DevOps
cloud

Problemáticas
Azure DevOps
Rebase automation
jenkins
pipelines
terraform
terratest
liquibase
bdd

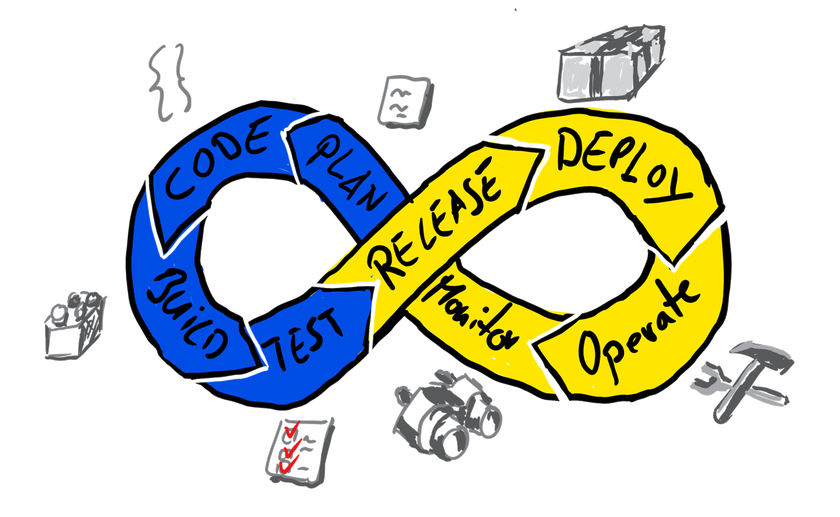
DevOps
Problematicas

- Visual Studio Team Services

- Creacion de recursos Manual
- Agentes Azure DevOps
- Generacion imagenes virtual machine
- Versionamiento de productos
- etc........
- Bases de Datos... scripts


