Onions adventures
How to use onion services and the
network
hiro@torproject.org

¡Hola!

Hi, I am silvia..
- Some known me as Hiro.
- I work at the Tor Project.
- I was part of the Information Security Group in the Department of Telematics Engineering at UPC-Barcelona where I got my Ph.D.

Know your onions
-
What is Tor and what it can do for you.
-
How Tor provides privacy and anonymity.
-
Using Tor at the application layer: The Tor Browser.
-
Onion services and bidirectional anonymity.
-
Using onion services.
-
Doing research within the Tor network.

What is and
what it can do for you

Tor is a privacy tool
- Tor is free software.
- Tor is a community made up of a diverse group of developers, researchers, relay operators, volunteers.
- Tor is an open network.
- Tor is a non-profit.

Tor is about 2M daily users using the network!
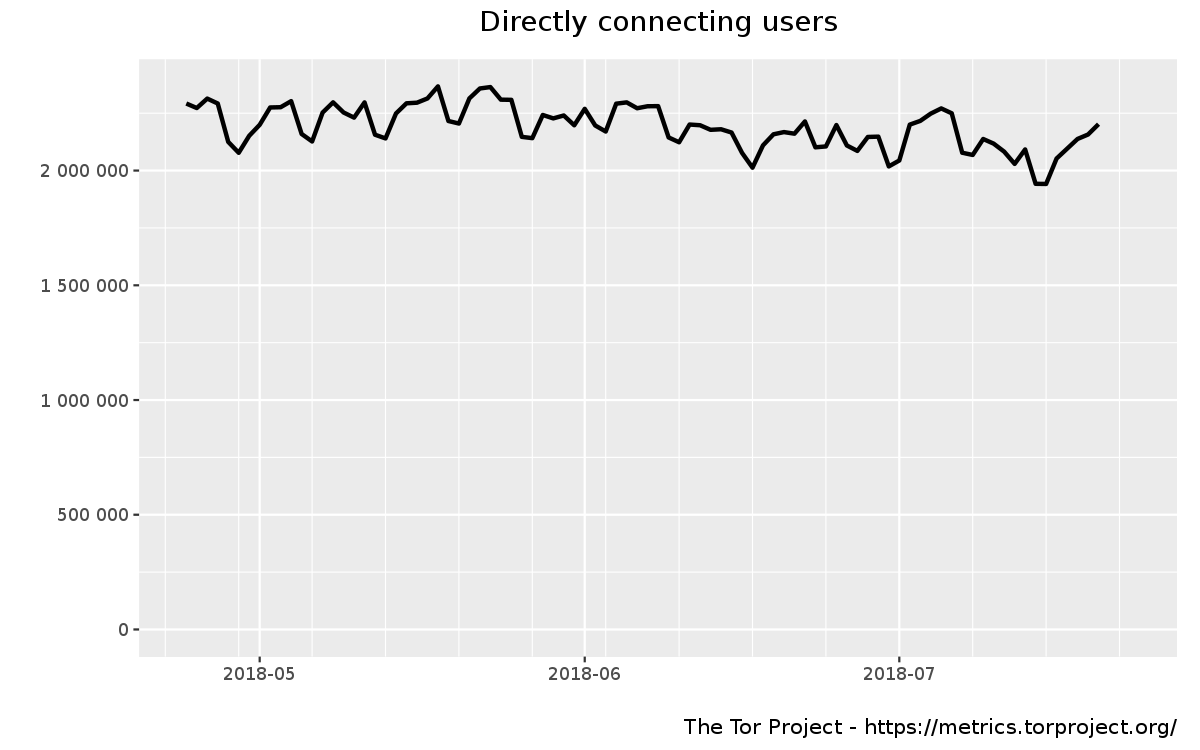

Tor is about 2K bridges and 6K relays


Tor provides about 200Gbit/s bandwidth


What does Tor do?
- Tor provides privacy.
- Tor provides anonymity.
- Tor provides communication security.
- Tor provides a traffic analysis resistant communication network.
- Tor provides reachability against censorship.

How does provide Privacy and Anonymity?

