Recon like a pro
- Jaimin Gohel
About Speaker
- MCA(GLSICT)
- Bug hunter
- Developer @Qloo IT Solutions
What is Reconnaissance?
Five Phases of a Pentest
-
Phase 1 | Reconnaissance
- Active (touching) or passive (indirect) data gathering on target
-
Phase 2 | Scanning
- Manual and automatic tools used to learn more about the infrastructure
-
Phase 3 | Gaining Access
- Taking control, extracting data, pivoting to attack other targets.
-
Phase 4 | Maintaining Access
- Persist, remain stealthy / don’t get caught and extract as much data as possible
-
Phase 5 | Covering Tracks
- Any changes, authorizations, etc. all must return to a state of non-recognition.
Types of Reconnaissance
-
Passive reconnaissance
-
DNS information
-
Sniffing through regular traffic
-
WHOIS database
-
-
Active reconnaissance
- OS scans
- Port scans
- Discover running services
- Programming languages used
Methods of Reconnaissance
- Recon through search engines
- DNS footprinting
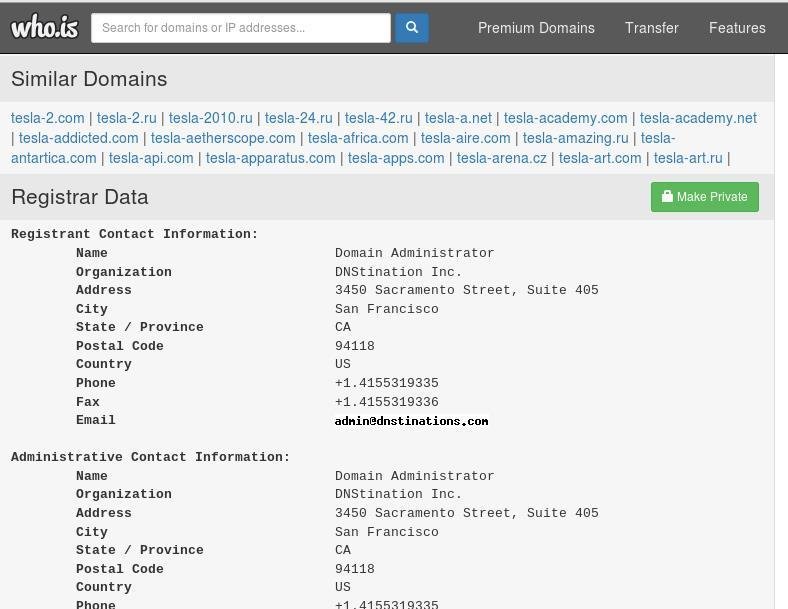
- WHOIS lookup
- Through social networking sites/ people search services
