: ami-0464f90f5928bccb8 # Amazon Linux 2023
ap-northeast-1:
AMI: ami-089a156ea4f52a0a3 # Amazon Linux 2023
Resources:
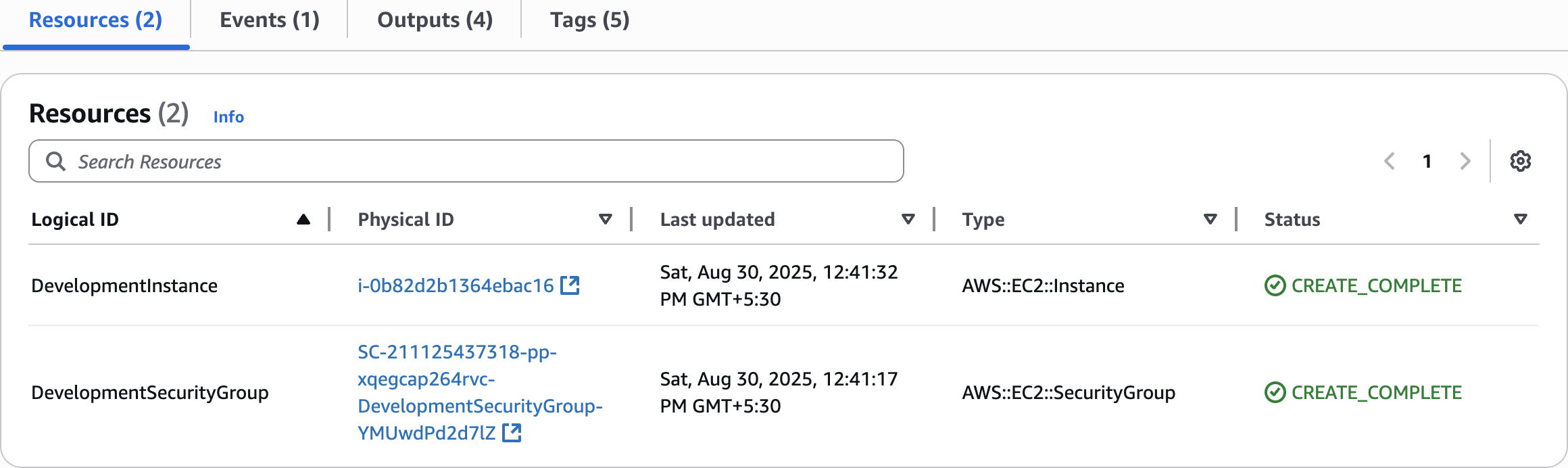
DevelopmentSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Security group for development EC2 instance
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 443
ToPort: 443
CidrIp: 0.0.0.0/0
Tags:
- Key: Name
Value: !Sub ${EnvironmentName}-SecurityGroup
- Key: Environment
Value: !Ref EnvironmentName
DevelopmentInstance:
Type: AWS::EC2::Instance
Properties:
InstanceType: !Ref InstanceType
ImageId: !FindInMap [ RegionMap, !Ref 'AWS::Region', AMI ]
KeyName: !Ref KeyPairName
SecurityGroups:
