The Silent Sentinel: Rust-Powered WASM for Lightning-Fast Bot Detection at the Edge
Entering edge computing, I noticed existing bot detection tools were slow and intrusive. Initially choosing AssemblyScript for compatibility with our Deno-based stack, I faced performance limitations and quickly pivoted to Rust for superior WebAssembly support.
This led to "The Silent Sentinel," a fast, client-side WASM module running via WebWorkers, seamlessly detecting bots at the CDN edge—offering a competitive alternative to market leaders like Cloudflare and Google reCAPTCHA.
Background
I'm Barış Güler, an engineering leader with several years in software engineering, currently based in Berlin. My passion lies at the intersection of technology leadership, serverless architectures, and AI-driven solutions. I've led diverse teams at companies like Intel, Delivery Hero, Blacklane, and Würth (Cloud Services)—building scalable products, mentoring engineers, and aligning tech strategies with business goals. I'm deeply interested in emerging technologies like Rust, WASM and Deno, and I enjoy sharing my experiences through talks, articles, and open-source contributions.
Building other solutions on Nginx Unit & Synthetic Data.
Who am I?
〞
I've spent 20+ years convincing computers to do what I want—usually successfully. If not, I just pretend it was an AI experiment.
– Me
How the Story Begins
〞
We need to refactor our architecture as it becomes unscalable and unmanagable.
– A CTO at a CDN Company
〞
How about building a client bot detection tool, first?
– Me

What's
Silent Sentinel?
A Bot detection tooling for CDN customers to let them detect & block unexpected visits to their web apss and pages.
Silent Sentinel
- Only Client-side
- Static Checking
- Performant with WASM
- Browser-native
Competitors
- Server-side needed
- Dynamic Checking
- Async
- Server + Client side management needed


Static Checking
- Browser characteristics
- User Agent, Screen / Window Size, etc.
- Plugins, Navigation, Resource & Paint Timings
- No-server communication
Dynamic Checking
- User characteristics
- Mouse movements, click rates etc.
- Client-Server communication
From Scratch to GA
CDNs & Edge
The ideation phase focused on leveraging the CDN's global edge network to distribute bot detection efficiently.
1.
Build from Scratch
Starting from zero, we developed a WASM module in AssemblyScript for static bot detection, ensuring lightweight, high-performance execution in browsers.
2.
Distribution & Launch
The product was deployed globally through CDN infrastructure, ensuring low latency and wide accessibility.
3.
1.
Discovery of requirements for a WASM module.
2.
Analysis of the current market players
3.
Setting the SLOs and SLAs in combination with the additional feature sets
5.
Review and Iterate on the execution of development
4.
Plan the development phase with Vertical Slicing in support with product target audience
6.
Build the project to an MVP to test and evaluate. Iterate using these learnings.
Experimentation w/ Toolings
| Tool | Pros | Cons |
|---|---|---|
| AssemblyScript | TS Linguistics | Type Conversions |
| Deno | Easy to start | Ecosystem not mature yet |
| NATS | Service communication made easy | Learning curve and setup on-premises |
| ScyllaDB | Distributed nature | N/A |
〞
A Typescript-like Language
for WebAssembly
– AssemblyScript

Implementation with AssemblyScript
Build the Module
During the ideation phase, we explored AssemblyScript for its seamless integration with our Deno-based ecosystem.
1.
Compile to WASM
The AssemblyScript code was compiled into a lightweight WebAssembly module, optimized for performance and portability.
2.
Embed via SDK
A client-side SDK was developed to dynamically load the WASM module via a CDN cache into a WebWorker created on-the-fly.
3.
First Tryout
Pros
- Familiar Syntax
- Static Typing
- Interoperability
Cons
- Limited type support
- Side of the WASM module
- Immature tooling
Rust
- Full type interoperability
- Ecosystem
- Memory safety
- Easy to use
- 1st class support for WASM
AssemblyScript
- Limited type support
- Side of the WASM module
- Immature tooling

Rust Wins!
1.
Begin by identifying the limitations of the current AssemblyScript implementation and defining the goals for the migration
2.
