OAuth 2.0
Josh Kerr
February 2, 2016
About Me
-
Software Developer/Architect
- Apps, Ops, Infrastructure, and Security
-
Work at USAA
-
JUG Co-Leader
-
Twitter
@jokerr
Agenda
-
Background
-
OAuth 2.0 Concepts
-
OAuth 2.0 Flows
-
Extensions
Why OAuth?
Example Scenario
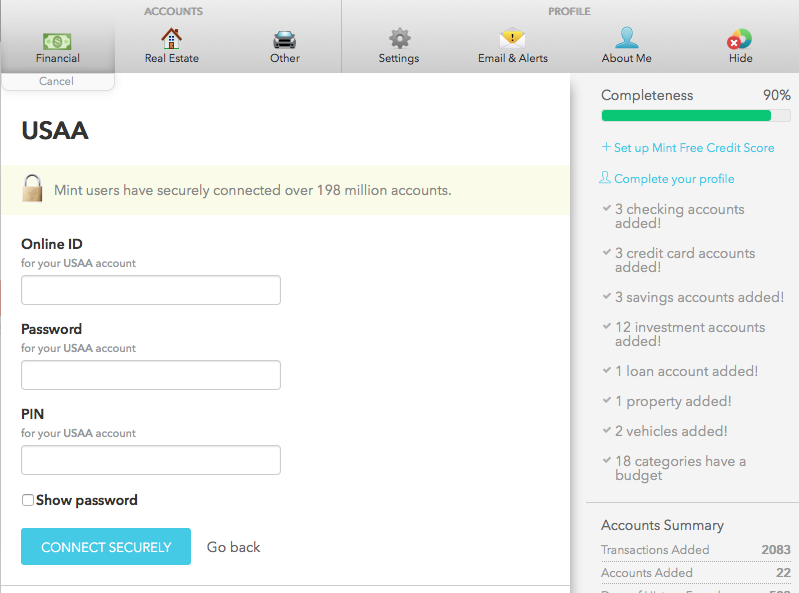
Example Scenario
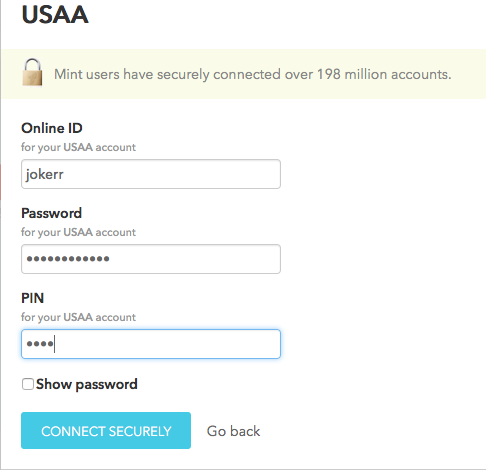
So what's the problem?


Enter OAuth!
Enter OAuth!
-
Open framework for security
-
No more password exchange
-
Delegated access
-
3rd Party apps store a token
-
Limited and scope
Brief History
OAuth 1.0
-
Shared secrets between endpoints
-
3 overlapping flows
-
Confusing spec

OAuth 2.0
-
Relies on TLS/SSL
-
Identifiable flows
-
Clearly defined roles
Real World Examples