- !Ref DevelopmentSecurityGroup
Tags:
- Key: Name
Value: !Sub ${EnvironmentName}-Instance
- Key: Environment
Value: !Ref EnvironmentName
- Key: ManagedBy
Value: ServiceCatalog
UserData:
Fn::Base64: !Sub |
#!/bin/bash
dnf update -y
dnf install -y httpd
systemctl start httpd
systemctl enable httpd
echo "<h1>Development Environment - ${EnvironmentName}</h1>" > /var/www/html/index.html
echo "<p>Instance Type: ${InstanceType}</p>" >> /var/www/html/index.html
echo "<p>Region: ${AWS::Region}</p>" >> /var/www/html/index.html
Outputs:
InstanceId:
Description: Instance ID of the development EC2 instance
Value: !Ref DevelopmentInstance
PublicIP:
Description: Public IP address of the instance
Value: !GetAtt DevelopmentInstance.PublicIp
WebURL:
Description: URL to access the web server
Value: !Sub 'http://${DevelopmentInstance.PublicIp}'
Step 4: Create a Service Catalog Product
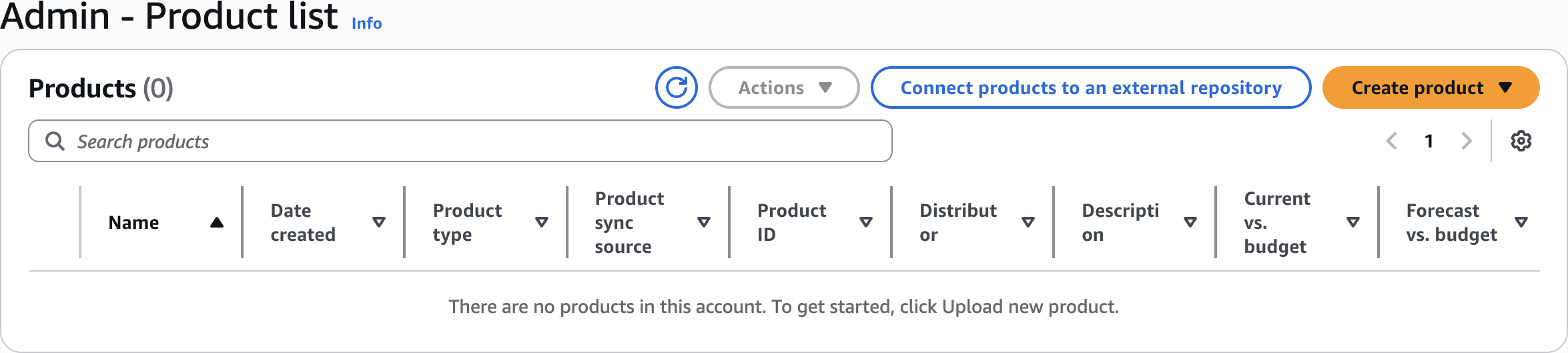
Create product
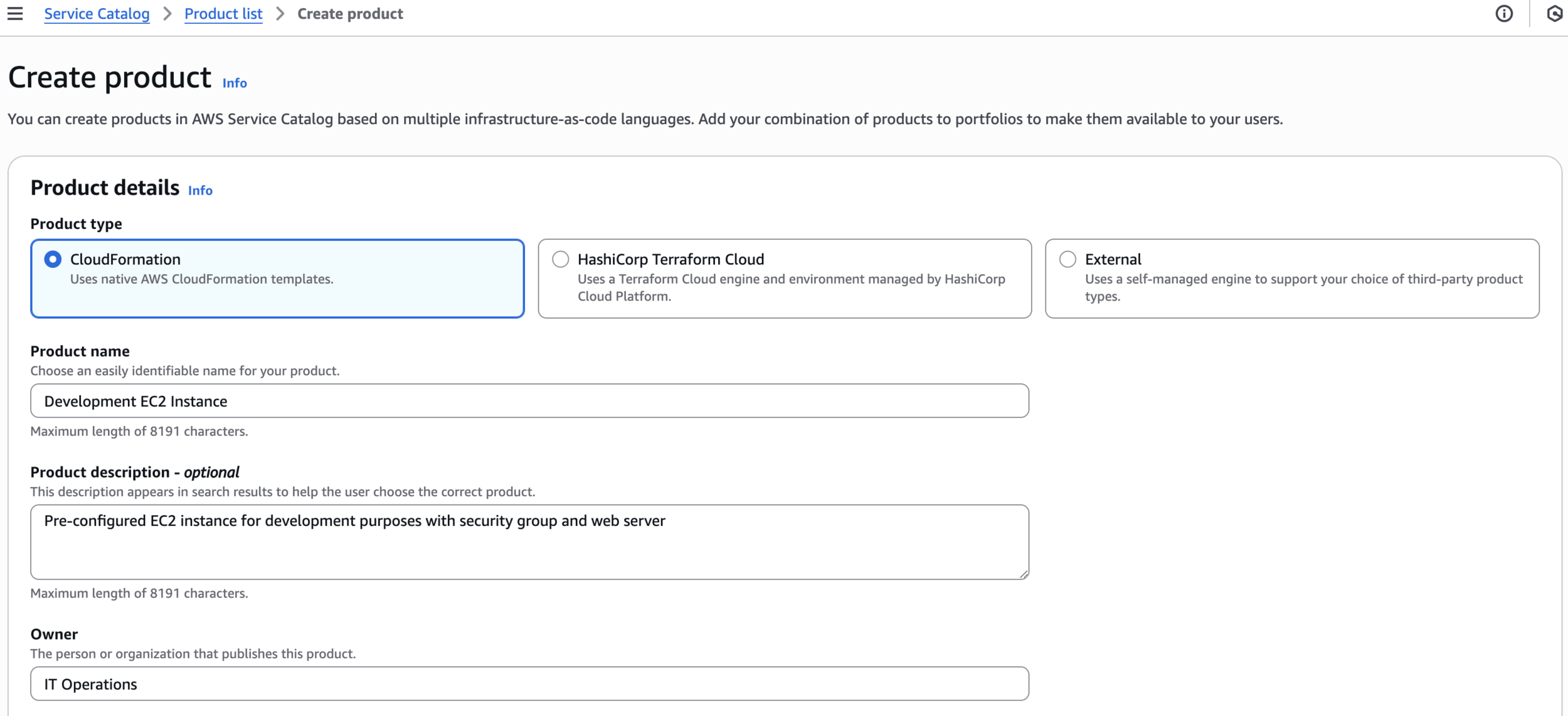
Development EC2 InstanceCreate product
Pre-configured EC2 instance for development purposes with security group and web serverIT Operations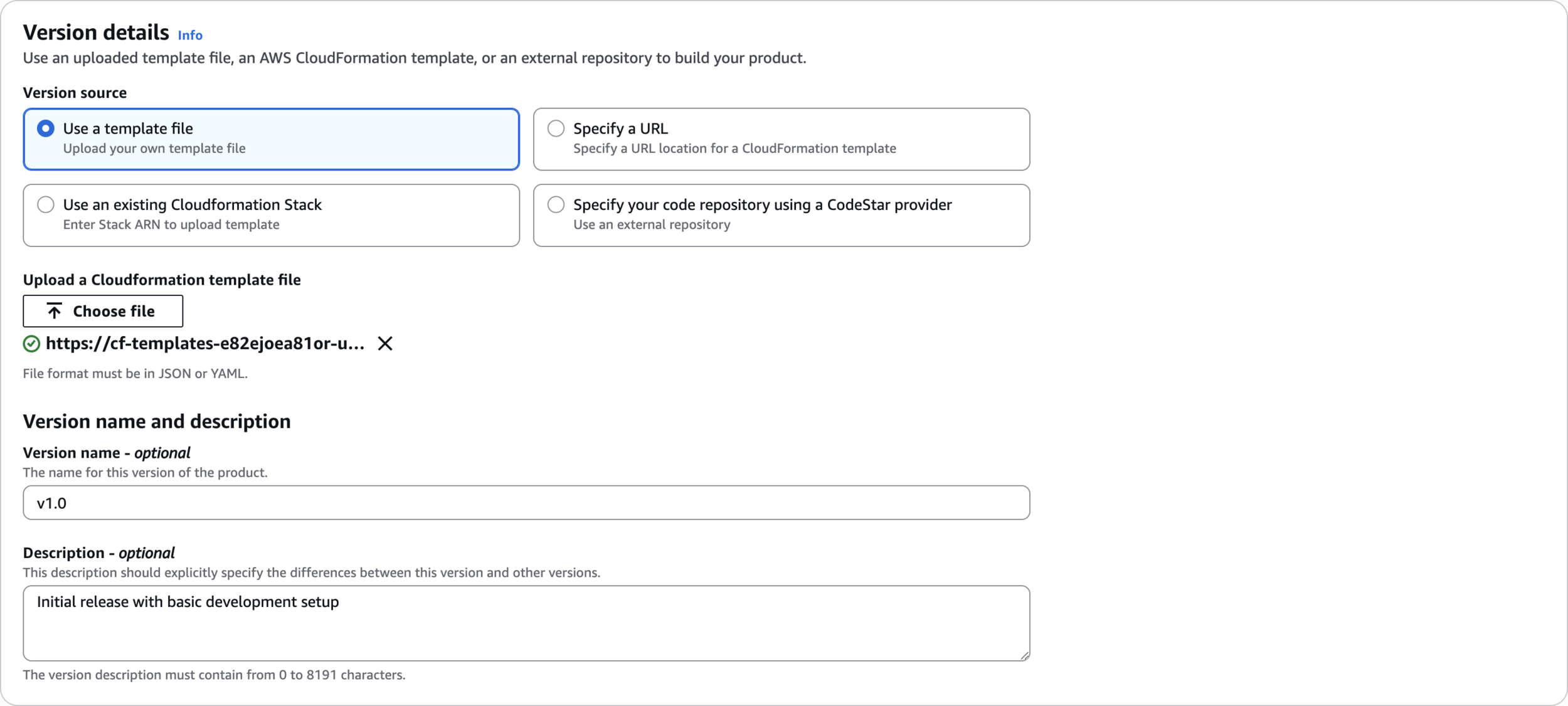
Version details
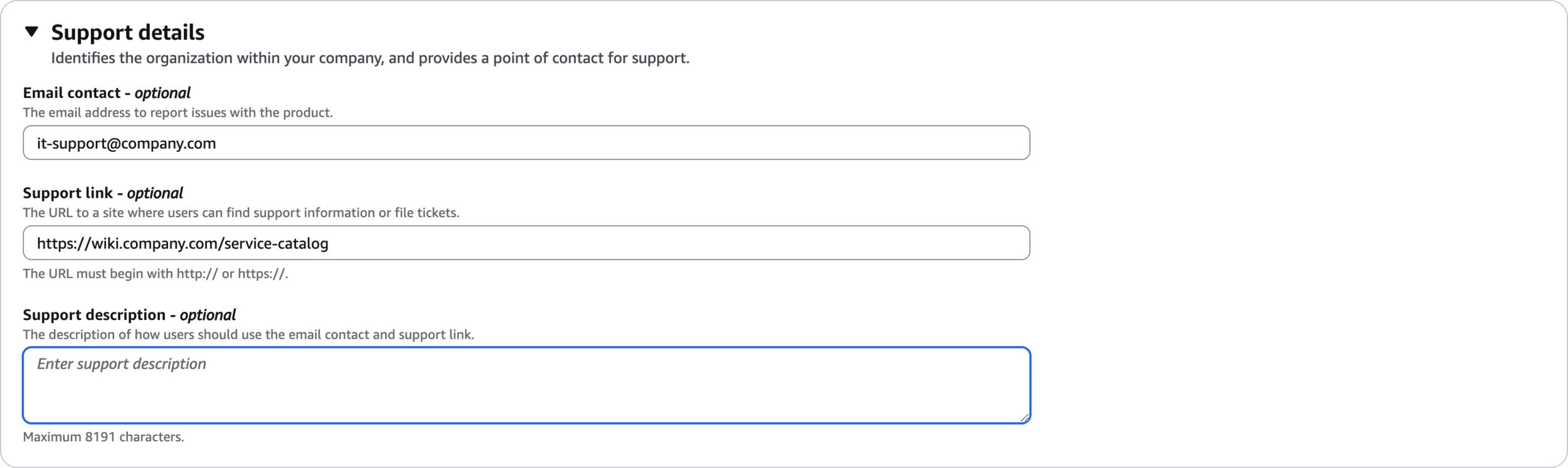
Support details
it-support@company.comhttps://wiki.company.com/service-catalog
Manage tags
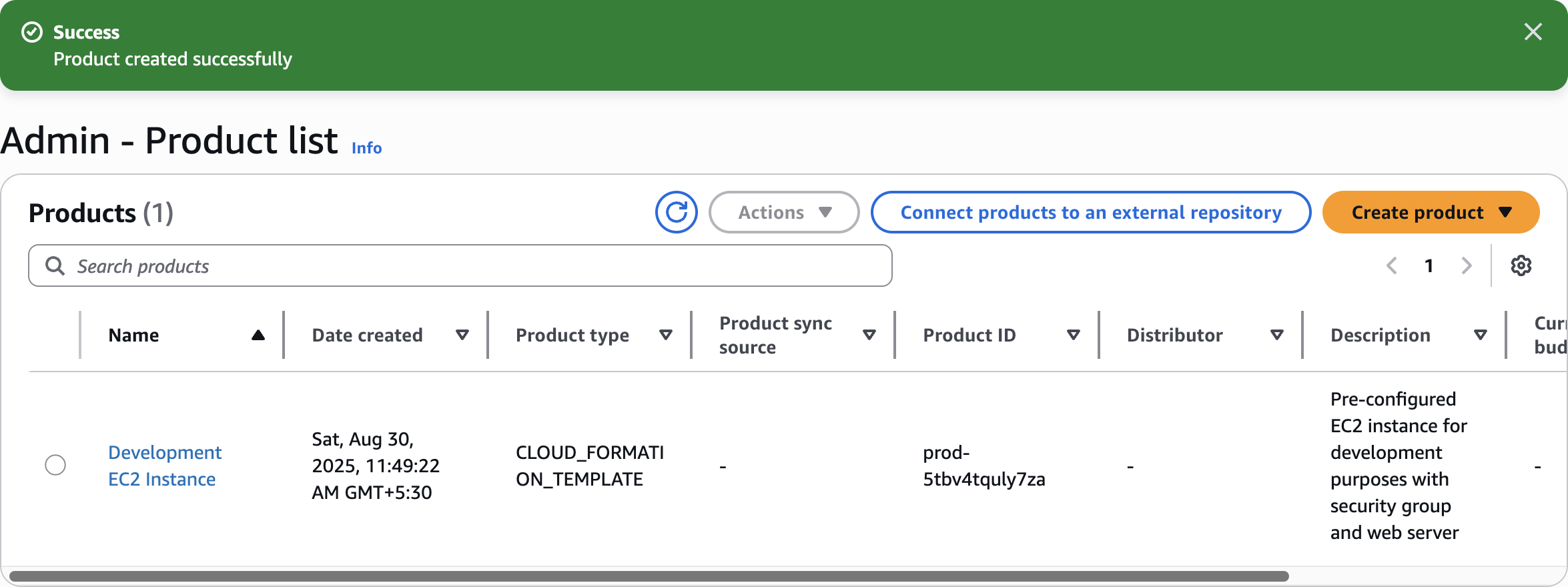