Investigate Rust’s capabilities for WebAssembly compilation and compare them with AssemblyScript
3.
Creating a Plan that sets the requirements for the design and build phases
5.
Test each iteration to validate functionality against benchmarks from the AssemblyScript version
4.
Develop a comprehensive migration plan
6.
Deploy the MVP globally through CDN infrastructure, leveraging caching for efficient distribution
Migration from AssemblyScript to Rust
- No need to think about tooling
- Direct compilation without hassle w/ wasm-pack
Experience with Rust Developing WASM Modules

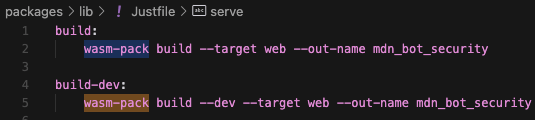
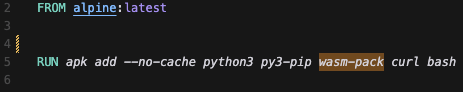
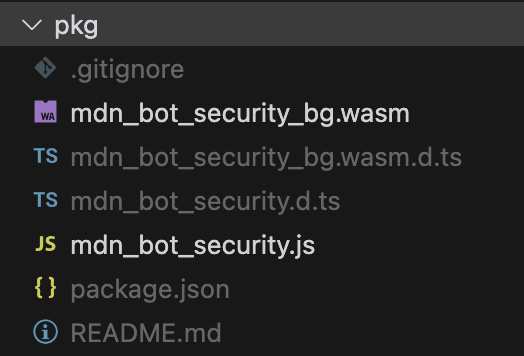
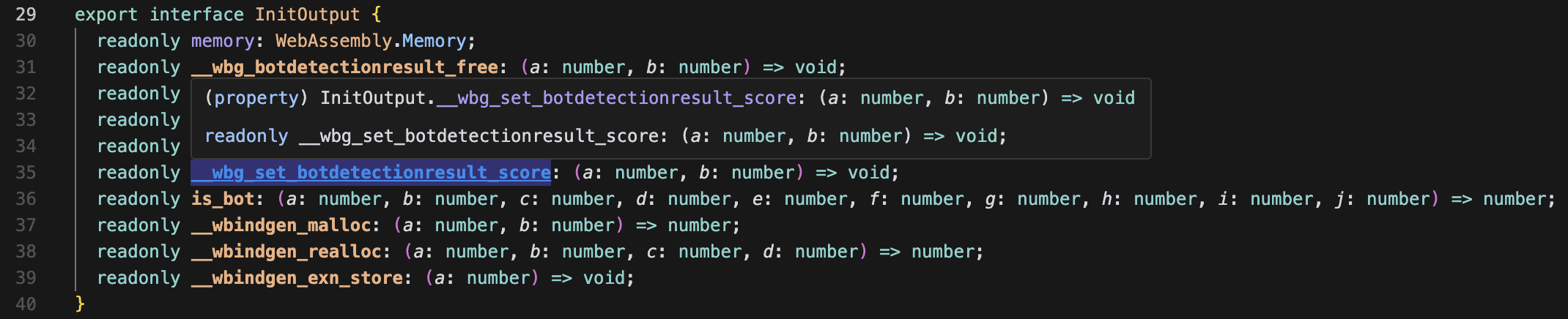

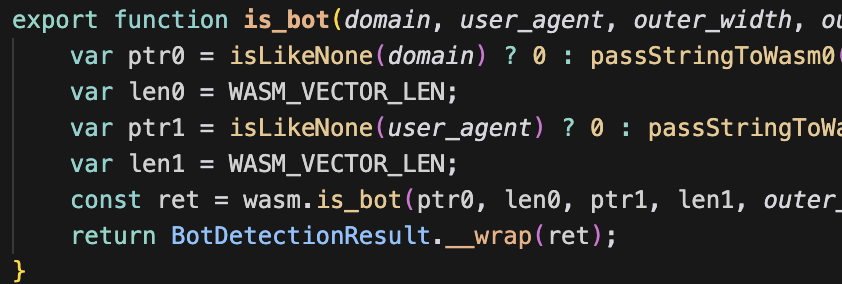
Implementation with Rust
Build the Module
During the ideation phase, expect to discuss the project in depth to clearly understand the goals and requirements.
