SUMMON
SECRETS AND SOURCE CONTROL
Dustin Collins
Developer Advocate @ Conjur
Organizer @ Boston DevOps meetup

secrets IN source control
+ simple
+ changes are tracked
- weak access control
- rotation requires commit + deploy
- cannot open-source
secrets NOT IN source control
+ better access control
+ can open-source
- implicit dependencies
- rotation requires coordination
- need a separate system for secrets storage
secrets ENCRYPTED in source control
+ secrets tracked in source
+ decryption key access can be managed
- decryption key access is hard to manage (least privilege)
- encrypted secrets are a 'black box' that can break your apps
secrets REFERENCED by source control
+ secrets tracked in source
+ swappable providers
+ access pattern is same regardless of environment
- may not work with older tooling that doesn't accept config through environment
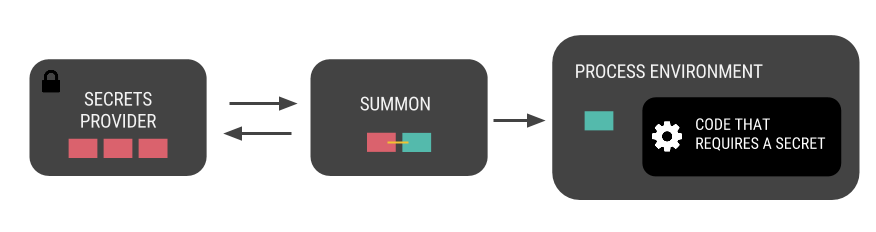
SUMMON
A command-line tool that resolves referenced secrets as environment variables into any process
AWS_ACCESS_KEY_ID: !var aws/$environment/access_key_id
AWS_SECRET_ACCESS_KEY: !var aws/$environment/secret_access_key
AWS_REGION: us-east-1
SSL_CERT: !var:file ssl/certs/private
secrets.yml
secrets by reference
providers
given a path to a secret, return its value
simple contract
1. return secret's value to stdout
2. return any error to stderr
can be written in any language
providers
available
- Conjur
- AWS S3
- OSX/Linux keyring
- Chef data bag
TODO
- Hiera
- HashiCorp Vault
- KeyWhiz
- you decide
CLI
written in Go, distributed as a single binary
NAME:
summon - Parse secrets.yml and export environment variables
USAGE:
summon [global options] command [command options] [arguments...]
VERSION:
0.4.0
COMMANDS:
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
-p, --provider Path to provider for fetching secrets
-f "secrets.yml" Path to secrets.yml
-D [-D option -D option] var=value causes substitution of value to $var
--yaml secrets.yml as a literal string
--ignore, -i Ignore unresolvable keys
--help, -h show help
--version, -v print the version
process
any tool that accepts environment variables can be used with Summon
once the process exits, the secrets are gone
Docker
$ summon -D 'env=dev' docker run -d --name myrabbit \
--env-file @SUMMONENVFILE \
rabbitmq:3-management
RABBITMQ_DEFAULT_USER: admin
RABBITMQ_DEFAULT_PASS: !var rabbitmq/$env/mgmt-password
secrets.yml
Chef
$ summon chef-client --once
user 'maintenance' do
password ENV['MAINTENANCE_PASSWORD']
end
recipe
MAINTENANCE_PASSWORD: !var ops/maintenance/password
secrets.yml
test-kitchen
$ summon test-kitchen converge
driver:
name: ec2
aws_ssh_key_id: <%= ENV['AWS_KEYPAIR_NAME'] %>
transport:
forward_agent: true
ssh_key: <%= ENV['SSH_PRIVATE_KEY_PATH'] %>
.kitchen.yml
AWS_KEYPAIR_NAME: cijenkins SSH_PRIVATE_KEY_PATH: !var:file aws/cijenkins/private-key
secrets.yml
PostgreSQL
$ summon -D 'dbname=reports' psql -d reports -u budgeting
PGPASSWORD: !var databases/$dbname/password
secrets.yml
Terraform
$ summon terraform apply
variable "access_key" {}
variable "secret_key" {}
variables.tf
TF_VAR_access_key: !var aws/dev/sys_powerful/access_key_id
TF_VAR_secret_key: !var aws/dev/sys_powerful/secret_access_key
secrets.yml
Ansible
$ summon -D 'user=jenkins' ansible-playbook jenkins.yml
ANSIBLE_PRIVATE_KEY_FILE: !var:file ssh/$user/private-key
secrets.yml
Summon does not solve authn/authz
This is up to the provider implementation
How to contribute
-
Use Summon, share your feedback
-
Write a new provider
-
Open PRs on Summon's core
Summon: Secrets and Source Control
By Dustin Collins
Summon: Secrets and Source Control
An overview of Summon, an open-source command line that makes working with secrets easier.
- 2,338


