Introduction to Traefik on Docker Swarm
Asmir Mustafic
PHP User Group Berlin - September 2019

Reverse Proxy
Me
@goetas
- Twitter: @goetas_asmir
- Github: @goetas
- LinkedIn: @goetas
- WWW: goetas.com
Asmir Mustafic

Berlin
Community
- jms/serializer (maintainer)
- masterminds/html5 (maintainer)
- hautelook/templated-uri-bundle (maintainer)
- goetas-webservices/xsd2php (author)
- goetas-webservices/xsd-reader (author)
- goetas-webservices/soap-client (author)
- goetas/twital (author)
- PHP-FIG secretary
Reverse Proxy or Proxy



proxy
reverse proxy
users
server
Load balancing




HTTPS



https
http
Merge URL Spaces


sport.host.com/top-10
politic.host.com/germany

host.com/politic/germany
host.com/sport/top-10
Compression



gzip
plain
Cache




cache
Serve static content



index.php
image.png

Logging





Authentication





Rate limiting





Security





Projects
HA Proxy
| load balancing | ✔ |
| logging | ✔ |
| https/ssl/http2 | ✘ |
| static content | ✘ |
| merge url space | ✘ |
| cache | ✘ |
| compression | ✘ |
TCP level
FAST! FAST! FAST! FAST! FAST! FAST!
Varnish
| load balancing | ✔ |
| logging | ✔ |
| https/ssl/http2 | ✘ |
| static content | ✘ |
| merge url space | ✔ |
| cache | ✔ |
| compression | ✔ |
CACHE! CACHE! CACHE! CACHE! CACHE!
HTTP level
nginx
| load balancing | ✔ |
| logging | ✘ ? |
| https/ssl/http2 | ✔ |
| static content | ✔ |
| merge url space | ✔ |
| cache | ✔ |
| compression | ✔ |
$ 670 million acquisition!
HTTP level
Static Configurations
Change configs and reload configs
Dynamic Environment


Dynamic Environment
































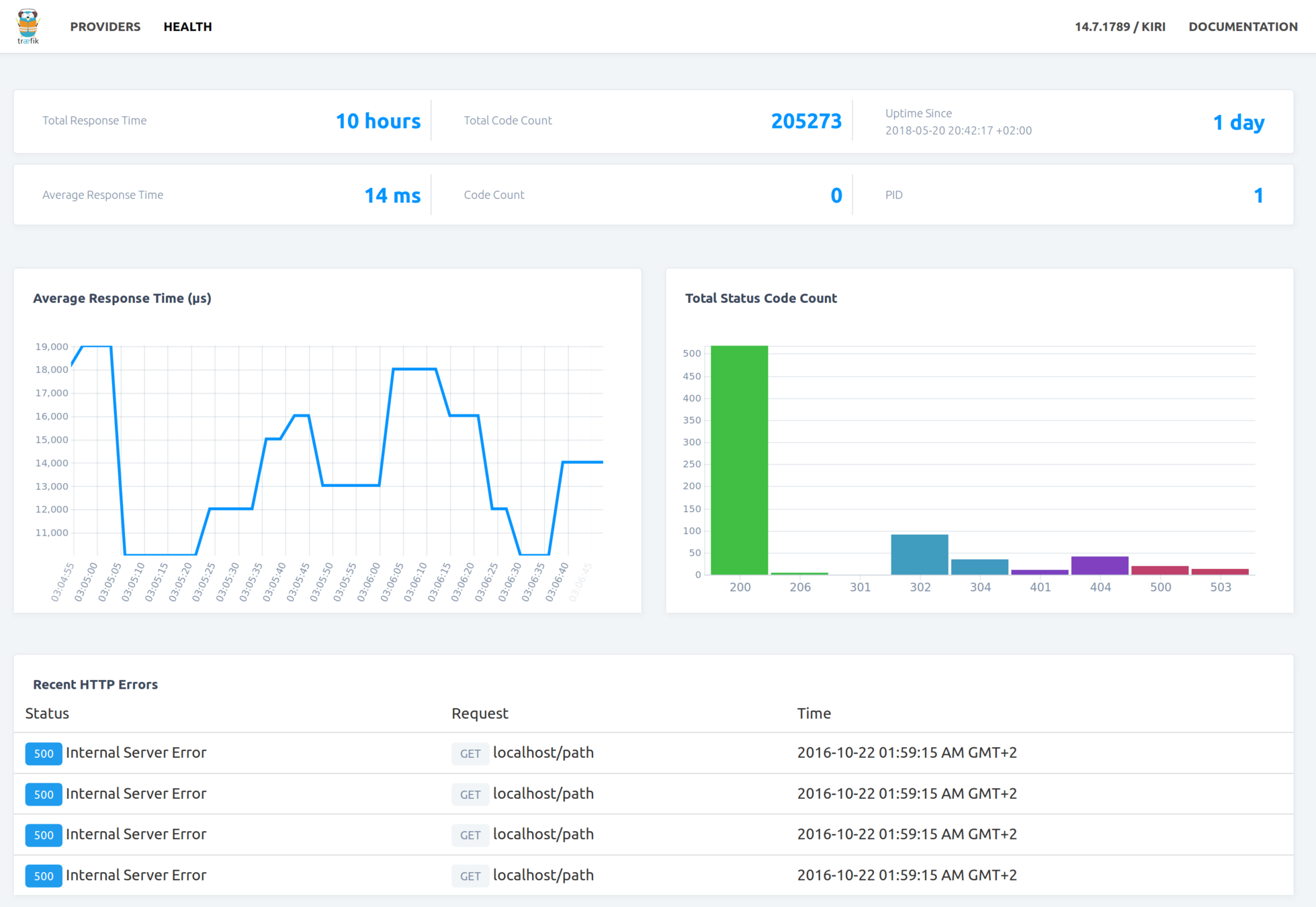
Traefik
MIT License
containo.us
Cloud Native Edge Router

