Reverse Engineering 1
講師: ItisCaleb
What is Reverse
順向工程
思路->原始碼->成品
逆向工程
成品->原始碼->思路
Why Reverse
Why Reverse
- 破解軟體
- 寫外掛
- 研究惡意軟體
- 當純想看在幹嘛
How to Reverse
靜態分析
靜態分析
不將程式跑起來,而直接從binary來分析
使用 Desassmbler(反組譯) 或是 Decompiler (反編譯) 來分析
- objdump 反組譯器
- Ghidra/IDA 反編譯器
- dnSpy 反編譯 C#
- jadx 反編譯 Java
- PE bear 分析 PE file
- etc.
靜態分析
動態分析
將程式實際跑起來
透過 Debugger (除錯器)觀察他的行為(呼叫函式的參數、記憶體)
動態分析
- gdb Linux 的 debugger
- x64dbg Windows 的 debugger
Basic review
資料型態
1 bit = 1/0
1 byte = 8 bits = 1 char
1 word = 2 bytes = 1 short
1 dword = 4 bytes = 1 int
1 qword = 8 bytes = 1 long int
資料型態(ARM)
1 bit = 1/0
1 byte = 8 bits
1 word = 4 bytes = 1 int
1 dword = 8 bytes = 1 long int
編譯過程
hello.c
hello.i
hello.s
hello.o
hello
*.obj
library
preprocessor
compiler
assembler
linker
執行過程
hello
memory
loader
execute
find entrypoint
X86 Instruction
Registers
| AH | AL | ||
| BH | BL | ||
| CH | CL | ||
| DH | DL |
63 32 31 16 15 8 7 0
| BP | ||
| SP | ||
| SI | ||
| DI |
| IP |
| 64 bits | 32 bits | 16 bits |
|---|---|---|
| RAX | EAX | AX |
| RBX | EBX | BX |
| RCX | ECX | CX |
| RDX | EDX | DX |
| RBP | EBP | BP |
| RSP | ESP | SP |
| RSI | ESI | SI |
| RDI | EDI | DI |
| RIP | EIP | IP |
General purpose
Stack pointer
Stack Base pointer
Program counter
Registers
Additional register r8 ~ r16 in x86-64
Register(Eflags)