1.
Compile to WASM
Our team makes each part of the build phase seamless with regular check-ins and deliverables.
2.
Embed via SDK
It's time to take the product live - the end if the build phase but the beginning of being in market.
3.

Success Metrics
| Metric | Level | Contact |
|---|---|---|
| False Positive Rate | Medium | <0.01% |
| Bot Detection Rate | High | >99% |
| Detection Response Time | High | <50ms |
| Customer Satisfaction | High | >95% |
- Bot Detection Response Time < 50ms
- System Availability = 99.9%
- False Positive Rate < 0.01%
- Detection Accuracy > 99%
- API Response Time < 100ms
Service Level Objectives (SLOs)
- System Uptime 99.9% Avalability
- Incident Response Time: 15 minutes for critical incidents
- Issue Resolution Time under 4 hours for critical incidents
- Monthly Performance Reports
- 24/7 Technical Support
Service Level Agreements (SLAs)
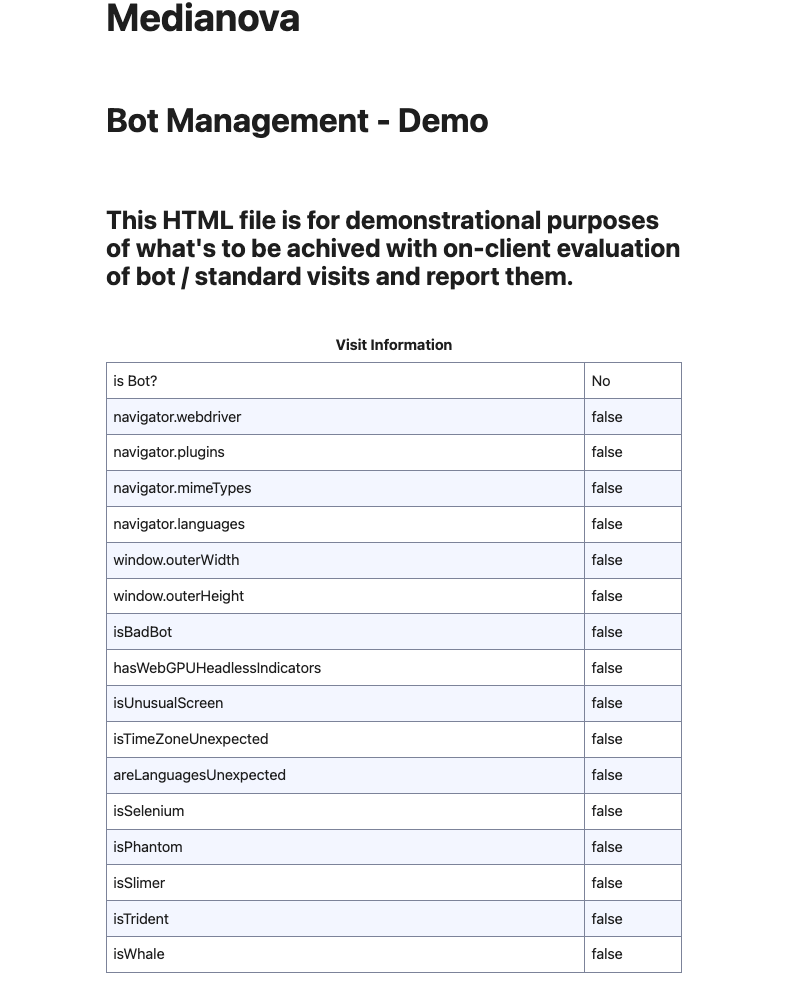