Product created successfully
Step 5: Add Product to Portfolio and Configure Constraints
Associate Product with Portfolio
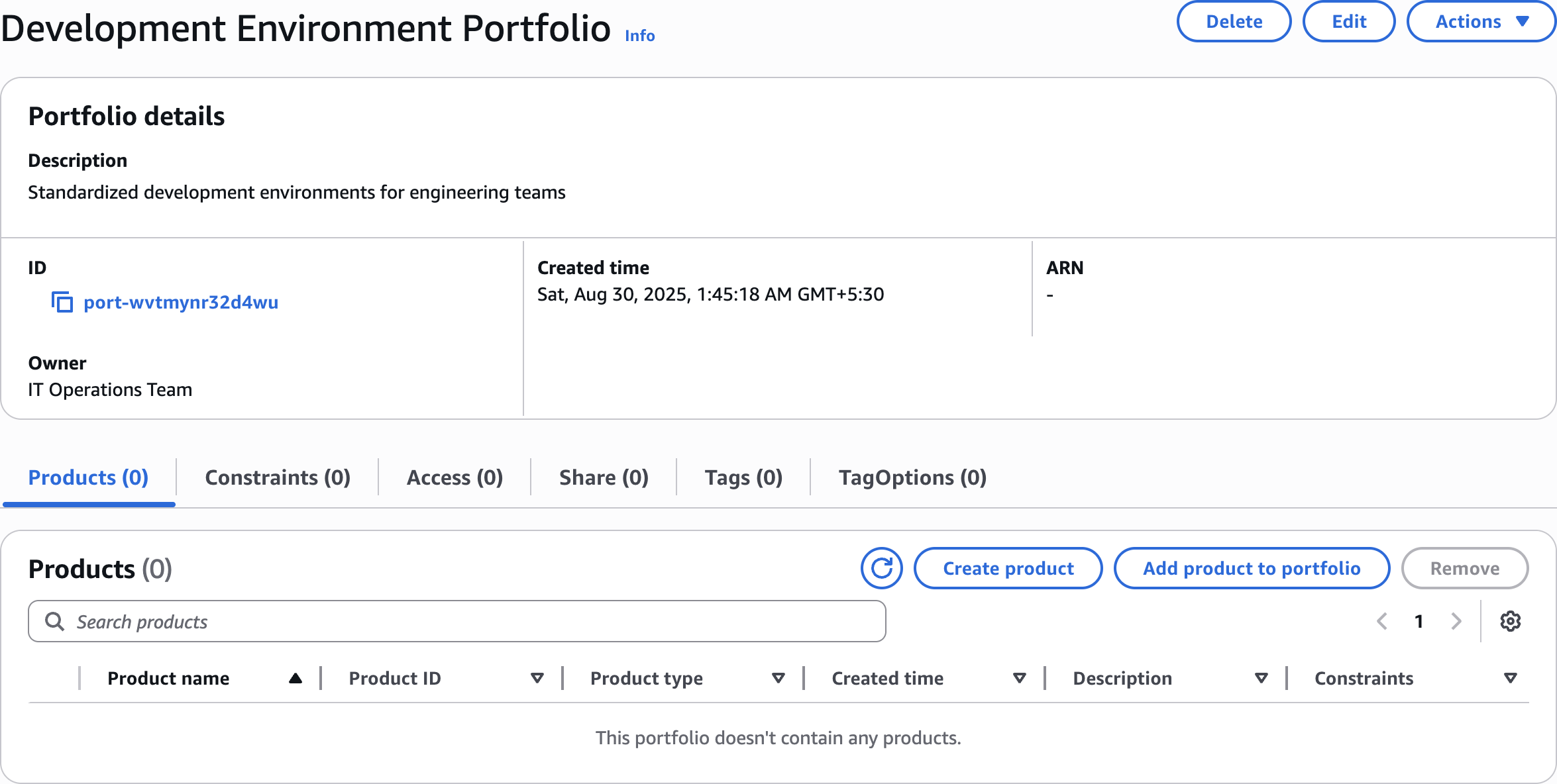
Add product to portfolio
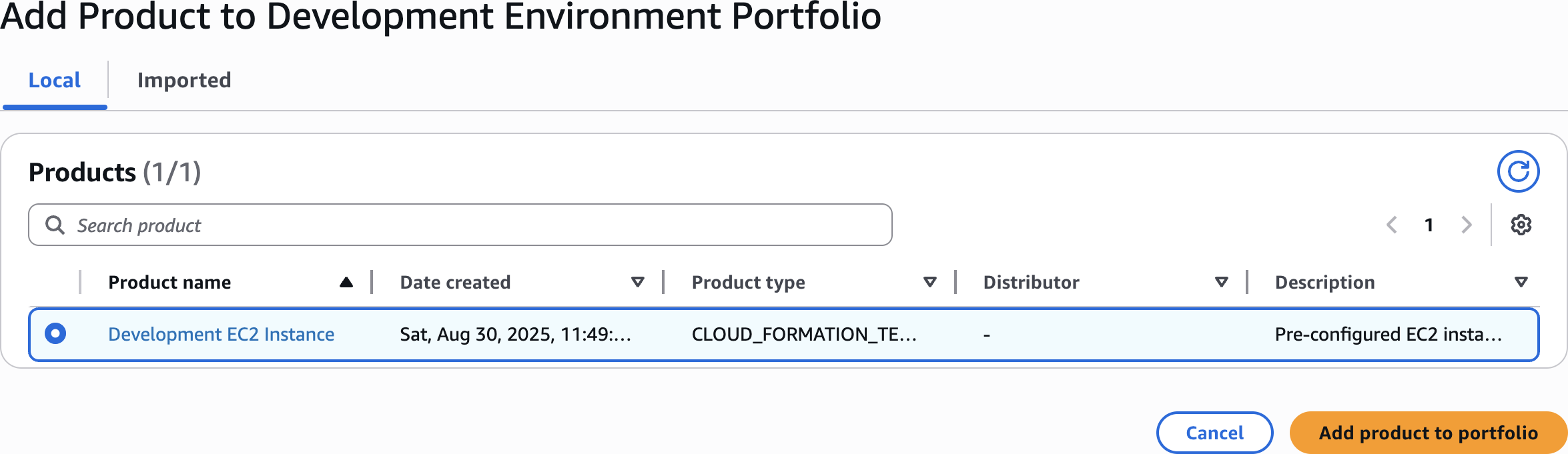
Add Product to Development Environment Portfolio
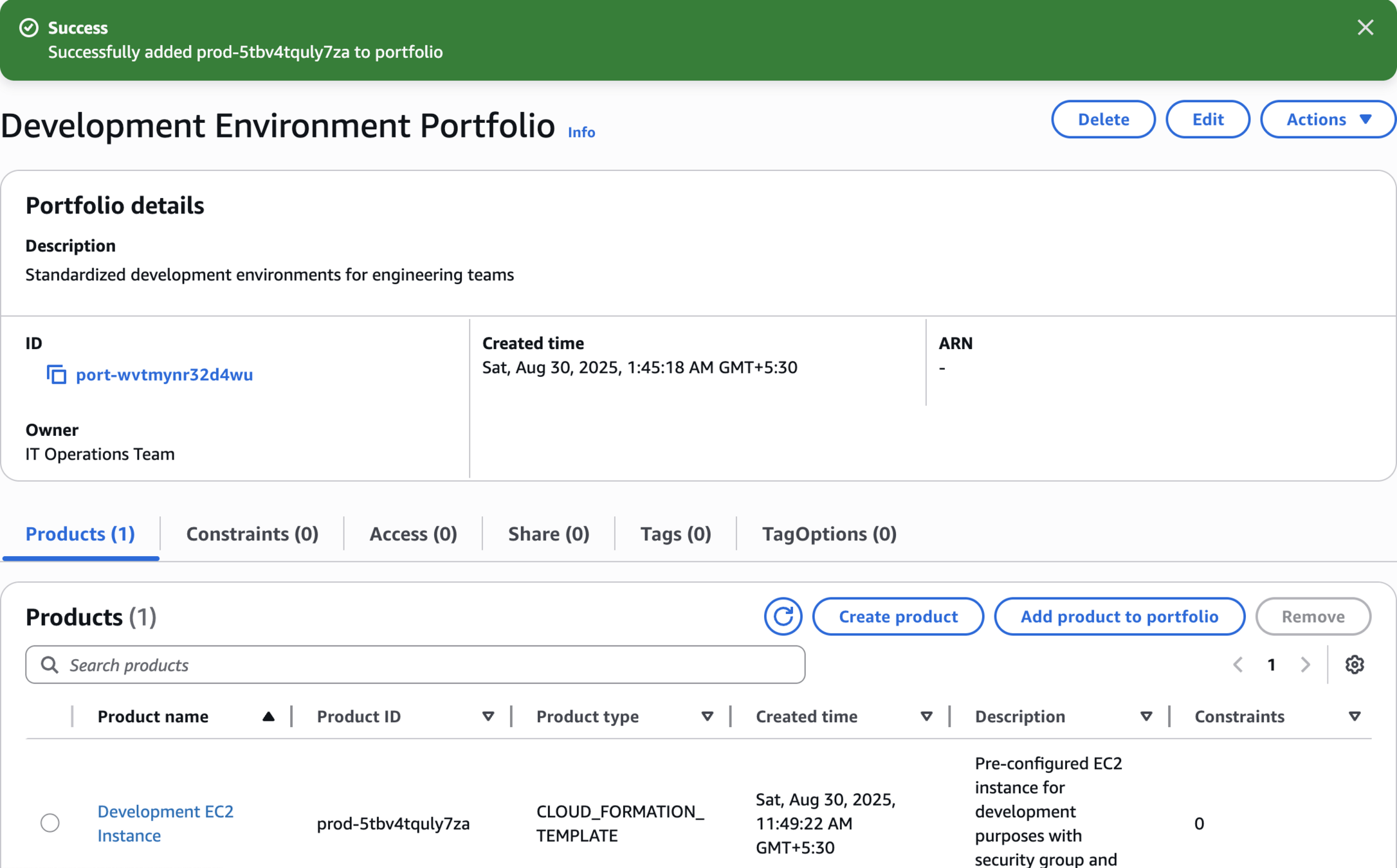
Add Launch Constraint
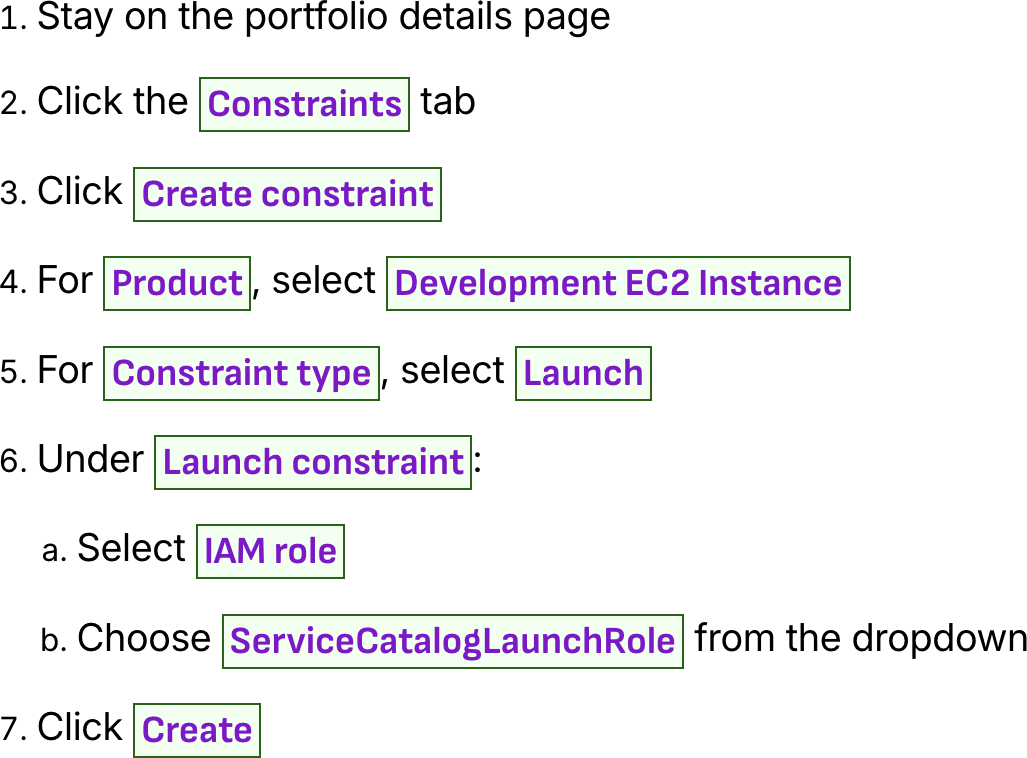
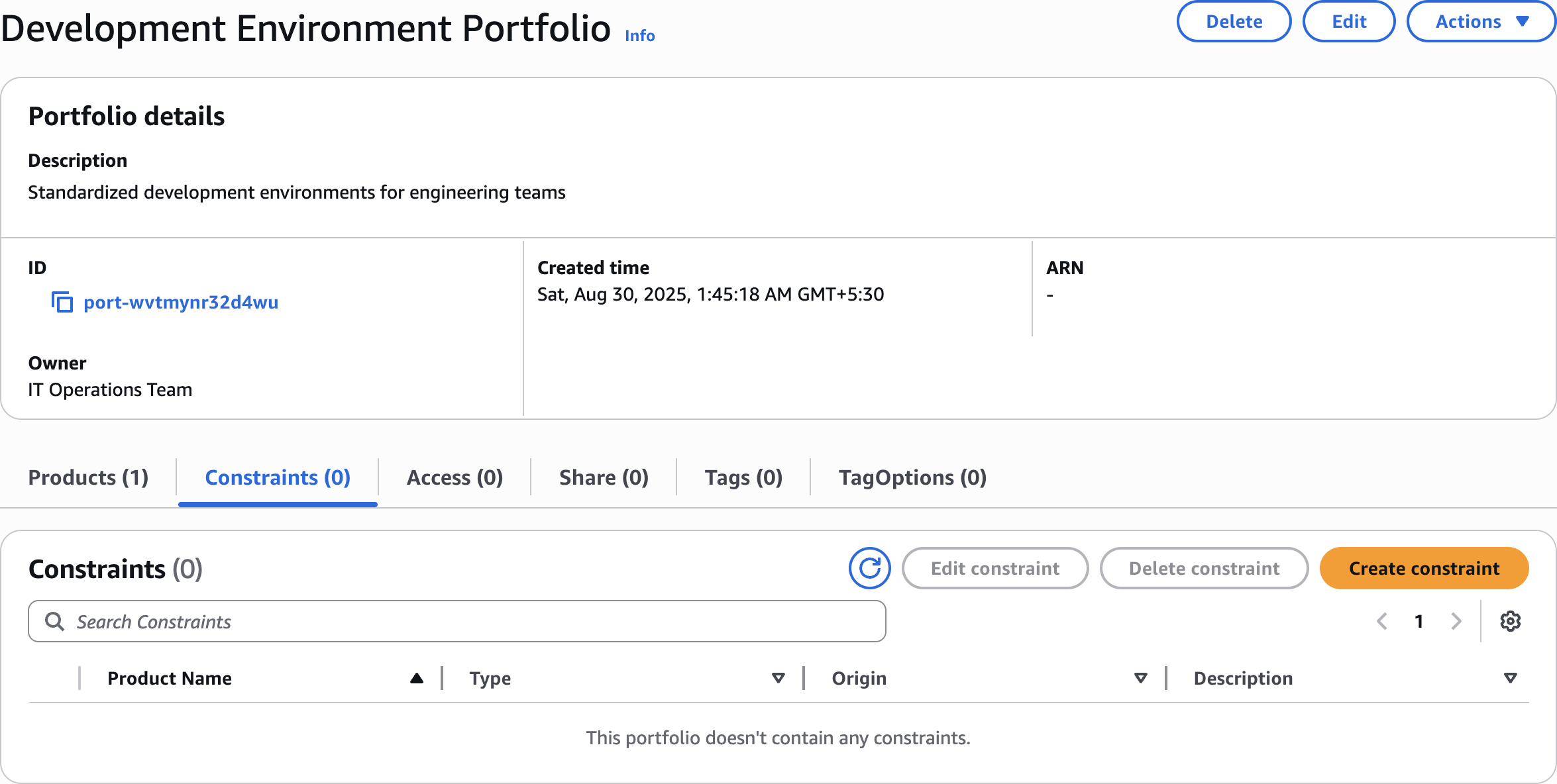
Create constraint
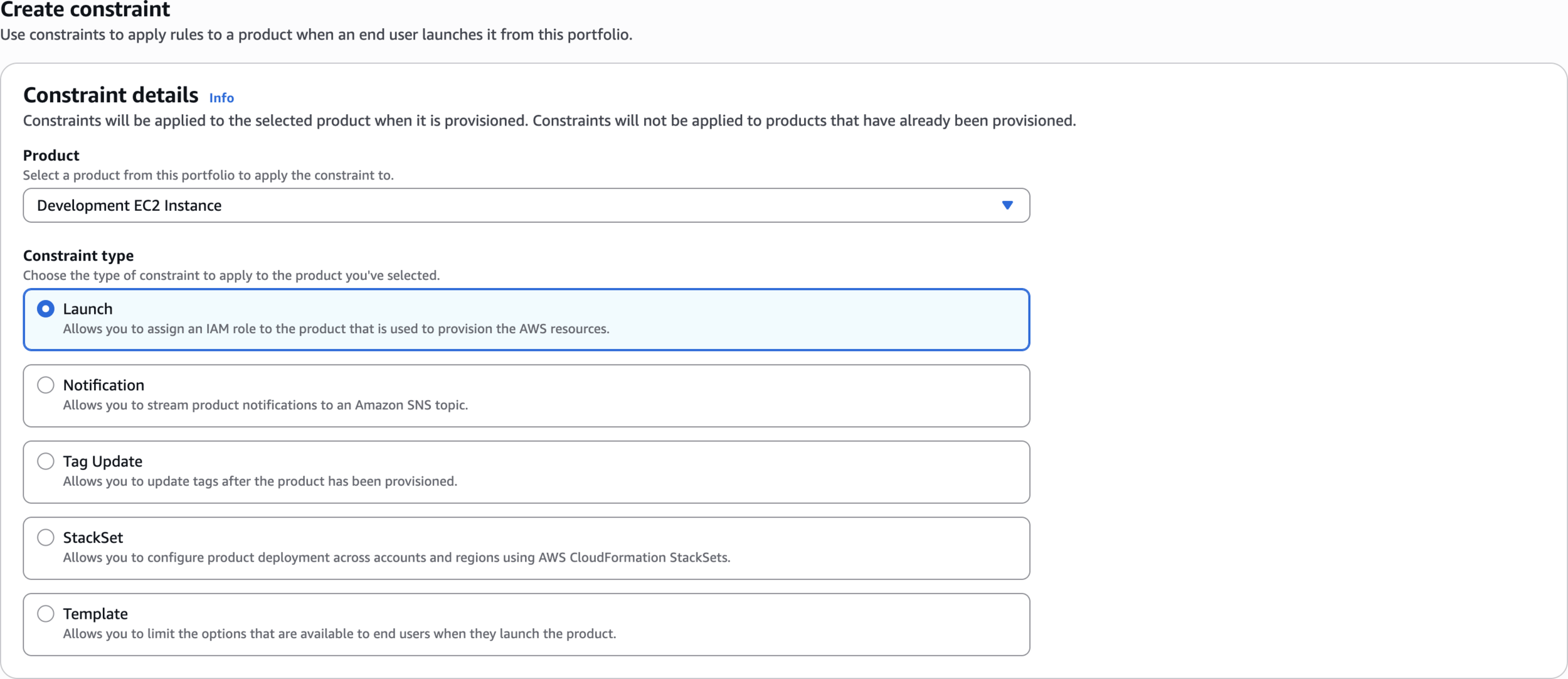
Constraint type
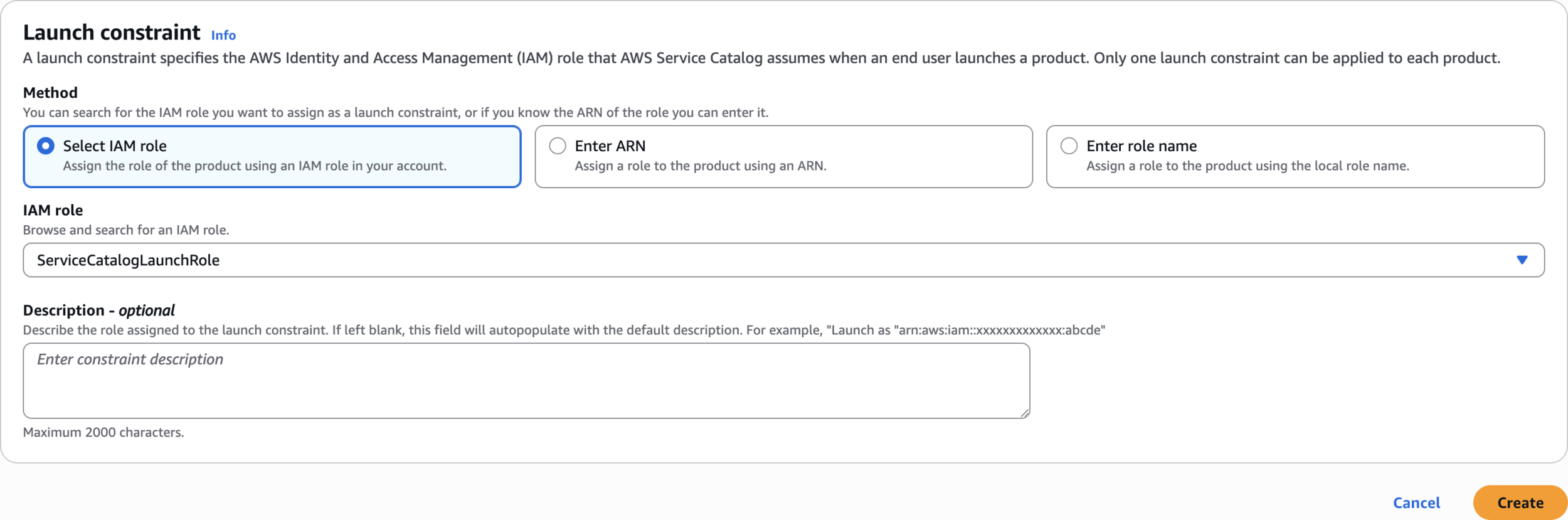
Select IAM role
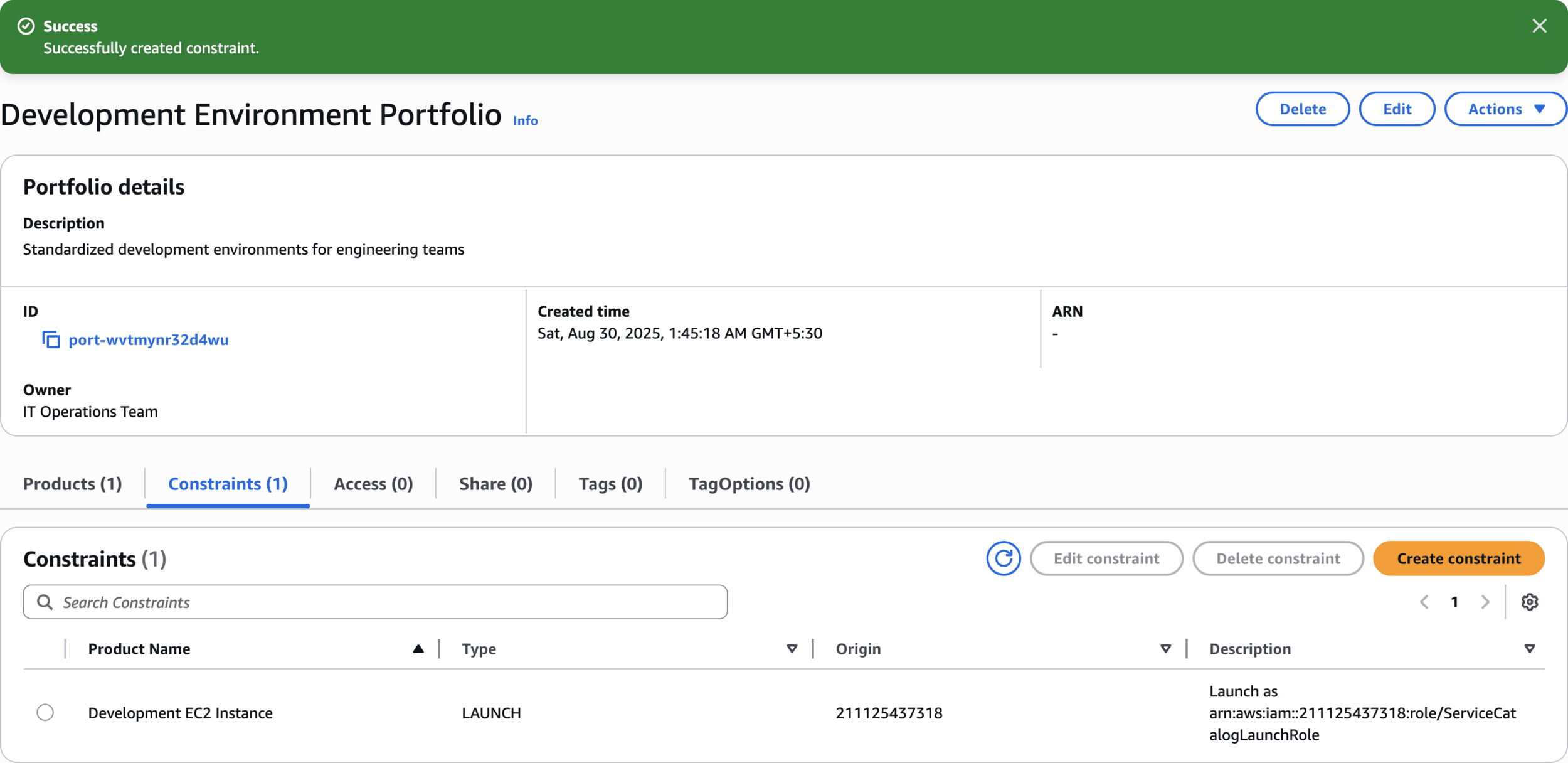
Successfully created constraint
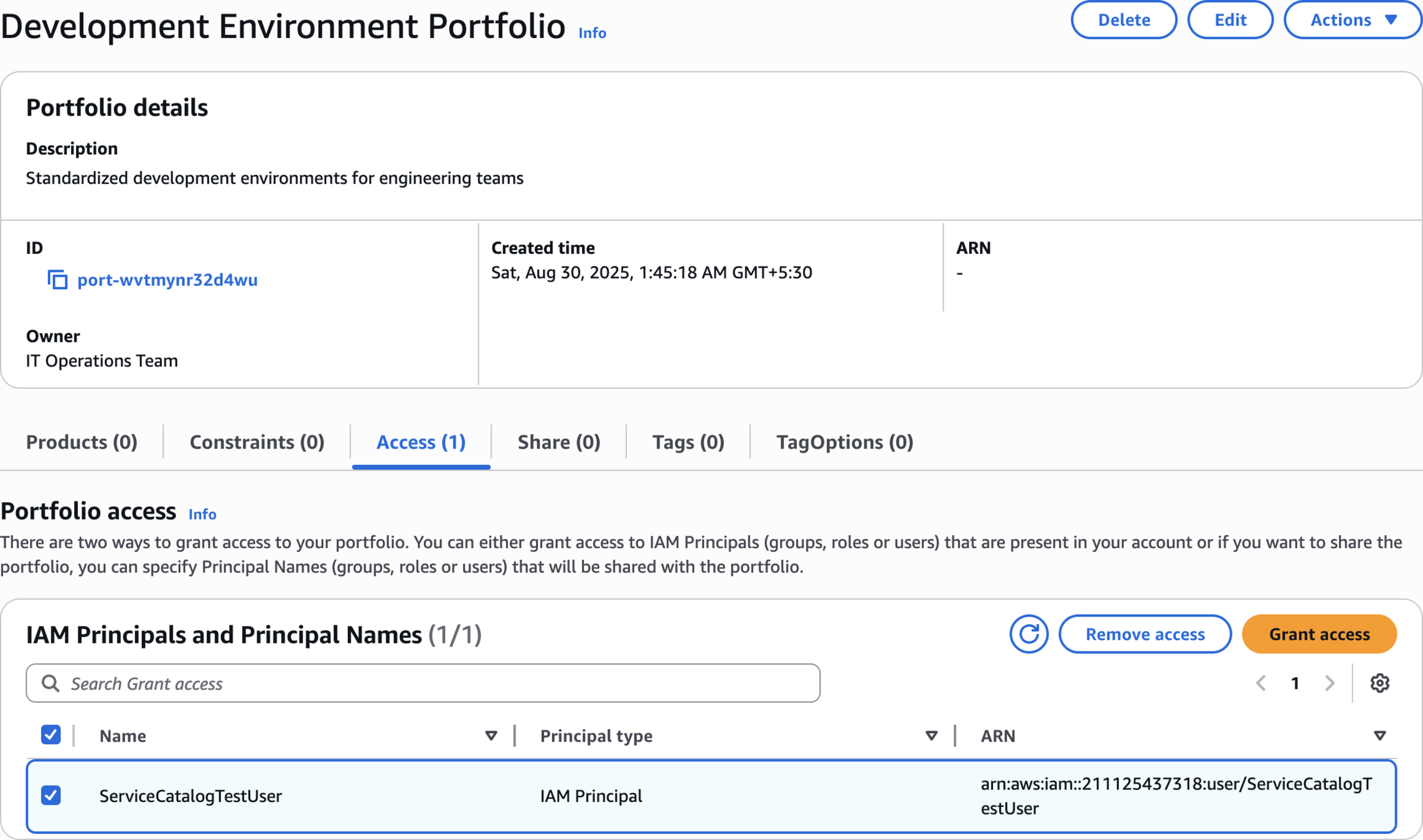