- Creacion de recursos Manual

Resource Group
App Service
Rebase 1
Rebase 2

Settigns AppService

Resource Group

App Service

Settigns AppService
Storage Account
Rebase 10

Resource Group

App Service

Settigns AppService

Storage Account
Key Vault

Database 1

Database 2

Slot

Storage Account 2
Traffic manager

Settigns AppService Slot
Azure DevOps

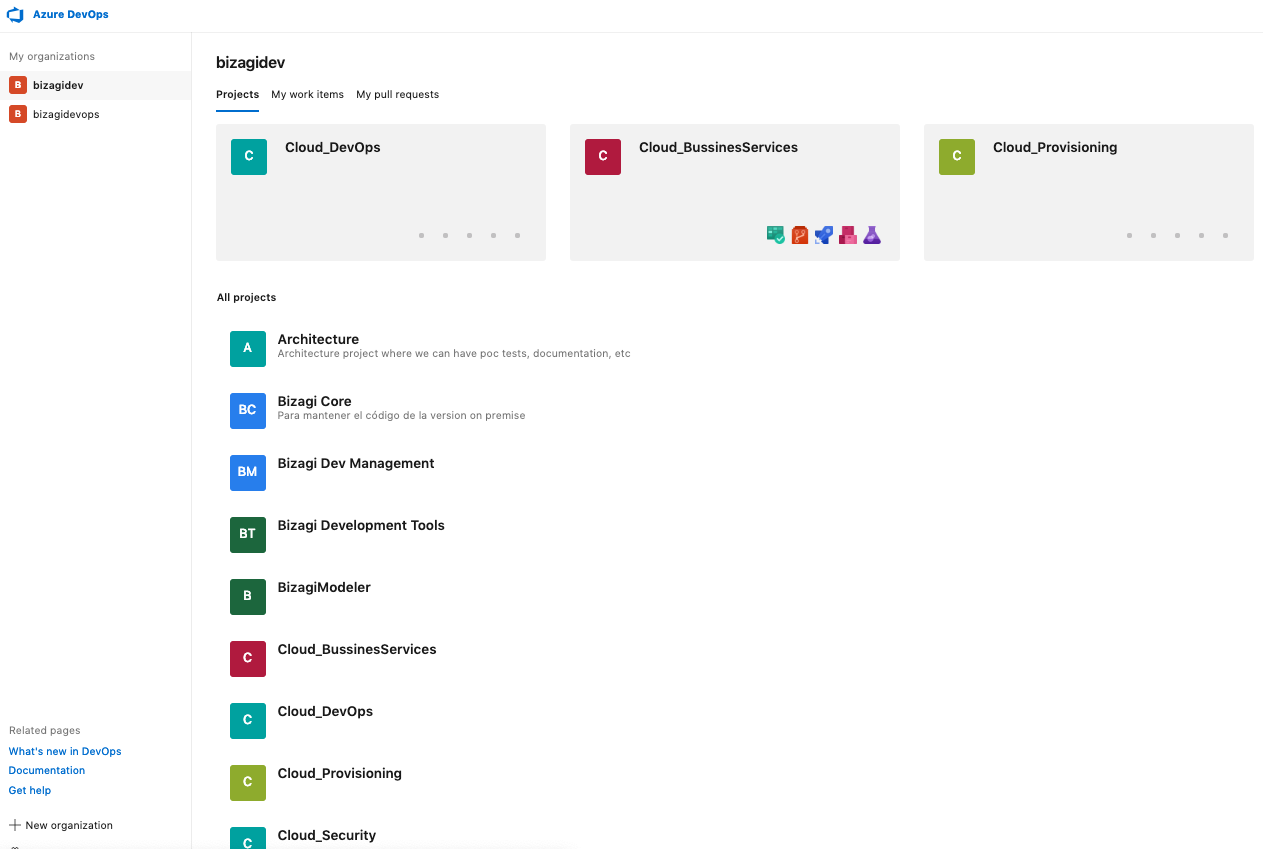
Proyectos cloud

Agentes

Build
que utilizamos?
Ciclo Proyecto Cloud. - Version Manager

Code
Dev



BUILD
Version Manager

Storage Account
RELEASE
Productos
Rebase Automation


REBASE AUTOMATION
- PIPELINES
- TERRAFORM
- Modulos
- Terratest
- LIQUIBASE
- INTEGRATION TEST
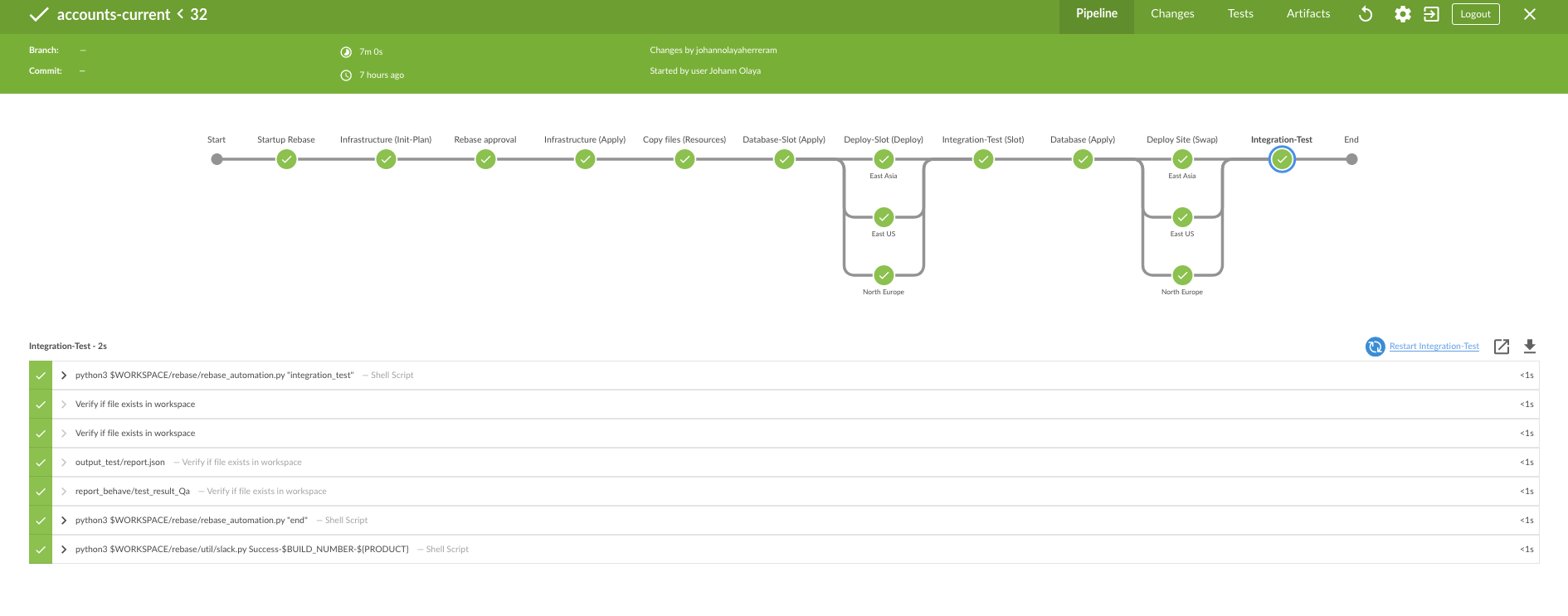
JENKINS Y PIPELINES

Servidor automatizacion Open Source
PIPELINE
Que es?
define el ciclo de vida de las aplicaciones mediante flujos
En que esta hecho
Ventajas
Crear flujos complejos y sencillos de entender para CI
Sobreviven a reinicios de servidor
Pausados... esperan a acciones para continuar flujo
NODOS
python


REBASE AUTOMATION

STEP
Tareas o comandos del flujo de trabajo
NODE
Agrupacion de tareas que comparten un workspace
STAGE
Etapas logicas del flujo de trabajo. Cada stage puede estar compuesto por un conjunto de steps, y cada node puede contener un conjunto de stages
PIPELINES

pipeline {
parameters {
string(description: '', name: 'PRODUCT')
string(description: '', name: 'CHANNEL')
string(description: '', name: 'PLAN_CREDENTIALS')
}
environment {
FOLDER = "/tmp/${params.PRODUCT}-"
PLAN = "${plan}"
DEVOPS_CREDENTIALS = "${devops_credentials}"
PLAN_CREDENTIALS = "${plan_credentials}"
}
agent {label 'devops'}
stages {
stage('Startup Rebase') {
steps {
echo "Startup Rebase"
echo "${plan}"
echo sh(returnStdout: true, script: 'env')
withPythonEnv('python3') {
sh 'pip3 install azure'
sh 'pip3 install slacker'
sh 'python3 $WORKSPACE/rebase/rebase_automation.py "startup"'
}
}
}
stage('Rebase approval') {
input {
message "Rebase Automation: ${PRODUCT}"
ok "Yes."
}
steps {
echo "Hello, nice to meet you."
}
stage('Rebase approval') {
input {
message "Rebase Automation: ${PRODUCT}"
ok "Yes."
}
steps {
echo "Approval."
}
}
stage('Infrastructure (Apply)') {
steps {
withPythonEnv('python3') {
sh 'python3 $WORKSPACE/rebase/rebase_automation.py "apply"'
}
}
}
stage('Copy files (Resources)') {
steps {
withPythonEnv('python3') {
sh 'python3 $WORKSPACE/rebase/rebase_automation.py "resources"'
}
}
}
Configuracion de Productos
automation
manager

files-templates
rebase
source

database

infrastructure

integration test







2018.12.14.1
2018.12.14.2
2018.12.14.3
2018.12.14.4


Configuracion release azure devops

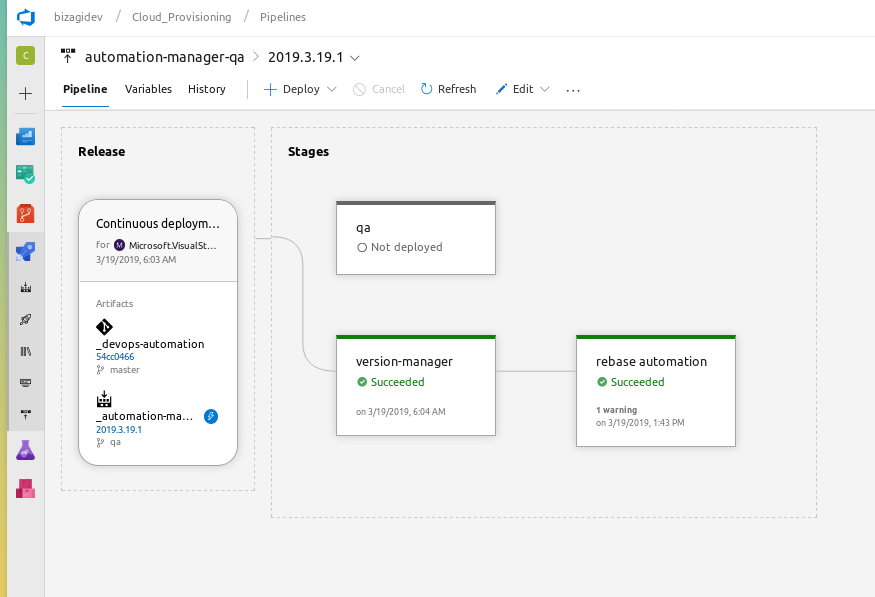
Azure DevOps
Plan de productos rebase automation

