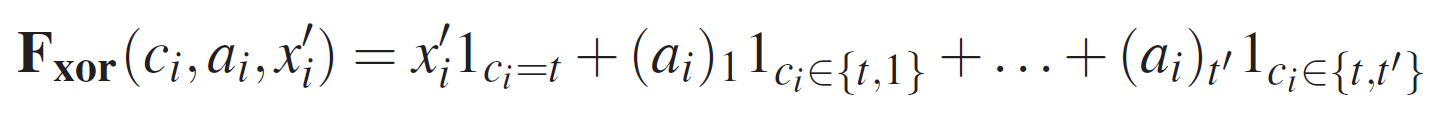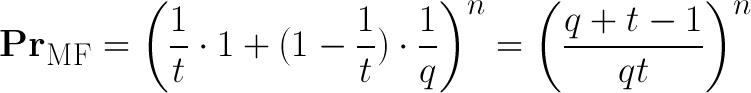The SKI Protocols
A Distance Bounding RFID Protocol Family
[Boureanu-Mitrokotsa-Vaudenay 2013]

Han Tüzün
Bilkent University
Outline
What is RFID?
Attacks
• Mafia-Fraud
• Distance-Fraud
Relay Attack
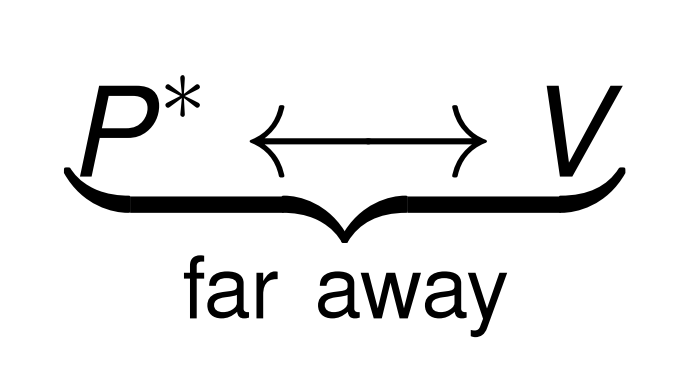
Mafia-Fraud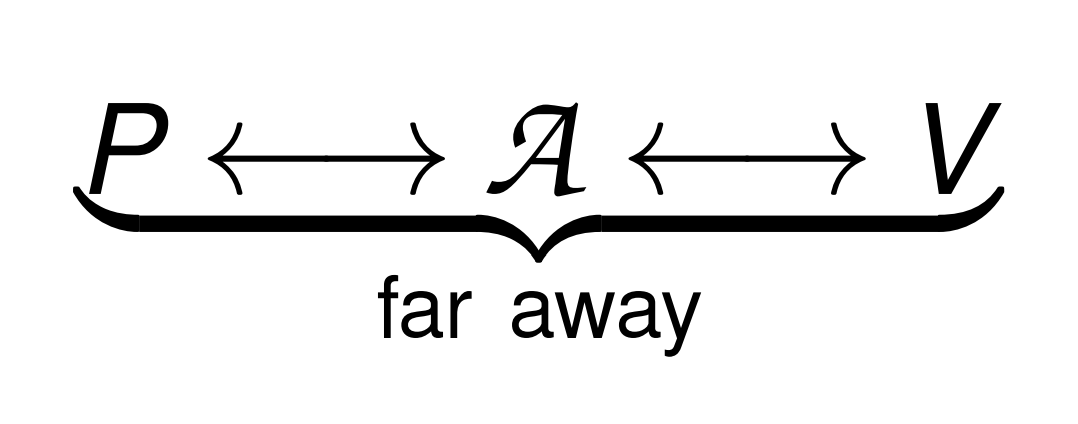
an adversary A tries to prove that
a prover P is close to a verifier V
Mafia-Fraud

Distance-Fraud
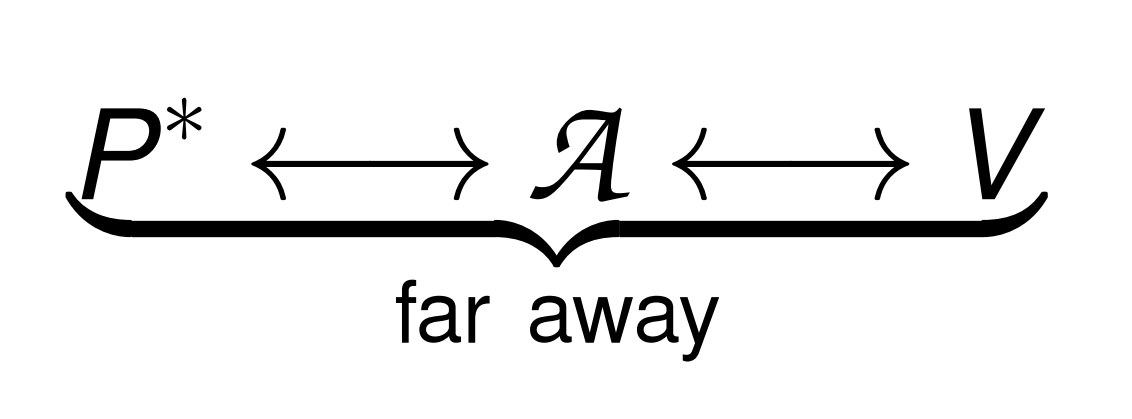
a malicious prover P* tries to prove that