How it works
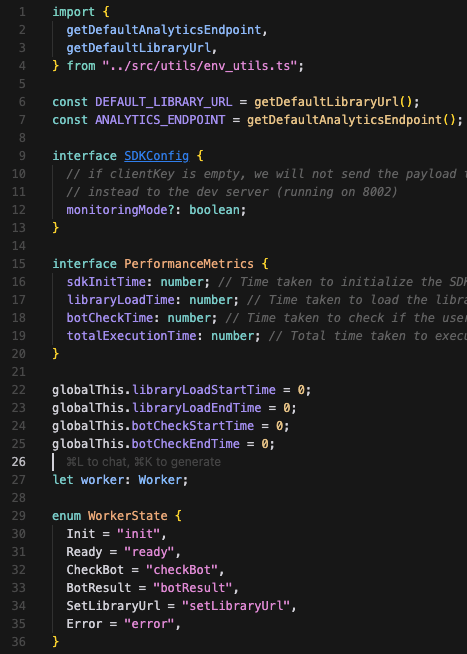
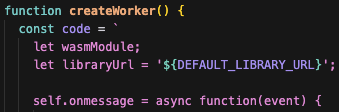
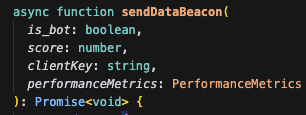
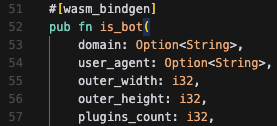
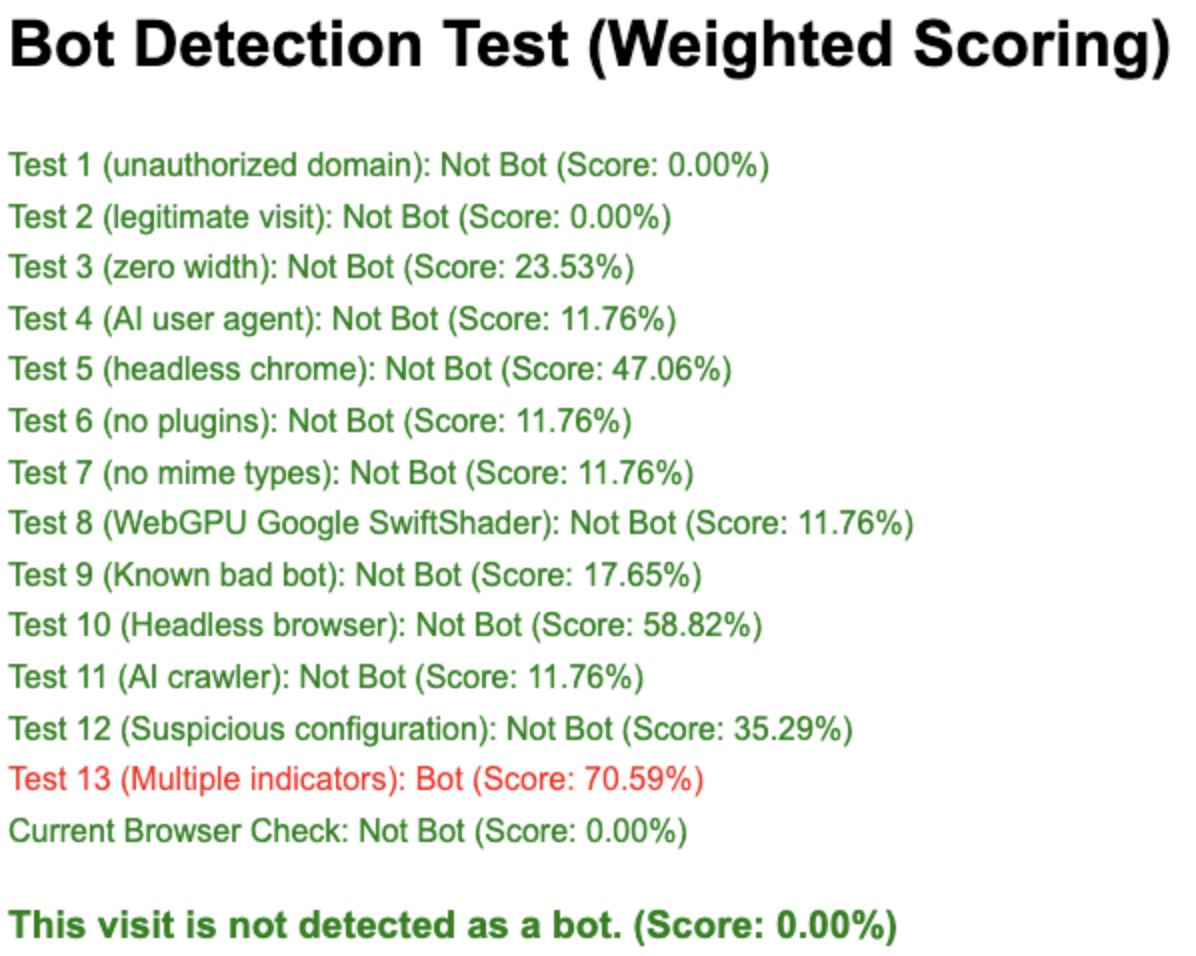
if Score > 60% then
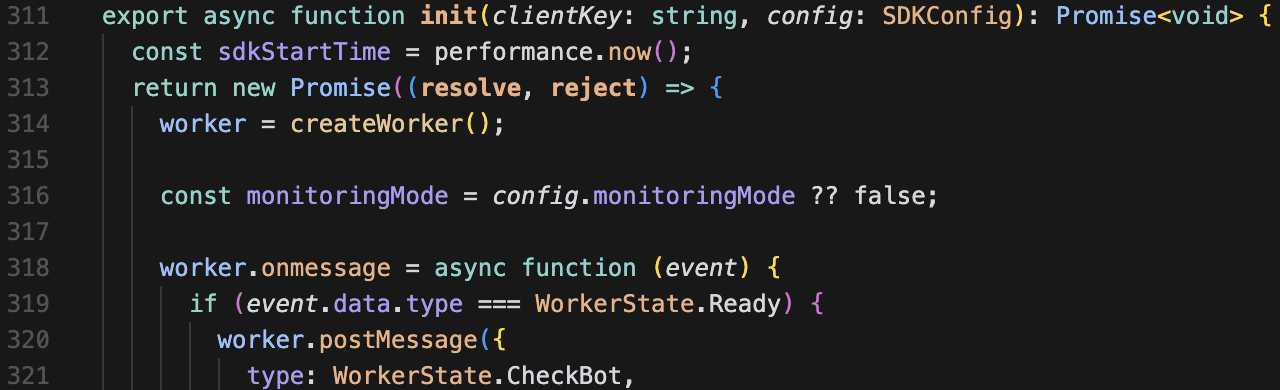
await init(clientKey, { monitoringMode });is_bot("example.com", "Mozilla/5.0", 1024, 768, 5, 10, "NVIDIA Corporation"), "example.com");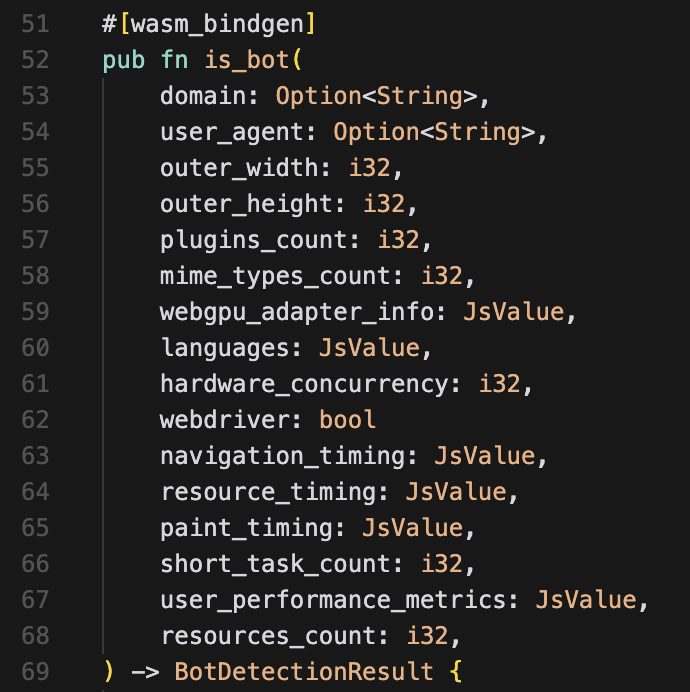
1.