1

Entradas
Plan
Secret


Plan

Apply
Iniciar
Infra
Terraform

Salidas

Config
Copy Files


Slot
Database
Liquibase

Deploy
Deploy Slot


Test Intg
Cucumber



Site
Database
Liquibase

Deploy
Swap
Allure

Test Intg
Cucumber
Allure



Terraform

2
Terraform es una herramienta de orquestación de código abierto desarrollado por Hashicorp que nos permite definir nuestra infraestructura como código
- Administra infraestructuras considerablemente grandes o puede administrar una sola aplicación.
- Terraform no se limita a un proveedor en específico.
- Proporciona una sintaxis simple y unificada que permite administrar recursos
- Las configuraciones que se realizan en Terraform puede ser compartida y reutilizable.
- El modelo de su centro de datos puede ser versionado, de esta forma es más sencillo observar el progreso de nuestro servicio y controlar los cambios.
Terraform - Modulos

2
Init
Plan
Apply
Destroy
State Terraform

Container
variable "name_prefix_g" {
description = "unique part of the name to give to resources"
}
variable "channel_g" {
description = "describe channel of product"
}
variable "location_g" {
description = "region where the resources should exist"
}
variable "tier_sp" {
description = "tier service plan product"
}
variable "size_sp" {
description = "size service plan web app product"
}
variable "admin_username_db" {
description = "size service plan web app product"
}
variable "admin_password_db" {
description = "size service plan web app product"
}
variable "credential" {
type = "map"
}
variable "start_ip_address_sdb_biz" {
description = "ip range bizagi access"
}
variable "start_ip_address_sdb_jenkins" {
description = "ip server jenkins"
}
variable "start_ip_address_sdb_portal" {
description = "ip server portal"
}
variable "size_db" {
description = "size database"
}
variable "size_db_slot" {
description = "size database slot"
}
variable "account_replication_type" {
description = "type of replication to storage account"
}
variable "app_services_settings" {
type = "map"
}
variable "app_services_slot_settings" {
type = "map"
}
variable "access_key_aws" {
description = "aws acceskey"
}
variable "secret_key_aws" {
description = "aws secret"
}
variable "region_aws" {
description = "aws region"
}
variable "zone_id_aws" {
description = "aws zone hostedid aws"
}
variable "type_aws" {
description = "aws type register cname aws"
}
variable "ttl_aws" {
description = "aws register ttl"
}
variable "dns_app_aws" {
description = "aws register ttl"
}
variable "domain_biz_aws" {
description = "aws register ttl"
}
variable "key_vault_id" {
description = "key vault id"
}
variable "microsoft_web_objectid" {
description = "object id micropsoft web app"
}
variable "container_assets" {
description = ""
}
variable "container_dbbackups" {
description = ""
}
variable "container_jsonexecutions" {
description = ""
}
variable "container_jsontemplates" {
description = ""
}
variable "automationManagerProductInstanceQueueName" {
description = ""
}
variable "automationManagerProductInstanceQueueName_slot" {
description = ""
}
variable "product_instance_bizagi_paas_trial" {
description = ""
}
variable "product_instance_bizagi_paas_trial_slot" {
description = ""
}
variable "product_instance_queue_debug" {
description = ""
}
variable "product_instance_queue_debug_slot" {
description = ""
}
variable "run_baseline_client" {
description = ""
}
variable "run_baseline_client_slot" {
description = ""
}
variable "automationManagerAmazonAccessKey" {
description = ""
}
variable "automationManagerAmazonSecretKey" {
description = ""
}
variable "automationManagerSmtpPassword" {
description = ""
}
variable "bizagiGatewayToken" {
description = ""
}
variable "bizagiGatewayTokenSlot" {
description = ""
}
variable "automationManagerBizagiHostZoneId" {
description = ""
}
variable "releaseManagementStorageStringConnection" {
description = ""
}
provider "azurerm" {
subscription_id = "${var.credential["subscription_id"]}"
client_id = "${var.credential["client_id"]}"
client_secret = "${var.credential["client_secret"]}"
tenant_id = "${var.credential["tenant_id"]}"
}
provider "aws" {
access_key = "${var.access_key_aws}"
secret_key = "${var.secret_key_aws}"
region = "${var.region_aws}"
}
locals {
bizagi_database_template = "https://${azurerm_storage_account.sa.name}.blob.core.windows.net/dbbizagi/BizagiDatabaseTemplate-468.bacpac"
connection_string = "Server=tcp:${azurerm_sql_server.sdb.fully_qualified_domain_name},1433;Initial Catalog=${azurerm_sql_database.db.name};Persist Security Info=False;User ID=${azurerm_sql_server.sdb.administrator_login};Password=${azurerm_sql_server.sdb.administrator_login_password};MultipleActiveResultSets=False;Encrypt=True;TrustServerCertificate=False;Connection Timeout=30;"
connection_string_slot = "Server=tcp:${azurerm_sql_server.sdb.fully_qualified_domain_name},1433;Initial Catalog=${azurerm_sql_database.db_slot.name};Persist Security Info=False;User ID=${azurerm_sql_server.sdb.administrator_login};Password=${azurerm_sql_server.sdb.administrator_login_password};MultipleActiveResultSets=False;Encrypt=True;TrustServerCertificate=False;Connection Timeout=30;"
url_app = "${var.location_g}-app-${var.name_prefix_g}-${var.channel_g}"
azure_domain = "azurewebsites.net"
connection_string_storage = "DefaultEndpointsProtocol=https;AccountName=${azurerm_storage_account.sa.name};AccountKey=${azurerm_storage_account.sa.primary_access_key}"
instrumentation_key_app = "${azurerm_application_insights.app_ins.instrumentation_key}"
json_executions_container = "${var.container_jsonexecutions}"
client_id = "${var.credential["client_id"]}"
app_insights_instrumentation_key = "${azurerm_application_insights.app_ins.instrumentation_key}"
json_templates_container = "${var.container_jsontemplates}"
storage_string_connection = "${local.connection_string_storage}"
key_vault_base_url = "${azurerm_key_vault.kv.vault_uri}"
key_vault_base_url_slot = "${azurerm_key_vault.kv_slot.vault_uri}"
queue_name_run_baseline_client = "${var.automationManagerProductInstanceQueueName}"
queue_name_run_baseline_client_slot = "${var.automationManagerProductInstanceQueueName_slot}"
db_backups_container = "${var.container_dbbackups}"
client_secret = "${var.credential["client_secret"]}"
}
resource "random_id" "server" {
keepers = {
azi_id = 1
}
byte_length = 8
}
resource "random_id" "sa" {
keepers = {
azi_id = 1
}
byte_length = 8
}
resource "random_string" "key_vault_name" {
length = 2
special = false
override_special = "/@\" "
}
resource "azurerm_resource_group" "rg" {
name = "${var.location_g}-rg-${var.name_prefix_g}-${var.channel_g}"
location = "${var.location_g}"
}
resource "azurerm_app_service_plan" "sp" {
name = "${var.location_g}-sp-${var.name_prefix_g}-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
sku {
tier = "${var.tier_sp}"
size = "${var.size_sp}"
}
}
resource "azurerm_sql_server" "sdb" {
name = "${var.location_g}-sdb-${var.name_prefix_g}-${var.channel_g}"
resource_group_name = "${azurerm_resource_group.rg.name}"
location = "${var.location_g}"
version = "12.0"
administrator_login = "${var.admin_username_db}"
administrator_login_password = "${var.admin_password_db}"
tags {
environment = "${var.name_prefix_g}"
}
}
resource "azurerm_sql_firewall_rule" "bizagiacces" {
name = "FirewallRuleBizagi"
resource_group_name = "${azurerm_resource_group.rg.name}"
server_name = "${azurerm_sql_server.sdb.name}"
start_ip_address = "${var.start_ip_address_sdb_biz}"
end_ip_address = "${var.start_ip_address_sdb_biz}"
depends_on = [
"azurerm_sql_server.sdb"]
}
resource "azurerm_sql_firewall_rule" "jenkinsaccess" {
name = "FirewallRueJenkins"
resource_group_name = "${azurerm_resource_group.rg.name}"
server_name = "${azurerm_sql_server.sdb.name}"
start_ip_address = "${var.start_ip_address_sdb_jenkins}"
end_ip_address = "${var.start_ip_address_sdb_jenkins}"
depends_on = [
"azurerm_sql_server.sdb"]
}
resource "azurerm_sql_firewall_rule" "portalaccess" {
name = "FirewallRuePortal"
resource_group_name = "${azurerm_resource_group.rg.name}"
server_name = "${azurerm_sql_server.sdb.name}"
start_ip_address = "${var.start_ip_address_sdb_portal}"
end_ip_address = "${var.start_ip_address_sdb_portal}"
depends_on = [
"azurerm_sql_server.sdb"]
}
resource "azurerm_sql_firewall_rule" "azure_services" {
name = "AllowAllAzureService"
resource_group_name = "${azurerm_resource_group.rg.name}"
server_name = "${azurerm_sql_server.sdb.name}"
start_ip_address = "0.0.0.0"
end_ip_address = "0.0.0.0"
}
resource "azurerm_sql_database" "db" {
name = "${var.name_prefix_g}-db-${var.channel_g}"
resource_group_name = "${azurerm_resource_group.rg.name}"
location = "${var.location_g}"
server_name = "${azurerm_sql_server.sdb.name}"
requested_service_objective_name = "${var.size_db}"
depends_on = [
"azurerm_sql_server.sdb"]
}
resource "azurerm_sql_database" "db_slot" {
name = "${var.name_prefix_g}-db-${var.channel_g}-slot"
resource_group_name = "${azurerm_resource_group.rg.name}"
location = "${var.location_g}"
server_name = "${azurerm_sql_server.sdb.name}"
requested_service_objective_name = "${var.size_db_slot}"
depends_on = [
"azurerm_sql_server.sdb"]
}
resource "azurerm_app_service" "app" {
name = "${var.location_g}-app-${var.name_prefix_g}-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
app_service_plan_id = "${azurerm_app_service_plan.sp.id}"
site_config {
dotnet_framework_version = "v4.0"
scm_type = "LocalGit"
always_on = true
}
app_settings = "${merge(
map("APPINSIGHTS_INSTRUMENTATIONKEY",local.instrumentation_key_app),
map("automationManagerJsonExecutionsContainer",local.json_executions_container),
map("automationManagerAppInsightsInstrumentationKey",local.app_insights_instrumentation_key),
map("automationManagerJsonTemplatesContainer",local.json_templates_container),
map("automationManagerStorageStringConnection",local.storage_string_connection),
map("automationManagerKeyVaultBaseUrl",local.key_vault_base_url),
map("automationManagerProductInstanceQueueName",local.queue_name_run_baseline_client),
map("automationManagerDBbackupsContainer",local.db_backups_container),
map("automationManagerClientSecret",local.client_secret),
map("automationManagerClientId",local.client_id),
map("automationManagerBizagiDBTemplateStorage",local.bizagi_database_template),
var.app_services_settings)}"
connection_string {
name = "DefaultDatabase"
type = "SQLServer"
value = "${local.connection_string}"
}
connection_string {
name = "AzureWebJobsDashboard"
type = "SQLServer"
value = "${local.connection_string_storage}"
}
connection_string {
name = "AzureWebJobsStorage"
type = "SQLServer"
value = "${local.connection_string_storage}"
}
depends_on = [
"azurerm_sql_database.db",
"azurerm_storage_account.sa",
"azurerm_application_insights.app_ins"]
}
data "aws_route53_zone" "domain" {
zone_id = "${var.zone_id_aws}"
private_zone = true
}
resource "aws_route53_record" "aws-route" {