he is close to a verifier V
Distance-Fraud

Terrorist-Fraud
a malicious prover P* helps an adversary A to prove that
P* is close to a verifier V
without giving A another advantage
Terrorist-Fraud
What is Distance-Bounding RFID Protocols?
Phases of DB RFID Protocols
Identification
Varible exchangeSignature exchange
Fast Phase:
Timing the delay between sending out a challenge
and receiving back the corresponding response
Popular DB RFID Protocols
Hancke & Kuhn (2005)
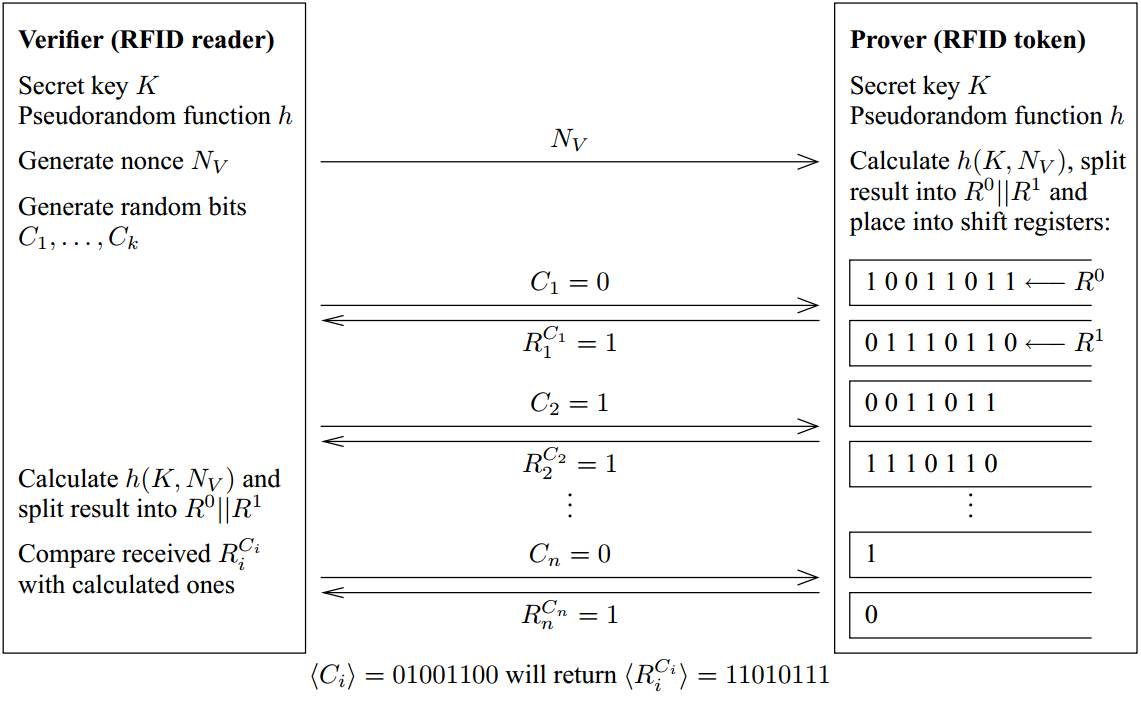
How to cope with TF?
