Methods to Detect and Prevent Cyber Security Threats
Understand and be able to explain the following security measures:
- biometric measures
- password systems
- CAPTCHA
- email to confirm identity
- automatic software updates
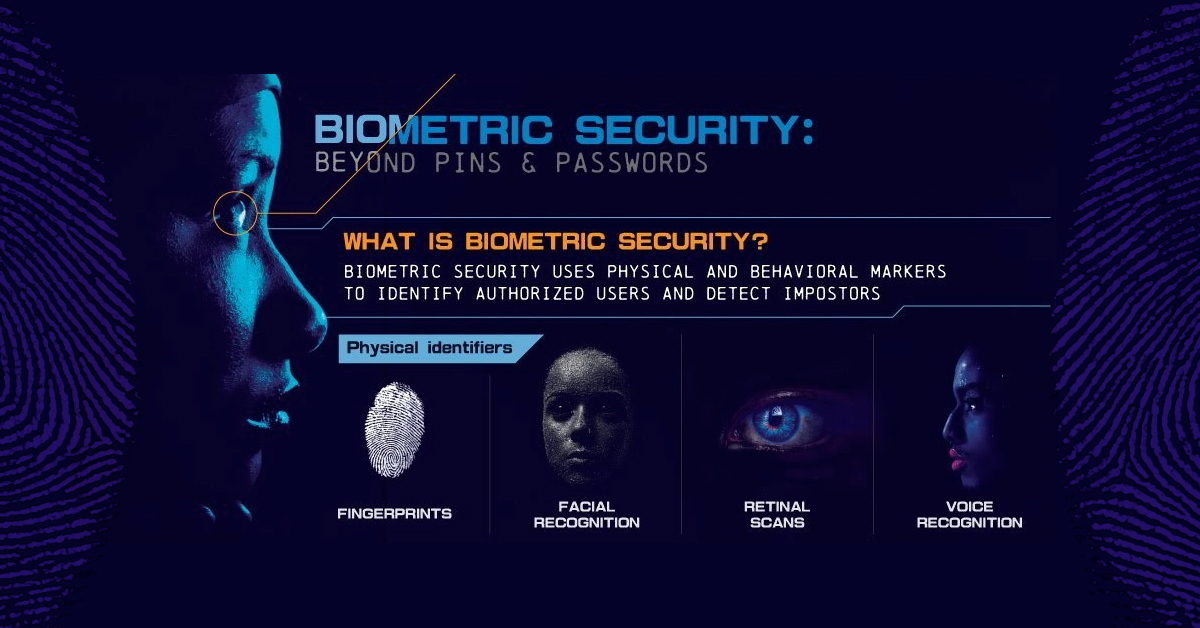
Biometric Measures
- Makes use of a person's physical features:
- fingerprint
- facial recognition
- voice recognition
- retinal scans
- To allow access to a system.
- Biometric methods cannot be forgotten or stolen, making them more secure than passwords.
Password Systems
- Currently the most common method for preventing unauthorised access to a network or computer.
- Essential that passwords are strong and not written down.
- Some sites/applications only ask for some of the characters from a password (e.g. 2nd, 5th and last), this makes it difficult for key-loggers to obtain the full password.

Password Systems
- Two-step authentication is becoming more common.
- This means the user has to enter a unique code sent via SMS, email or an authentication application after the user has entered their username and password.
- This code is usually only valid for a short period of time making it harder for a hacker to gain access to a system.
CAPTCHA
- A form of challenge response test used to determine whether a user is human.
- It involves asking a user to perform a task that a software (ro)bot could not.
- The most common form is the text CAPTCHA, where the user is show an set of distorted characters that they then have to type in.
