Hacking Node.js web services

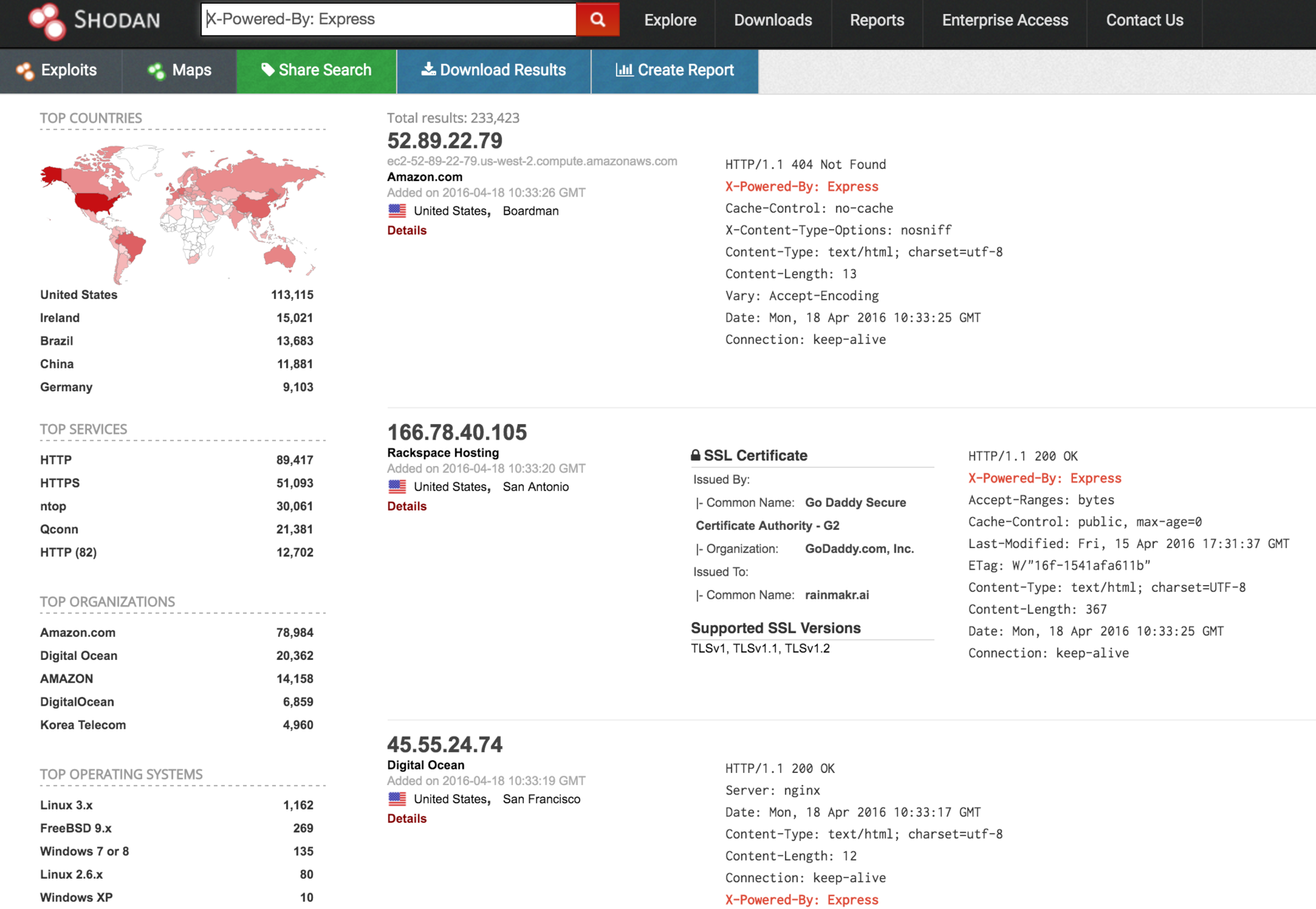
shodan. “X-Powered-By: Express”


shodan + exploitsearch



whoami
sysadmin, VoIP dev, pentester ...
@jesusprubio
Emergent Solutions Team (Backend Developer)



a1 - injection





Server side JS
SQL
NoSQL
db.users.findOne({“userName”: “admin”, “password”: { “$gt”: “” } } )


rules
Use mature stuff
About rolling your own crypto, session management ...