The SKI Protocols
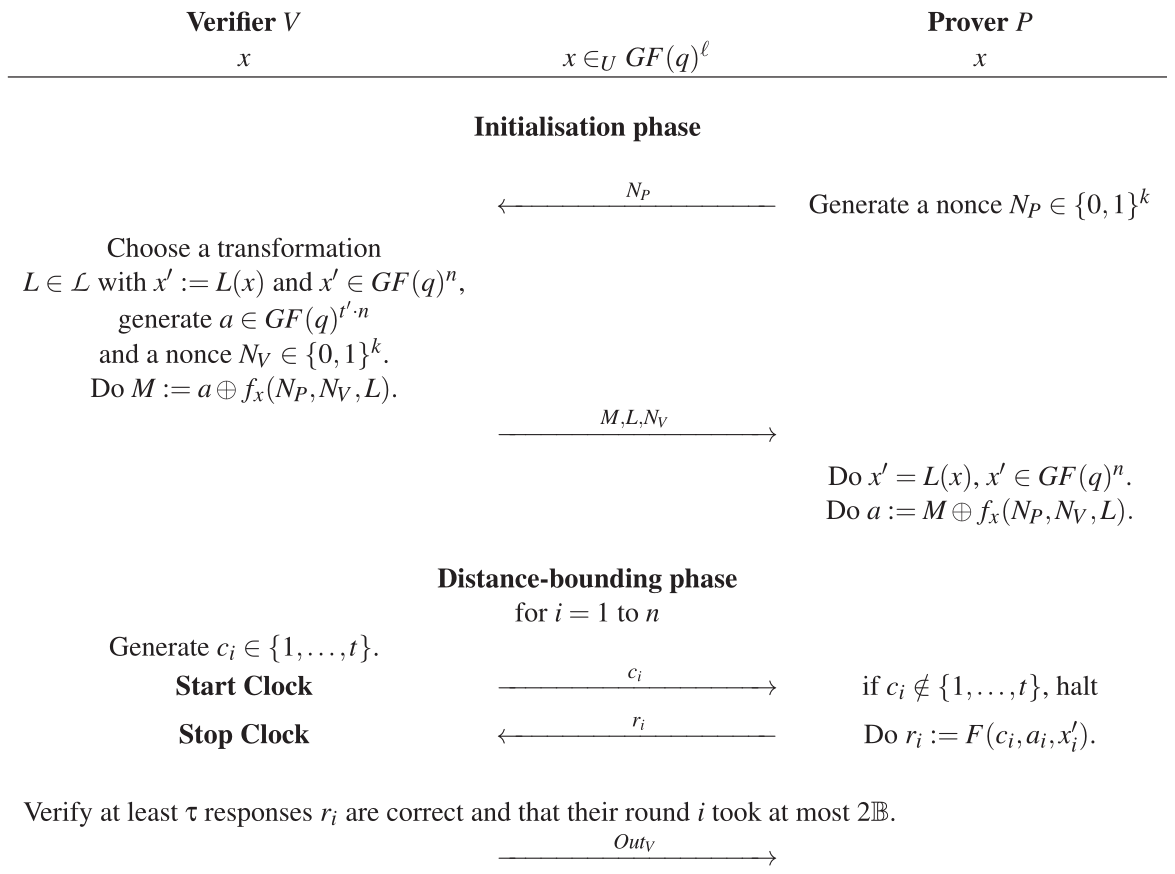
Overview of the SKI Protocols
Variables q , t and t'
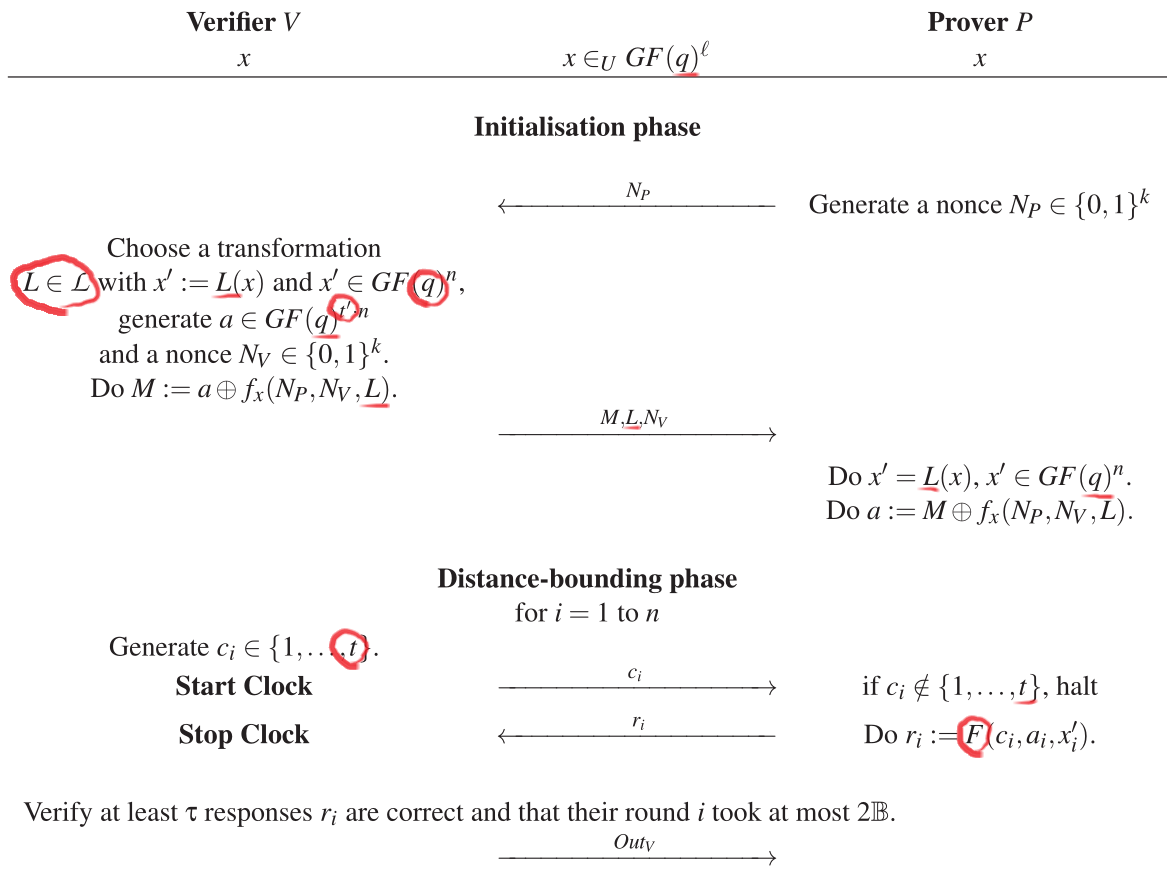
Linear Transformation ( ℒ )
- Protection against a TF by Hackne
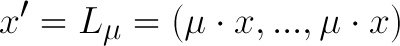
- In SKI, the adversary can get to learn L(x) + e
The Response-Function F
for i = 1 to n, i-th response produced by the following F:
Variations of the SKI Protocols
q, t, t', F, ℒ
SKI pro
SKI lite
Security Analysis of the SKIpro
• Framework for Security Analysis
•
Impersonation?