Start with the hardest problem to solve: Get the simple result from the WASM Module
2.
Inlclude an e2e test on top of what's implemented to be run each time in the CI/CD
3.
Iterate until you've reached to the point that satisfies the first sprint goal
5.
Showcase how it works to the C-levels / Directors & get feedback
4.
Review the first sprint, collect what went well or wrong and apply in the upcoming iteration
6.
Start the next sprint with the whole outcome and feedback collected
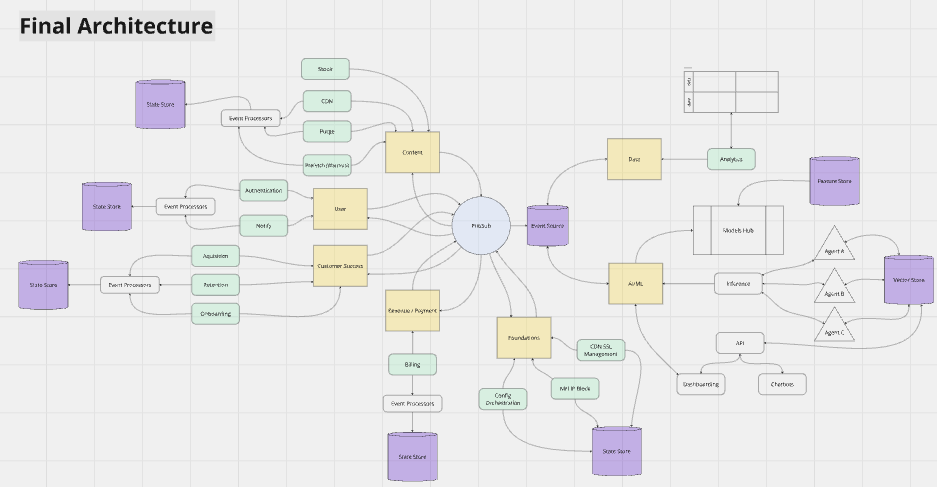
How It Looks Like
from a Bird-Eye View
1.
Send the payload to the Collector Service and transform data into its expected shape
2.
Streamline the analytics to the Bot Management Service and persist
3.
Trigger a CDC (Change Data Capture) & publish the data through the event bus
5.
Trigger CDC to let BFF (Backend-for-Frontend) Service know what's updated & persist it for analytics / dashboard purposes