Privacy by design
Tor provides privacy by distributing TRUST


How Tor works

Alice wants to talk to some Bob. Alice also wants to stay safe.
How Tor works

The connection between Alice and the tor network is encrypted. The connection between the last exit node and Bob is not.
That's why it is important to use HTTPS!
How Tor works

Anonymity > Encryption
Anonymity > Encryption
- Encryption doesn't hide conversations metadata
- Encryption doesn't hide your social graph
- Encryption doesn't hide network metadata
- Encryption doesn't hide your location
Using at the app layer:
Tor Browser

What is Tor Browser
Tor Browser is a modified Firefox ESR.
Tor Browser Packages:
-
Tor, Torbutton,
-
TorLauncher,
-
NoScript,
-
and HTTPS-Everywhere.
Why Tor makes a browser
Tor browser is designed to:
- Ensure the safe use of Tor.
- Reduce linkability of user activities on different websites.

Onion Services
Providing bidirectional anonymity
Next gen Onion Services
-
Better crypto [ed|curve25519 - Keccak(SHA3)]
-
54 chars for onion service address.
- Address the onion service through their public key
- The key system allows to create subkeys (so the main key stays hidden)
- Address the onion service through their public key
- Rendezvous Single Onion Services
- Improve traffic analysis resistance
- Shared randomness in the desc id

How Onion Services work

Bob is an onion service and Alice a Tor Browser user.
Bob picks 3 introduction points and builds a circuit.
How Onion Services work

Bob builds a descriptor and uploads it to the directory
How Onion Services work

Alice fetches the descriptor from the directory and learns how to reach Bob.
How Onion Services work

Alice tells Bob to meet her at the rendezvous point.
How Onion Services work

How Onion Services work
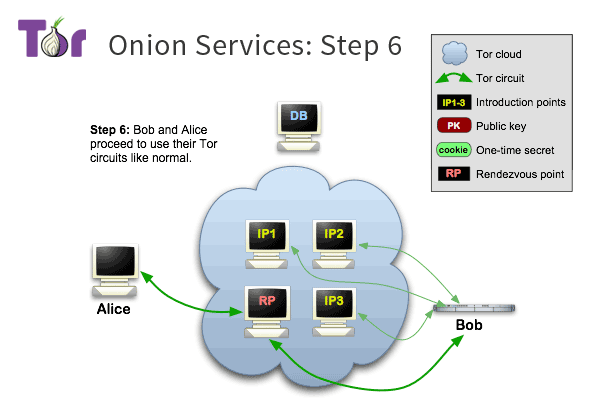
Both Alice and Bob connect with a 3 hops circuit to the RP.
Using Tor within other applications through onion services.
Tor ecosystem


Onion-micro-services ??
- Onion services can be integrated into existing web services, making them more secure.
- This is especially interesting for microservices architectures.

SSH onion-services
ssh:
container_name: onion_ssh
hostname: onion_ssh
build: ${PWD}/config/ssh
command: /home/root/init.sh
volumes:
- ./config/ssh/tor/torrc:/etc/tor/torrc
- ./config/ssh/keys/:/home/root/.ssh/keys
- ./config/ssh/init.sh:/home/root/init.sh
- ./config/ssh/sshd_config:/home/root/.ssh/ssh/sshd_config
ports:
- "2222:22"FROM debian
MAINTAINER hiro <hiro@torproject.org>
RUN apt-get update
RUN apt-get install -y sudo vim openssh-server tor
USER root
RUN mkdir -p 700 /home/root/.ssh \
&& mkdir /var/run/sshd \
&& mv /etc/ssh /home/root/.ssh/ssh \
&& ln -s /home/root/.ssh/ssh /etc/ssh
WORKDIR /home/root
VOLUME /home/root
EXPOSE 22SSH onion-services
## /etc/torcc
##
############### This section is just for location-hidden services ###
## Once you have configured a hidden service, you can look at the
## contents of the file ".../hidden_service/hostname" for the address
## to tell people.
##
## HiddenServicePort x y:z says to redirect requests on port x to the
## address y:z.
HiddenServiceDir /home/tor/onion_ssh_service/
HiddenServicePort 22 127.0.0.1:22SSH onion-services
$ docker-compose up --build ssh$ docker exec -it onion_ssh /bin/bash
$ torsocks ssh -o IdentitiesOnly=yes -i /home/hiro/.ssh/key -v root@wklfdwgq5txfvq5v.onion
TorSOCKS
$ torsocks curl http://yjuwkcxlgo7f7o6s.onion/
- Torsocks is a wrapper use applications through the Tor network
- In this example, we run curl through the tor network and reach the onion address for archive.torproject.org
- We have a how-to torify apps [WIP]
Using the Socks5 Proxy
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import requests
proxies = {
'http': 'socks5://127.0.0.1:9050',
'https': 'socks5://127.0.0.1:9050'
}
r = requests.get('http://yjuwkcxlgo7f7o6s.onion/', proxies=proxies)
- We can use the SOCKS5 proxy provided by tor
- In this example, we fetch archive.torproject.org via its onion address