Access
Step 6: Create and Configure Test User
IAM - Create user
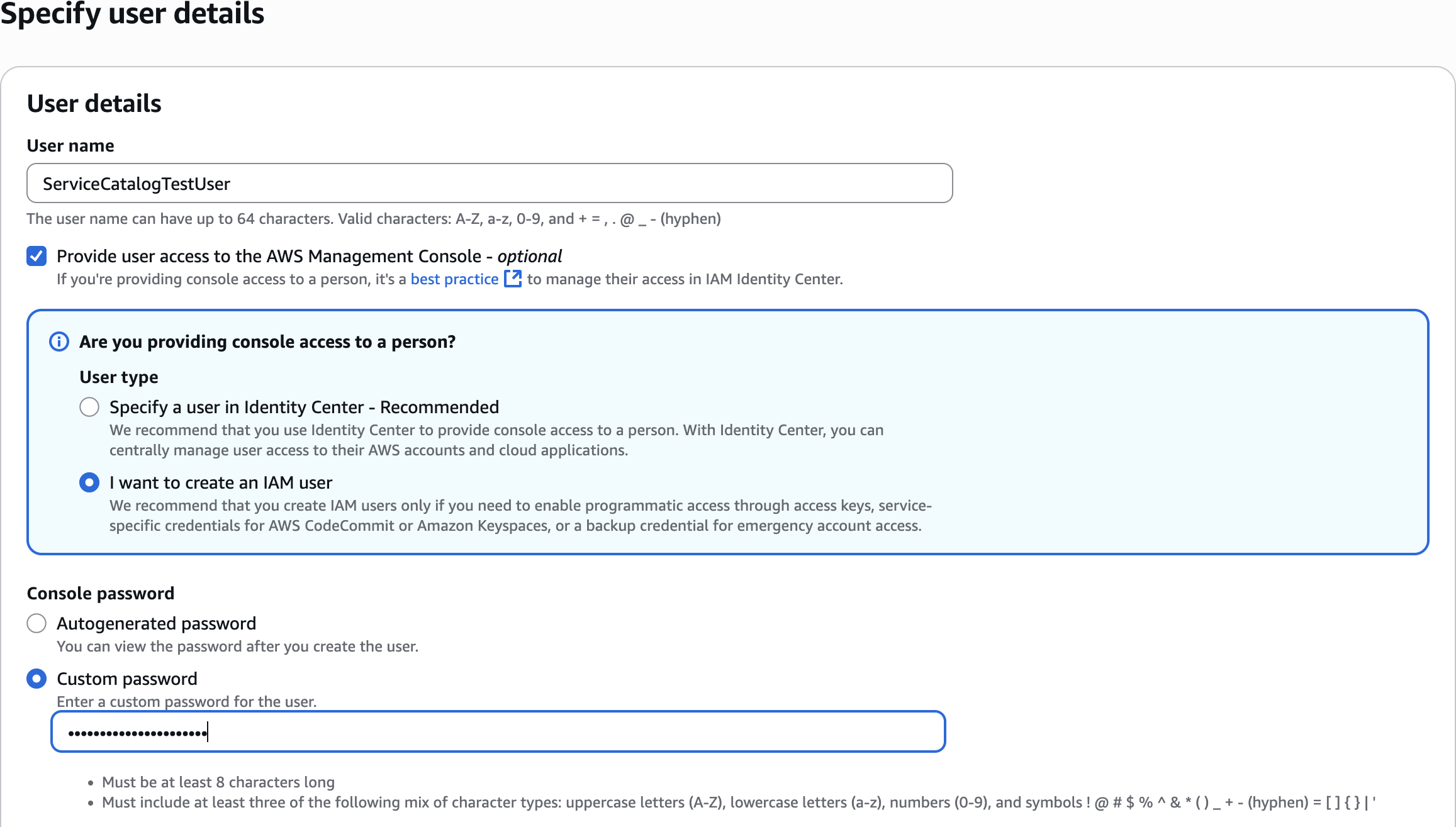
ServiceCatalog TestUser
Console password
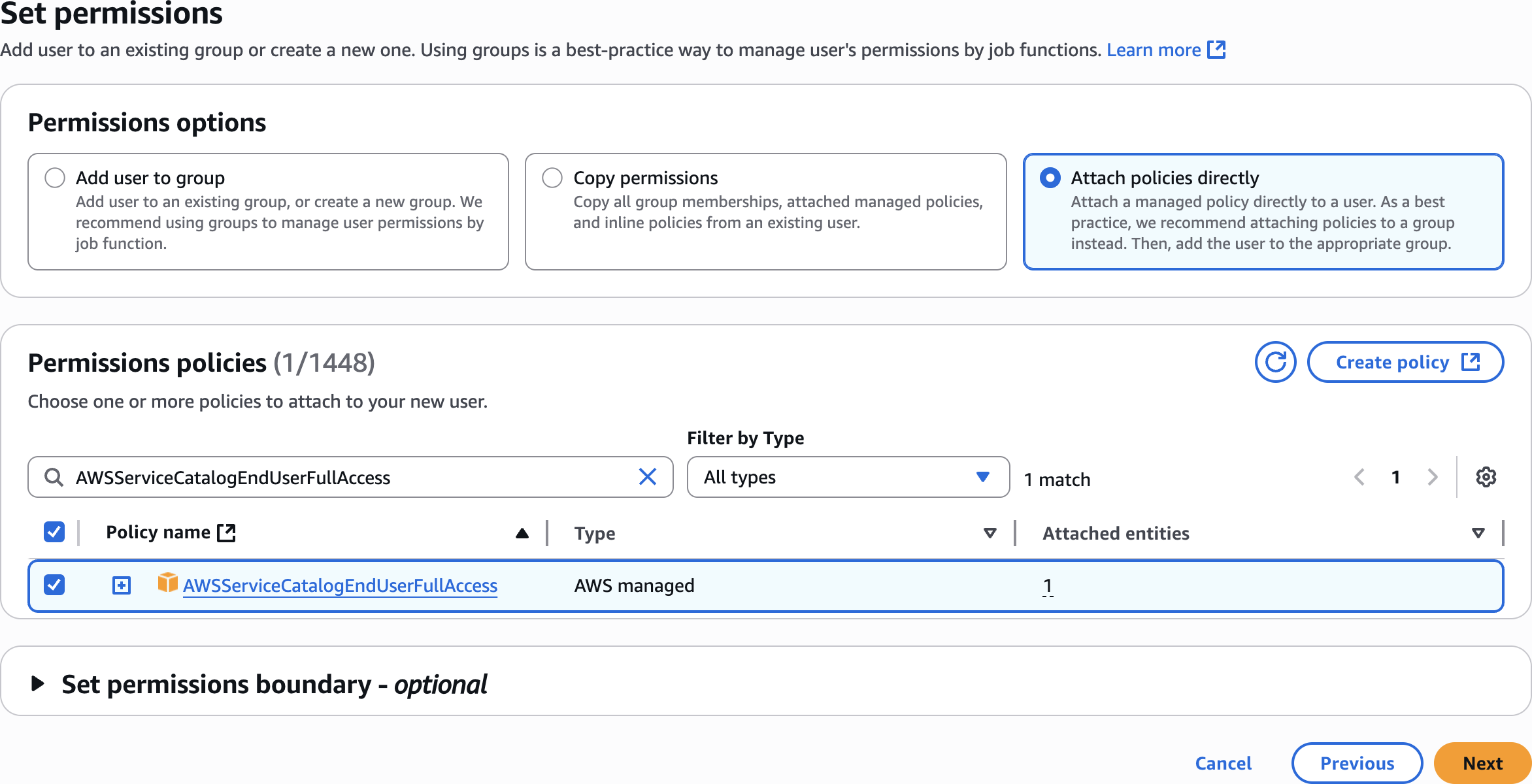
Set permissions
AWSServiceCatalogEndUserFullAccess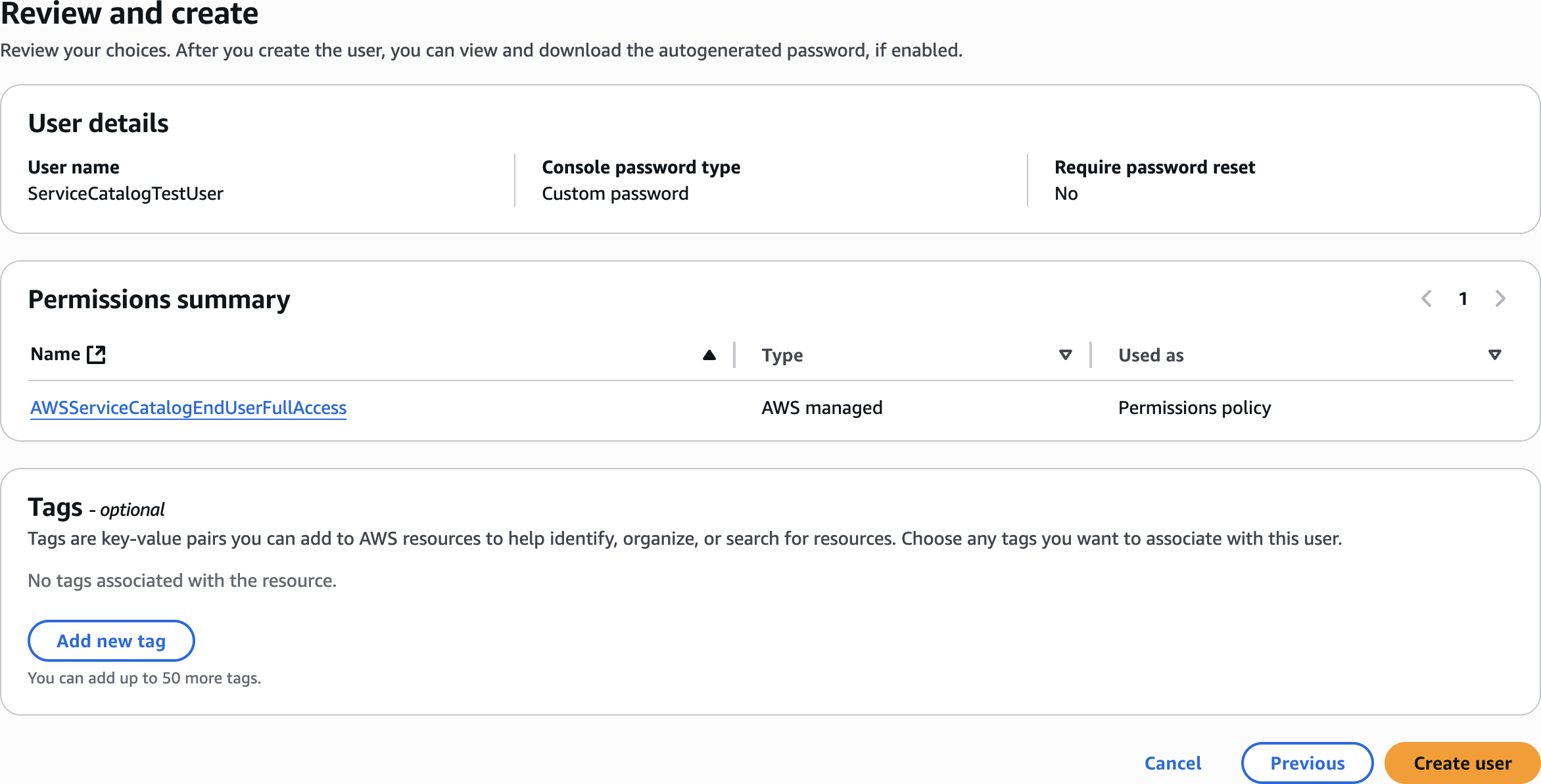
Review and create
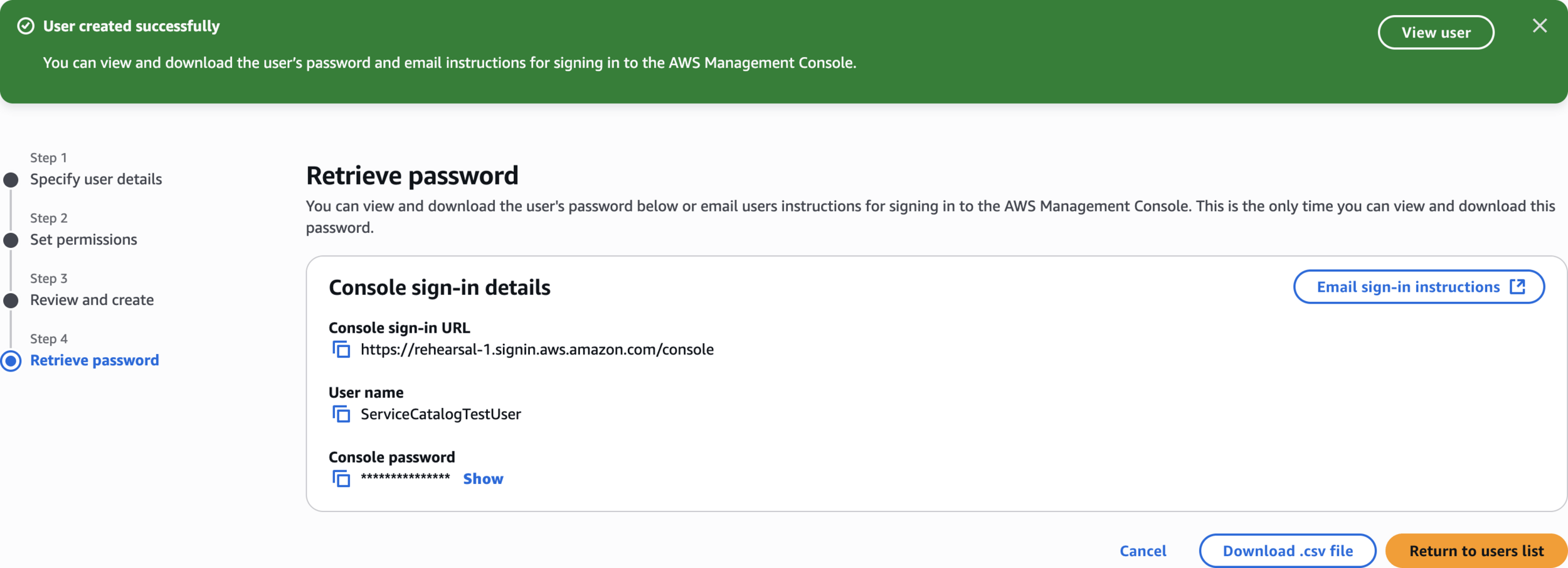
User created successfully
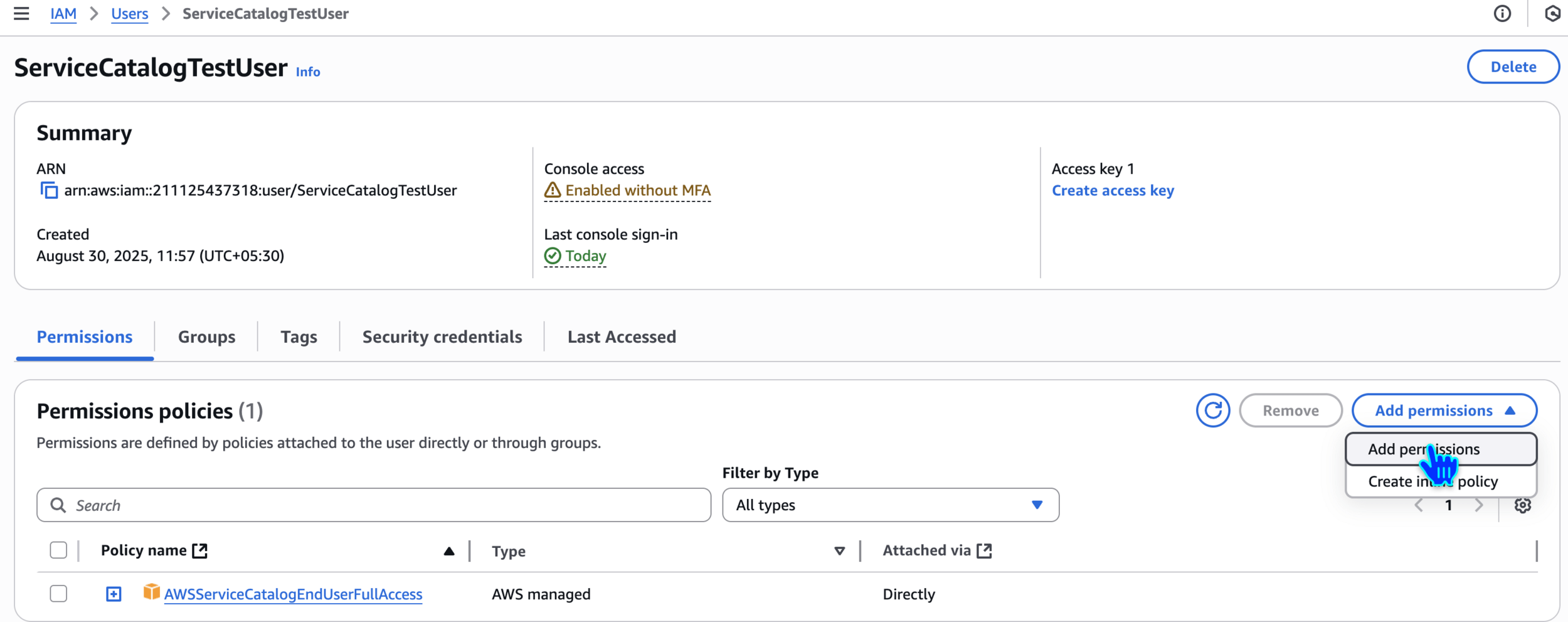
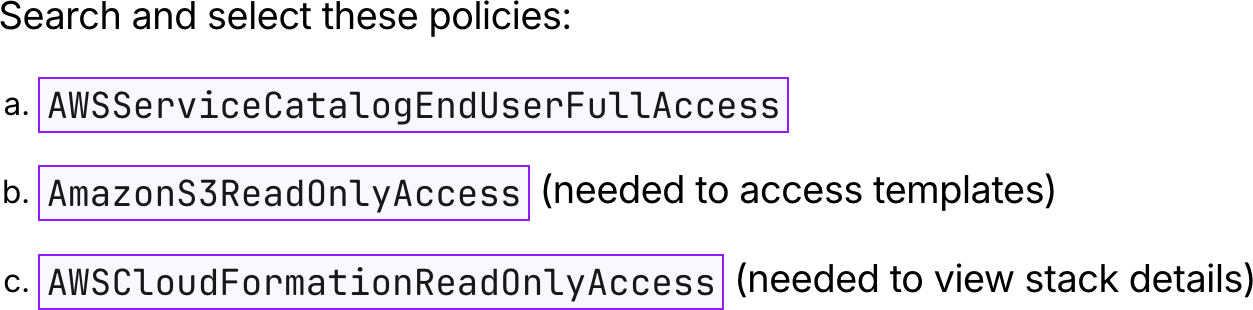
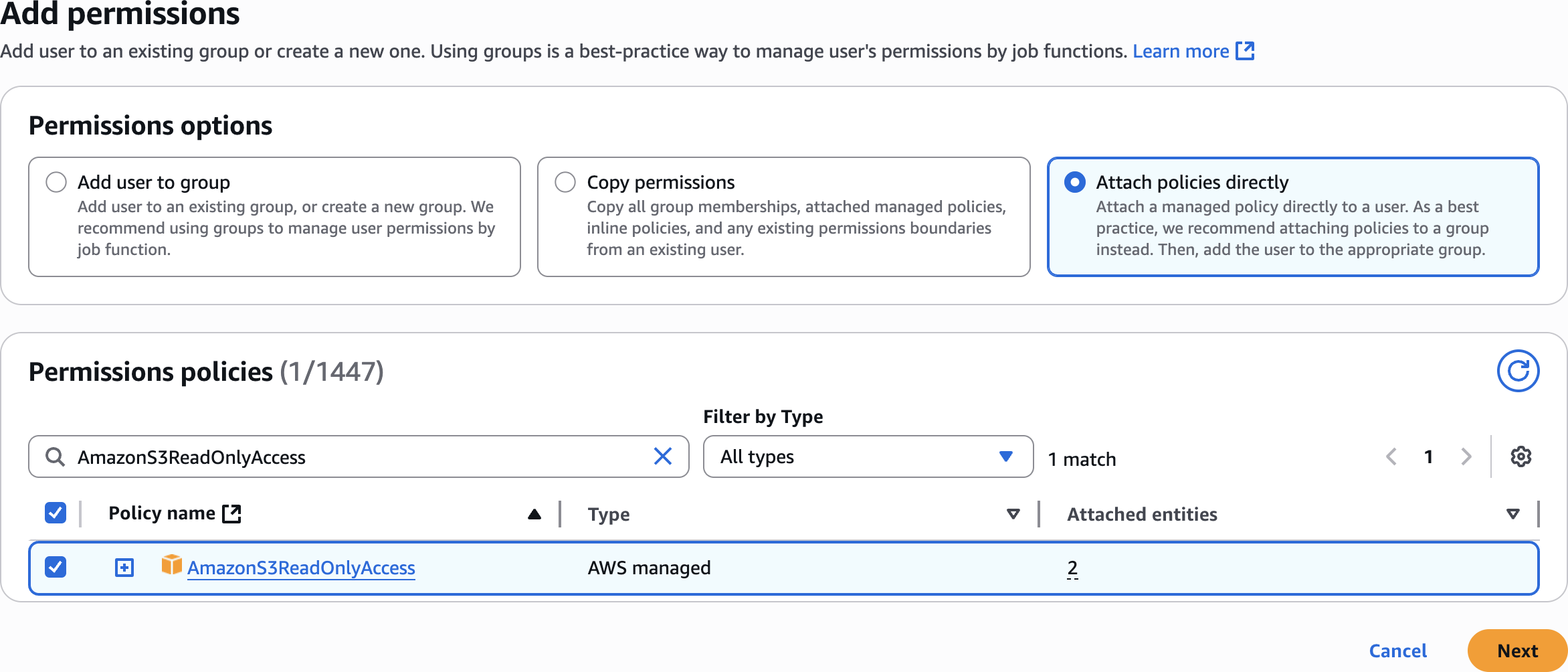
AmazonS3ReadOnlyAccessAdd permissions
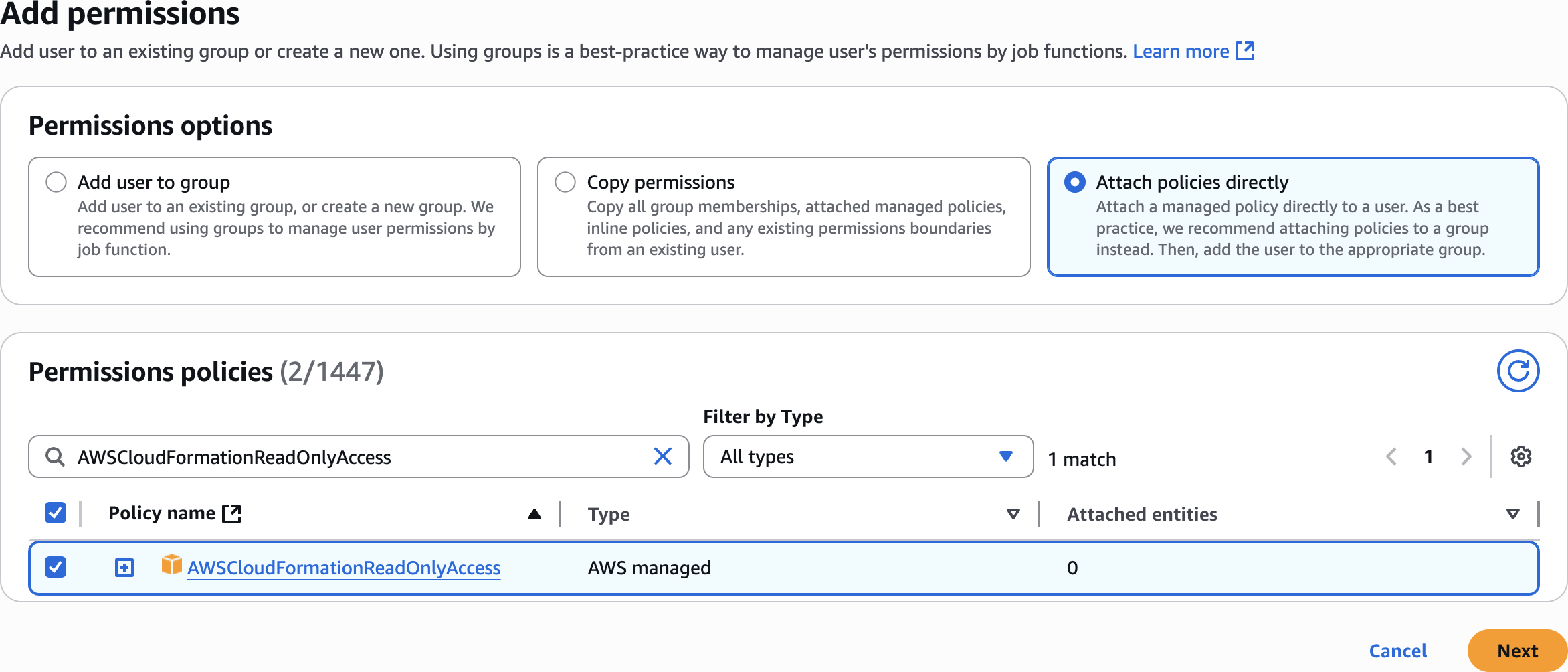
AWSCloudFormationReadOnlyAccessAdd permissions
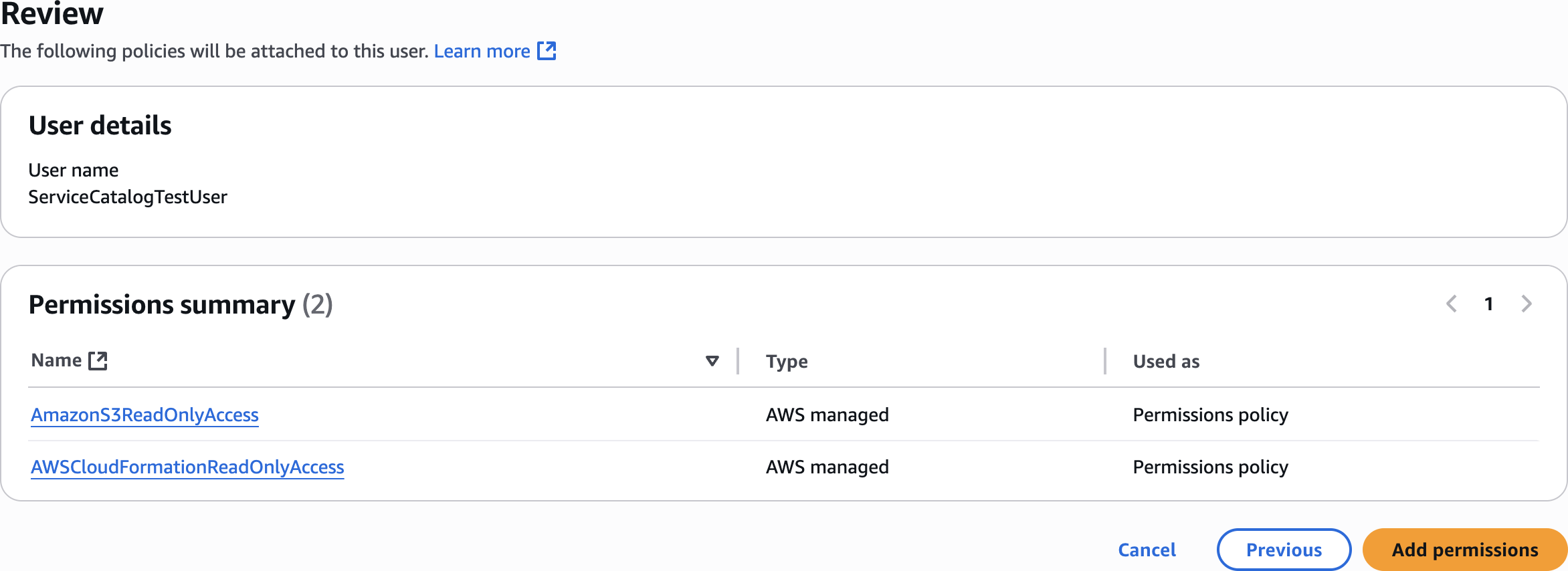
Review
