Deploy Nodejs with Docker & CoreOS
Edwin Fuquen
edwin@somespider.com
@efuquen

- A tool to conveniently manage containers.
- Containers share the same kernel of the host, but have different filesystems.
- Like lightweight VMs.
- The power of docker is the creation of lightweight, consistent, and easily shareable environments for running applications.
Dockerfile
- Is a build scripts
- Each line is a layer
- Layers build on top of each other successively
- Similar to git commits
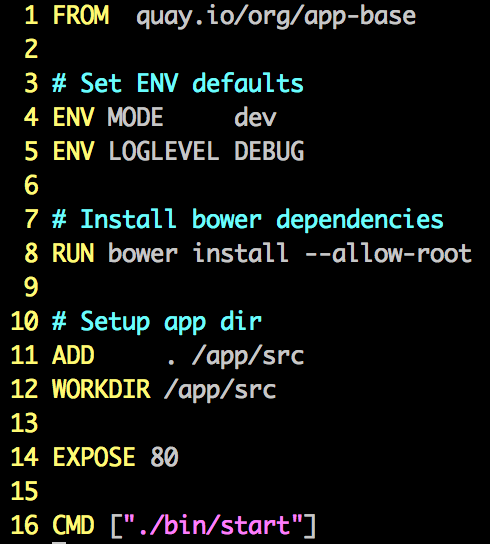
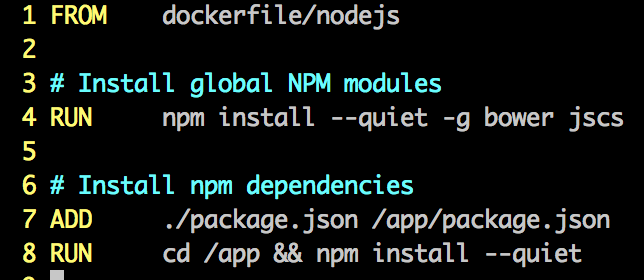
quay.io/org/app-base
quay.io/org/app
CoreOS

- Linux OS based on Chrome OS, which itself is based on Gentoo.
- There is no package manager, and only a few preinstalled tools.
- The most essential being docker, etcd, & fleetd.
- An OS fully built around managing containers in a distributed, fault tolerant cluster of machines.
- A distributed key/value store.
- Meant for config data, not high latency/throughput.
- Strongly consistent, very reliable.
- Think zookeeper replacement.
Fleetd
- Uses etcd to make a distributed init system.
- Essential runs systemd services on nodes.
- Feed in standard systemd unit files.
- But with some optional Fleet metadata.

Service Unit File
[Unit]
Description=registrator
Documentation=https://github.com/progrium/registrator
X-Image=progrium/registrator:master
[Service]
EnvironmentFile=/etc/environment
ExecStartPre=/usr/bin/docker pull progrium/registrator:master
ExecStart=/bin/sh -c "docker run \
--name %p.%i \
-v /var/run/docker.sock:/tmp/docker.sock \
progrium/registrator:master -ip $COREOS_PRIVATE_IPV4 \
etcd://$COREOS_PRIVATE_IPV4:4001/services"
ExecStop=/usr/bin/docker rm -f %p.%i
TimeoutStartSec=180s
TimeoutStopSec=30s
RestartSec=30s
Restart=on-failure
[X-Fleet]
X-Conflicts=%p@*.service
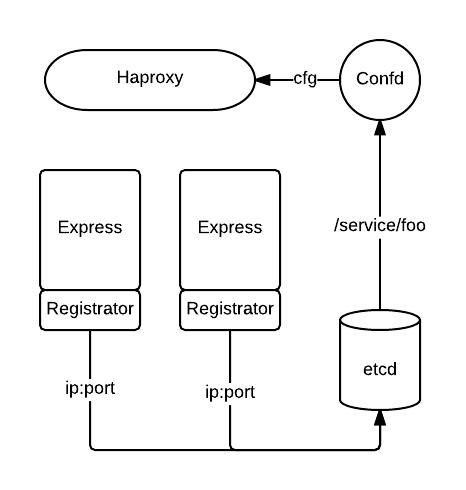
MachineMetadata=role=webService Discovery
- App ip & port are registered in etcd.
- confd gets notified when certain keys in etcd are modified
- Then haproxy.cfg templates get updated with added or removed app ip & port.
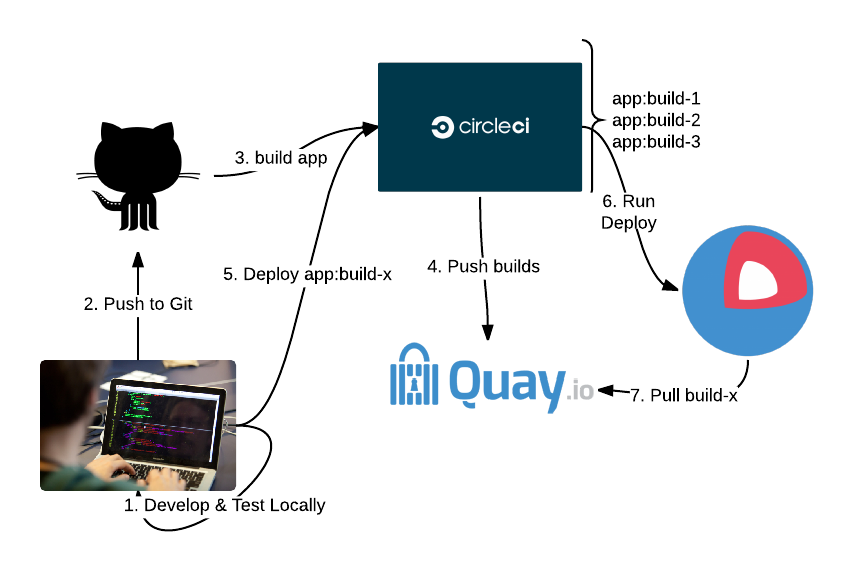
Build & Deploy
Docker Issues
- Daemon can leak memory.
- Docker builds can take a long time, lots of data.
- Docker pulls not verified.
- Containers don't persist.
Mitigation
- Don't log lots of data to stdout & stderr.
- Use smaller base images (i.e. debian & busybox).
- Follow image building best practices.
- Use an internal registry.
- Use data only containers for db's (still annoying).
CoreOS Issues
- Hard to install custom tools on the host.
- BTRFS has many maintenance issues.
- Docker has issues playing nice with systemd (mostly an issue with the docker daemon).
Mitigation
- Use privileged throwaway containers for ops work.
- Automate BTRFS cleanup/maintenance (and ext4 is in Alpha).
- systemd-docker: good writeup on the issue here.
- Rocket ... ?
TheMid
- New media site, establishing publishing platform.
- We're Hiring!
- Software Developer & Data Science roles
- jobs@themid.com
- themid.com/careers
ScriptEd >_
- Nonprofit puts developers in NYC high schools and provides paid summer internships.
- March 4 - NYC Tech Community Engagement Event.
- Contact sue@scripted.org
Script Event RSVP: http://scriptedinternships.splashthat.com
Thanks!
NodeJS, Docker, & CoreOS
By Edwin Fuquen
NodeJS, Docker, & CoreOS
- 1,669