zone_id = "${data.aws_route53_zone.domain.zone_id}"
name = "${var.dns_app_aws}.${data.aws_route53_zone.domain.name}"
type = "${var.type_aws}"
ttl = "${var.ttl_aws}"
records = [
"${local.url_app}.azurewebsites.net"]
}
resource "azurerm_app_service_custom_hostname_binding" "binding_app" {
hostname = "${var.dns_app_aws}.${var.domain_biz_aws}"
app_service_name = "${azurerm_app_service.app.name}"
resource_group_name = "${azurerm_resource_group.rg.name}"
depends_on = [
"aws_route53_record.aws-route"]
}
resource "azurerm_app_service_slot" "app_slot" {
name = "slot"
app_service_name = "${azurerm_app_service.app.name}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
app_service_plan_id = "${azurerm_app_service_plan.sp.id}"
site_config {
dotnet_framework_version = "v4.0"
scm_type = "LocalGit"
always_on = true
}
app_settings = "${merge(
map("APPINSIGHTS_INSTRUMENTATIONKEY",local.instrumentation_key_app),
map("automationManagerJsonExecutionsContainer",local.json_executions_container),
map("automationManagerAppInsightsInstrumentationKey",local.app_insights_instrumentation_key),
map("automationManagerJsonTemplatesContainer",local.json_templates_container),
map("automationManagerStorageStringConnection",local.storage_string_connection),
map("automationManagerKeyVaultBaseUrl",local.key_vault_base_url_slot),
map("automationManagerProductInstanceQueueName",local.queue_name_run_baseline_client_slot),
map("automationManagerDBbackupsContainer",local.db_backups_container),
map("automationManagerClientSecret",local.client_secret),
map("automationManagerClientId",local.client_id),
map("automationManagerBizagiDBTemplateStorage",local.bizagi_database_template),
var.app_services_slot_settings)}"
connection_string {
name = "DefaultDatabase"
type = "SQLServer"
value = "${local.connection_string_slot}"
}
connection_string {
name = "AzureWebJobsDashboard"
type = "SQLServer"
value = "${local.connection_string_storage}"
}
connection_string {
name = "AzureWebJobsStorage"
type = "SQLServer"
value = "${local.connection_string_storage}"
}
depends_on = [
"azurerm_sql_database.db_slot","azurerm_key_vault.kv_slot"]
}
resource "aws_route53_record" "aws-route-slot" {
zone_id = "${data.aws_route53_zone.domain.zone_id}"
name = "${var.dns_app_aws}slot.${data.aws_route53_zone.domain.name}"
type = "${var.type_aws}"
ttl = "${var.ttl_aws}"
records = [
"${local.url_app}-slot.${local.azure_domain}"]
depends_on = [
"azurerm_app_service_slot.app_slot"]
}
data "template_file" "ssl_binding" {
template = "${file("ssl_binding.json")}"
vars {
service_plan_id = "${azurerm_app_service_plan.sp.id}"
app_service_name = "${azurerm_app_service.app.name}/${var.dns_app_aws}.${var.domain_biz_aws}"
app_service_slot_name = "${azurerm_app_service.app.name}/slot/${var.dns_app_aws}slot.${var.domain_biz_aws}"
key_vault_id = "${var.key_vault_id}"
}
}
resource "azurerm_template_deployment" "ssl_binding" {
name = "${var.location_g}-app-service-binding-${var.channel_g}"
resource_group_name = "${azurerm_resource_group.rg.name}"
deployment_mode = "Incremental"
template_body = "${data.template_file.ssl_binding.rendered}"
depends_on = [
"azurerm_app_service_slot.app_slot",
"azurerm_app_service.app",
"aws_route53_record.aws-route",
"aws_route53_record.aws-route-slot"]
}
resource "azurerm_storage_account" "sa" {
name = "${random_id.sa.hex}"
resource_group_name = "${azurerm_resource_group.rg.name}"
location = "${azurerm_resource_group.rg.location}"
account_tier = "Standard"
account_replication_type = "${var.account_replication_type}"
}
resource "azurerm_storage_container" "assets_sa" {
name = "${var.container_assets}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "dbbackups_sa" {
name = "${var.container_dbbackups}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "jsonexecutions_sa" {
name = "${var.container_jsonexecutions}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "jsontemplates_sa" {
name = "${var.container_jsontemplates}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_queue" "queuerunclient_sa" {
name = "${var.automationManagerProductInstanceQueueName}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunclient_sa_slot" {
name = "${var.automationManagerProductInstanceQueueName_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuepaastrial_sa" {
name = "${var.product_instance_bizagi_paas_trial}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuepaastrial_sa_slot" {
name = "${var.product_instance_bizagi_paas_trial_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queueinstancedebug_sa" {
name = "${var.product_instance_queue_debug}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queueinstancedebug_sa_slot" {
name = "${var.product_instance_queue_debug_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunbaseclient_sa" {
name = "${var.run_baseline_client}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunbaseclient_sa_slot" {
name = "${var.run_baseline_client_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_application_insights" "app_ins" {
name = "${var.location_g}-ins-${var.name_prefix_g}-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
application_type = "Web"
}
resource "azurerm_key_vault" "kv" {
name = "${var.location_g}-kv-rm-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
sku {
name = "standard"
}
tenant_id = "${var.credential["tenant_id"]}"
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.credential["object_id"]}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.microsoft_web_objectid}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
enabled_for_disk_encryption = true
}
resource "azurerm_key_vault_secret" "secret_01" {
name = "automationManagerAmazonAccessKey"
value = "${var.automationManagerAmazonAccessKey}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_02" {
name = "automationManagerAmazonSecretKey"
value = "${var.automationManagerAmazonSecretKey}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_03" {
name = "automationManagerSmtpPassword"
value = "${var.automationManagerSmtpPassword}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_04" {
name = "bizagiGatewayToken"
value = "${var.bizagiGatewayToken}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_05" {
name = "certificateClientId"
value = "${local.client_id}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_06" {
name = "certificateClientSecret"
value = "${local.client_secret}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_07" {
name = "automationManagerBizagiHostZoneId"
value = "${var.automationManagerBizagiHostZoneId}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_08" {
name = "releaseManagementStorageStringConnection"
value = "${var.releaseManagementStorageStringConnection}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault" "kv_slot" {
name = "${var.location_g}-kv-rm-${var.channel_g}-slot"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
sku {
name = "standard"
}
tenant_id = "${var.credential["tenant_id"]}"
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.credential["object_id"]}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.microsoft_web_objectid}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
enabled_for_disk_encryption = true
}
resource "azurerm_key_vault_secret" "secret_01_slot" {
name = "automationManagerAmazonAccessKey"
value = "${var.automationManagerAmazonAccessKey}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_02_slot" {
name = "automationManagerAmazonSecretKey"
value = "${var.automationManagerAmazonSecretKey}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_03_slot" {
name = "automationManagerSmtpPassword"
value = "${var.automationManagerSmtpPassword}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_04_slot" {
name = "bizagiGatewayToken"
value = "${var.bizagiGatewayTokenSlot}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_05_slot" {
name = "certificateClientId"
value = "${local.client_id}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_06_slot" {
name = "certificateClientSecret"
value = "${local.client_secret}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_07_slot" {
name = "automationManagerBizagiHostZoneId"
value = "${var.automationManagerBizagiHostZoneId}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_08_slot" {
name = "releaseManagementStorageStringConnection"
value = "${var.releaseManagementStorageStringConnection}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
terraform {
backend "azurerm" {}
}
output "app_service_name" {
value = "${azurerm_app_service.app.name}"
depends_on = [
"azurerm_app_service.app.name"]
}
output "app_service_slot_name" {
value = "${azurerm_app_service_slot.app_slot.name}"
depends_on = [
"azurerm_app_service_slot.app_slot.name"]
}
output "key_vault_name" {
value = "${azurerm_key_vault.kv.name}"
depends_on = [
"azurerm_key_vault.kv"]
}
output "key_vault_name_slot" {
value = "${azurerm_key_vault.kv_slot.name}"
depends_on = [
"azurerm_key_vault.kv_slot"]
}
output "server_db_name" {
value = "${azurerm_sql_server.sdb.name}"
depends_on = [
"azurerm_sql_server.sdb"]
}
output "database_db_name" {
value = "${azurerm_sql_database.db.name}"
depends_on = [
"azurerm_sql_database.db"]
}
output "database_db_slot_name" {
value = "${azurerm_sql_database.db_slot.name}"
depends_on = [
"azurerm_sql_database.db_slot"]
}
output "connection_string_appservice" {
value = "Server=tcp:${azurerm_sql_server.sdb.fully_qualified_domain_name},1433;Initial Catalog=${azurerm_sql_database.db.name};Persist Security Info=False;User ID=${azurerm_sql_server.sdb.administrator_login};Password=${azurerm_sql_server.sdb.administrator_login_password};MultipleActiveResultSets=False;Encrypt=True;TrustServerCertificate=False;Connection Timeout=30;"
depends_on = [
"azurerm_sql_database.db"]
}
output "connection_string_base" {
value = "jdbc:sqlserver://${azurerm_sql_server.sdb.fully_qualified_domain_name}:1433;database=${azurerm_sql_database.db.name};"
depends_on = [
"azurerm_sql_database.db"]
}
output "connection_string_slot" {
value = "jdbc:sqlserver://${azurerm_sql_server.sdb.fully_qualified_domain_name}:1433;database=${azurerm_sql_database.db_slot.name};"
depends_on = [
"azurerm_sql_database.db_slot"]
}
output "user_db_base" {
value = "${azurerm_sql_server.sdb.administrator_login}"
depends_on = [
"azurerm_sql_database.db"]
}
output "password_db_base" {
value = "${azurerm_sql_server.sdb.administrator_login_password}"
depends_on = [
"azurerm_sql_database.db"]
}
output "instrumentation_key_app" {
value = "${azurerm_application_insights.app_ins.instrumentation_key}"
}
output "storage_account_name" {
value = "${azurerm_storage_account.sa.name}"
}
output "storage_account_key" {
value = "${azurerm_storage_account.sa.primary_access_key}"
}
output "resource_group_name" {
value = "${azurerm_resource_group.rg.name}"
}
output "app_slot_name" {
value = "${azurerm_app_service_slot.app_slot.name}"
}
935 lines
Terraform - Modulos