- Advanced google hacking techniques
- Find services used by target host
- Website recon
Recon through search engines (Shodan.io)
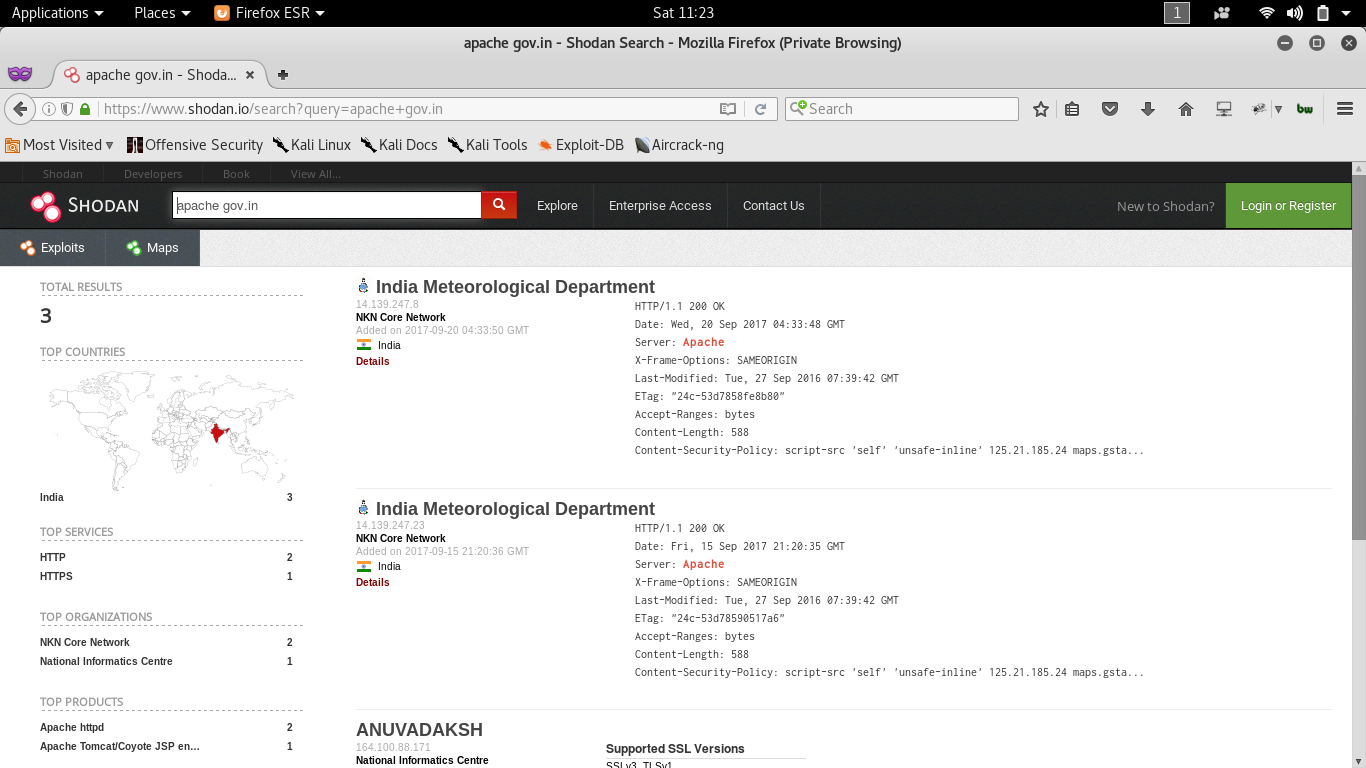
Recon through search engines (Shodan.io)
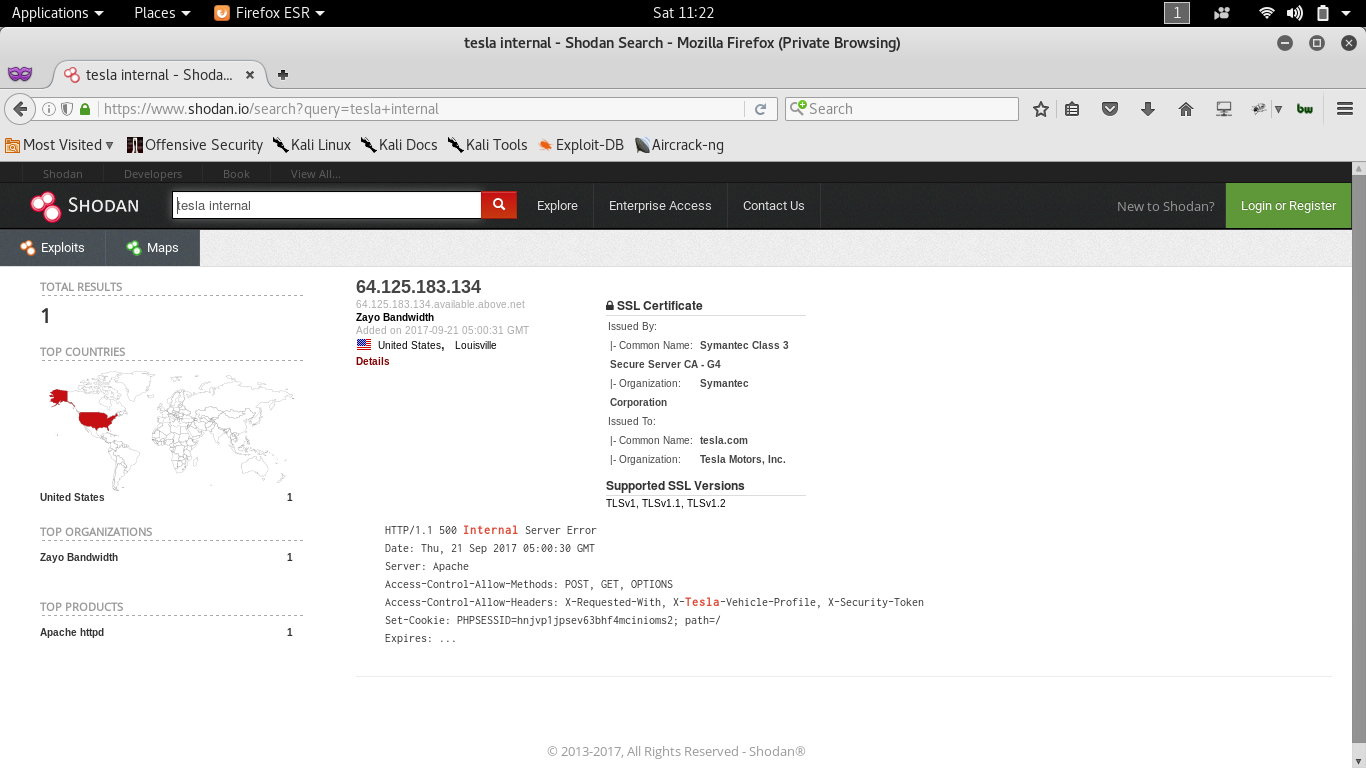
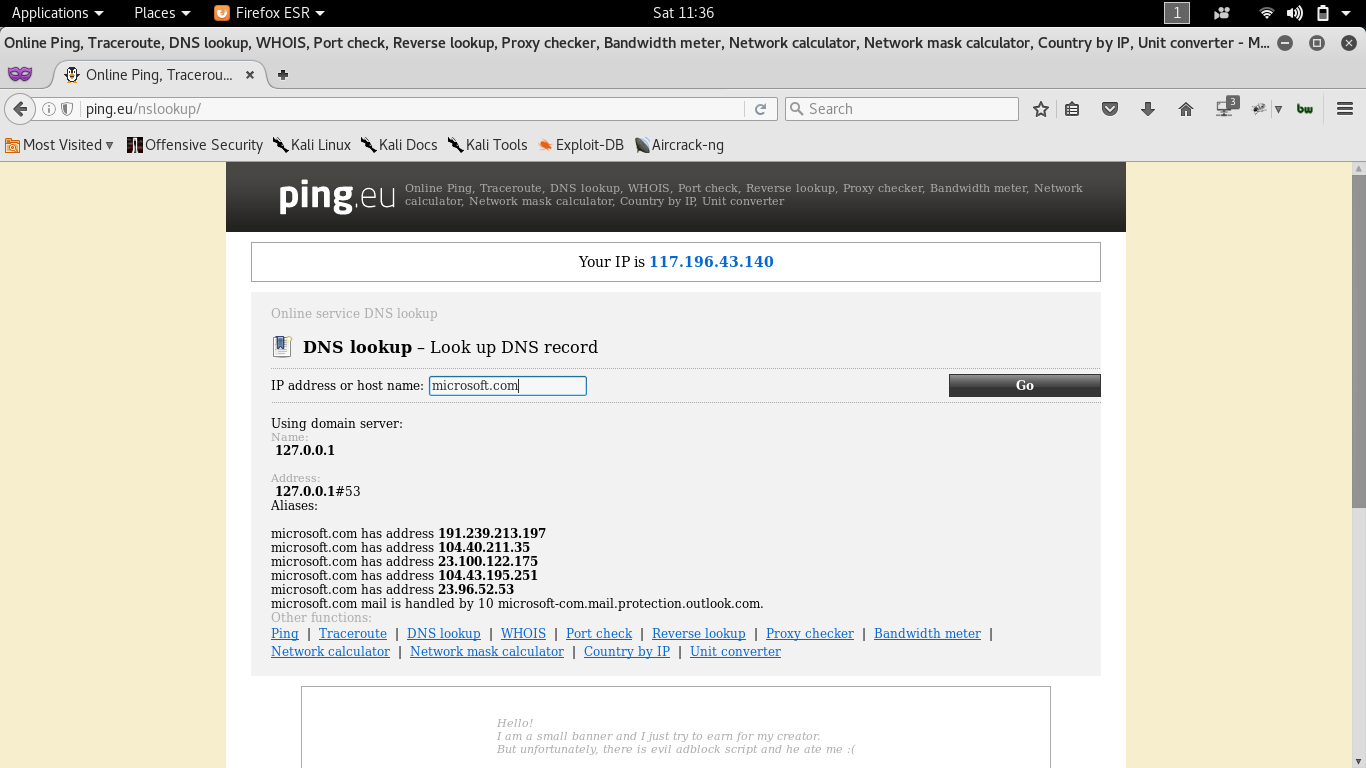
DNS footprinting (http://ping.eu/nslookup/)
WHOIS lookup
- Domain name details
- Contact details of domain owner
- Domain name server
- When a domain has been created
- Expiry records
WHOIS lookup (https://who.is)

WHOIS lookup (https://who.is) cont.