Cleanup


a2 - broken auth
Session Management: encrypt user credentials in DB, secure cookies, sessions timeout ...


Password Guessing Attack: username/passwords enumeration, password complexity, length ...



ZAP. creds brute-force




ZAP. creds brute-force






a3 - XSS. reflected



XSS. persistent



XSS. DOM based



a4 - insecure DOR



a5 - security misconfig







a6 - sensitive data






a7 - access controls



a8 - CSRF



CSRF. solution



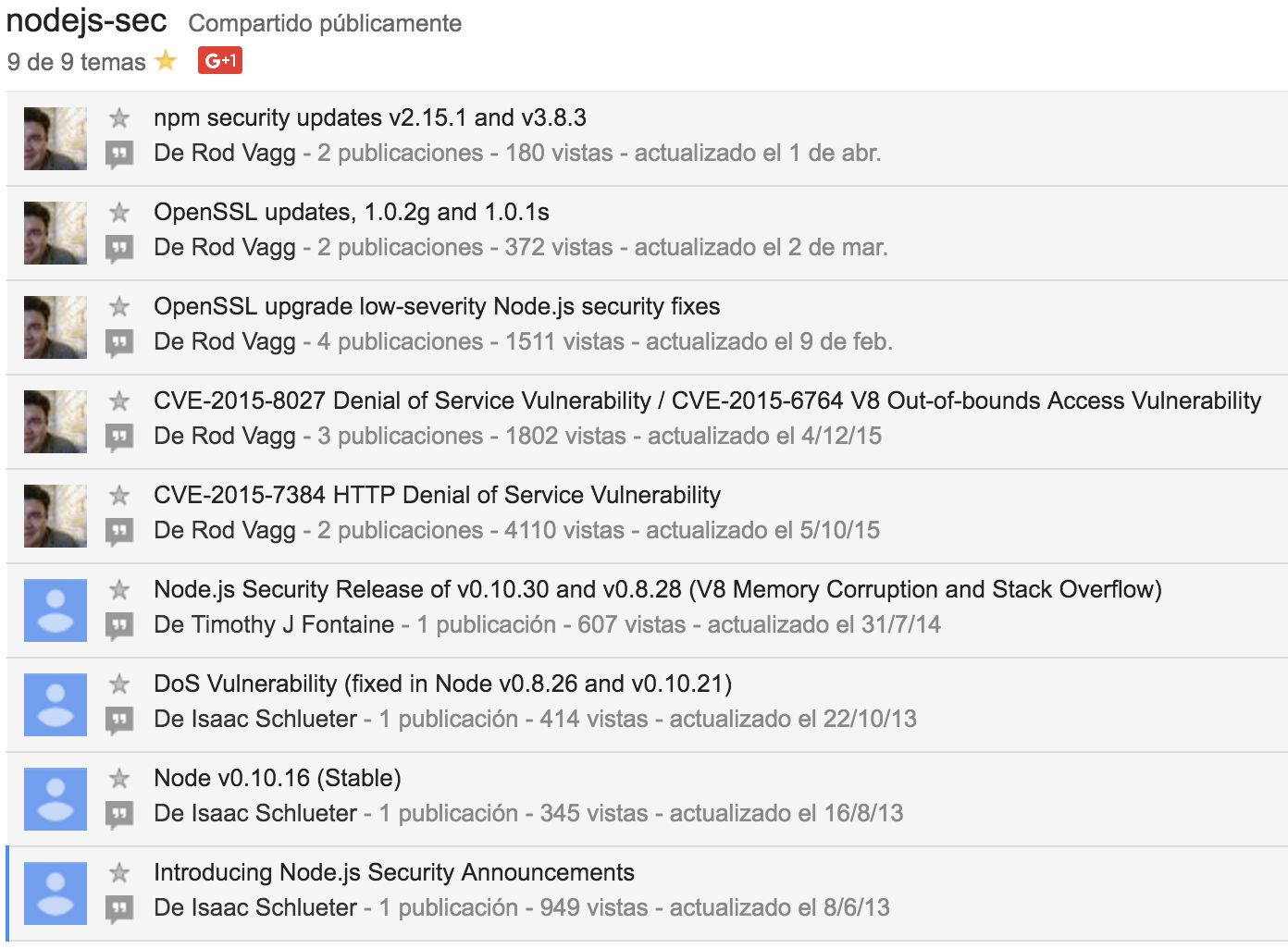
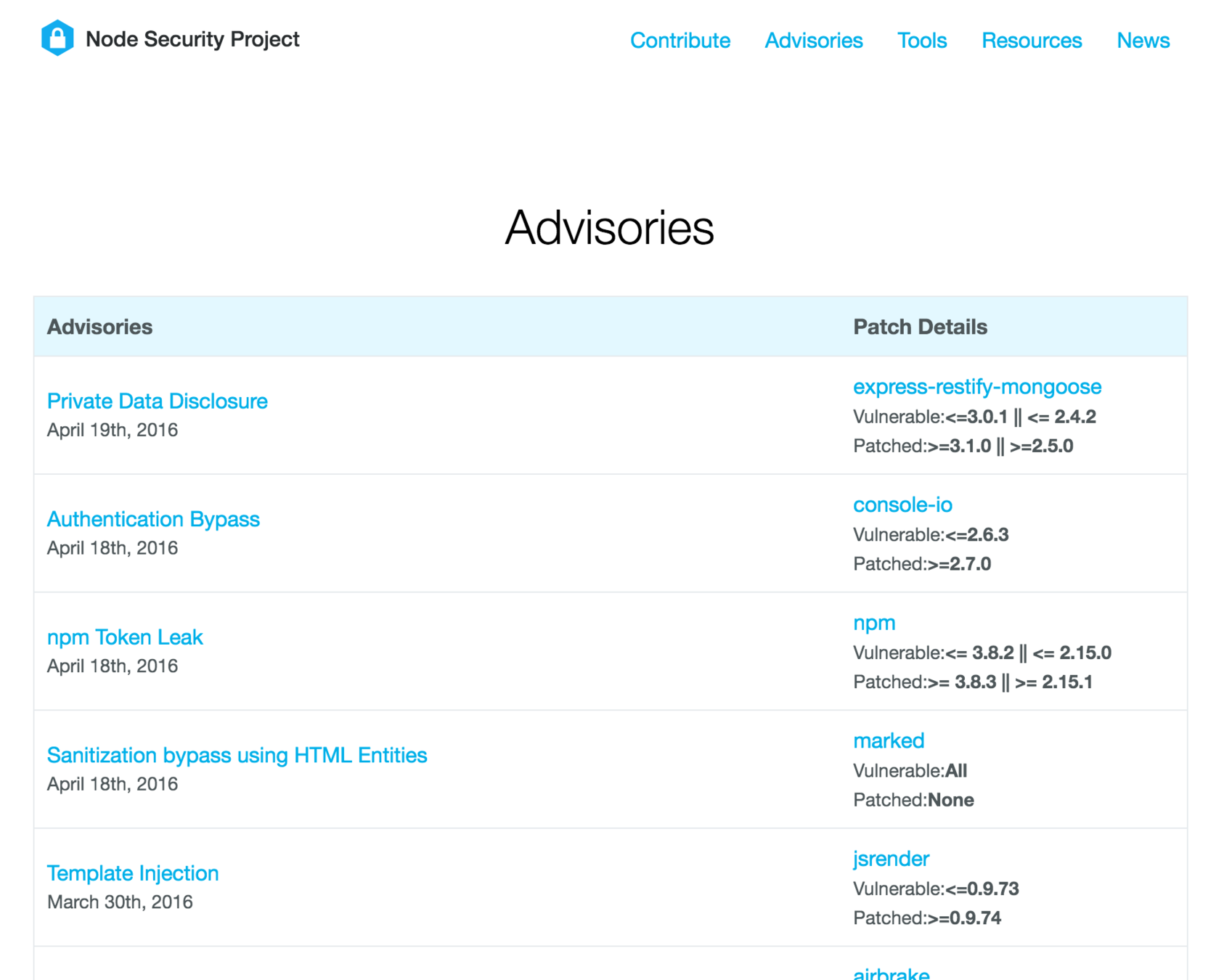
a9 - insecure components. vulns