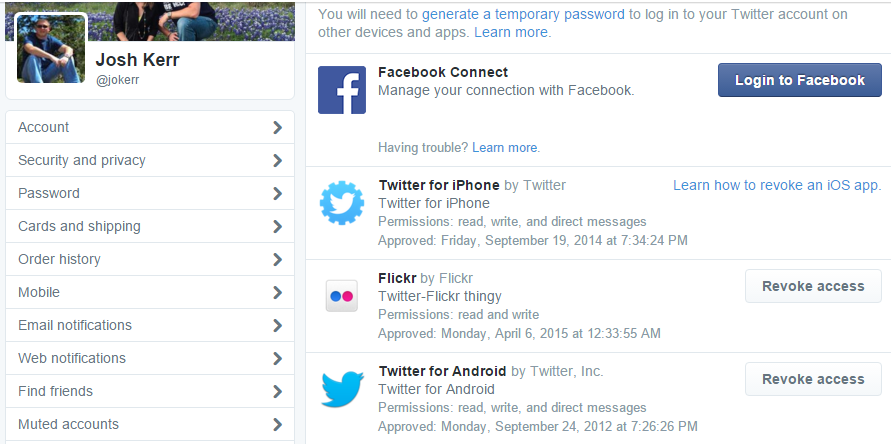
The Basics
Authentication
Authorization
vs.
Roles
-
Resource Owner - The user
-
Resource Server - The API
-
Authorization Server - Issues tokens
-
Client - The application
Scopes
-
Similar to permissions
-
Limits the usefulness of the token
-
Users consent via UI (when shown)
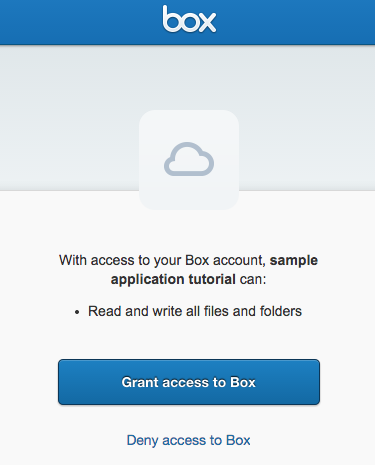
Client Registration
-
Clients register with the Authorization Server
-
Confidential vs. Public
Access Token
-
Short lived
-
Reference vs. Value
-
Format is up to you
-
Bearer vs. MAC
Refresh Token
-
Longer lived
-
Used with client credentails to obtain an access token
Authorization Code
Implicit
Client Resource Owner
Client Credential
Authorization Code
Authorization Code
-
Most common form of OAuth
-
Typically Server 2 Server
-
Confidential client
-
Tokens are refresh-able
Client Application
Auth Server
Resource Server
Resource Owner
Request token
Login and approve
Authorization code
Exchange code for a token
Access Token
Call secured service with Access Token
{
"access_token": "T9cE5asGnuyYCCqIZFoWjFHl",
"expires_in": 3600,
"token_type": "bearer",
"refresh_token": "J7rxTiWOHMoSC1isKZgCUfGMinKBDLZWP9BgR"
}POST https://myapp.com/api/oauth2/token
grant_type=authorization_code&code=123456abcdef&
client_id=MY_CLIENT_ID&client_secret=MY_CLIENT_SECRETGET https://myapp.com/api/oauth2/authorize?response_type=code&
client_id=MY_CLIENT_ID&state=security_state&
redirect_url=https://jokerr.net/oauthhttps://jokerr.net/oauth?code=123456abcdef&state=security_stateGET /resource HTTP/1.1
Host: myapp.com
Authorization: Bearer T9cE5asGnuyYCCqIZFoWjFHl
Implicit
-
Typically browser based
-
Client secret is assumed to be compromised
-
Tokens are not refreshable
Implicit
Client Application
Auth Server
Resource Server
Resource Owner
Request token
Login and approve
Access Token
Call secured service with Access Token
GET https://myapp.com/authorize?response_type=token&
client_id=MY_CLIENT_ID&
redirect_url=https://jokerr.net/oauthhttps://jokerr.net/oauth?access_token=T9cE5asGCCqIZFo
&token_type=bearerClient Resource Owner
-
Exchange your credentials for a token
-
Confidential client usually created by the service provider
-
Tokens are refreshable
Client Resource Owner
Client Application
Auth Server
Resource Server
Resource Owner
Request Token with username/password
Access Token
Call secured service with Access Token
Validate credentials
POST https://myapp.com/api/oauth2/token
grant_type=password&
username=jokerr&
password=12345&
client_id=MY_CLIENT_ID{
"access_token": "T9cE5asGnuyYCCqIZFoWjFHl",
"expires_in": 3600,
"token_type": "bearer",
"refresh_token": "J7rxTiWOHMoSC1isKZgCVJ9bKBDLZWP9BgR"
}Client Credential
-
Actions are not performed on behalf of a user (think batch)
-
Tokens are not refreshable
Client Resource Owner
Client Application
Auth Server
Resource Server
Request Token with client credentials
Access Token
Call secured service with Access Token
Validate credentials
POST https://myapp.com/api/oauth2/token
grant_type=client_credentials&
client_id=MY_CLIENT_ID&
client_secret=MY_CLIENT_SECRET{
"access_token": "T9cE5asGnuyYCCqIZFoWjFHl",
"expires_in": 3600,
"token_type": "bearer"
}JWT Token
JWT
JSON Web Token is a means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is digitally signed using JSON Web Signature (JWS) and/or encrypted using JSON Web Encryption (JWE).

header.payload.signature
-
JSON object
-
Defined structure and keys (claims)
-
Can be signed (JWS)
-
Can be encrypted (JWE)
JWT
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
.
eyJzdWIiOiJKb2tlcnIiLCJuYW1lIjoiSm9zaCBLZXJyIiwiYXVkIjoiU0FUIEpVRyJ9
.
VUJOunV-K9lOqjf-jAr_pGZIt6ja3fNXXS-v8vmyx7A{
"alg": "HS256",
"typ": "JWT"
}
.
{
"sub": "Jokerr",
"name": "Josh Kerr",
"aud": "SAT JUG",
"iat": 1453342985,
"exp": 1454379784
}
.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret
)JWT Demo

JWT Token...
Who Cares?
JWT
-
Similar to a SAML token but lighter and compact
-
Great for authentication scenarios or information exchanges
-
Can be passed over headers or querystring
OAuth + JWT
-
Extension of the spec
-
Can be used for client authentication
-
Can be the access token
{
"iss": "https://idp.jokerr.net",
"sub": "jokerr",
"aud": "https://satjug.slack.com",
"iat": 1453342985,
"exp": 1454379784,
"jti": "8ce244c2-9090-43e3-8aaf-2632a6daf33b"
}POST https://myapp.com/api/oauth2/token
grant_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer
&assertion=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJpc3MiOiJodHRwczovL2lkcC5qb2tlcn[...omitted...]zYiJ9.
WgIONUSAR7L5CmbtwbZBmQaYFBQrMBInS5PbmS_vW-w
OpenID Connect
What's the problem?
-
Access Token doesn't prove authentication
-
No standardized user indentification
-
OAuth 2.0 + Identity Token
-
OAuth is an authorization framework
-
Identity Token (JWT) for authentication
OpenID connect
Java Options?
Apache Oltu
Spring Security OAuth
Refrences
- OAuth 2.0 RFC (https://tools.ietf.org/html/rfc6749)
- JWT RFC (https://tools.ietf.org/html/rfc7519)
- OAuth 2.0 JWT RFC (https://tools.ietf.org/html/rfc7523)
- OpenID Connect (http://openid.net/connect/)
- JWT Debugger (http://jwt.io)
- Spring Security OAuth (http://projects.spring.io/spring-security-oauth/)
- Apache Oltu (https://oltu.apache.org/)
Questions?
oauth
By Josh Kerr
oauth
- 792