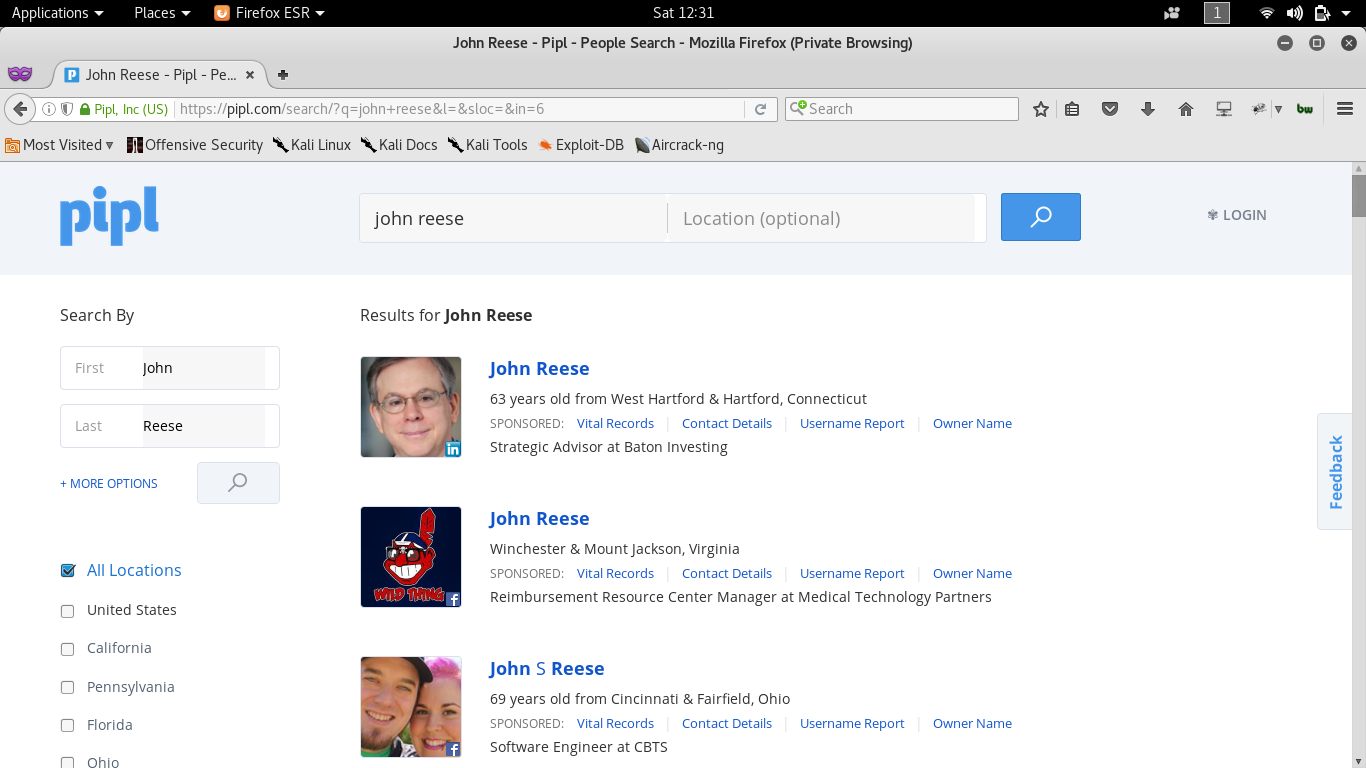
Through social networking sites/ people search services
- Social networking sites are great source of personal and organizational information
- Information about an individual can be found at various people search websites
- Eg. Linkedin.com, pipl.com
Social site (https://pipl.com)
Advanced google hacking techniques
- Google hacking refers to creating complex search queries in order to extract sensitive hidden information
- It helps attacker to find possible vulnerable targets
- It used advanced google search operators to locate specific strings of text within the search result
Advanced google hacking techniques
- intitle:
- intitle:Admin login
- intext:
- intext:email
- inurl:
- inurl:view/view.php
