Hack to the Future

day one: guide to being a hacker
{ what you will learn }
- Ethical hacking
- Networking
- Defensive techniques against hackers
- Privacy & security
- Python (the programming language, not the animal)


{ student survey }
- Open the Chromium browser and go to:
- https://www.surveymonkey.com/r/8KRCYZP
- Take the survey and press "Done" when you're done
- Please answer honestly; help us help you


{ icebreaker }
- Hacking is all about finding information that is not given to you and extrapolating from data
- You are a hacker, trying to use non-digital methods to discreetly find out information about a person of interest
- Your goal is to find out their: age, grade level, where they're from, hobbies/interests, and other information that you gave to us freely on the survey
- However, you may not ask those questions abruptly
- If you do, the person you are talking to will raise their hand and you'll be disqualified
- You are allowed to intentionally act in a way that is misleading (ex. Speaking in a British accent)
- However, you may not ask those questions abruptly
- Your goal is to find out their: age, grade level, where they're from, hobbies/interests, and other information that you gave to us freely on the survey
- At the end, you will write down and present 5 "facts" about your target
- There will be a prize for the person who gets the most accurate facts
{ icebreaker }
- We'll pair you all up, introduce yourselves with your real first name!
- Be friendly and normal. You must be normal, or else you will be a terrible hacker because you need to blend in
- Do not refuse to speak/engage in conversation, because that won't be normal
- We will demonstrate how to carry out a normal conversation while secretly trying to look for weaknesses and gather data!
- We'll first show you what you shouldn't do
{ introductions }
-
John Headland
- Default :)
- Annoyed >:(
- Dangerous >:)
-
Irene Fang
- Needs no introduction


{ rules }
- Everyone gets respect
- Leave no one behind
- No phones/tablets/miscellaneous devices not approved by instructors
- No installing/downloading unauthorized programs/files
- Considering that you are in a hacking class, be intelligent and understand that any trick you found on Google, your instructors have seen
- No open food/drinks in front of computers
- No spinning in your chairs while we're talking
- "Three Before Me": Ask three of your peers before asking instructors for assistance


{ ethics }
-
Do not take the things you learn in the class and try to break into things in the real world
- We are teaching you these techniques to defend yourselves
- Hacking can be legally grey; understand that there are real consequences if you try something fishy and are caught
- There are cybersecurity professionals whose jobs are to identify attackers
- Share information
- Hacking should be done for a good cause


{ hackers & crackers }

DON'T BE A CRACKER
{ what is "hacking"? }
- To modify a program so it takes an input and produces a different output than originally intended
- In terms of cybersecurity: it's to circumvent security by exploiting weaknesses in a computer system or network
- Hackers have advanced knowledge of computers and usually write programs in skillful or clever ways
- Crackers usually use pre-written code/scripts to break into computers, with malicious intent


{ how to be a hacker }
- First of all, you must use GNU/Linux
- No Windows or Mac OS X spyware
- They would be imprisoned on the spot
- Respect your freedoms and privacy!
- Free & open source software (FOSS)
- Full control & transparent
- No Windows or Mac OS X spyware
- Most hacking tools are written for Linux


Step 1
{ how to be a hacker }
- Stop using anything Google-related!!!!
- Google Analytics
- Just like Microsoft Windows 10
- Listens to your conversations
- Siri & Cortana
- The Facebook app does the same


Step 2
{ how to be a hacker }
- Learn a programming language
- Devote your life to it
- Preferably Python or C++
- We will teach you Python in this class


Step 3
{ how to be a hacker }
- Wear a grey/black hoodie AT ALL TIMES!!!!
- Even at home in front of your computer
- Without it, you're not legit
- Wear a white, grey, or black hat (preferably a fedora) at all times when in public to signal your alignment
- More on that next


Step 4
{ types of hackers }
- White Hat
- Ethical hackers
- Hacks into networks to test or evaluate the security; penetration testing
- Grey Hat
- Hackers that may violate laws/ethical standards, but without malicious intent
- Black Hat
- Hackers that illegally and maliciously hack into systems for personal gain, usually money


{ preliminary teachings }
- Before we teach you how to hack, there are a few things you must learn first:
- How to use our OS, GNU/Linux
- The command language, Bash
- The programming language, Python
- Networking
- If you don't know these things, you won't be able to hack at all


{ shell }
-
A shell is the program that passes keyboard commands to the operating system (such as Windows, OS X, GNU/Linux, BSD) to carry out
- Also referred to as the terminal emulator (commonly known as the terminal) or command line
- The terminal is where we interact with the shell to directly and completely control the computer
- The default shell for UNIX based operating systems is Bash
- Bash == Bourne Again Shell