HTTP(s) protocol
Traefik
DYNAMIC CONFIGURATIONS!
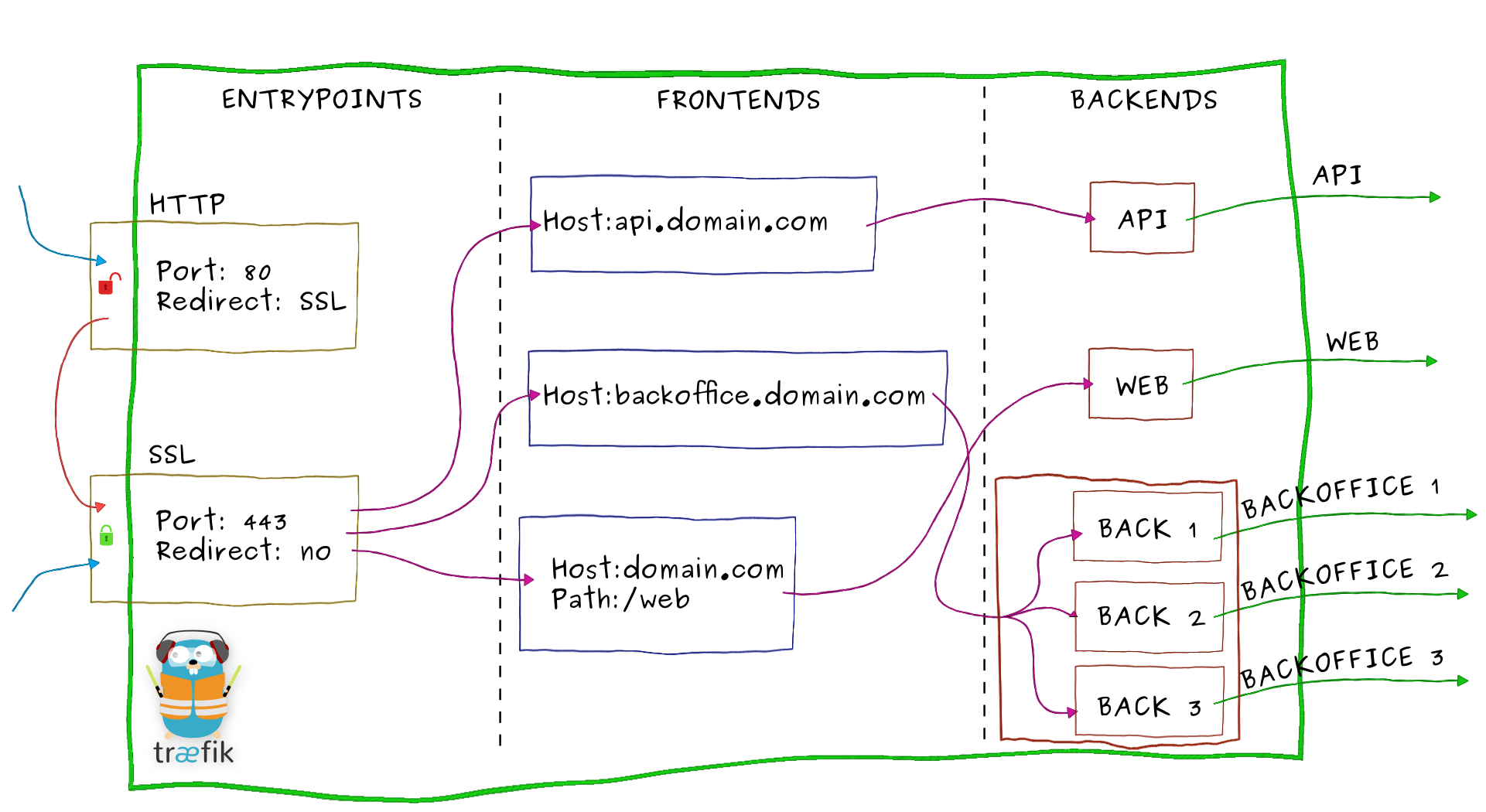
Architecture
Configuration
# Entry Points
[entryPoints]
[entryPoints.http]
address = ":80"
# Frontends
[frontends]
[frontends.frontend1]
entryPoints = ["http"]
backend = "backend1"
# Backends
[backends]
[backends.backend1]
[backends.backend1.servers]
[backends.backend1.servers.server0]
url = "http://10.10.10.1:80"TOML file
Traefik
version: '3.4'
services:
reverse-proxy:
image: traefik:1.7-alpine
command: "-c /conf.toml"
volumes:
- "./conf.toml:/conf.toml"
ports:
- "80:80"
- "443:443"
# - "8080:8080"$ docker-compose up -d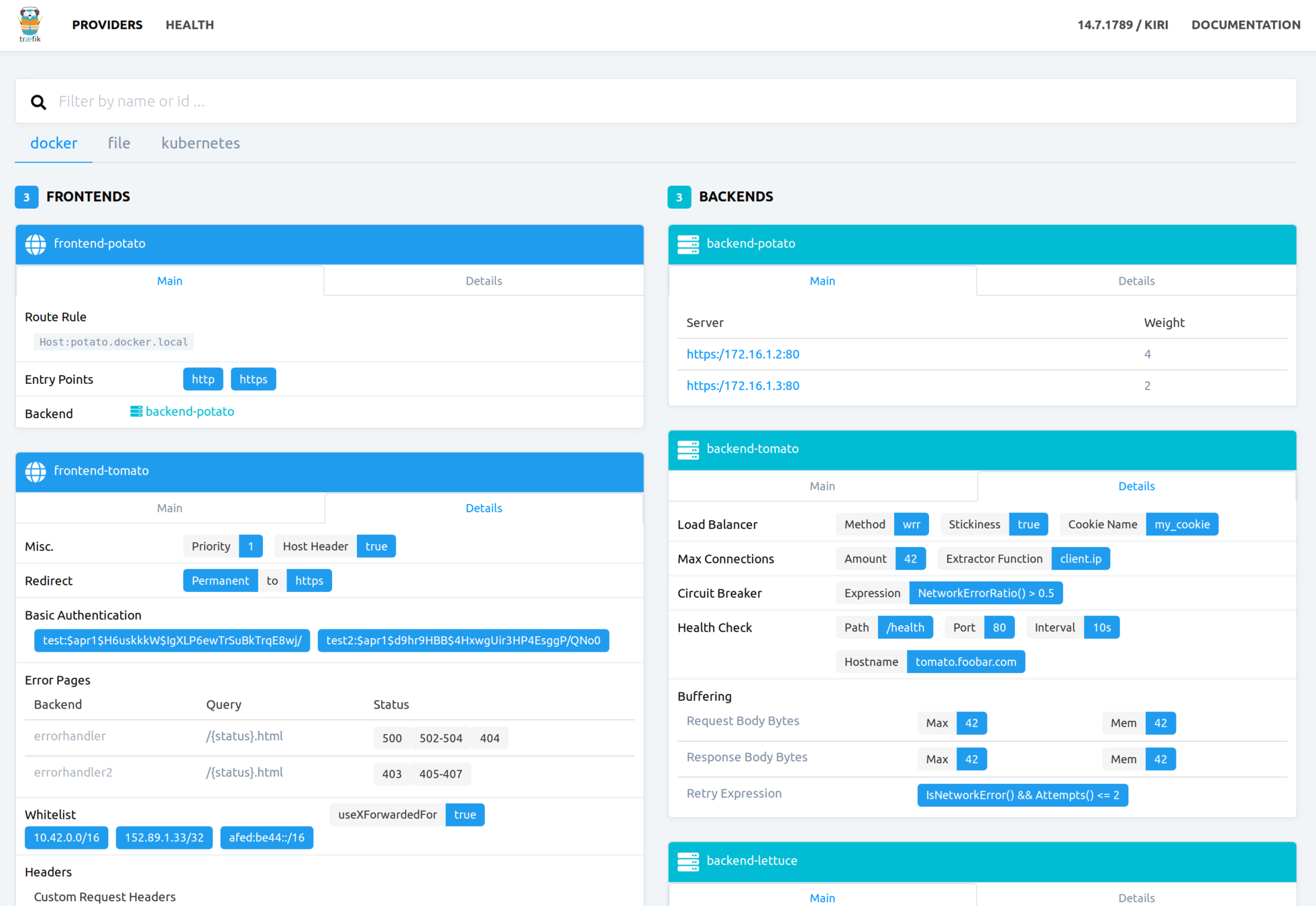
SSL/HTTPS
HTTP2
AUTH
Rate Limiting
Custom Errors
Load balance RR, WRR
Circuit breakers
Health Checks
Sticky Sessions
Custom Headers
HA Cluster
Prometheus
OpenTracing
Let's Encrypt
Configuration Discovery
Docker / Swarm mode
Kubernetes
Mesos / Marathon
Rancher (API, Metadata)
Azure Service Fabric
Consul Catalog
Eureka
Amazon ECS