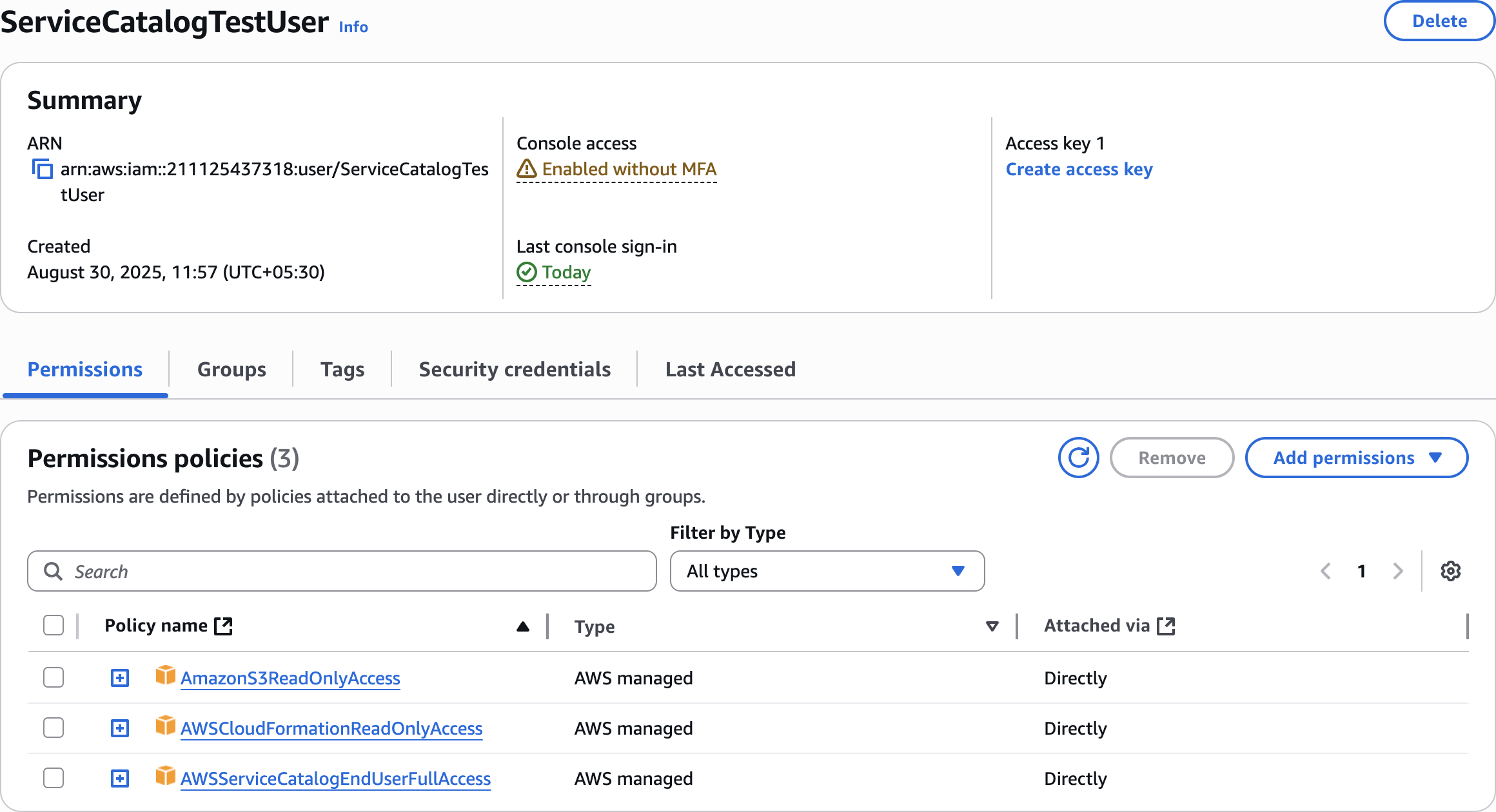
ServiceCatalog TestUser
Grant Portfolio Access to the IAM User
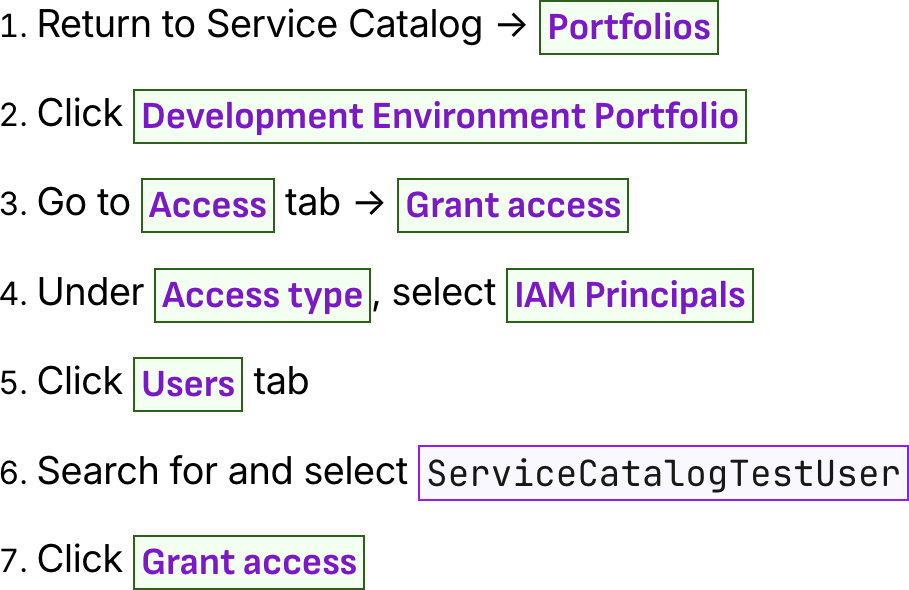
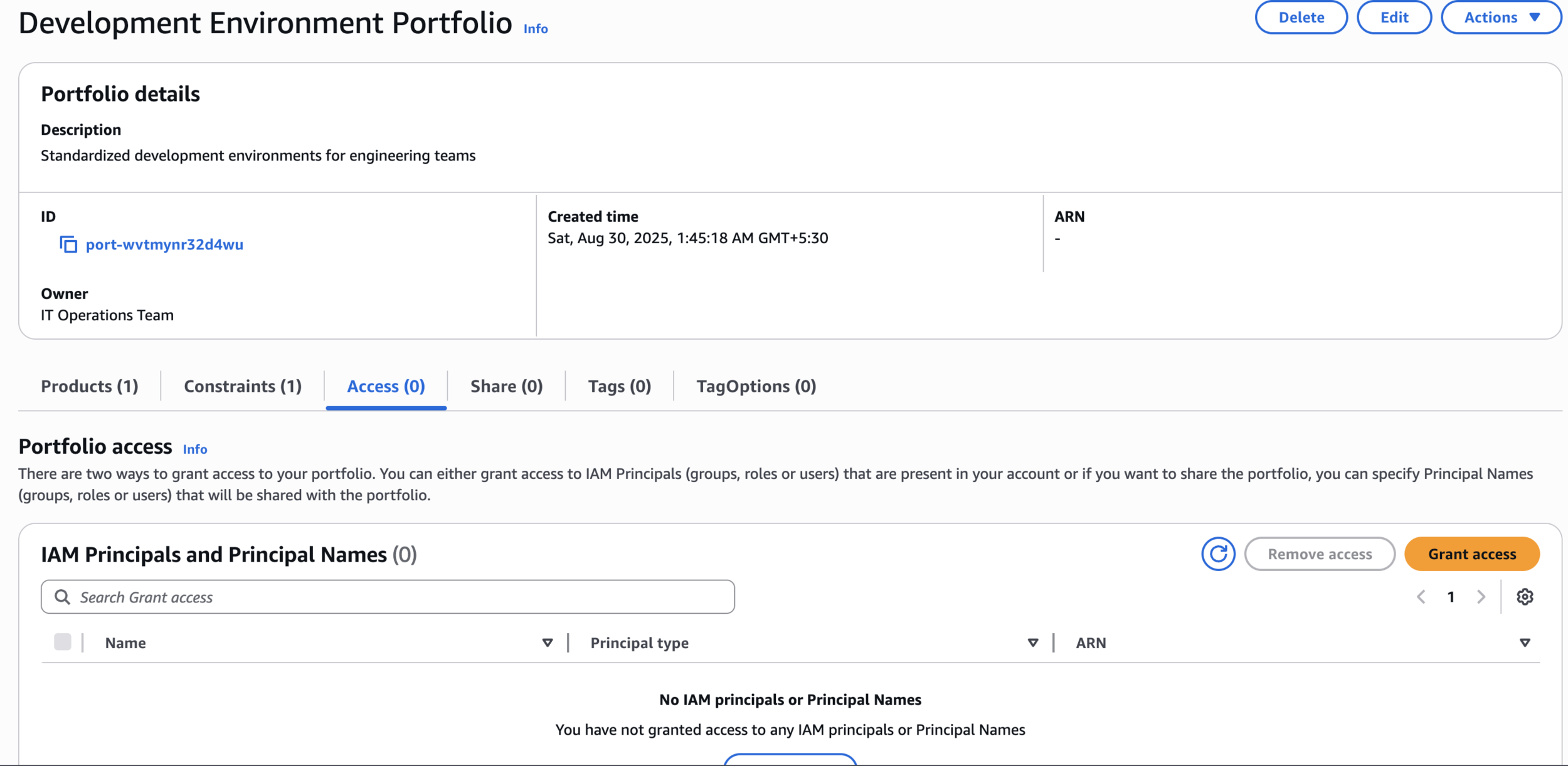
Development Environment Portfolio
Add users
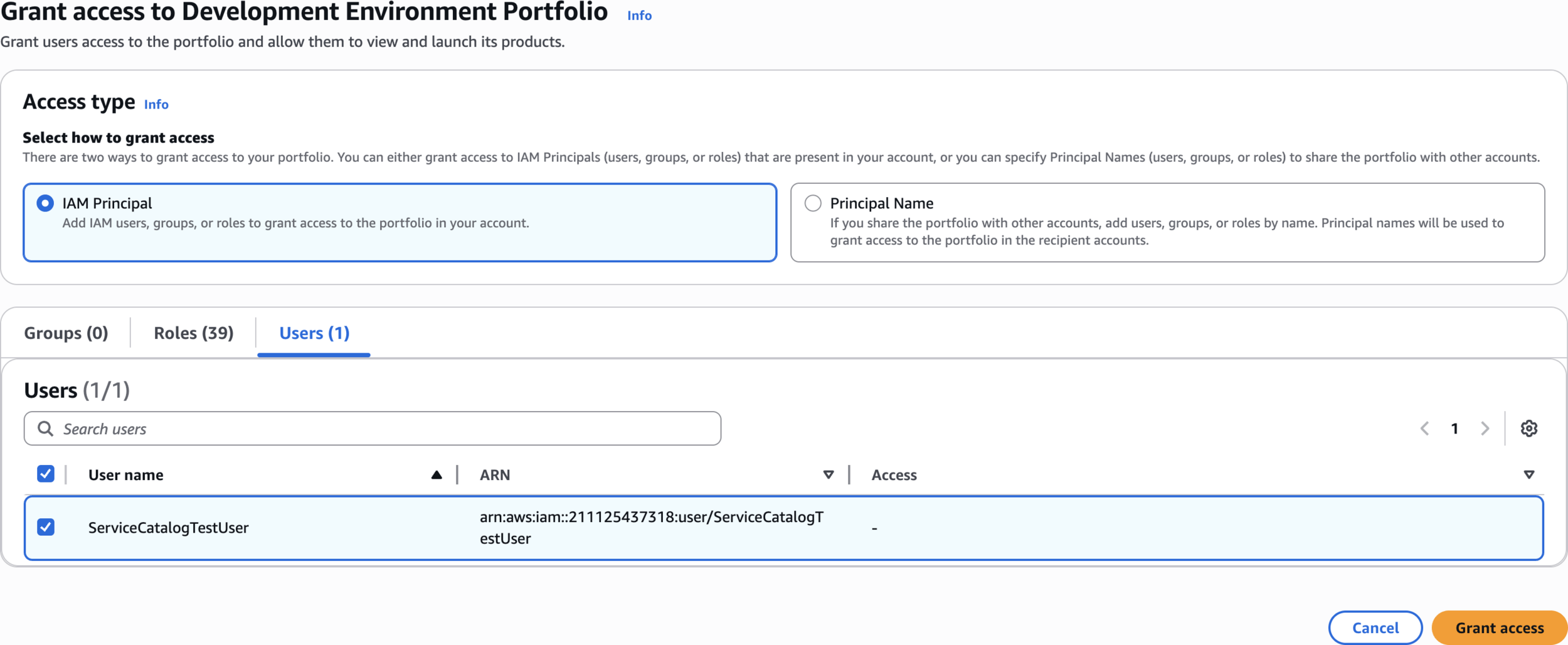
Grant access
Step 7: Create EC2 Key Pair
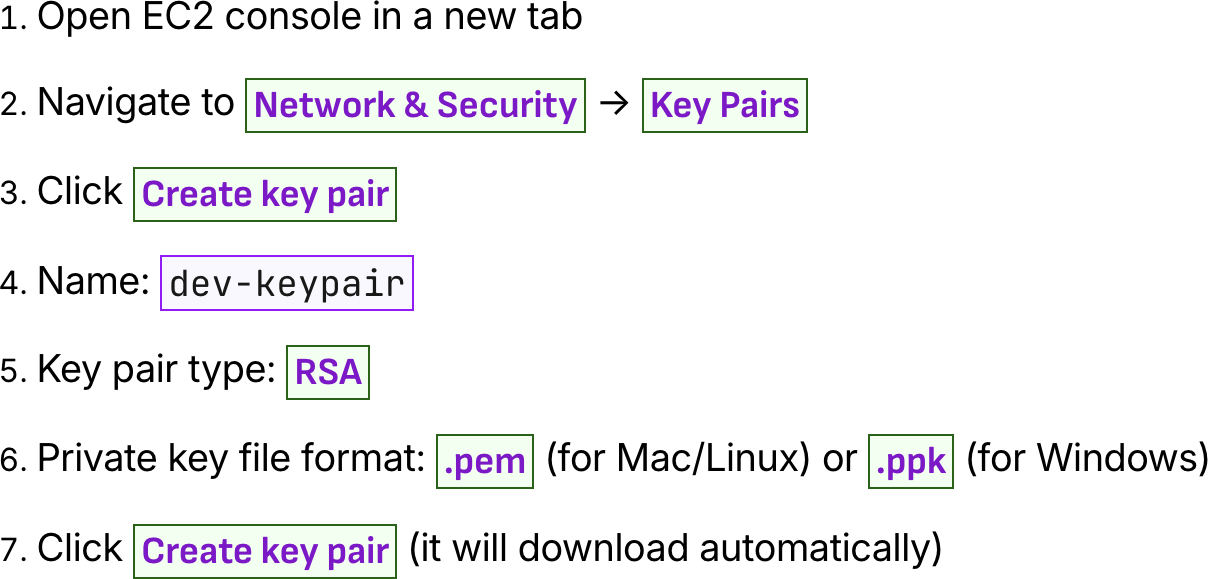
Key pairs


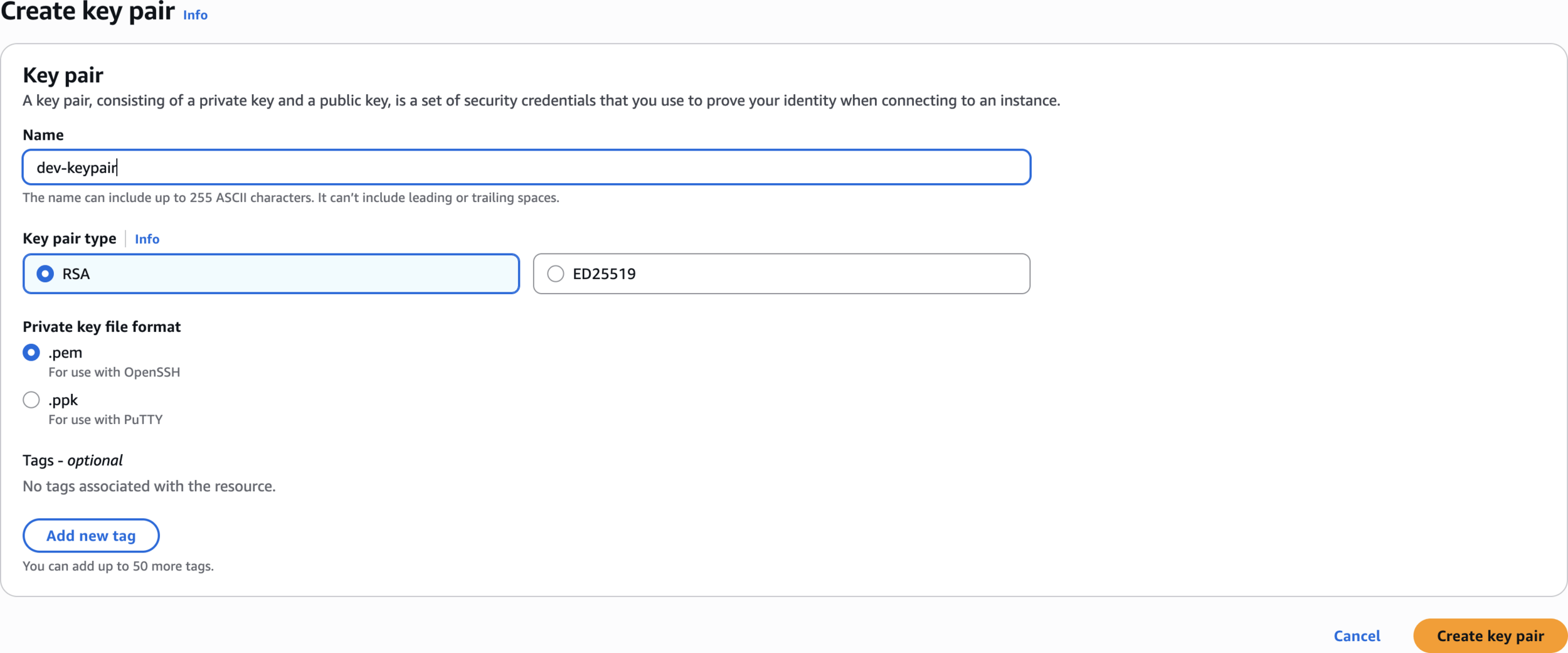
dev-keypairCreate key pair
Step 8: Test Product Provisioning as End User
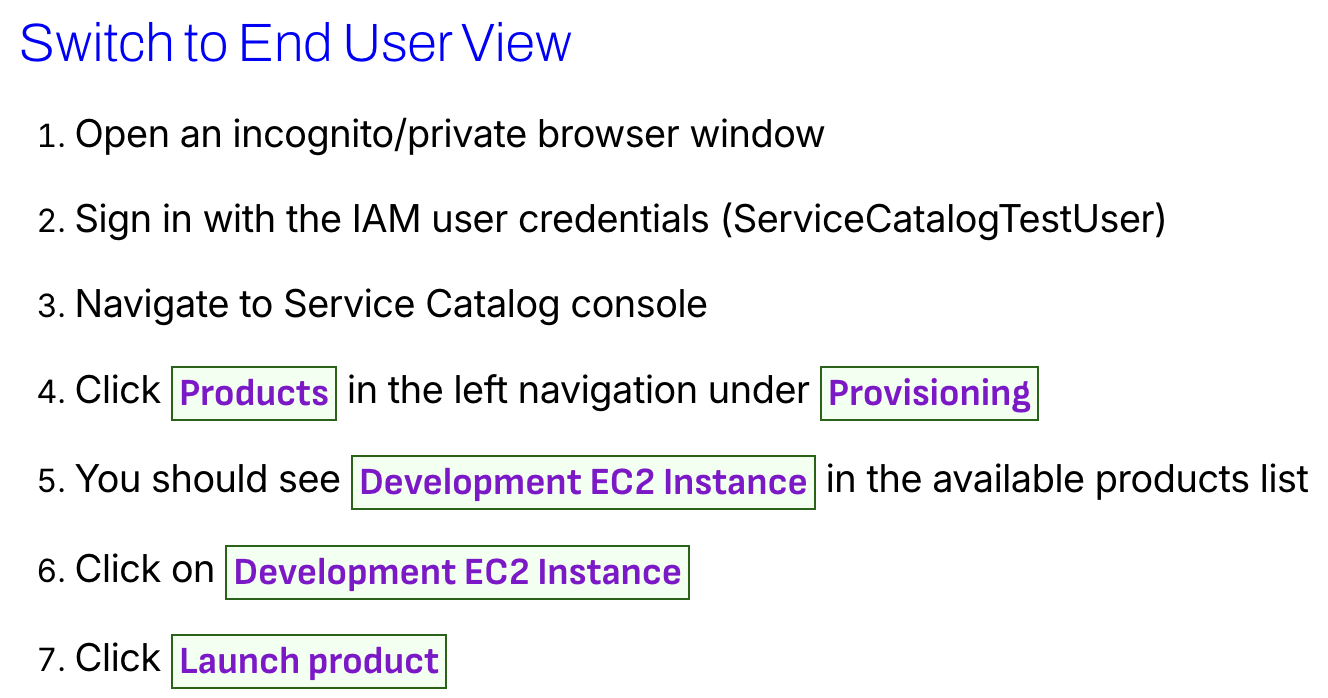
Login as End User
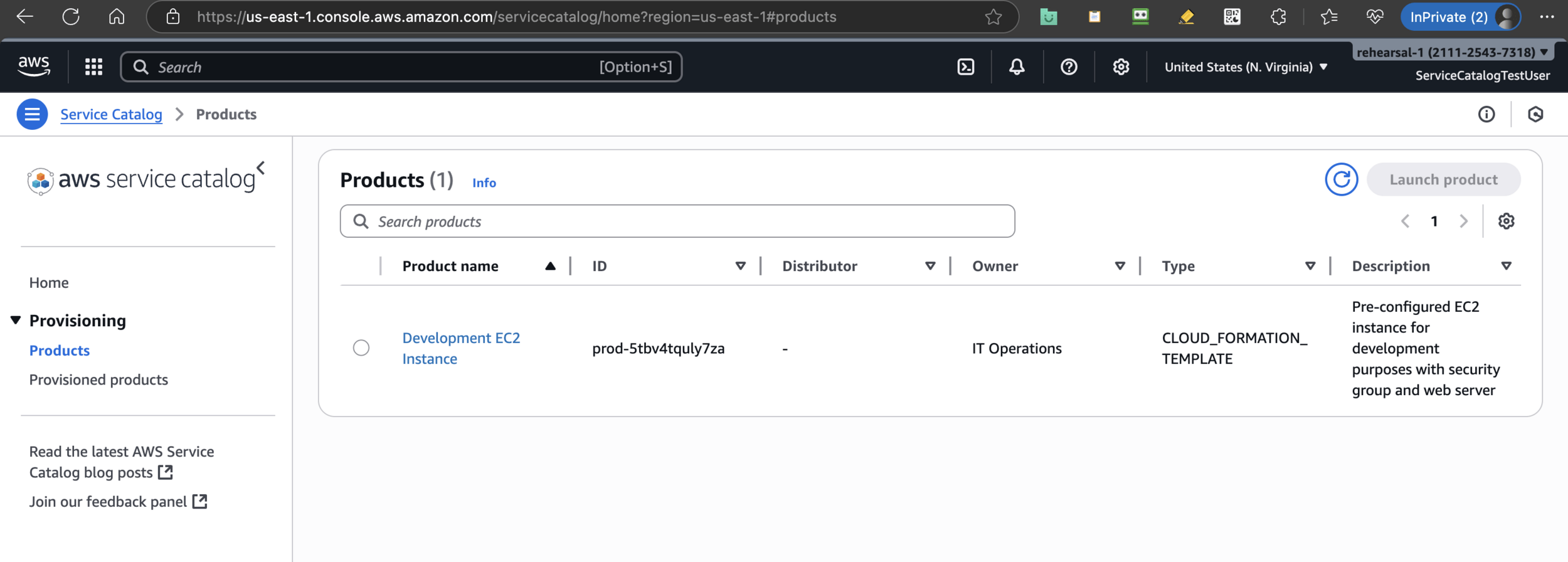
Go to Service Catalog
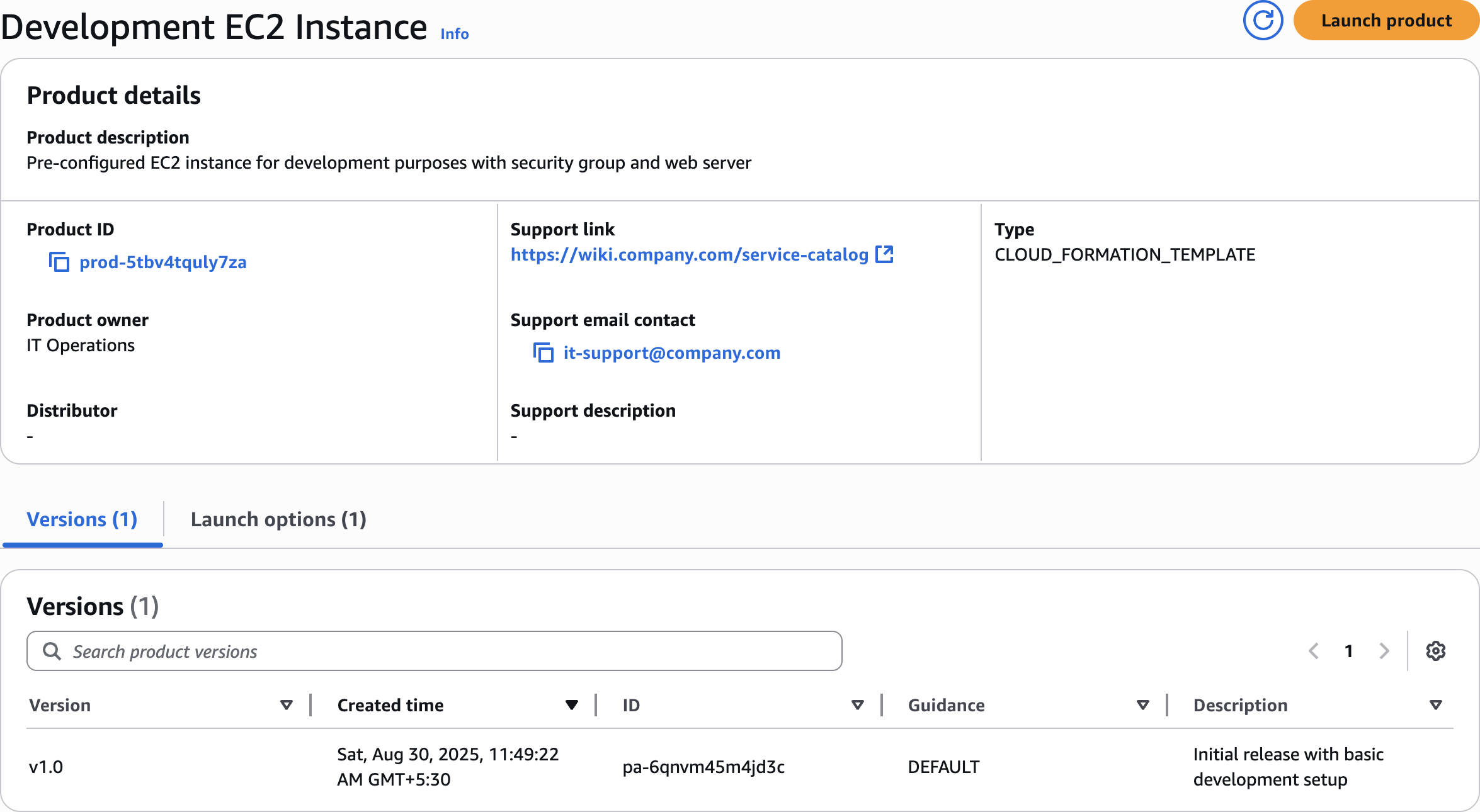
Launch product