• Distance-Fraud Resistance
Impersonation?
an adversary A tries to prove that
a prover P is close to a verifier V
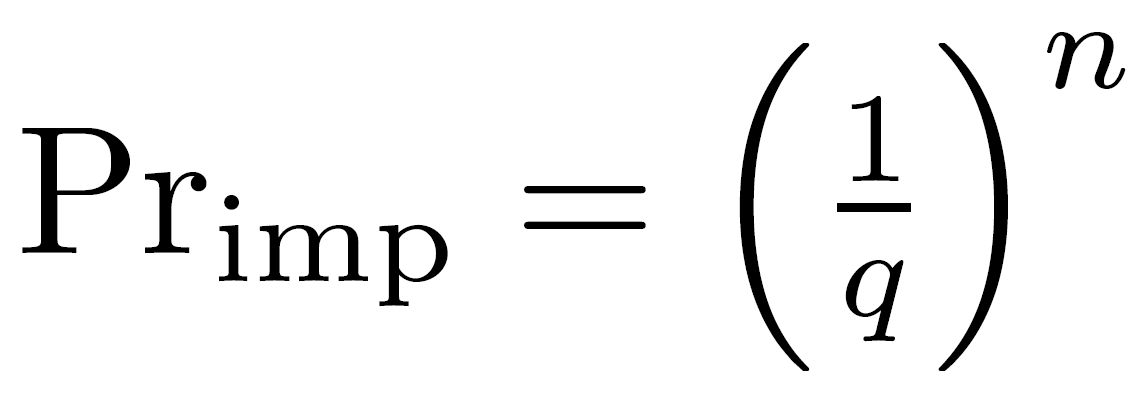
Distance-Fraud Scheme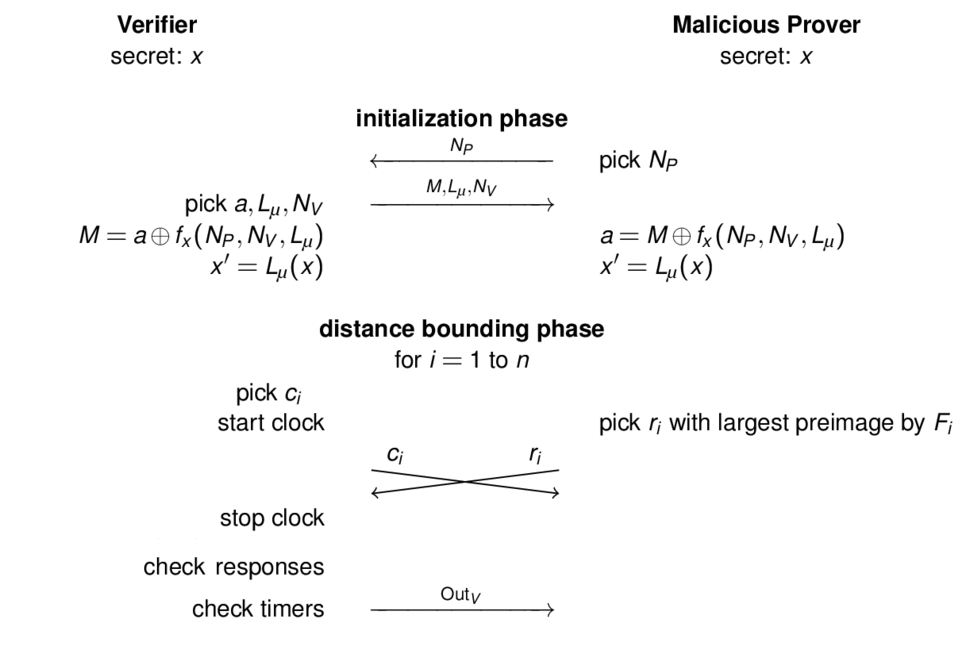
Distance-Fraud Probability
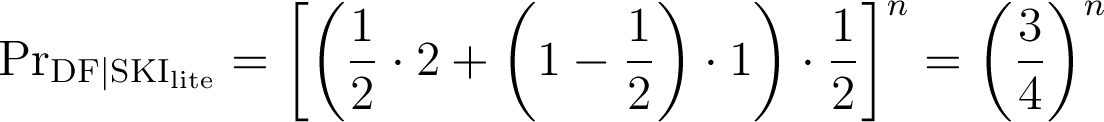
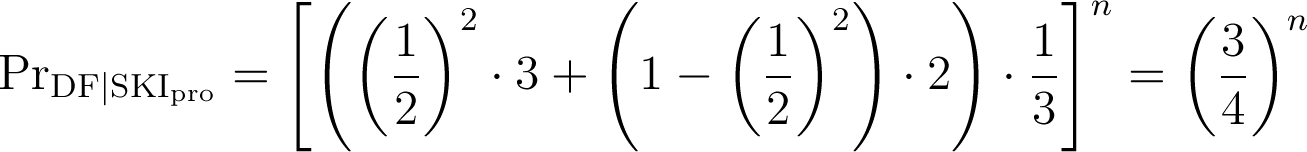
Mafia-Fraud Scheme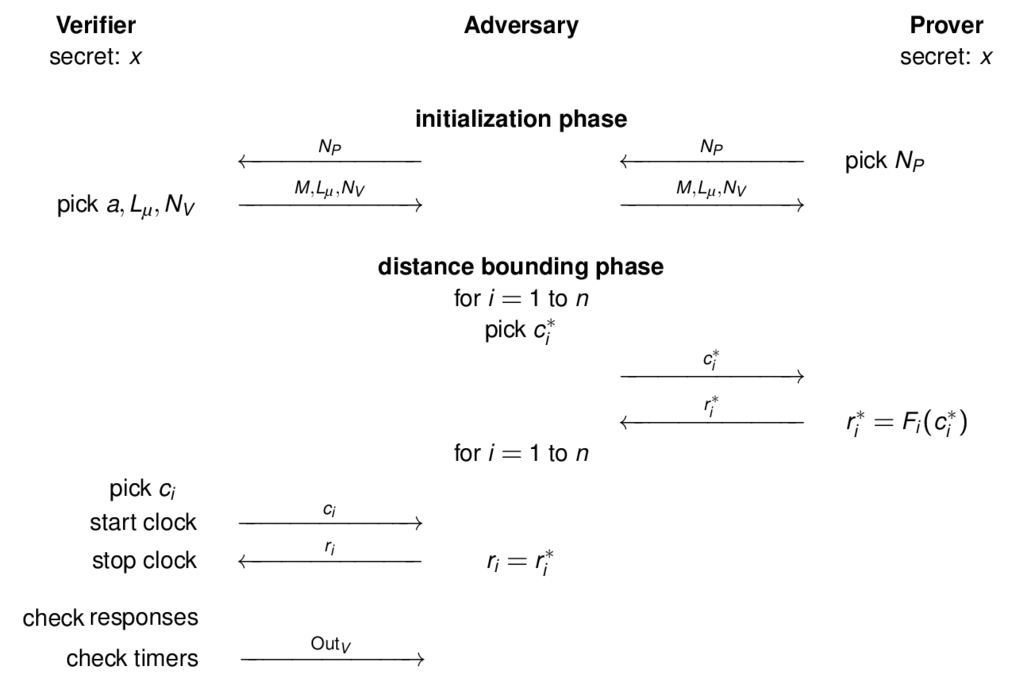
Mafia-Fraud Probability
Terrorist-Fraud Scheme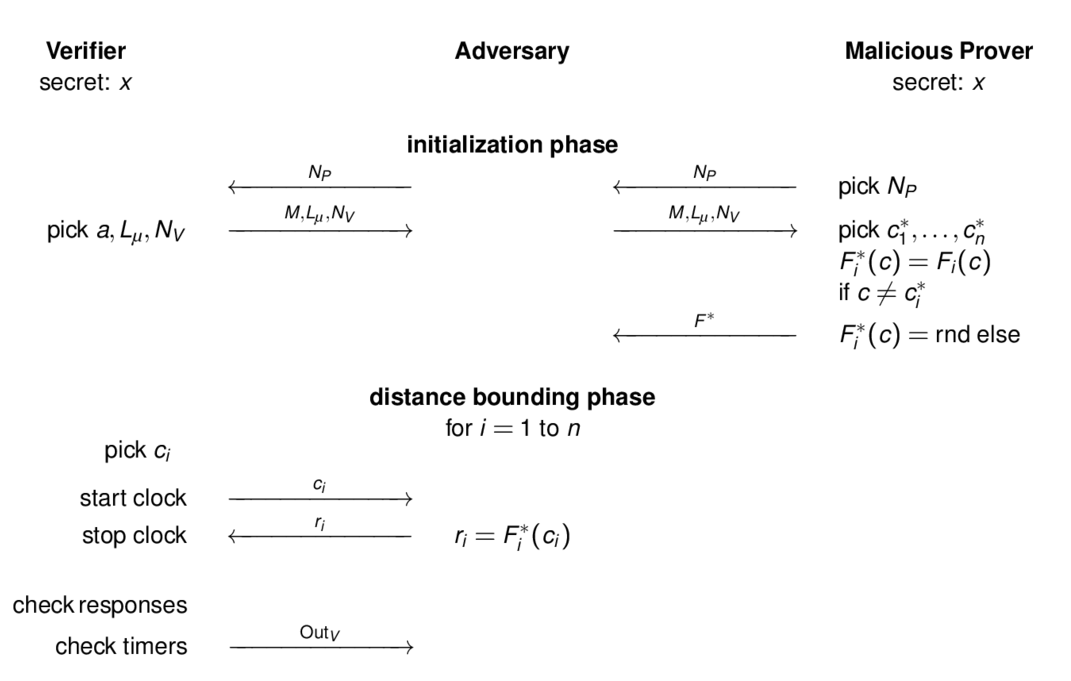
Terrorist-Fraud Probability