- site:
- site:example.com
Advanced google hacking techniques
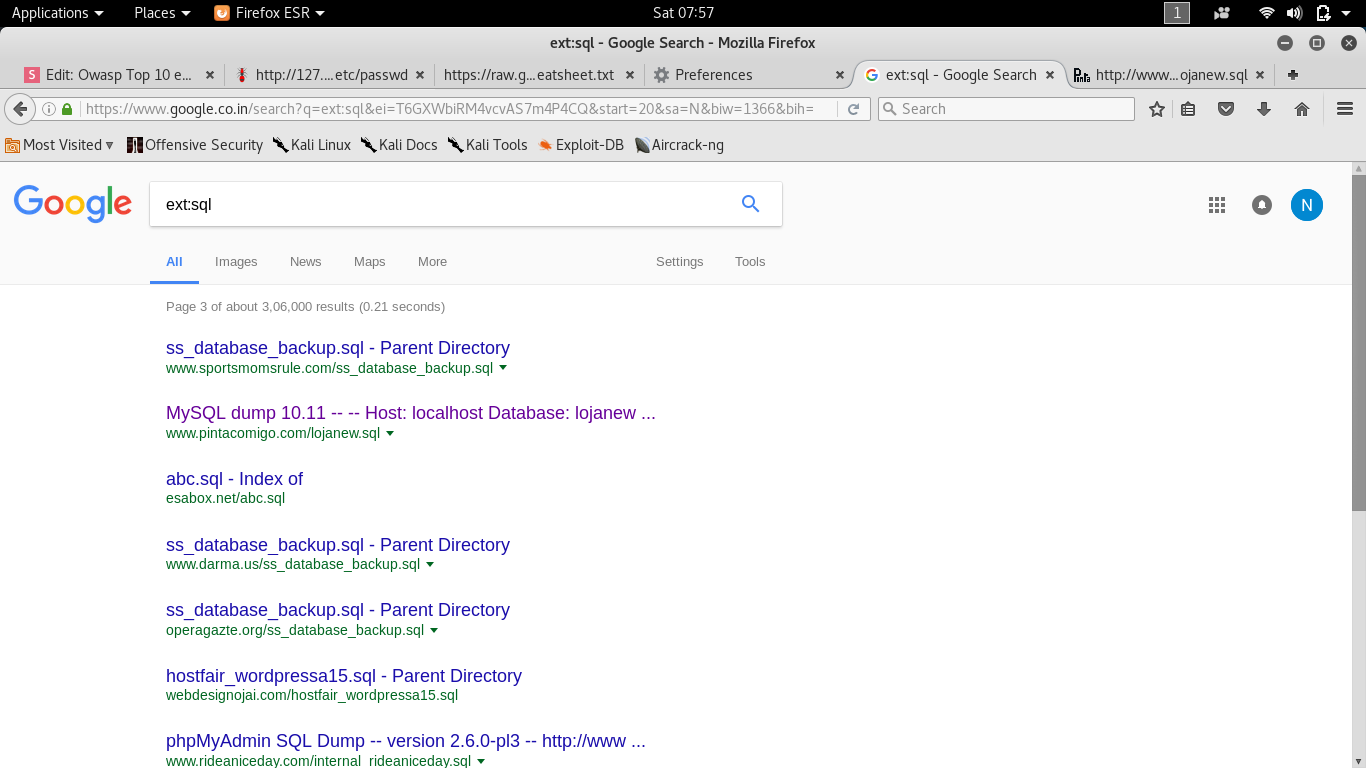
- site:example.com ext:xml | ext:conf | ext:cnf | ext:reg | ext:inf | ext:rdp | ext:cfg | ext:txt | ext:ora | ext:ini
- site:example.com ext:sql | ext:dbf | ext:mdb
- site:example.com ext:bkf | ext:bkp | ext:bak | ext:old | ext:backup
- site:example.com intext:"sql syntax near" | intext:"syntax error has occurred" | intext:"incorrect syntax near"
Advanced google hacking techniques
Find services used by target host
- wappalyzer
- Wappalyzer is a browser extension that uncovers the technologies used on websites. It detects content management systems, eCommerce platforms, web servers, JavaScript frameworks, analytics tools and many more.