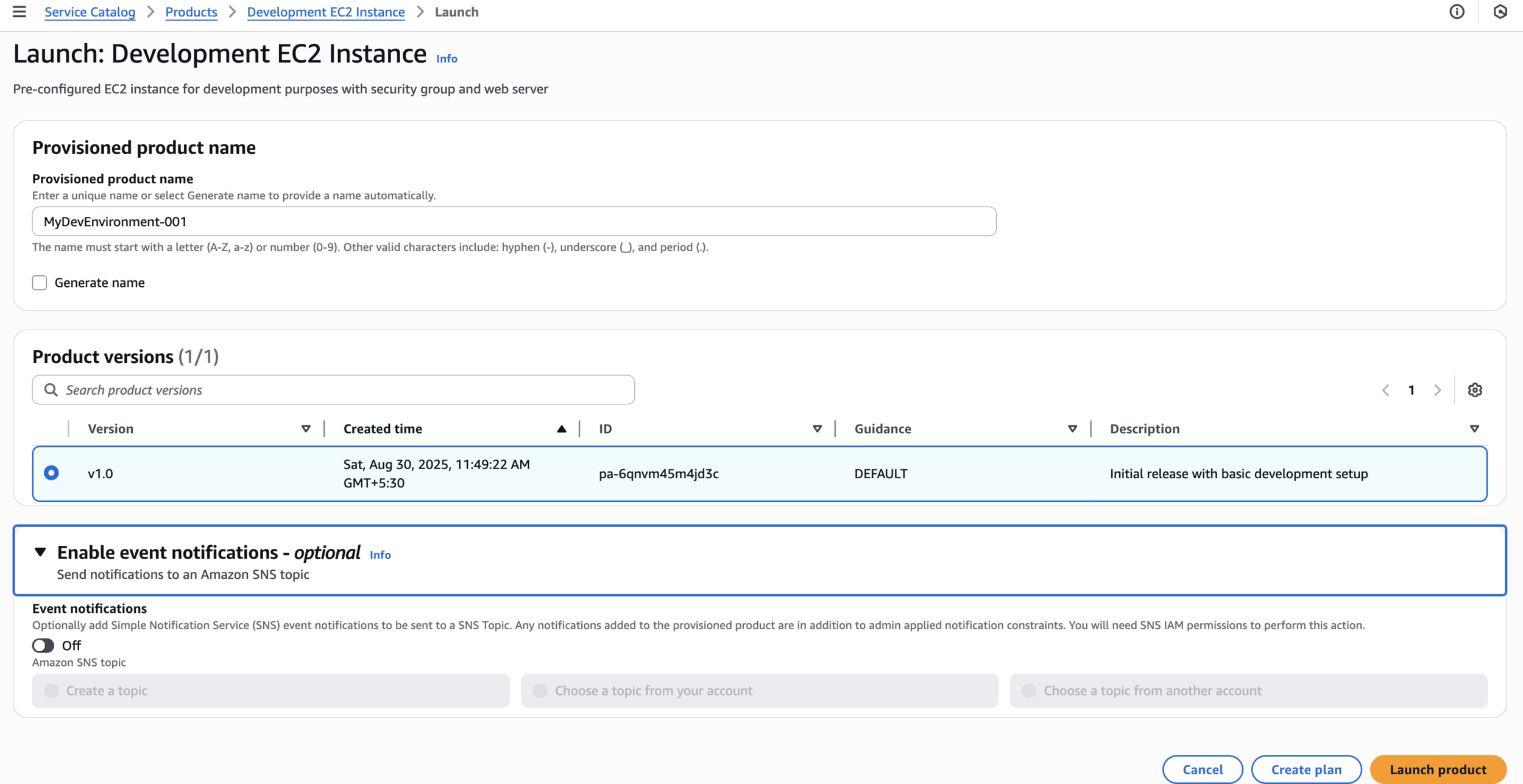
MyDevEnvironment-001Launch product
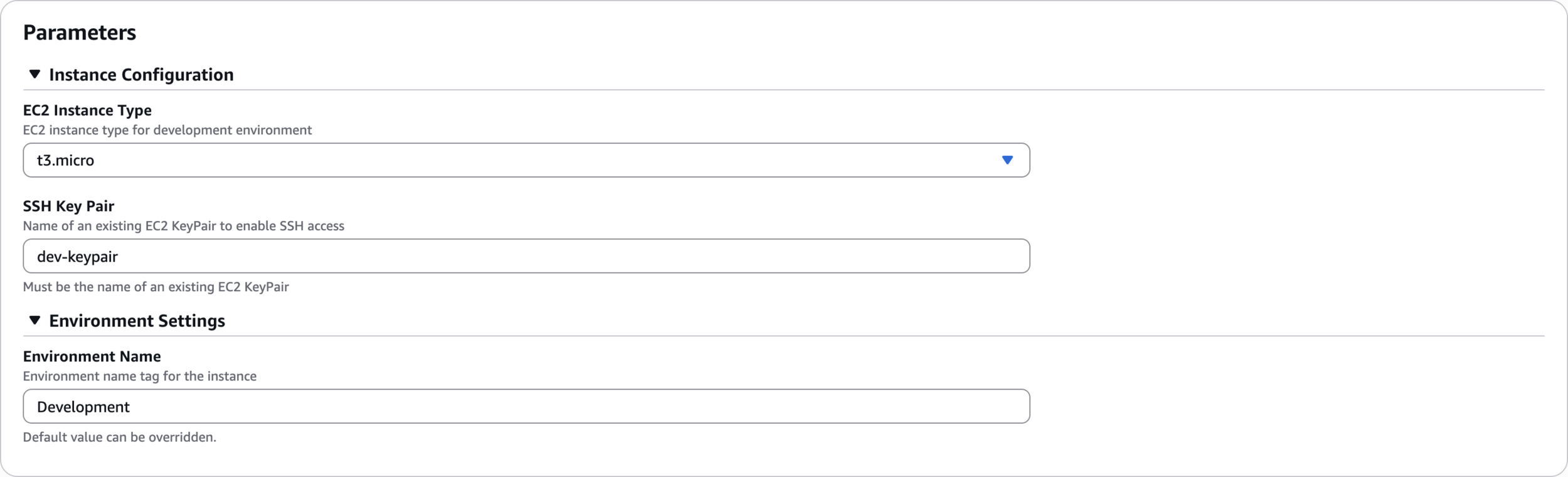
Fill Parameters
dev-keypair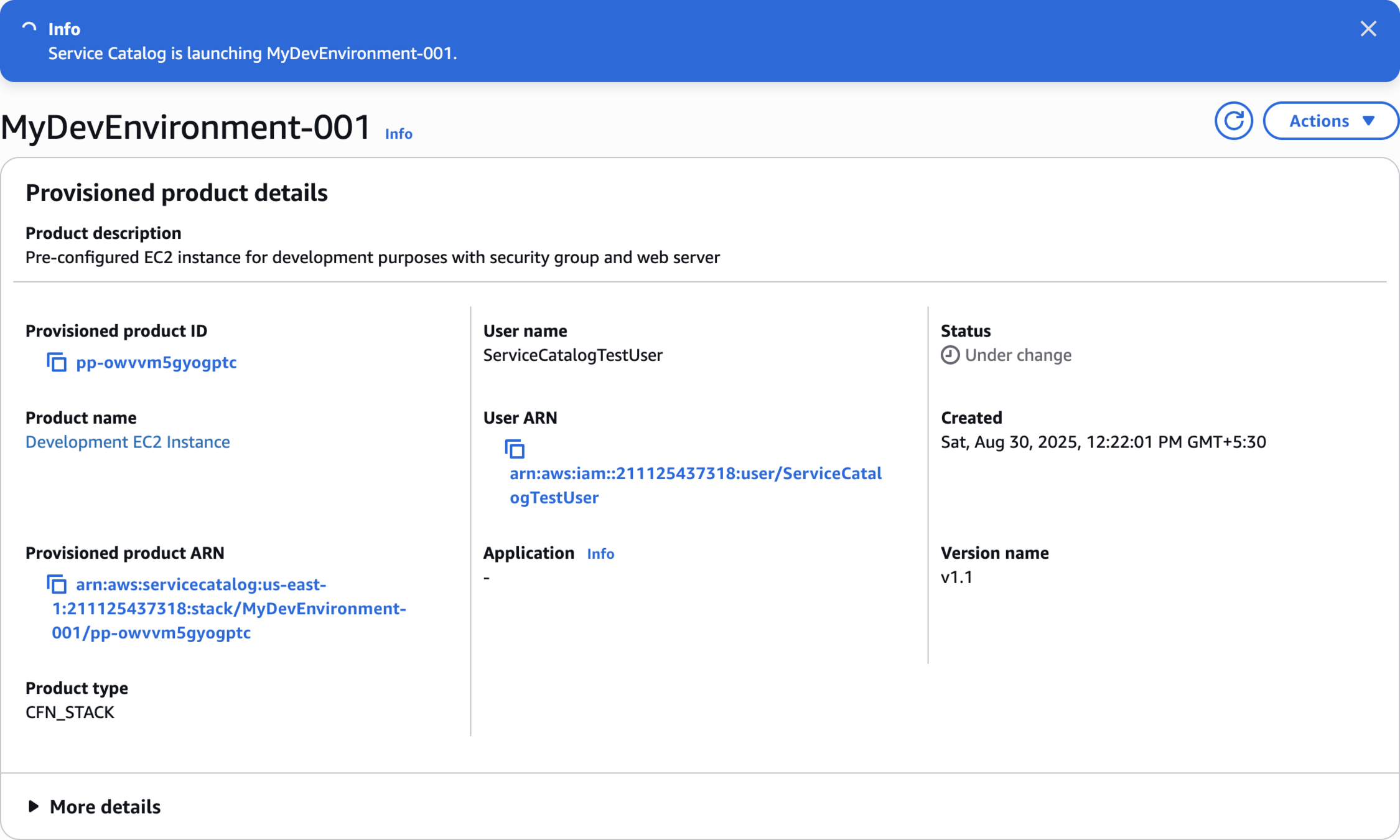
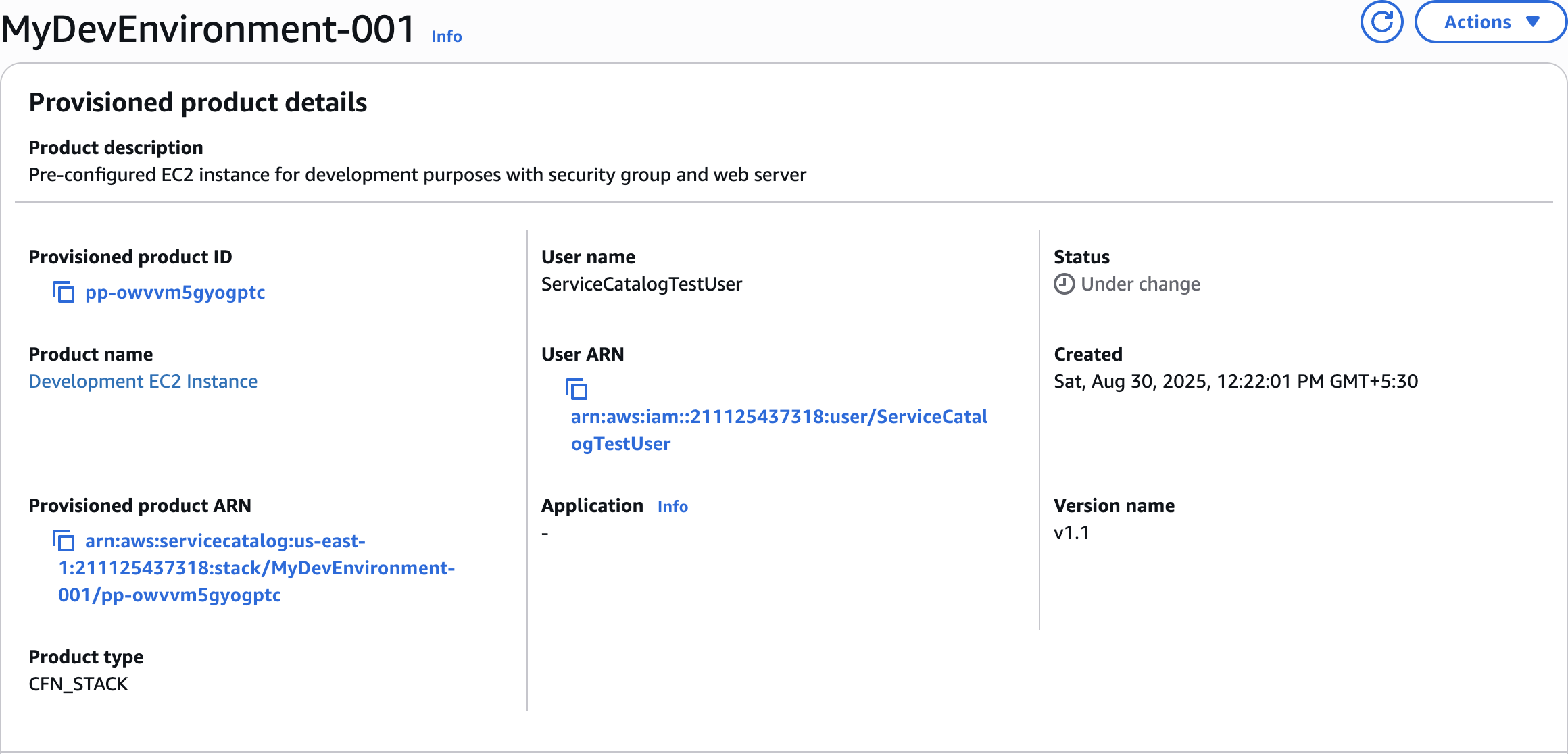
Status • Under change
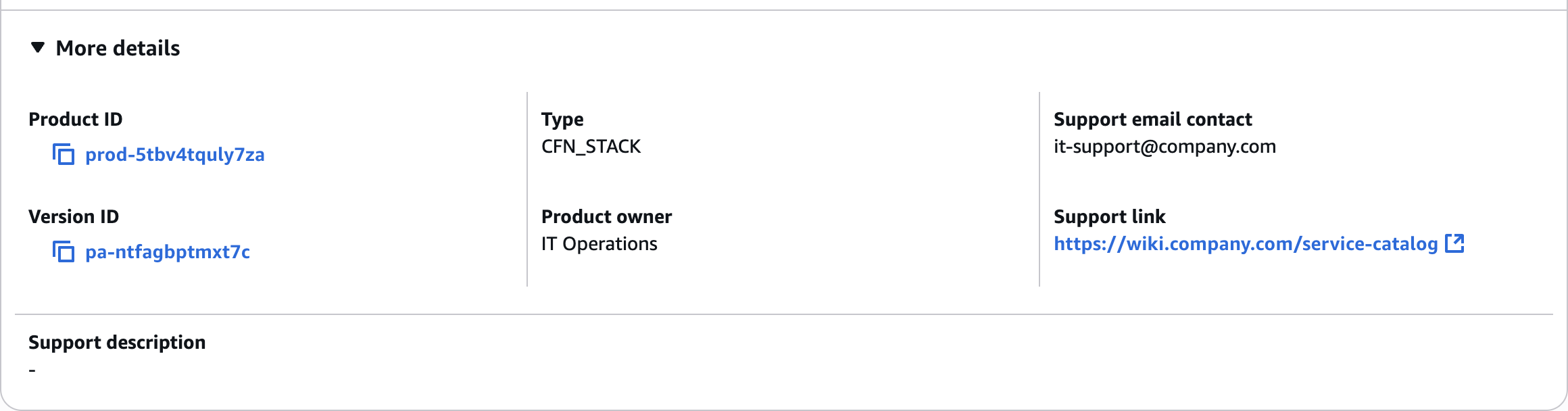
More details
Resources (2)
Events (1)
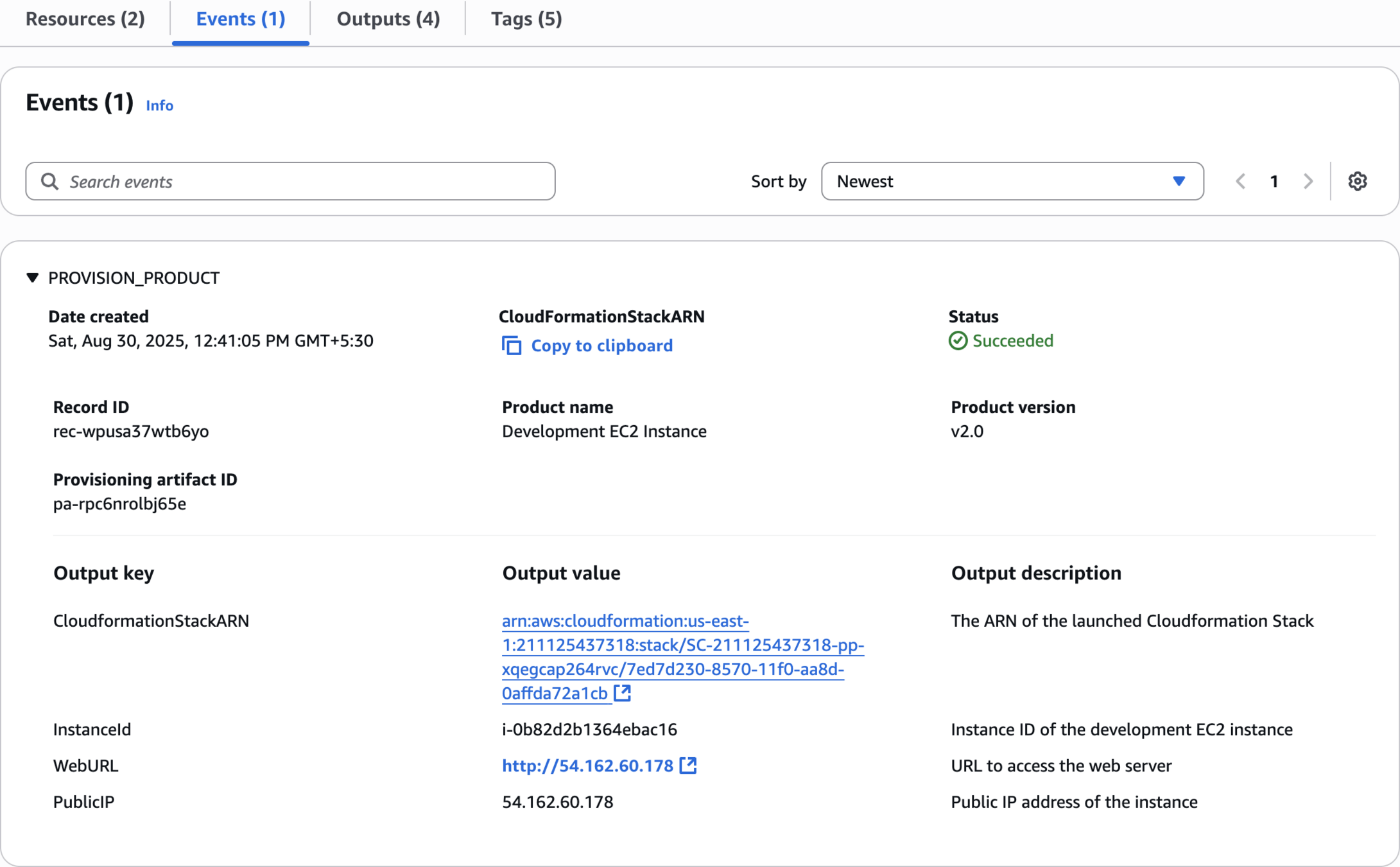
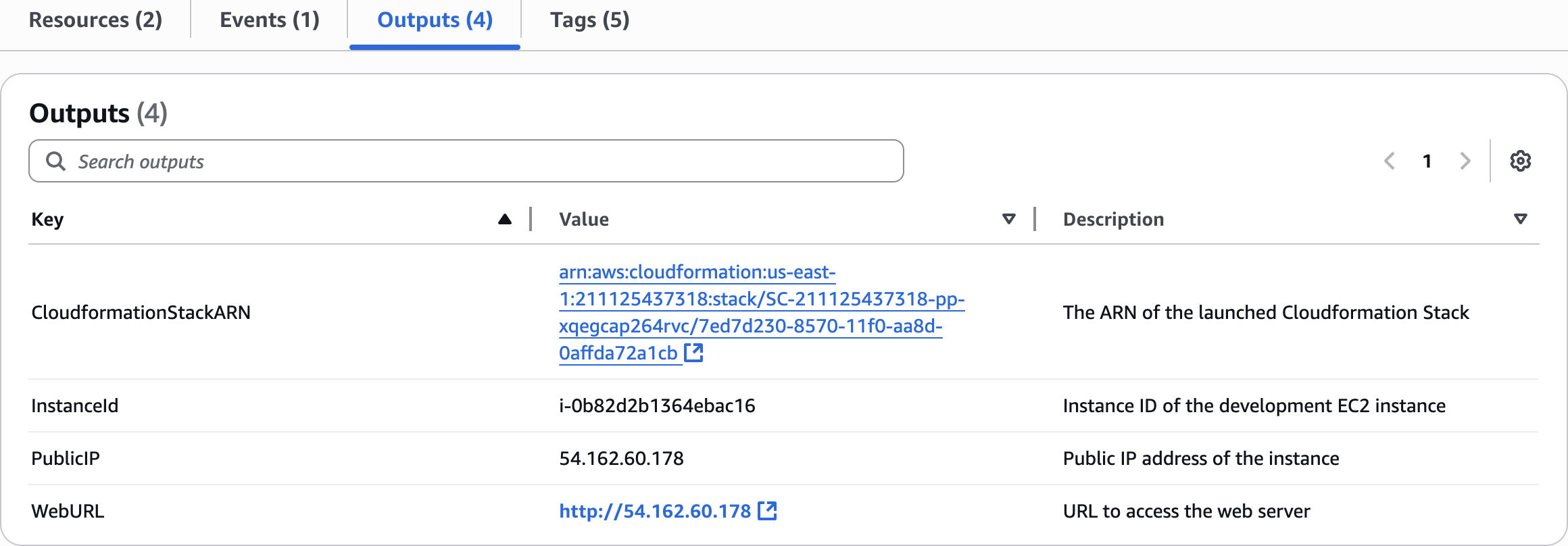
Outputs (4)
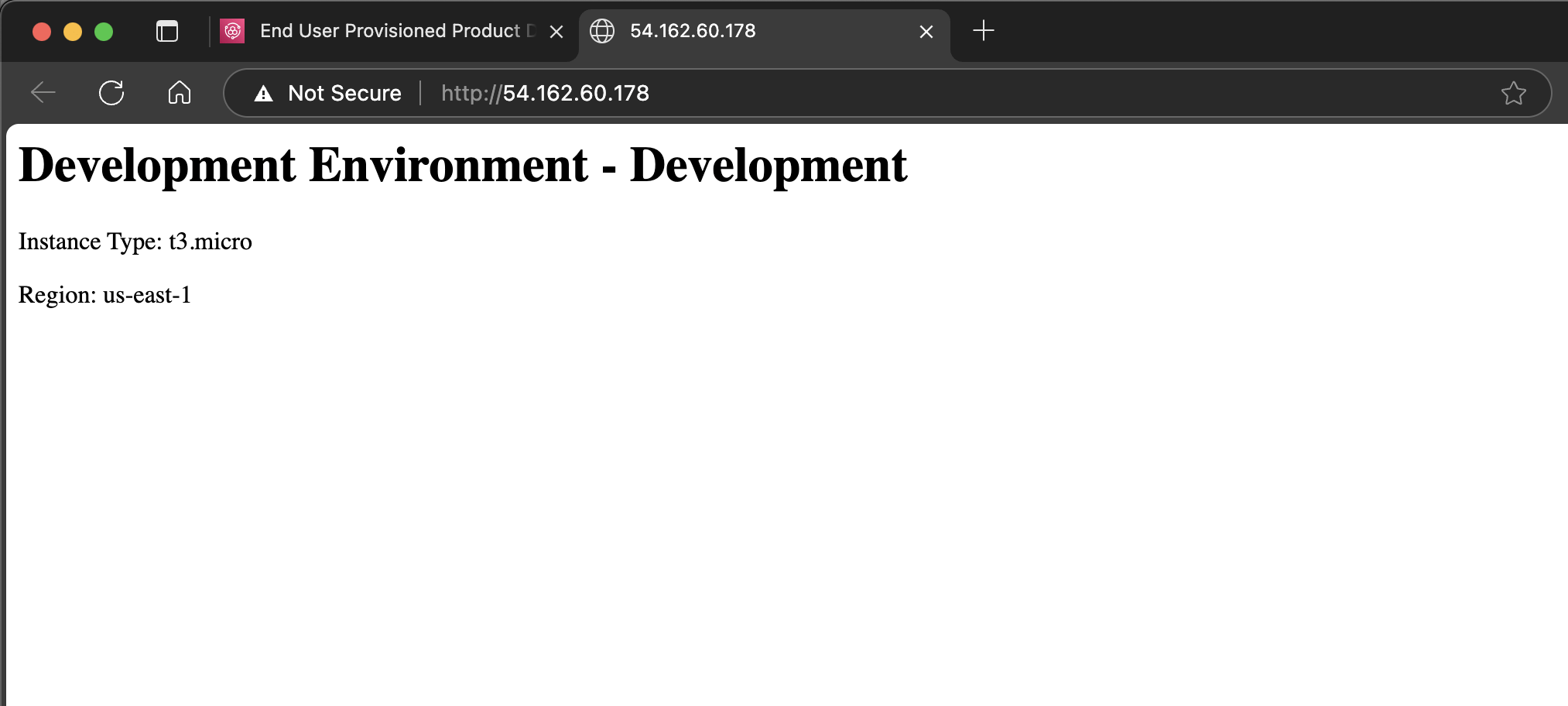
Clean Up
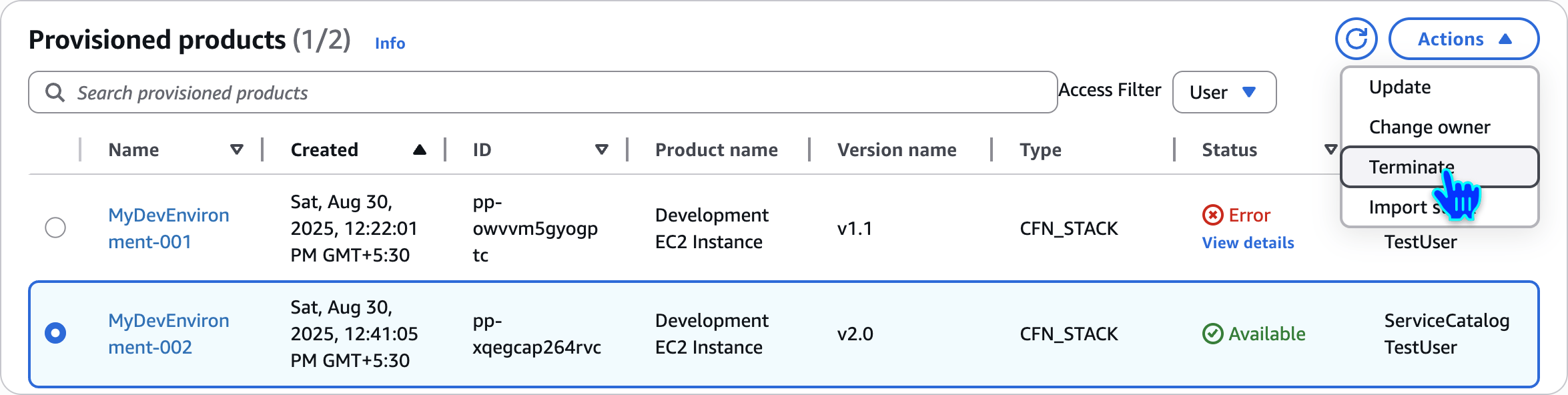
Terminate Provisioned Products
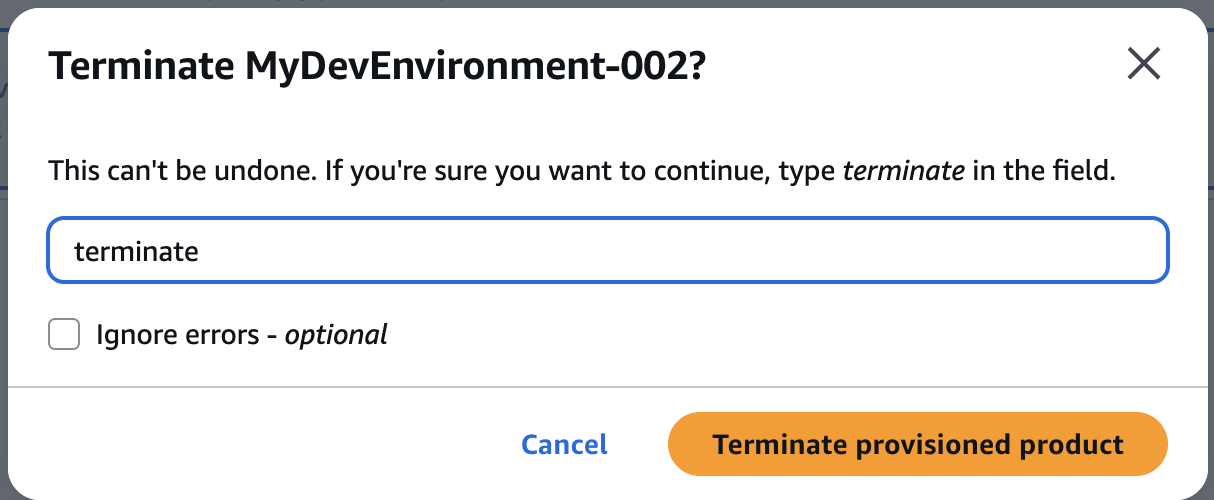
Terminate MyDevEnvironment
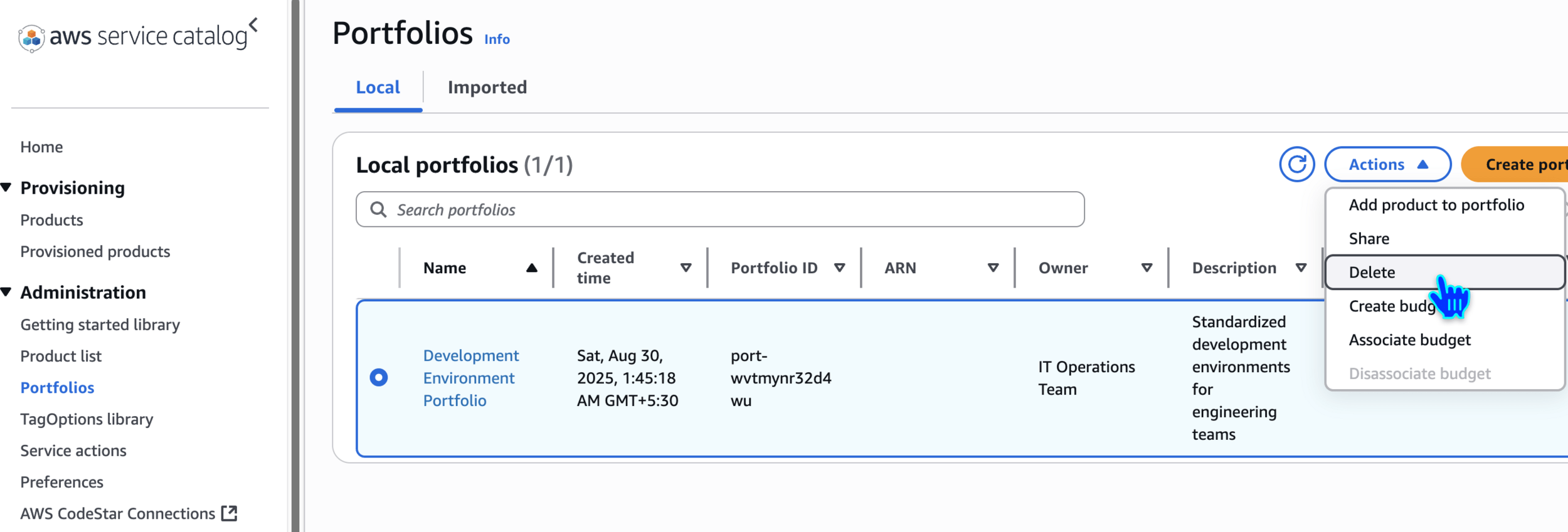
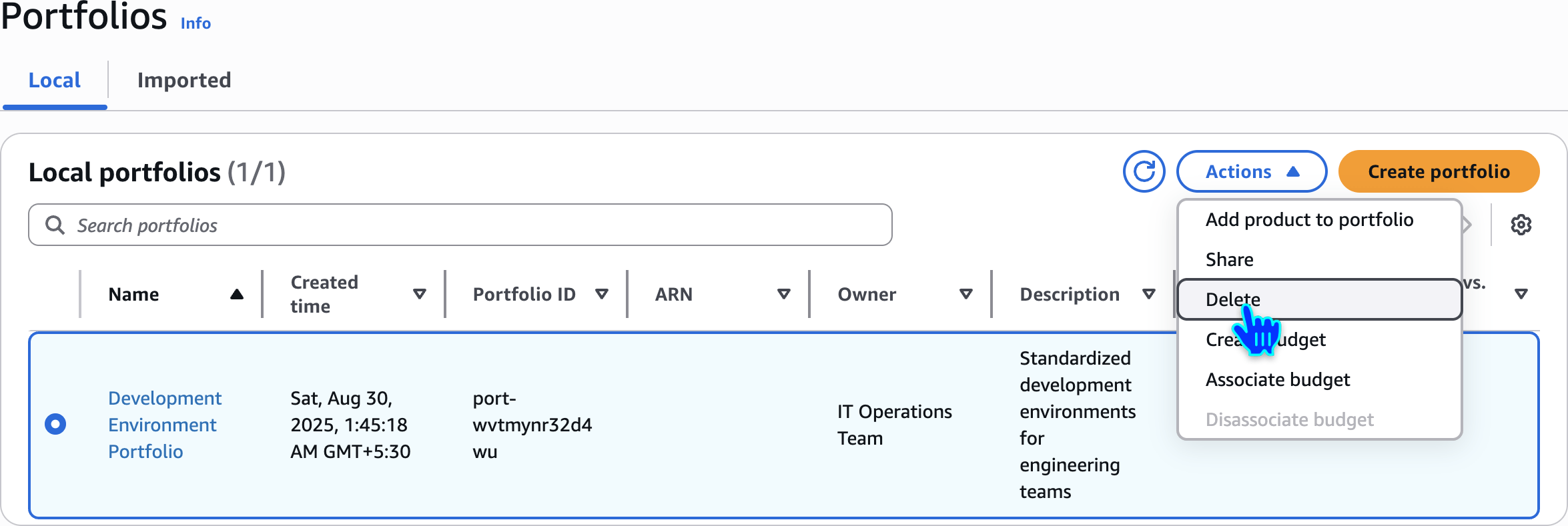