Amazon DynamoDB
Rest API
Configuration
# Enable Docker Provider.
[docker]
endpoint = "tcp://1.2.3.4:2377"
watch = true
swarmMode = true
exposedByDefault = false
Discovery
Docker Swarm TOML configs
Configuration
Discovery
version: '3.4'
services:
web:
image: nginx
deploy:
labels:
- "traefik.enable=true"
- "traefik.frontend.rule=Host:example.com"
Docker / Docker Swarm
Configuration
Discovery
version: '3.4'
services:
web:
image: nginx
deploy:
labels:
- "traefik.enable=true"
- "traefik.frontend.rule=Host:example.com"
- "traefik.port=80"
- "traefik.backend.healthcheck.path=/health"
- "traefik.backend.loadbalancer.method=wrr"
- "traefik.backend.loadbalancer.stickiness=true"
- "..."Docker / Docker Swarm
Configuration
Discovery
---
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
replicas: 1
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
containers:
- image: traefik
name: traefik-ingress-lb
ports:
- name: http
containerPort: 80
- name: admin
containerPort: 8080
args:
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
type: NodePort
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
- watchKubernetes
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
replicas: 1
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
containers:
- image: traefik
name: traefik-ingress-lb
ports:
- name: http
containerPort: 80
- name: admin
containerPort: 8080
args:
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
type: NodePort---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: DaemonSet
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
containers:
- image: traefik
name: traefik-ingress-lb
ports:
- name: http
containerPort: 80
hostPort: 80
- name: admin
containerPort: 8080
securityContext:
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
args:
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
Cluster Mode
leader / worker
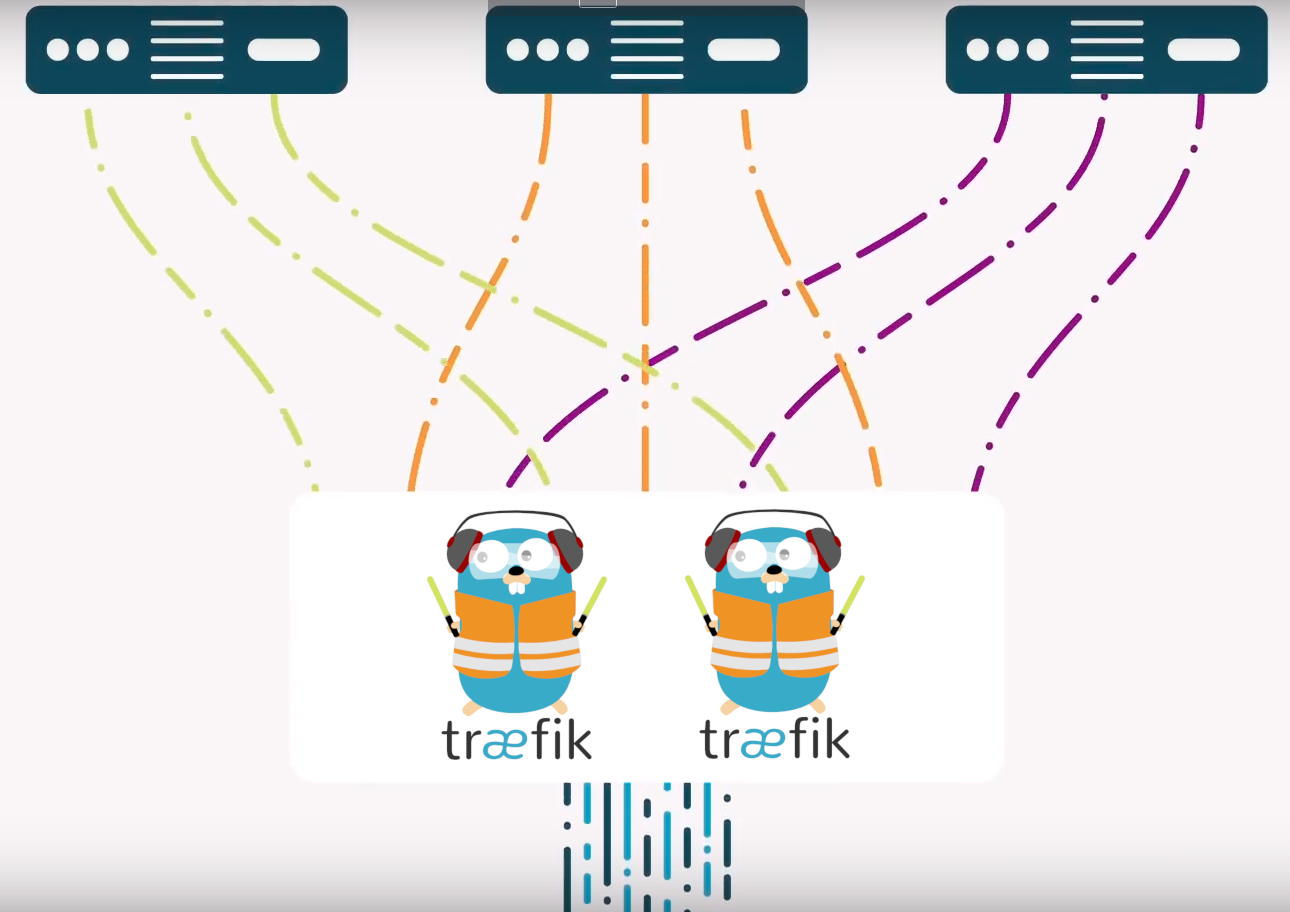
Cluster Storage
K/V Stores:
Consul
etcd
ZooKeeper
boltdb
Cluster