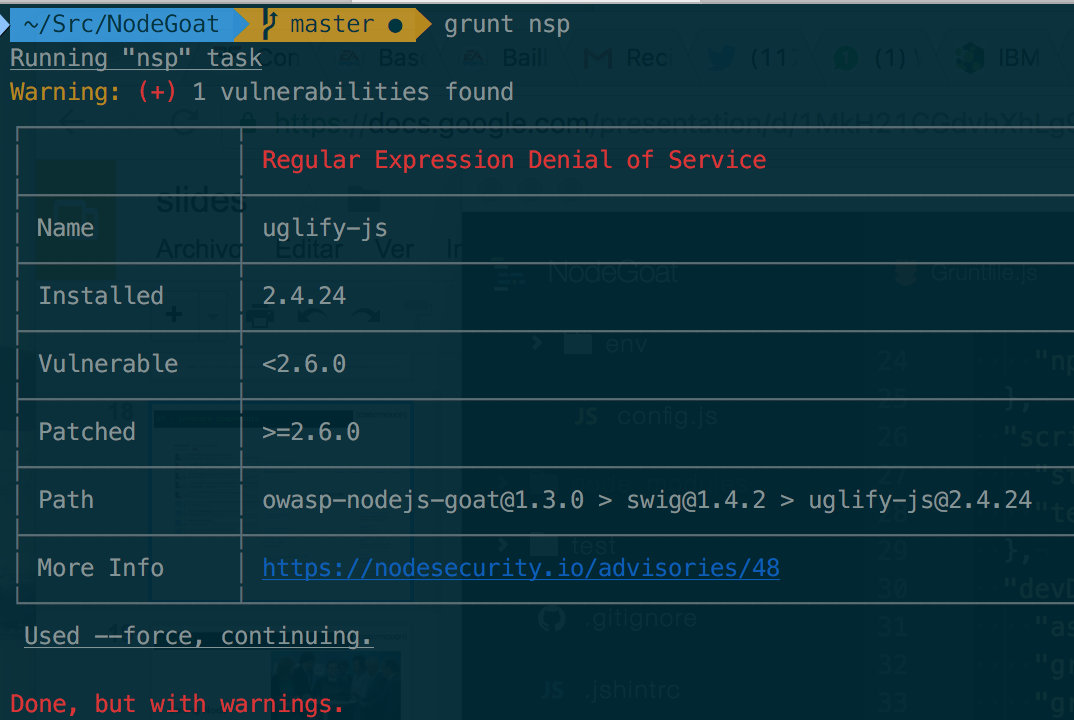
insecure components. nsp client



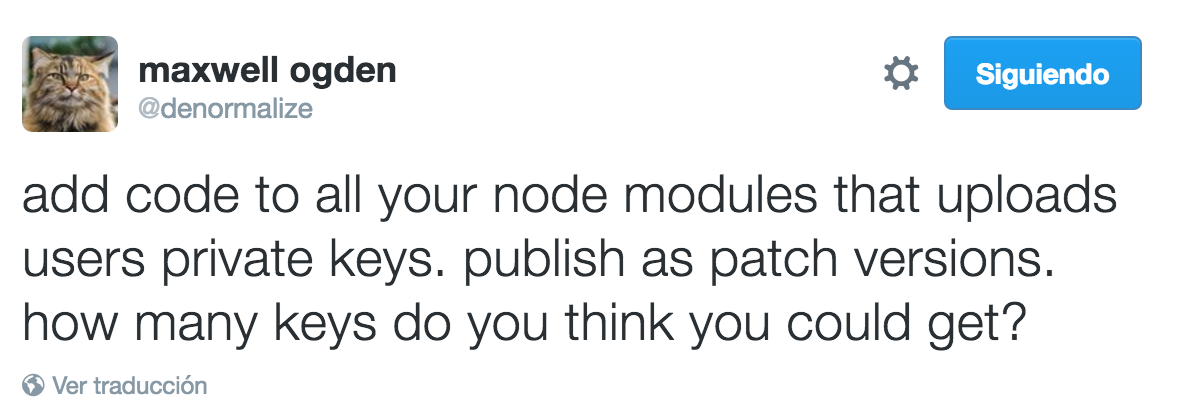
insecure components. malware



insecure components. real case





a10 - unvalidated redirects





more ZAP. auto-scan



My 2 cts. checklist


:) ¿?



Hacking Node.js web services
By Jesús Pérez