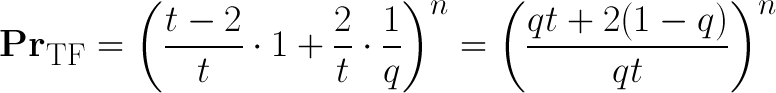
Terrorist-Fraud by Hancke
- Choose a noise-vector e of Hamming weight n - Ƭ
- Provide a slightly modified table ci-> F(ci, ai, xi) :
- if ei = 1, then F(ci, ai, xi) is flipped
- else, do not change the output of F
- Response challenge
- Reconstruct x + e
- In SKI, the adversary can get to learn L(x) + e
My Opinions
• Hard implementation of protocols with q > 2
• A powerful SKI version is not analysed
• Insufficient visualization
References
- Bourenau, Mitrokosta, Vaudenay (2013). Secure & Lightweight Distance Bounding
- Bourenau, Mitrokosta, Vaudenay (2013). Towards Secure Distance Bounding
- Vaudenay (2012). On the Need for Provably Secure Distance Bounding
- Avoine, Bingöl, Kardas, Lauradoux, Martin (2011). A Framework for Analyzing RFID Distance Bounding Protocols
- Avione, Lauradoux, Martin (2011). How Secret-sharing can Defeat Terrorist Fraud
-
Lauradoux (2011). Distance Bounding Protocols and Terrorist Fraud
Thank You
The SKI Protocol
By Han Tuzun
The SKI Protocol
- 1,628