2
resource "azurerm_resource_group" "rg" {
name = "${var.location}-rg-${var.prefix_rs}-${var.channel_g}"
location = "${var.location}"
}
locals {
local_kv_secrets="${merge(
map("certificateClientId",var.credential["client_id"]),
map("certificateClientSecret",var.credential["client_secret"]),
var.kv_secrets)}"
local_kv_secrets_slot="${merge(
map("certificateClientId",var.credential["client_id"]),
map("certificateClientSecret",var.credential["client_secret"]),
var.kv_secrets_slot)}"
local_policy_object="${concat(
list(var.credential["object_id"]),
list(var.microsoft_web_objectid),
var.policy_object)}"
local_app_setings="${merge(
map("automationManagerStorageStringConnection",module.rb-storage-account-basic.sa_connection),
map("automationManagerKeyVaultBaseUrl",module.rb-key-vault-basic.kv_url_base),
map("automationManagerClientSecret",var.credential["client_secret"]),
map("automationManagerClientId",var.credential["client_id"]),
var.app_settings)}"
local_app_setings_slot="${merge(
map("automationManagerStorageStringConnection",module.rb-storage-account-basic.sa_connection),
map("automationManagerKeyVaultBaseUrl",module.rb-key-vault-basic-slot.kv_url_base),
map("automationManagerClientSecret",var.credential["client_secret"]),
map("automationManagerClientId",var.credential["client_id"]),
var.app_settings_slot)}"
local_db_connection_app_base={
name = "DefaultDatabase"
type = "SQLServer"
value = "${module.rb-server-database-basic.db_connection_app_base}"
}
local_db_connection_app_slot={
name = "DefaultDatabase"
type = "SQLServer"
value = "${module.rb-server-database-basic.db_connection_app_slot}"
}
local_db_connection_sa_02={
name = "AzureWebJobsDashboard"
type = "SQLServer"
value = "${module.rb-storage-account-basic.sa_connection}"
}
local_db_connection_sa_03={
name = "AzureWebJobsStorage"
type = "SQLServer"
value = "${module.rb-storage-account-basic.sa_connection}"
}
}
module "rb-key-vault-basic" {
source="git::https://github.com/bizagiengineering/terraform-modules.git//key-vault-basic"
prefix_rs="${var.prefix_rs}"
channel_g="${var.channel_g}"
location="${var.location}"
rg_name="${azurerm_resource_group.rg.name}"
credential="${var.credential}"
kv_secrets="${local.local_kv_secrets}"
kv_sku = "${var.kv_sku}"
policy_object="${local.local_policy_object}"
}
module "rb-key-vault-basic-slot" {
source="git::https://github.com/bizagiengineering/terraform-modules.git//key-vault-basic"
prefix_rs="${var.prefix_rs}"
channel_g="${var.channel_g}-slot"
location="${var.location}"
rg_name="${azurerm_resource_group.rg.name}"
credential="${var.credential}"
kv_secrets="${local.local_kv_secrets_slot}"
kv_sku = "${var.kv_sku}"
policy_object="${local.local_policy_object}"
}
module "rb-server-database-basic" {
source="git::https://github.com/bizagiengineering/terraform-modules.git//server-database-basic"
prefix_rs="${var.prefix_rs}"
channel_g="${var.channel_g}"
rg_name="${azurerm_resource_group.rg.name}"
location="${var.location}"
db_user="${var.db_user}"
db_password="${var.db_password}"
db_size="${var.db_size}"
db_size_slot="${var.db_size_slot}"
sdb_firewall_ips="${var.sdb_firewall_ips}"
}
module "rb-storage-account-basic" {
source = "git::https://github.com/bizagiengineering/terraform-modules.git//storage-account-basic"
prefix_rs = "${var.prefix_rs}"
channel_g = "${var.channel_g}"
location = "${var.location}"
rg_name = "${azurerm_resource_group.rg.name}"
sa_tier = "${var.sa_tier}"
sa_replication_type = "${var.sa_replication_type}"
sa_containers="${var.sa_containers}"
sa_queues="${var.sa_queues}"
sa_tables="${var.sa_tables}"
}
module "rb-webapp-basic" {
source="git::https://github.com/bizagiengineering/terraform-modules.git//webapp-basic"
rg_name="${azurerm_resource_group.rg.name}"
prefix_rs="${var.prefix_rs}"
channel_g="${var.channel_g}"
location="${var.location}"
sp_tier="${var.sp_tier}"
sp_size="${var.sp_size}"
app_tls_version="${var.app_min_tls_version}"
app_settings="${local.local_app_setings}"
app_settings_slot = "${local.local_app_setings_slot}"
connection_01="${local.local_db_connection_app_base}"
connection_02="${local.local_db_connection_sa_02}"
connection_03="${local.local_db_connection_sa_03}"
connection_slot_01="${local.local_db_connection_app_slot}"
connection_slot_02="${local.local_db_connection_sa_02}"
connection_slot_03="${local.local_db_connection_sa_03}"
}
module "rb-dns_binding" {
source = "git::https://github.com/bizagiengineering/terraform-modules.git//dns-binding"
prefix_rs = "${var.prefix_rs}"
channel_g = "${var.channel_g}"
location = "${var.location}"
rg_name = "${azurerm_resource_group.rg.name}"
aws_zone_id="${var.aws_zone_id}"
app_dns="${var.app_dns}"
aws_ttl="${var.aws_ttl}"
aws_type="${var.aws_type}"
app_url="${module.rb-webapp-basic.app_name}"
aws_domain_bizagi="${var.aws_domain_bizagi}"
app_name="${module.rb-webapp-basic.app_name}"
app_name_slot="${module.rb-webapp-basic.app_slot_name}"
key_vault_id="${var.key_vault_id}"
sp_id="${module.rb-webapp-basic.sp_id}"
}
data "template_file" "ssl_binding" {
template = "${file("ssl_binding.json")}"
vars {
service_plan_id = "${module.rb-webapp-basic.sp_id}"
app_service_name = "${module.rb-webapp-basic.app_name}/${var.app_dns}.${var.aws_domain_bizagi}"
app_service_slot_name = "${module.rb-webapp-basic.app_name}/slot/${var.app_dns}slot.${var.aws_domain_bizagi}"
key_vault_id = "${var.key_vault_id}"
}
}
resource "azurerm_template_deployment" "ssl_binding" {
name = "${var.location}-app-service-binding-${var.channel_g}"
resource_group_name = "${azurerm_resource_group.rg.name}"
deployment_mode = "Incremental"
template_body = "${data.template_file.ssl_binding.rendered}"
depends_on = ["module.rb-webapp-basic"]
}
terraform {
backend "azurerm" {}
}
162 lines
935 lines
Terraform - Modulos