{ gnu/linux }
- What is GNU/Linux?
- Unix-like OS composed of GNU packages/coreutils and the Linux kernel
- What is GNU?
- FOSS containing the core utilities and basic tools necessary to do things on your PC
- What is Linux?
- Kernel
- Central core of OS
- Handles Input/Output requests from software
- Links software and hardware (CPU)
- Kernel


{ ubuntu }
- In Hack to the Future, our main OS will be Ubuntu
- Debian-based distribution of GNU/Linux
- GNU/Linux has free distros that are community/company-made
- Beginner-friendly
- Uses Unity as the default desktop environment
- Uses .deb files as its packages and the apt package manager
- Try to use the terminal as much as possible, like real hackers!!


{ learning terminal }
- To get you used to using terminal and learn some basic Bash, we will play a game
- It is a really fun game where you explore a world and discover things
- Spells are commands, items are files, and locations are directories
- In Chromium, enter the following url:
- http://mprat.org/Terminus
- Follow along with the directions and read carefully
- Remember: Three Before Me


{ unix file system }

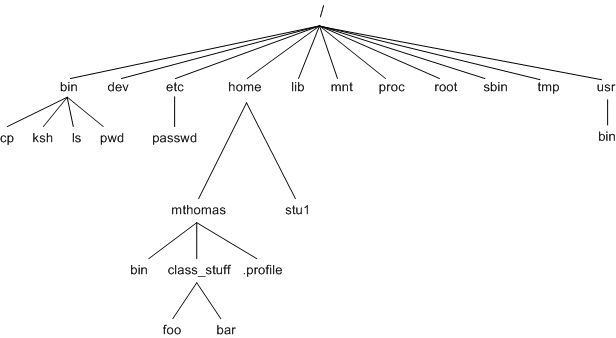
- Looks like a tree
- How your files look/are arranged in your computer
- We will navigate the UNIX file system using the command you learned in Terminus
{ paths }
- A path in the file system traces out the location of a file/folder from a given directory
- When you first open terminal, bu default you are placed in your user's home directory
-
Ex. Let's say we're looking for the index.html file in John's Profile folder, which is in his App Development folder, which is on his Desktop, which is in his User directory, under Home, which directly branches from root. To get to that location, we specify a path:
- "~" or tilde stands for /home/user/
- ~/Desktop/JRDLAppDev_John/Profile


{ paths }
- Can be written as absolute or relative paths
- Absolute Paths
- Points to the file/directory regardless of the current working directory
- Includes the root /
- Ex. /home/john/Documents/HTTF/blackhat.py
- Relative Paths
- Points to the file/directory starting from the current working directory
- Written without the root /
-
Ex. pwd == /home/john/
- Documents/HTTF/whitehat.py


{ basic bash }
- cd [folder] change directory
- ls list
- pwd print working directory
- touch [file] make a file
- mkdir [folder] make a directory (folder)
- less [file] read and display the contents of a file
- cat [file] concatenates files and prints the resulting contents into the terminal emulator
- mv [source] [dest] moves or renames the file
- cp [source] [dest] copies the source to destination
- rm [file] removes the file PERMANENTLY
- Case sensitivity matters!


{ bash syntax }
-
command -option [argument]
- The command is the command that Bash executes
- Ex. cd, touch, mkdir, ls
- The option is written after a dash (-), it allows you to undergo different ways of executing the command
- Ex. ls -a The a option lists all of the files, including hidden ones (files/directories beginning with a .)
- You can use multiple options at once, a la: pacman -Syu
- The argument is whatever you're passing into the command
- Ex. cd Desktop, passes in the Desktop argument to be cd'd into
- The command is the command that Bash executes
- Use spaces to separate commands, options, and arguments

{ manual }
- If you don't know how to use a command, use man command to open a manual for the command
- It tells you the syntax for that command
- The possible options
- What to pass in for arguments


{ navigation }
- cd [folder] will bring you to a certain folder
-
ls will list the contents of your present directory, so you can decide which folder to cd into next
- IF YOU DON'T KNOW WHERE TO GO, USE ls
- If you don't know where you are, use pwd
-
.. is the previous directory, so cd .. will take you a directory up on the file system. Go backwards
- Ex. You're in ~/Desktop/JrDLA
- cd .. will take you to ~/Desktop
- You can cd through/back multiple folder at once if you know the path
- Tab completion is your friend