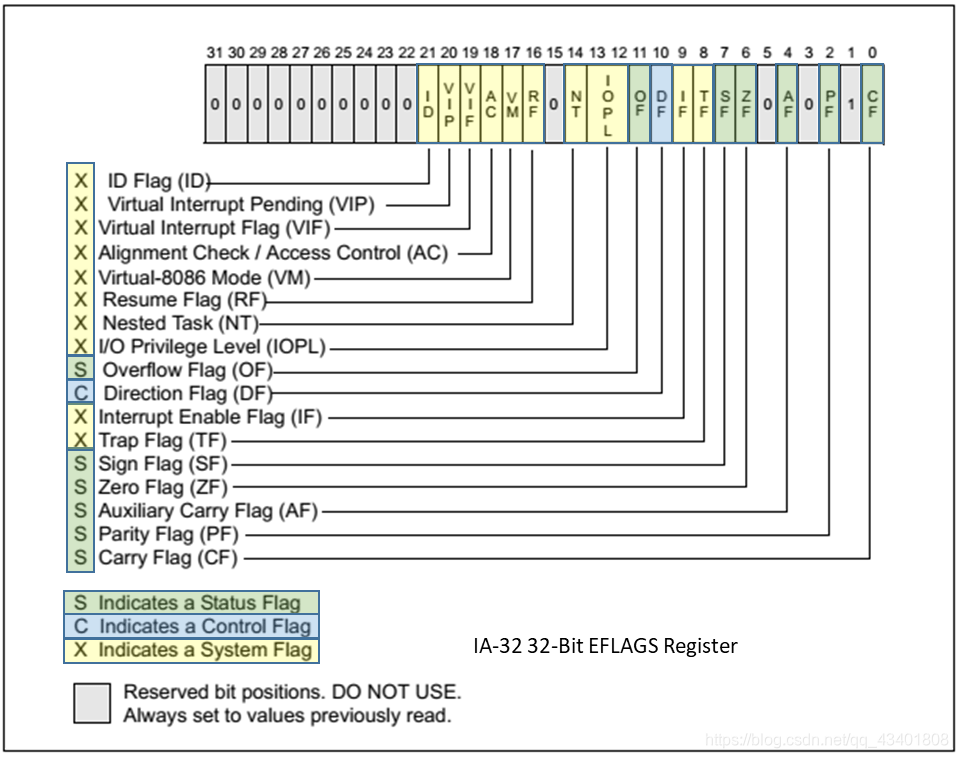
Register(Eflags)
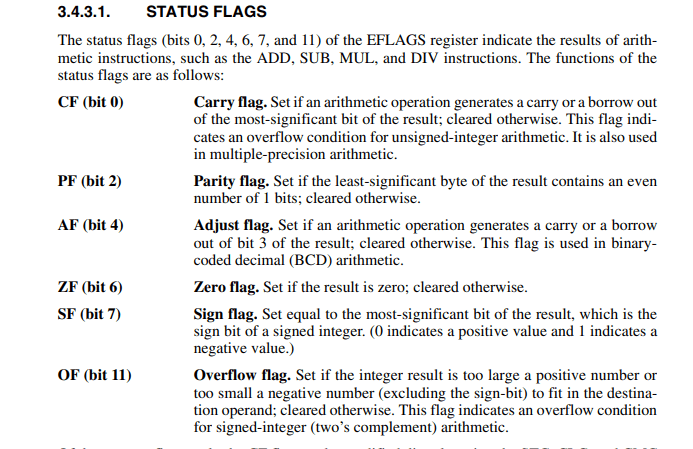
Instructions
// move
mov rax, rbx // rax = rbx
mov rax, dword ptr [rbx] // int rax = *(int*)rbx
// load effective address
lea rax, [0xdeadbeef] // rax = 0xdeadbeef
lea rax, [rbx*4+0x10] // rax = rbx*4+0x10
Instructions
// arithmetic
add rax, rbx // rax += rbx
sub rax, rbx // rax -= rbx
inc rax // rax++
dec rax // rax--
shr rax, 1 // rax = rax >> 1
shl rax, 1 // rax = rax << 1
// logic
and rax, rbx // rax &= rbx
or rax, rbx // rax |= rbx
xor rax, rbx // rax ^= rbx
not rax // rax = !rax
Instructions
mov rax, 7
mov rbx, 6
sub rax, rbx // 7 - 6 ZF=0 CF=0
sub rax, rbx // 1 - 6 ZF=0 CF=1
mov rax, 5
sub rax, rax // 5 - 5 ZF=1 CF=0Instructions
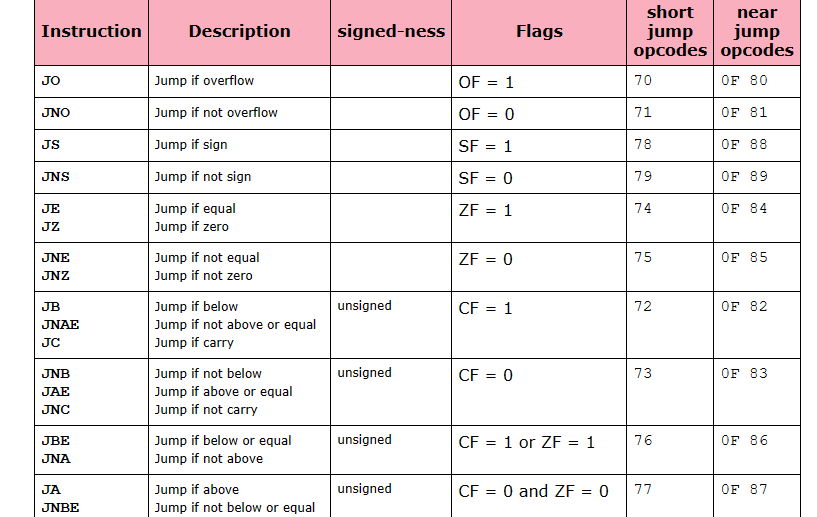
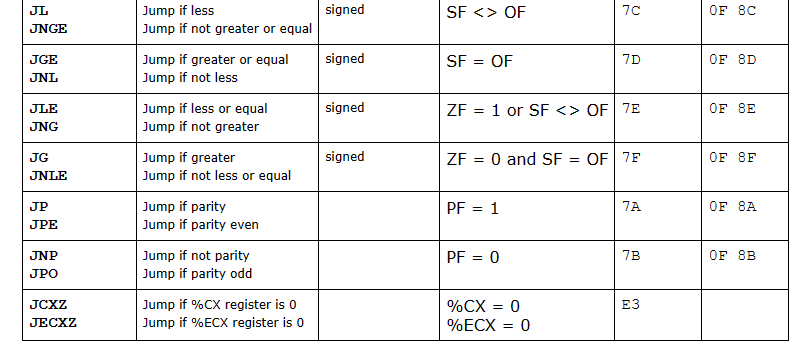
x86 vs ARM
// Intel
mov rax, 11
mov rax, rbx
add rax, rbx
sub rax, 12
// op <dst> <src>
// rax = 11
// AT&T
movl $11, %rax
mov %rbx, %rax
add %rbx, %rax
subl $12, %rax
// op <src> <dst>
// 11 -> raxTools
Ghidra

Ghidra
- 開源
- 免費(沒錢買IDA)
- 反組譯/反編譯
- 定義 struct
- 改函數名
- plugin
GDB
- Linux 使用的除錯器
- CLI
- 強大
- 設中斷點
- 查看記憶體
apt install gdbGDB
- b 設中斷點
- r 執行程式
- c 繼續執行
- disas 看反組譯
- si 步入指令
- ni 步過指令
- x 查看記憶體
x64dbg
其他資源
Reverse Engineering 1
By ItisCaleb (Caleb)
Reverse Engineering 1
- 127