- bultwith.com
- Demo
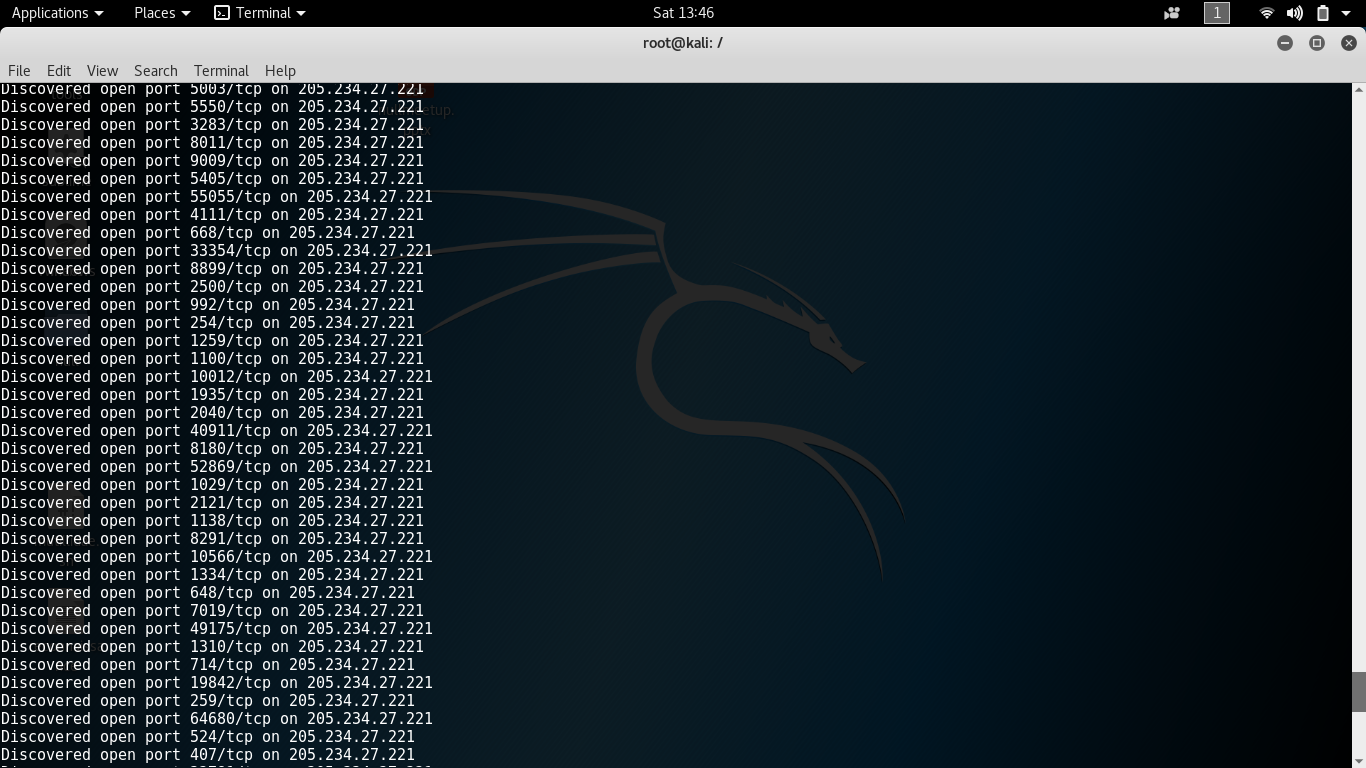
- nmap
- NMAP(network mapper) used to discover hosts and services on a computer network, thus building a "map" of the network.