{ valid file names }
- When naming folders/files do NOT:
- Have spaces in the middle of your filenames
- Hack to the Future
- In lieu of spaces, we use underscores or camel case
- ThisIsCamelCase
- Have spaces in the middle of your filenames
- File extensions don't matter in GNU/Linux
- File names that begin with . are hidden


{ exercise }
- cd to your Desktop
- On your Desktop, create a new folder with your first and last name
- Remember the file naming rule about spaces
- Inside the folder named after you, create three new folders: Project1, Project2, Project3
- Within each project folder, create:
- a file called "I_am_a_text_file"
- two folders: "python" and "c"
- within each python folder, create a file called "HelloWorld.py
- Within each project folder, create:
- Then delete all of the Project# directories with the rm command (using the r & f options)


{ treasure hunt }
- Let's put your newfound knowledge to use
- cd back to your Desktop
- git clone https://github.com/JHeadland/TreasureHunt
- cd TreasureHunt
- ls to view the contents of the directory
- cat or less the rules and begin!


{ break time! }


{ python }
- What is Python?
- Why are we using Python?
- Beginner-friendly
- Powerful
- Versatile
- You can hack and network using it
- A lot of hacking tools are written in Python



{ syntax }
- Basically grammar for computers
- We, as humans, can understand incorrectly structured English sentences
- We can extrapolate from data
- Computers read everything exactly as written, top-down
- There's a grammar for every language, including computer language -- it's called syntax


{ hello world }
- cd into Documents and make a directory named "python_work", cd into that
- Make a file called "hello_world.py"
- Edit the file (gedit hello_world.py) and type:
-
print("Hello world!")
-
- Launch your new program in the terminal!
- python3 file.py


{ data types }
- String
- "This is a string."
- Boolean
- True/False
- Integer
- whole numbers ex 5
- Float
- floating points ex 3.1415


{ operators }
- +, -, *, /, %, <, >
- Open up your Python interpreter and try it out
- Ex. Type "python3" into your terminal
-
>>> 5+5*10
- Note: Ctrl+D quits out of the interpreter back into the terminal emulator!


{ exercise }
-
Try to solve this math problem by typing one line into the interpreter:
- Suppose you do chores once a week, for which you get $10 allowance, and you have a part-time job which you do 5 times a week and get $50 — how much money would you earn in a year?


{ variables }
- In the interpreter type in:
-
>>> irene = 100
-
>>> print(irene)
-
- We just created a variable, called "irene"
- What is the data type of the variable irene?
- A variable is just something that stores value
- A variable varies, and can be reassigned. Try:
-
>>> irene = 200
-
>>> john = irene
-
>>> print(john)
-


{ variables }
- Variables must follow certain naming conventions
- NEVER start with a number
- NO spaces
- Use underscores or camel casing
- No special characters (*,.!@#;: etc)
- Syntax:
-
variableName = value
-


{ = vs == }
- = assigns
-
The value on the right gets assigned to the variable on the left
-
ex num = 10
-
- == compares values and checks for equality
- Returns True or False
-
ex num == 10


{ strings }
- Anything encased in quotes ("") is a string
- In Python, you just need to put quotes around the value
-
>>> fred = "This is a string"
-
>>> print(fred)
-
- You can use single quotes
- Be consistent
- Use double quotes if there is an apostrophe in the string
- You can concatenate things to a string with +
-
>>> str = "world!"
-
>>> print("Hello " + str)
-


{ tricks with strings }
- >>> print(20 * 'abcd')
- A "%" can be a placeholder for values:
- >>> mytext = 'I am %s years old'
- >>> print(mytext % 12)
- %s is used in the string, % to assign the value
- Other ways of using it
- >>> name = 'Joe'
- >>> print('Hello %s, how are you?' % name)
- When using multiple placeholders, use parentheses and commas to separate them
- >>> print("Hi %s how is %s" % ("Joe"," Jane"))


{ strings & variables }
- DON'T FORGET TO USE QUOTES FOR STRINGS
- If you just put a string without quotes, it'll be read as a variable name
- Ex. print("Hey Bob") prints the string "Hey Bob"
- print(Hey Bob) tries to print two variables with the names "Hey" and "Bob"


{ exercise }
Create three variables containing your first name, last name, and age. Then print a string as a cohesive sentence using all three (either by using concatenation or placeholders)
Ex. "Hello, my name is John Headland and I'm 20 years old."