2
resource "azurerm_storage_account" "sa" {
name = "${random_id.sa.hex}"
resource_group_name = "${azurerm_resource_group.rg.name}"
location = "${azurerm_resource_group.rg.location}"
account_tier = "Standard"
account_replication_type = "${var.account_replication_type}"
}
resource "azurerm_storage_container" "assets_sa" {
name = "${var.container_assets}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "dbbackups_sa" {
name = "${var.container_dbbackups}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "jsonexecutions_sa" {
name = "${var.container_jsonexecutions}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_container" "jsontemplates_sa" {
name = "${var.container_jsontemplates}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
container_access_type = "private"
}
resource "azurerm_storage_queue" "queuerunclient_sa" {
name = "${var.automationManagerProductInstanceQueueName}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunclient_sa_slot" {
name = "${var.automationManagerProductInstanceQueueName_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuepaastrial_sa" {
name = "${var.product_instance_bizagi_paas_trial}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuepaastrial_sa_slot" {
name = "${var.product_instance_bizagi_paas_trial_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queueinstancedebug_sa" {
name = "${var.product_instance_queue_debug}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queueinstancedebug_sa_slot" {
name = "${var.product_instance_queue_debug_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunbaseclient_sa" {
name = "${var.run_baseline_client}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_storage_queue" "queuerunbaseclient_sa_slot" {
name = "${var.run_baseline_client_slot}"
resource_group_name = "${azurerm_resource_group.rg.name}"
storage_account_name = "${azurerm_storage_account.sa.name}"
}
resource "azurerm_application_insights" "app_ins" {
name = "${var.location_g}-ins-${var.name_prefix_g}-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
application_type = "Web"
}
resource "azurerm_key_vault" "kv" {
name = "${var.location_g}-kv-rm-${var.channel_g}"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
sku {
name = "standard"
}
tenant_id = "${var.credential["tenant_id"]}"
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.credential["object_id"]}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.microsoft_web_objectid}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
enabled_for_disk_encryption = true
}
resource "azurerm_key_vault_secret" "secret_01" {
name = "automationManagerAmazonAccessKey"
value = "${var.automationManagerAmazonAccessKey}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_02" {
name = "automationManagerAmazonSecretKey"
value = "${var.automationManagerAmazonSecretKey}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_03" {
name = "automationManagerSmtpPassword"
value = "${var.automationManagerSmtpPassword}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_04" {
name = "bizagiGatewayToken"
value = "${var.bizagiGatewayToken}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_05" {
name = "certificateClientId"
value = "${local.client_id}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_06" {
name = "certificateClientSecret"
value = "${local.client_secret}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_07" {
name = "automationManagerBizagiHostZoneId"
value = "${var.automationManagerBizagiHostZoneId}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_08" {
name = "releaseManagementStorageStringConnection"
value = "${var.releaseManagementStorageStringConnection}"
vault_uri = "${azurerm_key_vault.kv.vault_uri}"
}
resource "azurerm_key_vault" "kv_slot" {
name = "${var.location_g}-kv-rm-${var.channel_g}-slot"
location = "${azurerm_resource_group.rg.location}"
resource_group_name = "${azurerm_resource_group.rg.name}"
sku {
name = "standard"
}
tenant_id = "${var.credential["tenant_id"]}"
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.credential["object_id"]}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
access_policy {
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${var.microsoft_web_objectid}"
key_permissions = [
"backup",
"create",
"decrypt",
"delete",
"encrypt",
"get",
"import",
"list",
"purge",
"recover",
"restore",
"sign",
"unwrapKey",
"update",
"verify",
"wrapKey"
]
secret_permissions = [
"backup",
"delete",
"get",
"list",
"purge",
"recover",
"restore",
"set"
]
}
enabled_for_disk_encryption = true
}
resource "azurerm_key_vault_secret" "secret_01_slot" {
name = "automationManagerAmazonAccessKey"
value = "${var.automationManagerAmazonAccessKey}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_02_slot" {
name = "automationManagerAmazonSecretKey"
value = "${var.automationManagerAmazonSecretKey}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_03_slot" {
name = "automationManagerSmtpPassword"
value = "${var.automationManagerSmtpPassword}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_04_slot" {
name = "bizagiGatewayToken"
value = "${var.bizagiGatewayTokenSlot}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_05_slot" {
name = "certificateClientId"
value = "${local.client_id}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_06_slot" {
name = "certificateClientSecret"
value = "${local.client_secret}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_07_slot" {
name = "automationManagerBizagiHostZoneId"
value = "${var.automationManagerBizagiHostZoneId}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_secret" "secret_08_slot" {
name = "releaseManagementStorageStringConnection"
value = "${var.releaseManagementStorageStringConnection}"
vault_uri = "${azurerm_key_vault.kv_slot.vault_uri}"
}
resource "azurerm_key_vault_access_policy" "kv_policy" {
count = "${length(var.policy_object)}"
key_vault_id = "${azurerm_key_vault.kv.id}"
tenant_id = "${var.credential["tenant_id"]}"
object_id = "${element(var.policy_object,count.index%length(var.policy_object))}"
key_permissions = "${var.key_permissions}"
secret_permissions = "${var.secret_permissions}"
certificate_permissions = "${var.certificate_permissions}"
depends_on = ["azurerm_key_vault.kv"]
}
resource "azurerm_key_vault_secret" "kv_secret" {
count = "${length(keys(var.kv_secrets))}"
name = "${element(keys(var.kv_secrets), count.index)}"
value = "${element(values(var.kv_secrets), count.index)}"
key_vault_id = "${azurerm_key_vault.kv.id}"
depends_on = ["azurerm_key_vault.kv","azurerm_key_vault_access_policy.kv_policy"]
}Terraform - Terratest