traefik 1
traefik 2
traefik 3
consul (k/v)
internet
backend
Complete Example
Docker-Swarm based
Traefik (1/2)
version: '3.4'
services:
traefik-init:
image: traefik:1.7-alpine
command:
- "storeconfig"
- "--consul"
- "--consul.endpoint=3.4.5.6:8500"
- "--consul.watch"
- "--defaultentrypoints=http,https"
- "--entrypoints=Name:http Address::80 Redirect.EntryPoint:https"
- "--entrypoints=Name:https Address::443 Compress:true"
- "--docker.endpoint=tcp://1.2.3.4:2375"
- "--docker.swarmMode"
- "--docker.exposedByDefault=false"
deploy:
restart_policy:
condition: noneTraefik (2/2)
version: '3.4'
services:
reverse-proxy:
image: traefik:1.7-alpine
command:
- "--consul"
- "--consul.watch"
- "--consul.endpoint=3.4.5.6:8500"
ports:
- target: 80
published: 80
mode: host
- target: 443
published: 443
mode: host
- target: 8080 # dashboard
published: 8080
mode: host
deploy:
replicas: 3Thank you!
- Twitter: @goetas_asmir
- Github: @goetas
- LinkedIn: @goetas
- WWW: goetas.com
Introduction to Traefik on Docker Swarm - PHP UG - Berlin
By Asmir Mustafic
Introduction to Traefik on Docker Swarm - PHP UG - Berlin
- 2,641