Onions for the
decentralised weB
Onion services can also be used for p2p applications:
-
OnionShare is a file sharing app that works by starting a web server, making it accessible as a Tor Onion Service, and generating an unguessable URL to access and download the files.
- https://onionshare.org
NEXT STEP
Start a container from any device and share any kind of service and make this as easy as opening an app!
Onions for the
decentralised weB
$ ./dev_scripts/onionpeer.py
api_client = docker.APIClient(base_url='unix://var/run/docker.sock')
client = docker.from_env()
build = [line for line in api_client.build(path='./containers/website',
tag='website',
dockerfile='./Dockerfile')]
container = client.containers.run('website:latest', detach=True)
nginx = container.exec_run('nginx', user='root').outputResearch within The tor Network
Many people around the world are doing research on how to improve the Tor design, what's going on in the Tor network, and more generally on attacks and defenses for anonymous communication systems.
Research within The tor Network
Data
- We've been collecting data to learn more about the Tor network: how many relays and clients there are in the network, what capabilities they have, how fast the network is, how many clients are connecting via bridges, what traffic exits the network, etc.
- We are also developing tools to process these huge data archives and come up with useful statistics. Let us know what other information you'd like to see, and we can work with you to help make sure it gets collected safely and robustly.
Research within The tor Network
Analysis.
- If you're investigating Tor, or solving a Tor-related problem, please talk to us somewhere along the w
- Since the Tor protocol and the Tor network are both moving targets, measuring things without understanding what's going on behind the scenes is going to result in bad conclusions.
- In particular, different groups often unwittingly run a variety of experiments in parallel, and at the same time we're constantly modifying the design to try new approaches.
Research within The tor Network
Measurement and attack tools.
- We're building a repository of tools that can be used to measure, analyze, or perform attacks on Tor.
- Many research groups end up needing to do similar measurements (for example, change the Tor design in some way and then see if latency improves), and we hope to help everybody standardize on a few tools and then make them really good.
- Also, while there are some really neat Tor attacks that people have published about, it's hard to track down a copy of the code they used. Let us know if you have new tools we should list, or improvements to the existing ones. The more the better, at this stage.
Research within The tor Network
We need defenses too — not just attacks.
- Most researchers find it easy and fun to come up with novel attacks on anonymity systems. We've seen this result lately in terms of improved congestion attacks, attacks based on remotely measuring latency or throughput, and so on.
- Knowing how things can go wrong is important, and we recognize that the incentives in academia aren't aligned with spending energy on designing defenses, but it sure would be great to get more attention to how to address the attacks.
- We'd love to help brainstorm about how to make Tor better. As a bonus, your paper might even end up with a stronger "countermeasures" section.
Research within The tor Network
In Person help
- If you're doing interesting and important Tor research and need help understanding how the Tor network or design works, interpreting your data, crafting your experiments, etc, we can send a Tor researcher to your doorstep.
- As you might expect, we don't have a lot of free time; but making sure that research is done in a way that's useful to us is really important. So let us know, and we'll work something out.
Research IDEAS
- Minimize deanonymization attacks.
- Measuring diversity of the Tor network over time.
- Improving performances of the Tor network.
- Optimize Tor circuit usage patterns for clients.
- Minimize website fingerprinting attacks.
- Finding new applications for onion services.
- ... your imagination is the limit :)
https://research-staging.torproject.org/ideas/
https://www.petsymposium.org/
Cyberspace.
A consensual hallucination experienced daily by billions of legitimate operators, in every nation, by children being taught mathematical concepts...
A graphic representation of data abstracted from banks of every computer in the human system. Unthinkable complexity. Lines of light ranged in the nonspace of the mind, clusters and constellations of data. Like city lights, receding...
William Gibson, Neuromancer
Learn more...
- www.torproject.org
- Tor Browser design doc
- Mozilla Firefox Extended Support Release
- Tor Projects
- Tor Rendezvous Specification - Version 3
- Secure Messaging with Onion Services, a How-To
UPC seminar
By hiropaw
UPC seminar
- 1,094