4.
Capture the sanitized data published to a topic, persist it within the Bot Management Service
6.
Ping the whatever client it is listened from with SSE (Server-sent Events)
— for the Service Orchestration
right tools for the right job!
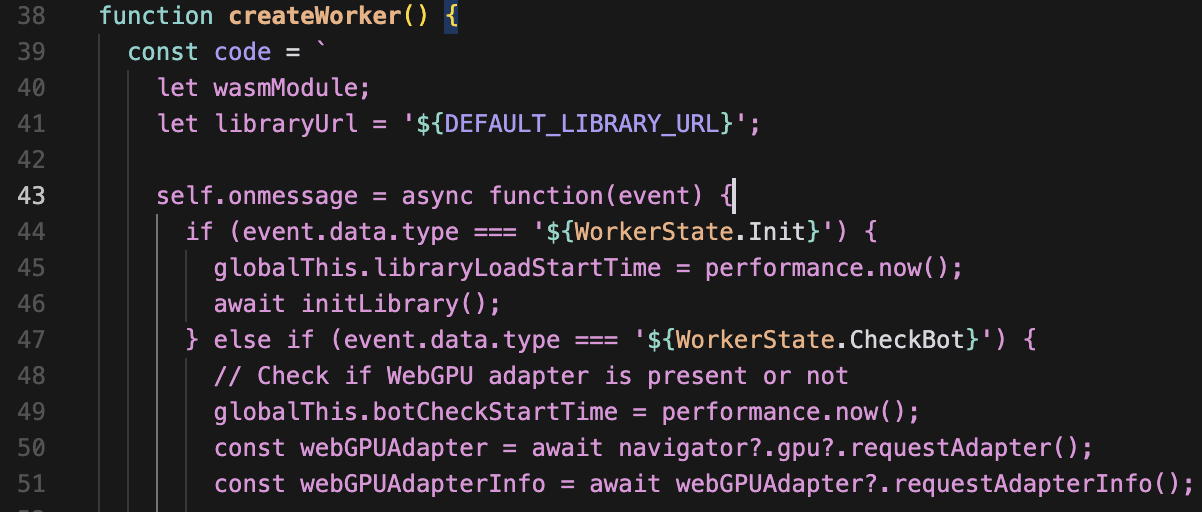
WebWorkers
https://developer.mozilla.org/en-US/docs/Web/API/Web_Workers_API
sendBeacon
https://developer.mozilla.org/en-US/docs/Web/API/Navigator/sendBeacon
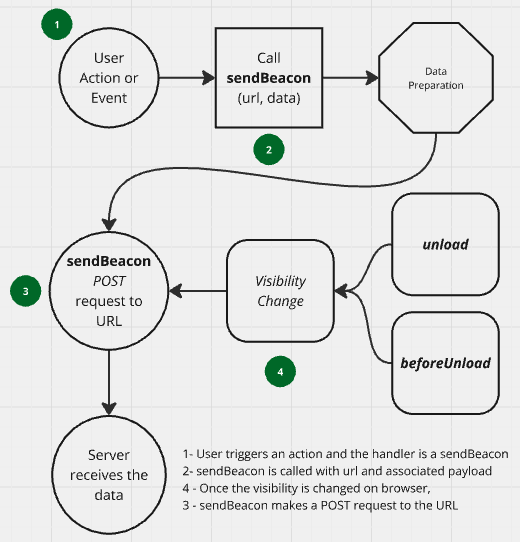
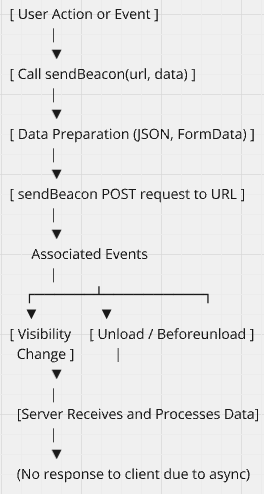
sendBeacon
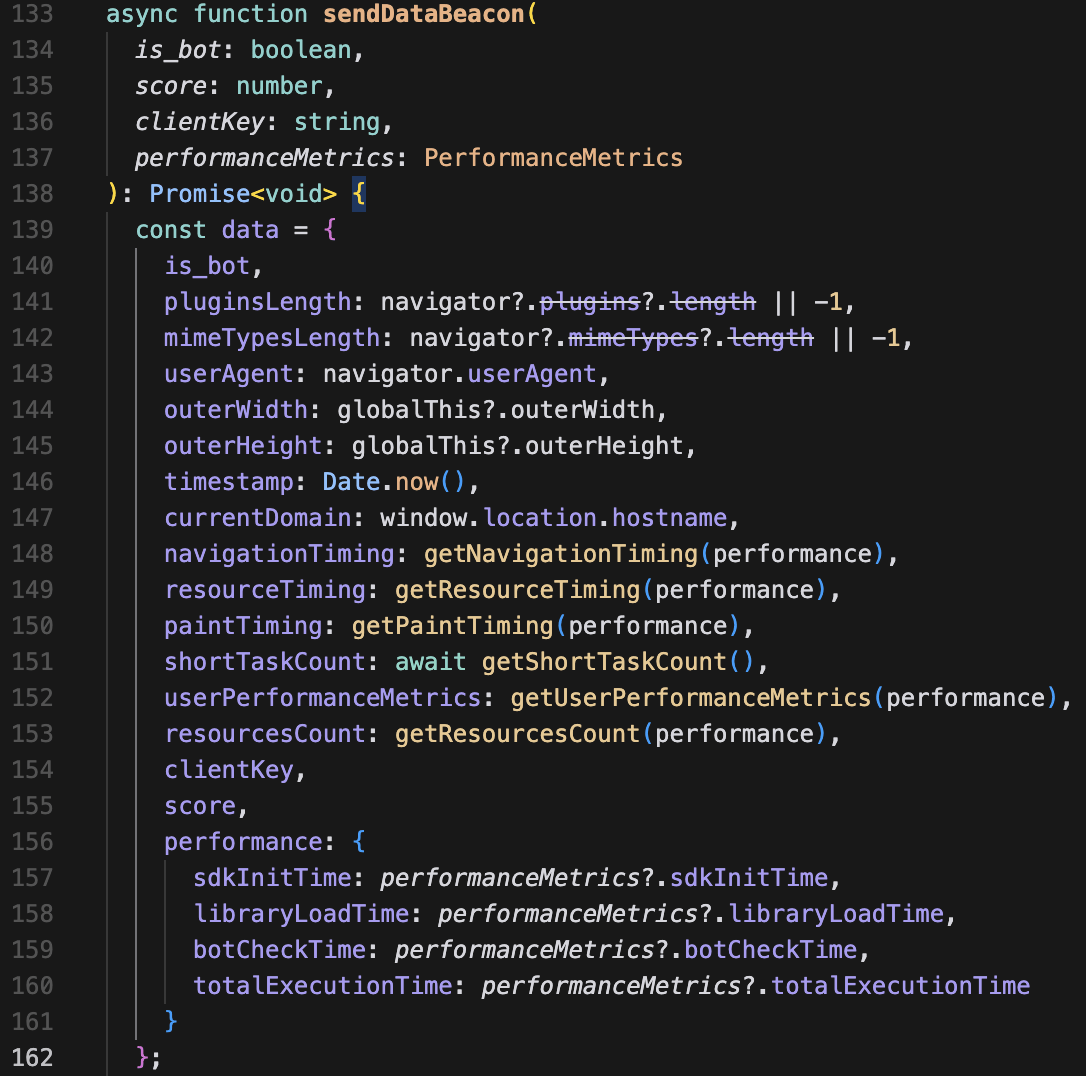
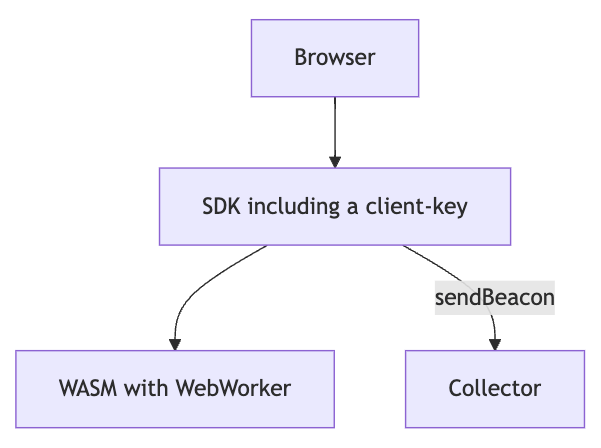
The most optimum client-side performance 🤗
"culturing" for the job!
— for the Cultural Transformation
Service Orchestration & Cultural Transformation

Vertical Slicing
Event-driven Approach
Trunk-based
Start first, make it better, and make the best!
Everything is events!
Go live immediately, activate later!
now it is used in ~2M websites


Key Takeaways
- Start small with wasm-pack 👌🏽
- Make sure if you have a caching mechanism provided by a CDN 🫙
- Streamline development first to the deployment with a proper but simple CI/CD ♻️
Key Takeaways
- Write only needed e2e tests first 🔍
- Don't use any tooling before observing them reaching v1.0.0. for WASM. 🙏🏽
- Production-ready WASM takes time, estimate gracefully.
- Have fun! 🎉
THANK YOU!
Contact me via email or Linkedin if you have any questions or interested in how to build apps with WebAssembly.

WASMIO/25 - The Silent Sentinel: Rust-Powered WASM for Lightning-Fast Bot Detection at the Edge
By Barış Güler
WASMIO/25 - The Silent Sentinel: Rust-Powered WASM for Lightning-Fast Bot Detection at the Edge
- 454