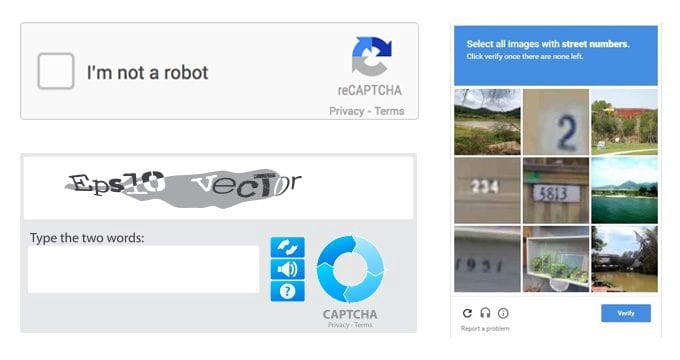
CAPTCHA
- Picture recognition CAPTCHAs show a series of images that the user has to select all of a certain type (e.g. cars).
- Some CAPTCHAs only need the user to click on a check box to confirm they are human.
- CAPTCHAs are good at preventing fake registrations on websites and other spam.
- However, users find them irritating and can be put off accessing a site as a result.

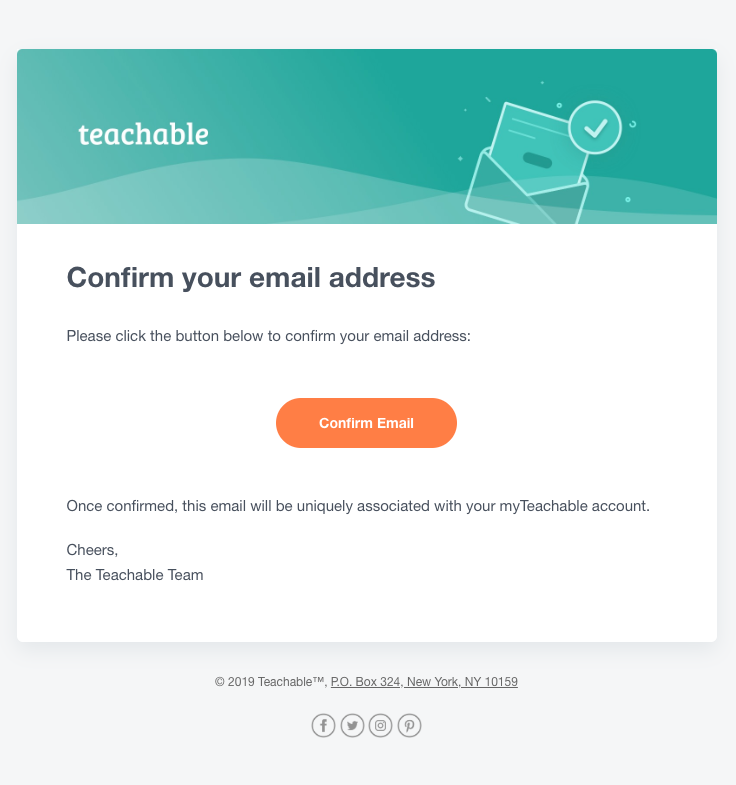
Email Confirmations
- Used after a user creates an online account.
- The site might send an email for the user to click on a link, to confirm the email address is linked to the person that created the account.
- The online account will only be confirmed once the verification link is clicked.
- It allows the site to confirm the new account is real and not automated.
- It also alerts users if someone is trying to illegitimately use their email address.
Automatic Software Updates
- Keeping software up to date, helps to keep systems secure.
- Most programs now allow automatic updates and operating systems will update and install patches as soon as they are available.
- This means the time an exploitable weakness is on a system is kept to a minimum.
- It also reduces the chances of the user forgetting to perform updates.
Questions
- Identify and describe two methods that can be used to ensure that users are real when signing up to a website.
Answers
CAPTCHAs - users are required to select a sub-set of images or enter text that has been distorted.
Email confirmation - users are sent an email with a link they need to click to confirm their email address is valid.
- Identify and describe two methods that can be used to ensure that users are real when signing up to a website.
6d Detect and Prevent Cyber Security Threats
By David James
6d Detect and Prevent Cyber Security Threats
Computer Science - Cyber Security - Detect and Prevent Cyber Security Threats
- 776



