Group Members
NOOR ASHEERA BINTI MAZLAN 1323774

BEKKAI AMINE FATAH 1429659
HUSNI BIN HASSAN BASRI 1318789
ASYRAF BIN AHMAD ROSLAN 1414331
AHMAD RASYAD BIN HANIZAM 1416113
Security Technologies?
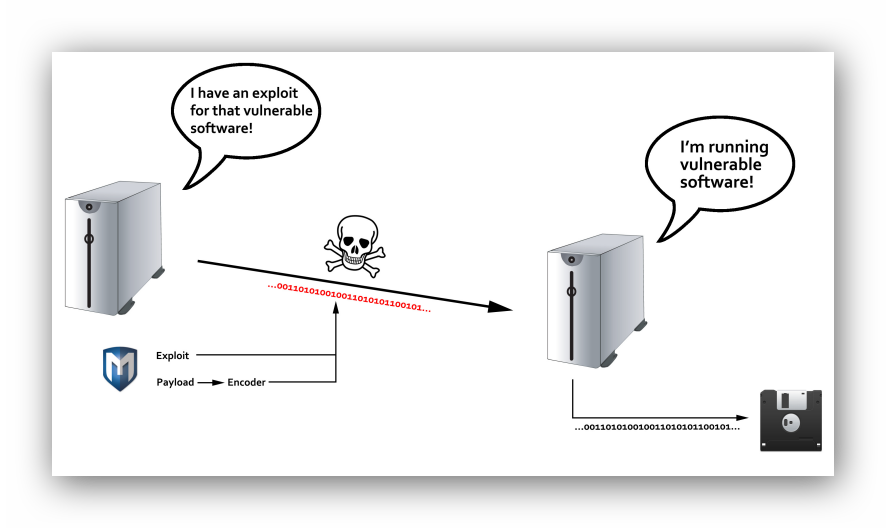
Metasploit

What is it?
Open Source project
- pentesting tool
- Framework
- Collection of tools and functionalities
- combine or create new functionalities
What's inside?
Exploits
a piece of code that can be used by an attacker to take advantage of a vulnerability.
Payloads
a code or a tool that we will leave behind in the hacked system after the exploit has been successfully executed.
Post
are modules that we can use post exploitation of the system.
Encoders
are modules that enable us to encode our payloads in various ways to not be detected
Nops
are short for No OPerationS.This can be crucial in creating a buffer overflow.
Auxiliary
includes numerous modules. such as fuzzers, scanners, DOS attacks.
Pros & Cons
Who
How
Intention
Pros
- Determine the variety of different attacks vectors.
- Identify select high-risk weaknesses.
- Identifying cracks that are impossible to detect through automated security systems.
- Testing and improving the strength and response.
Cons
- Tester Trustworthiness.
- Unrealistic Test Conditions.
Playlaods and the backdoors created by Metasploit might be highly detectable by antiviruses and this is due to the nature of Metasploit being an open source
Popular attacks
MS08-067 (windows XP)
MS06-040 (windows NT)
Overcoming Attacks
- Patching if available.
- A software used to fix security vulnerabilities and bugs.
- Run applications and processes with low privilege.
- Network access only limited to trusted hosts.
- Monitor the network for anomalies.
Metasploit for Security
A case study
Challenge
Can we automate the detection of specific exploits on a network traffic in a campus university network ?
Islamic perspective

“Ye are the best community that hath been raised up for mankind. Ye enjoin right conduct and forbid indecency; and ye believe in Allah. And if the People of the Scripture had believed it had been better for them. Some of them are believers; but most of them are evil-livers.”
Quran 3:110
Demo
Disclaimer:
This demonstration is for educational purposes only.
We are not responsible for any illegal use of the information provided by this demo in any way shape or form.
These tools are very powerful and can cause a lot of damage to systems.
Conclusion

Metasploit
By gimyboya
Metasploit
- 641