{ lists }
- You can create a list object if you want to modify or access specific elements in the list
- >>> food_items = ['eggs', 'milk', 'cheese']
- >>> print(food_items)
- Access items by using brackets and the index
- Zero based
- >>> print(food_items[2])
- >>> food_items[1] = 'lettuce'
- To add to the end of a list, use .append(element)
- >>> food_items.append('chocolate bar')
- >>> print(food_items)
- Use parentheses instead of brackets to create a tuple (an immutable list)


{ range }
- You can use the range() function to create a list of numbers
- Put two numbers in the parentheses to create a list from the first number, to the second number minus 1
- Ex. range(4, 8) == [4, 5, 6, 7]
- Put one number in the parentheses to create a list from 0 to the number minus 1
- Ex. range(5) == [0, 1, 2, 3, 4]


{ slicing lists }
- If you specify the range of indices you want to work with, the list returns only those indices using a colon (:)
- Like the range function, it's the first number to the second number - 1
- Ex. players = ["Kirk", "Ross", "Dean", "Noah", "Irene"]
- player[0:3] == ["Kirk", "Ross", "Dean"]
- It returns a slice of the list!


{ exercises }
Create a list of pizza toppings of at least size 5. Print the message "My pizza has these toppings: " followed by the use of a slice to print the last three items of the list
Make a list of 3 people, living or deceased, that you would like to have dinner with. Then you realize your dinner table has grown in size! Append 2 more people to the list.


{ social engineering }


{ social engineering }


- Any act that influences a person to take an action against their best interest
- Also called "human hacking"
- Very general and very psychological
- It's used a lot against companies, because social engineering schemes could compromise much if just one employee falls into a trap.
- ex. Leaving a USB with the label "Executive Payroll FY 2016-2017" in a sitting area, that actually contains malware on it
- There are no technical safeguards against social engineering
- Phishing
- Trying to get information through fraudulent emails/phonecalls/other methods
- Pretexting
- Pretending to be someone else (giving something a "pretext" to gain access)
- Baiting
- Placing appealing lures and getting people to "take the bait", and get their information
- Quid pro quo
- Giving people an incentive/reward for giving you some information
- Tailgating
- "Piggybacking", taking advantage of other people/blending in with them to get access
{ real world examples }


- A Wal-Mart store manager in a small military town in Canada got an urgent phone call last month from "Gary Darnell"
- Darnell told the manager Wal-Mart had a multi-million-dollar opportunity to win a major government contract, and that he was assigned to visit the handful of Wal-Mart stores picked as likely pilot spots. First, he needed to get a complete picture of the store's operations.
{ real world examples }


Darnell asked the manager about all of his store's physical logistics: its janitorial contractor, cafeteria food-services provider, employee pay cycle and staff shift schedules. He learned what time the managers take their breaks and where they usually go for lunch.
Keeping up a steady patter about the new project and life in Bentonville, Darnell got the manager to give up some key details about the type of PC he used. Darnell quickly found out the make and version numbers of the computer's operating system, Web browser and antivirus software.
{ real world examples }


Finally, Darnell directed the manager to an external website to fill out a survey to prep for the upcoming visit.
The manager dutifully plugged the address into his browser. His computer blocked the connection, but Darnell wasn't fazed. He said he'd call the IT department and have it unlocked.
After thanking the manager for his help, Darnell made plans to follow up the next day. The manager promised to send Darnell over a list of good hotels in the area.
{ real world examples }


Then "Gary Darnell" hung up and stepped out of the soundproof booth he had been in for the last 20 minutes.
"All flags! All flags!" he announced, throwing his arms up in a V-for-Victory symbol.
His audience of some 100 spectators at the Defcon conference in Las Vegas burst into applause. They had been listening to both sides of the call through a loudspeaker broadcast.
{ challenge }

- Plan a real social engineering attack that we will execute on our local Walmart
- Obviously, you're children so you can't really impersonate management
- So, we the instructors will execute your plans
- You will research detailed information about Walmart and present a LibreOffice Impress presentation (like Ubuntu's Powerpoint) detailing how to you will extract as much information as possible from their managers
- You must be extremely detailed: script out exactly what you want us to say, how to respond in what situations (backup plans), how to spoof phone numbers, etc.
- Find out all the phone numbers and departments, fact check and think this through!
{ survey time }
- We would like to know what you learned/how you feel about the class
- We will NOT share your responses with anyone else
- You can feel safe sharing your honest opinions; no one will be offended or penalized
- Please be detailed and honest with your answers
- We want to make the class as fun as possible
- Be realistic, if you say something like "buy more TVs to play Overwatch" or "give us money", we will completely disregard anything ANYONE says
- Do not ruin this for your peers
- In Chromium, go to:
- https://www.surveymonkey.com/r/CXXSQ5Q
Hack to the Future Day 1
By jtheadland
Hack to the Future Day 1
- 857