2
Libreria que permite escribir pruebas para el codigo de infrastructura.
Packer, Docker images, terraform...etc
Pre-requisitos: GO
package test
import (
"testing"
"github.com/gruntwork-io/terratest/modules/terraform"
"github.com/stretchr/testify/assert"
)
func TestWebAppBasic(t *testing.T) {
t.Parallel()
expected_rg_name := "eastus-rg-ops-dev"
expected_web_app_name := "eastus-app-ops-dev"
terraformOptions := &terraform.Options{
TerraformDir: "modules/web-app",
Vars: map[string]interface{}{
"rg_name":"opstest",
"prefix_rs":"ops",
"channel_g":"dev",
"location":"eastus",
"sp_tier":"Standard",
"sp_size":"S1",
"app_tls_version": "1.0",
"subscription_id": "jojojo",
"client_id" : "oooo",
"client_secret" : "joojo,
"tenant_id" : "jkjkj",
},
}
defer terraform.Destroy(t, terraformOptions)
terraform.InitAndApply(t, terraformOptions)
actualText := terraform.Output(t, terraformOptions, "rg_name")
assert.Equal(t, expected_rg_name, actualText)
actualText2 := terraform.Output(t, terraformOptions, "app_name")
assert.Equal(t, expected_web_app_name, actualText2)
}Init
Plan
Apply
Destroy
Liquibase