Delete Portfolios
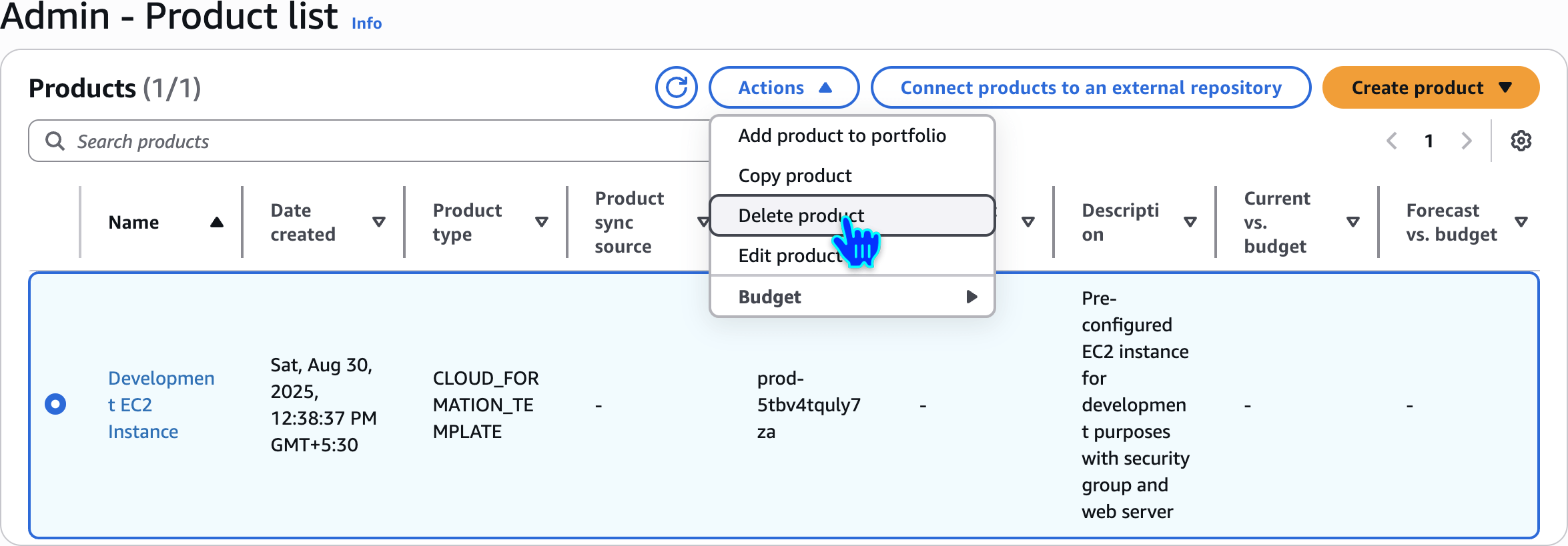
Delete Product
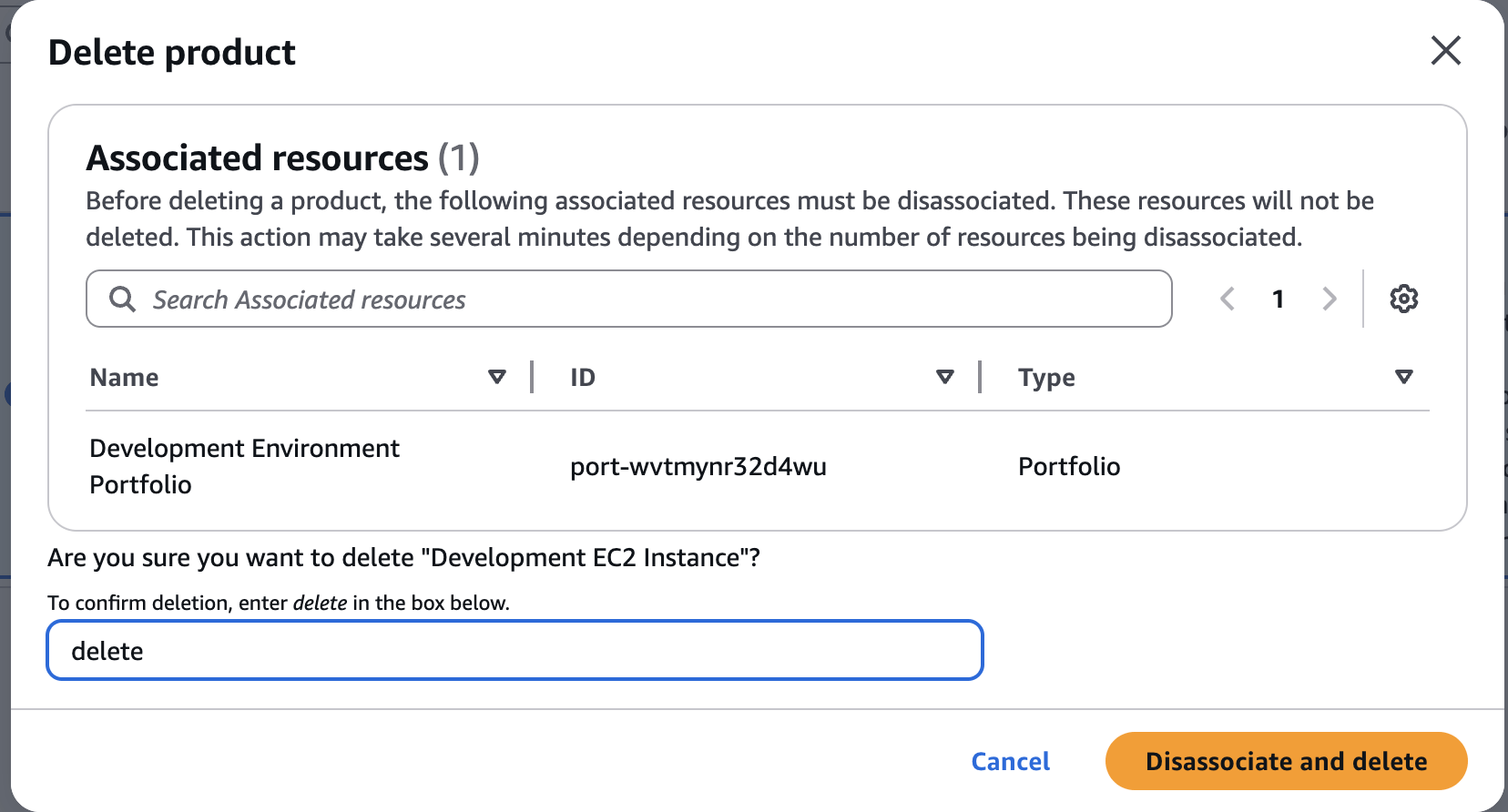
delete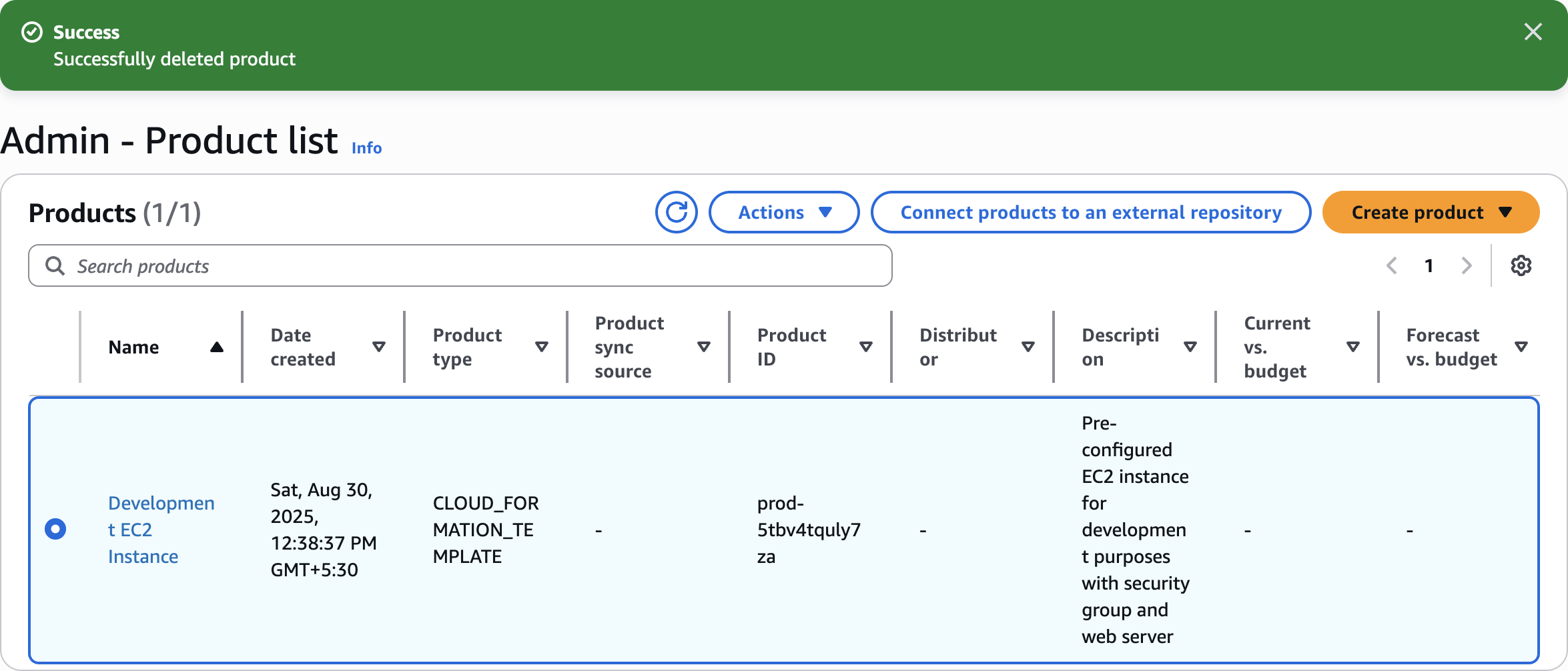
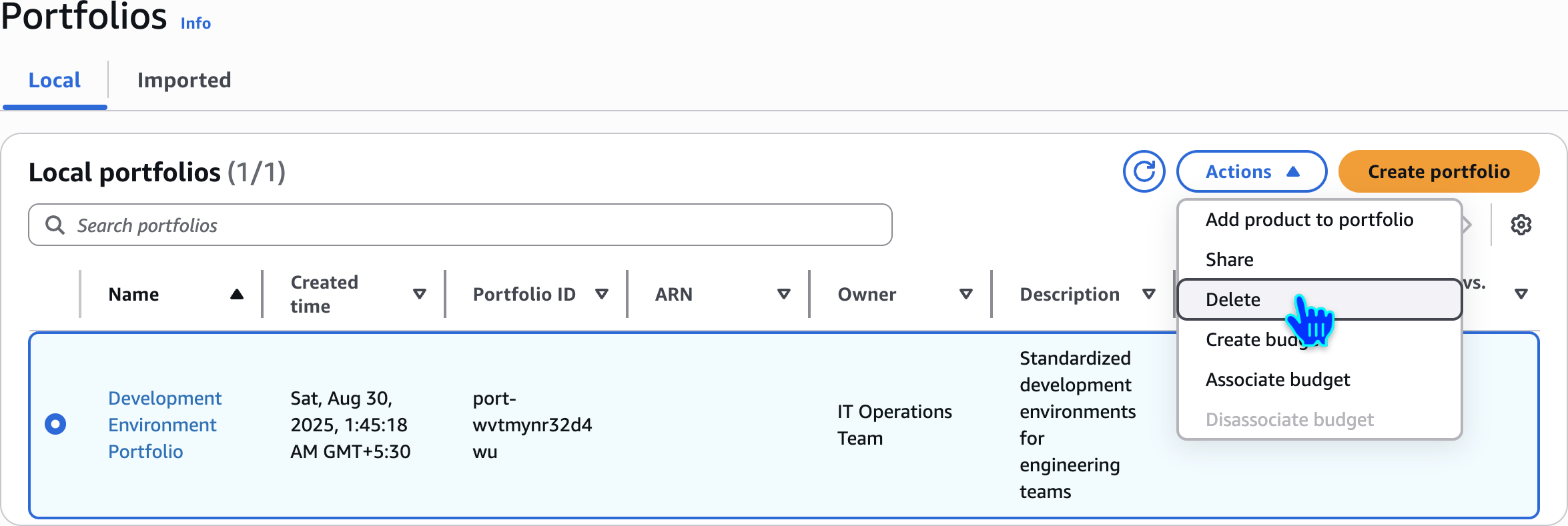
Delete Portfolios
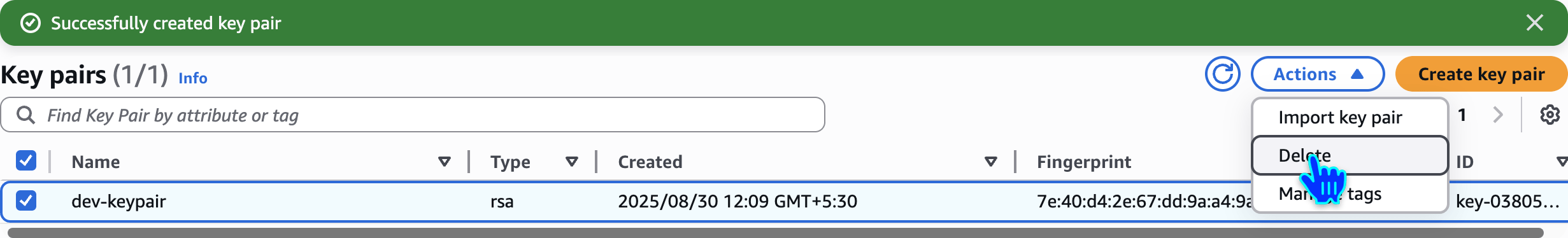
Delete Key Pair
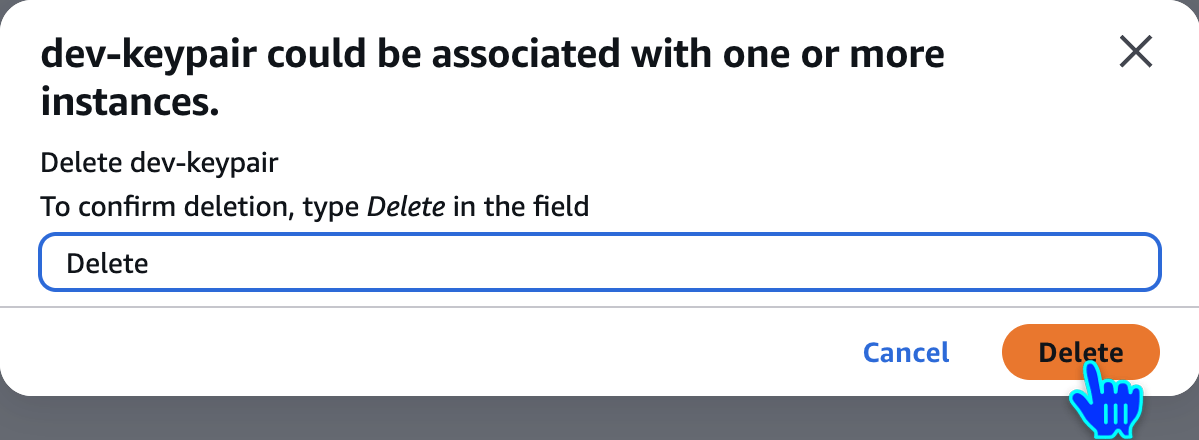
Delete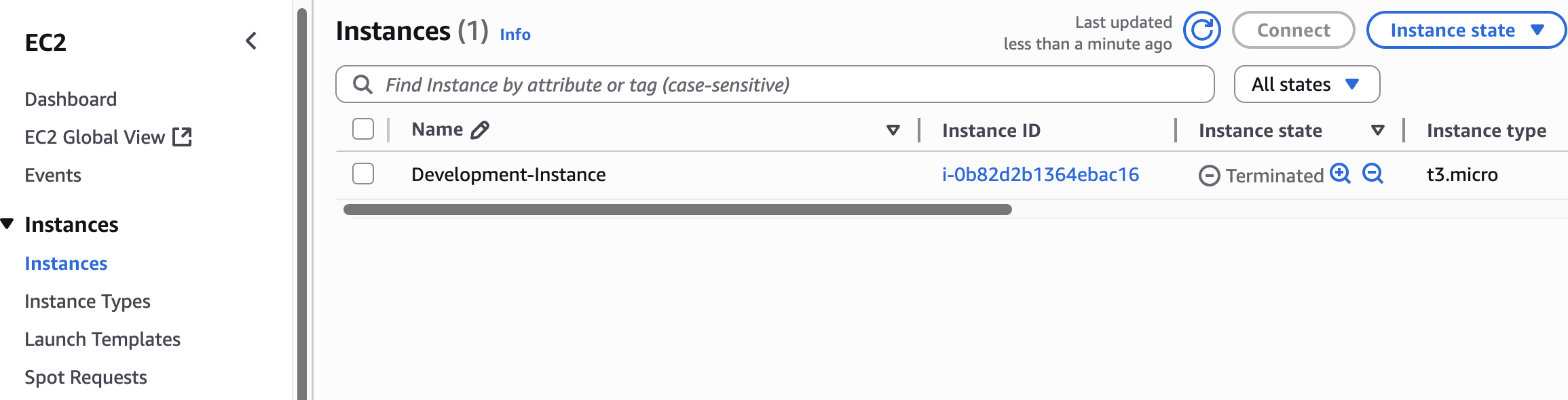
Check EC2 Instances
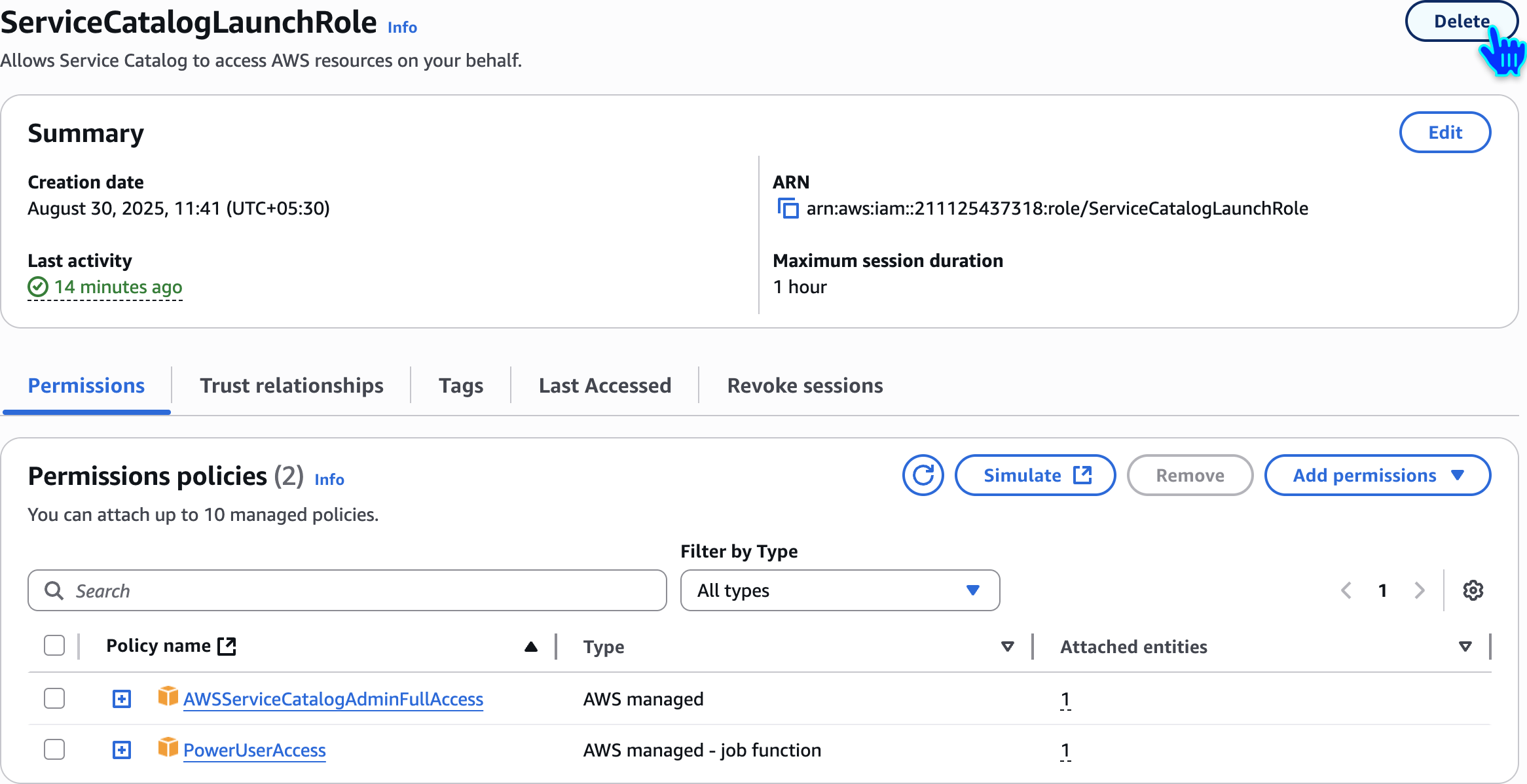
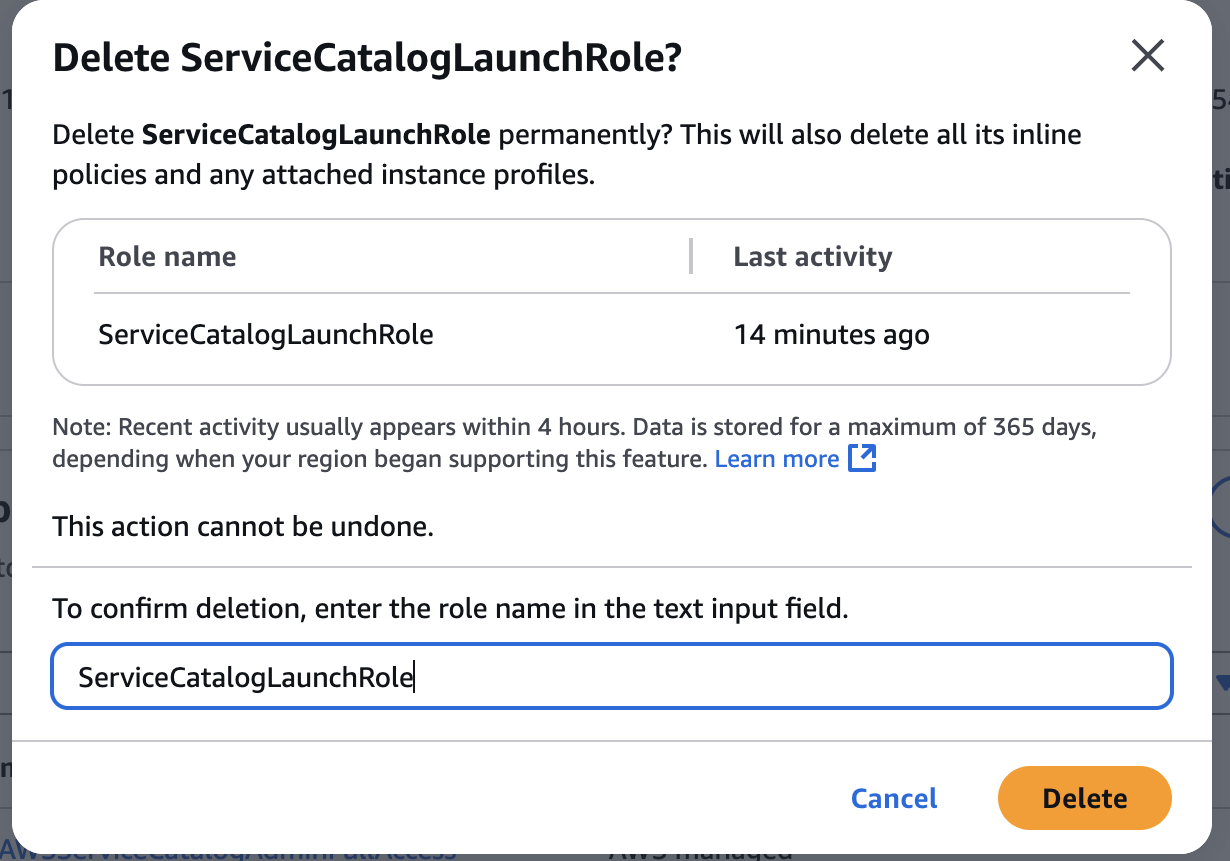
Delete IAM Role
Delete IAM User
🙏
Thanks
for
Watching
AWS Service Catalog - Hands-On Demo
By Deepak Dubey
AWS Service Catalog - Hands-On Demo
AWS Service Catalog - Hands-On Demo
- 306