Namp example
Website recon
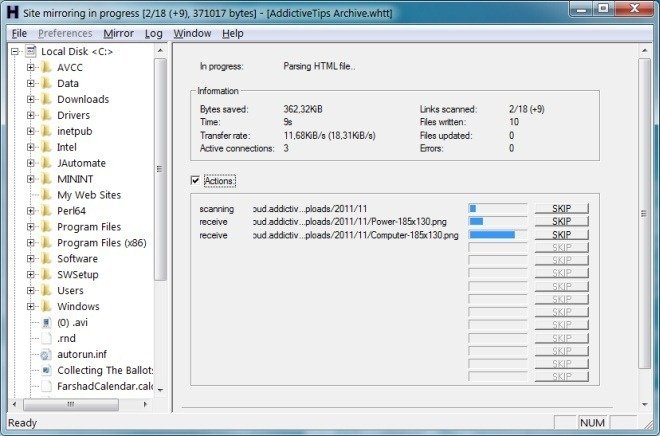
- Web data extractors
- httrack
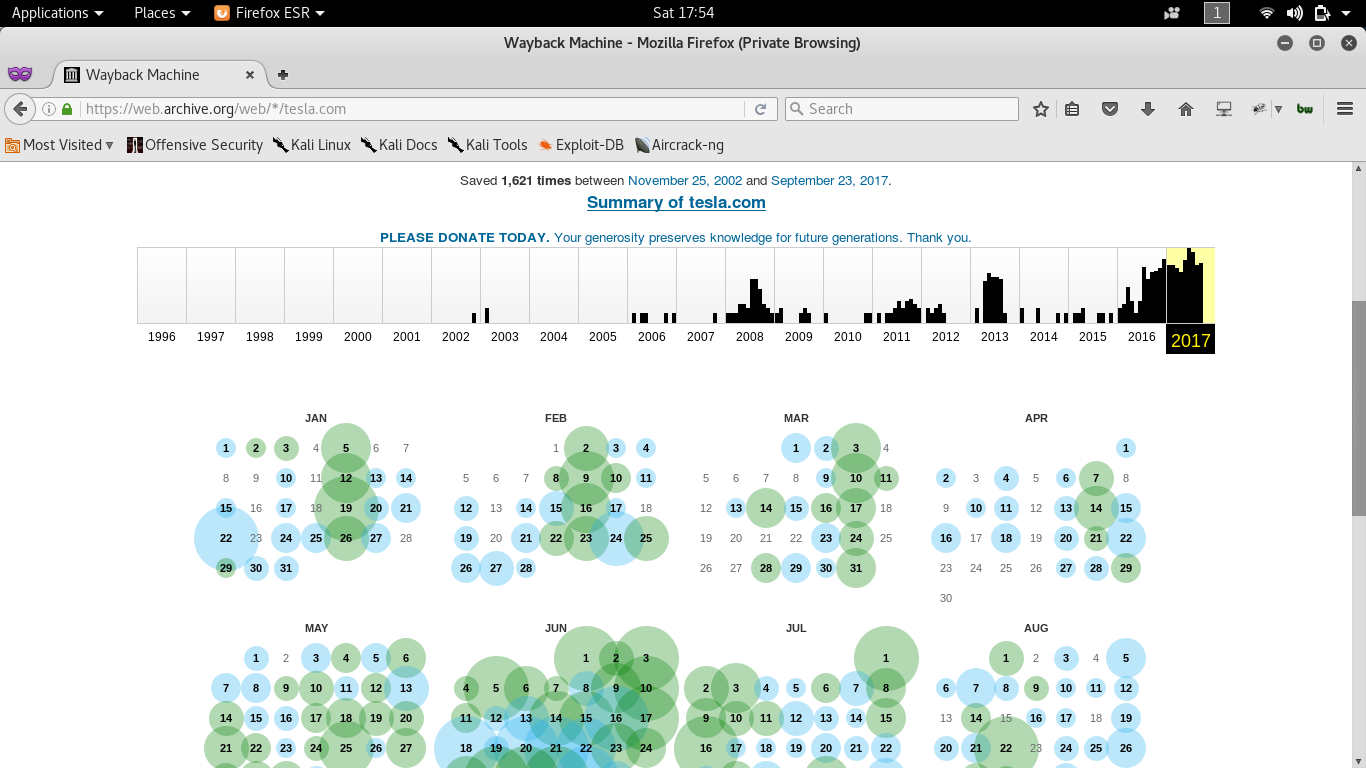
- Wayback machine
- archive.org
- Examine html source code
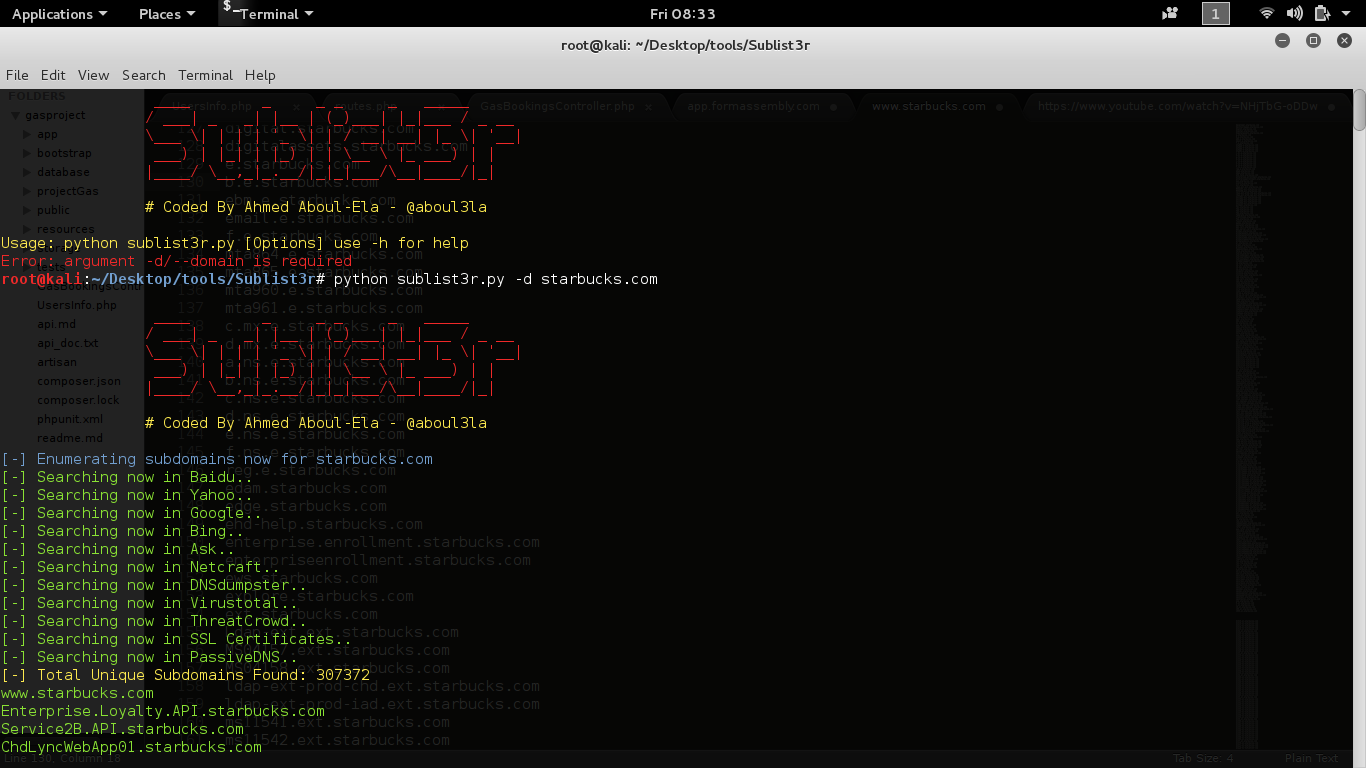
- subdomain finder
- sublister, knockpy
Web data extractors(httrack)
Wayback machine(https://archive.org)
Subdomain scanning (Sublist3r)
Questions?
Recon like a pro
By Jaimin Gohel
Recon like a pro
Recon like a pro by Jaimin Gohel
- 1,159