3
Liquibase es un librería Open Source (licencia Apache 2.0), que nos permite realizar el seguimiento, gestión y aplicación de cambios en el modelo de datos
<?xml version="1.0" encoding="UTF-8"?>
<databaseChangeLog
xmlns="http://www.liquibase.org/xml/ns/dbchangelog"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:ext="http://www.liquibase.org/xml/ns/dbchangelog-ext"
xsi:schemaLocation="http://www.liquibase.org/xml/ns/dbchangelog http://www.liquibase.org/xml/ns/dbchangelog/dbchangelog-3.0.xsd
http://www.liquibase.org/xml/ns/dbchangelog-ext http://www.liquibase.org/xml/ns/dbchangelog/dbchangelog-ext.xsd">
<changeSet author="automation-devops" id="1">
<sqlFile dbms="mssql"
encoding="utf8"
endDelimiter="\nGO"
path="scripts/01-DLL-AutomationManager.sql"
relativeToChangelogFile="true"
splitStatements="true"
stripComments="false"/>
</changeSet>
<changeSet author="automation-devops" id="2">
<sqlFile dbms="mssql"
encoding="utf8"
endDelimiter="\nGO"
path="scripts/02-TRIGGERS-AutomationManager.sql"
relativeToChangelogFile="true"
splitStatements="true"
stripComments="false"/>
</changeSet>
<changeSet author="automation-devops" id="3">
<sqlFile dbms="mssql"
encoding="utf8"
endDelimiter="\nGO"
path="scripts/03-DML-AutomationManager.sql"
relativeToChangelogFile="true"
splitStatements="true"
stripComments="false"/>
</changeSet>
<changeSet author="automation-devops" id="4">
<sqlFile dbms="mssql"
encoding="utf8"
endDelimiter="\nGO"
path="scripts/04-General-DML-AutomationManager.sql"
relativeToChangelogFile="true"
splitStatements="true"
stripComments="false"/>
</changeSet>
</databaseChangeLog>DatabaseChangeLog

Id
author
filename
dateexecuted
MD5SUM
1
automation-devops
/tmp/run/qa/changelog.xml
2018-11-03 00:43:06
7:c8fd3f67e78addbfe89bd41f3131f330
Python
Ejecuta task de Liquibase


herramienta de automatización de la construcción
Opcion 2: Servicios de actualizacion de BD
ejemplo: platform
Deploy

4

Idempotente


Version manager

jar
deployment
1
latest

deploy table
2

latest
slot
Integration test

5
BDD
Behaviour Driver Development
Verificar comportamiento código
BDD es un proceso de desarrollo de software que trata de combinar los aspectos técnicos y los de negocio, de manera que tengamos un marco de trabajo, y un marco de pruebas, en el que los requisitos de negocio formen parte del proceso de desarrollo
Integration test

5
BDD
Gherkin
lenguaje comprensible por humanos y por ordenadores, con el que se desbribe las funcionalidades, definiendo el comportamiento del software, sin entrar en su implementación
Feature: Rebase Automation
Rebase automation allows the process of rebase the cloud products.
The tasks of execution are creation of infrastructure, management operations with databases,
deployment of applications, execution of integration tests and other operations.
Rebase automation allows
Scenario Outline:
Given we have the first execution for the product <product> in channel <channel> and credentials <credentials>
When rebase automation is executed
And the resource group with name <name_rg> is created
Then execution result should be <status>
And resource group with name <name_rg>
And it should create the webapp with name <name_app>
And database with name <name_db>
And database server with name <name_dbs>
And location value is <location>
And <setting01> value is <value_setting01>
#And connection database is not null
Examples: Products
| product |channel | credentials | name_app | name_db | name_dbs | name_rg | status | location | setting01 | value_setting01 |
| modules |qa |CLOUDDEVOPSREBASEATUTOMATION | eastus-app-devopstest-qa | eastus-sdb-devopstest-qa/devopstest-db-qa | eastus-sdb-devopstest-qa | eastus-devopstest-rg-qa | SUCCESS | East US | setting01 | bizagi.com. |
Scenario Outline:
Given we have the first execution for the product <product> in channel <channel> and credentials <credentials>
When rebase automation is executed
Then se ejecutan los script base en el slot y el resultado debe ser <status>
Examples: Products
| product |channel | credentials | status |
| modules |qa | CLOUDDEVOPSREBASEATUTOMATION | EXECUTED |
- Feature: Indica el nombre de la funcionalidad que vamos a probar.
- Scenario: Describe cada escenario que vamos a probar.
- Given: Provee contexto para el escenario en que se va a ejecutar el test, tales como punto donde se ejecuta el test, o prerequisitos en los datos.
- When: Especifica el conjunto de acciones que lanzan el test. La interacción del usuario que acciona la funcionalidad que deseamos testear.
- Then: Especifica el resultado esperado en el test. Observamos los cambios en el sistema y vemos si son los deseados.
Integration test

5
Python
Behave
NodeJS
Cucumber
JUnit
BDD
Lenguajes
Frameworks BDD
Reportes

Script
Frameworks BDD
RA. Publicar

Swap

5

Idempotente


Version manager

jar
deployment
1
latest

Swap table
2
slot

site
Calidad Rebase Automation




Logs Jenkins-Azure Devops
Jenkins

Jenkins y los nodos se crean automaticamente
Pruebas de integracion de VM y Nodos
Migracion de Cloud
Backup Jenkins
Compromiso de equipos

Preguntas

Felipe Rojas
Johann de Jesús
GRACIAS
DevOps Cloud
Dev ups...
By jabjohanna
Dev ups...
- 36