Web Security "Course"
- XSS, Clickjacking, Phising, MITM
Risks
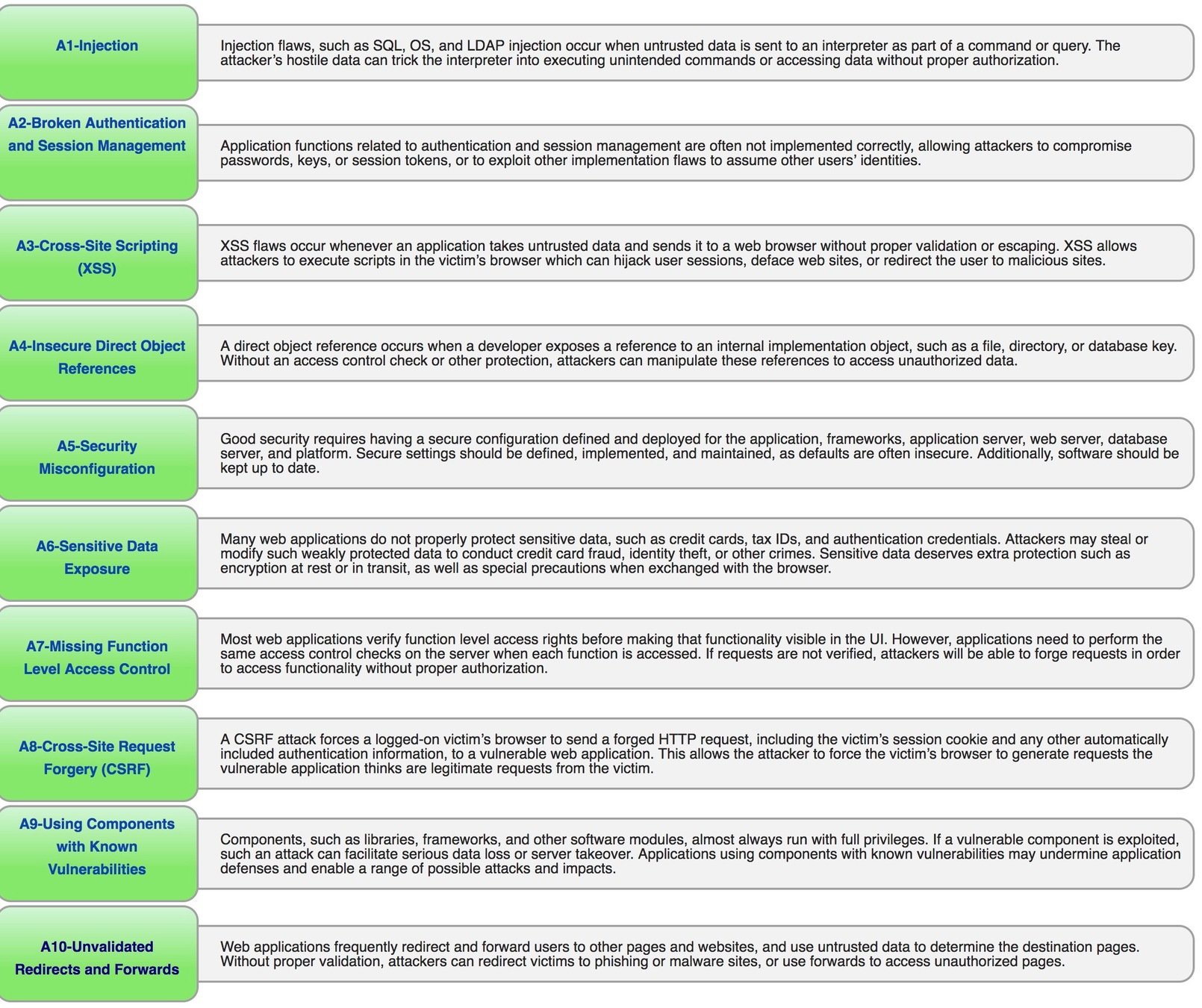
XSS
Clickjacking
Phising
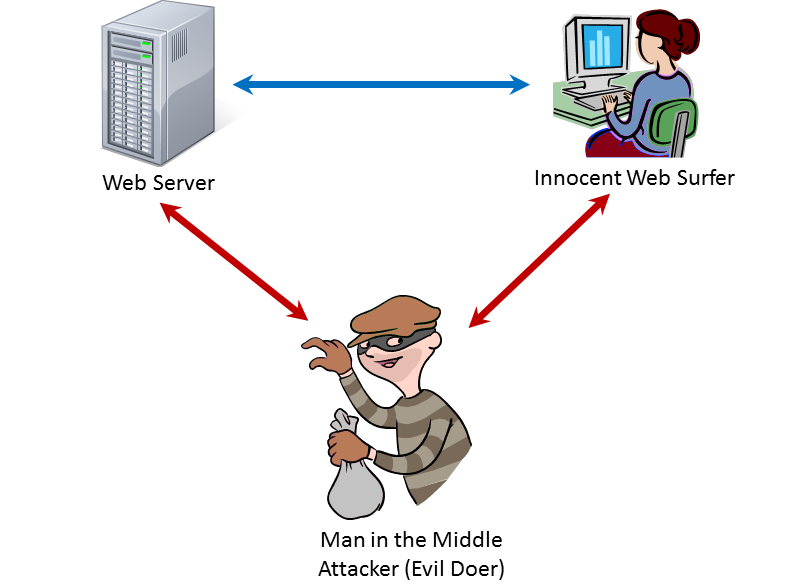
Man in the Middle Attack
Text
Defenses
- Sanitation, Escaping
- Security Headers:
- Content-Security Policy (CSP)
-
HTTP Strict Transport Security (HSTS)
-
HTTP Public Key Pinning (HPKP)
-
X-Content-Type-Options
-
X-Frame-Options
-
X-XSS-Protection
-
Referrer Policy
-
Subresource Integrity (SRI)
Sanitation, Escaping
Escaping must be context sensitive!
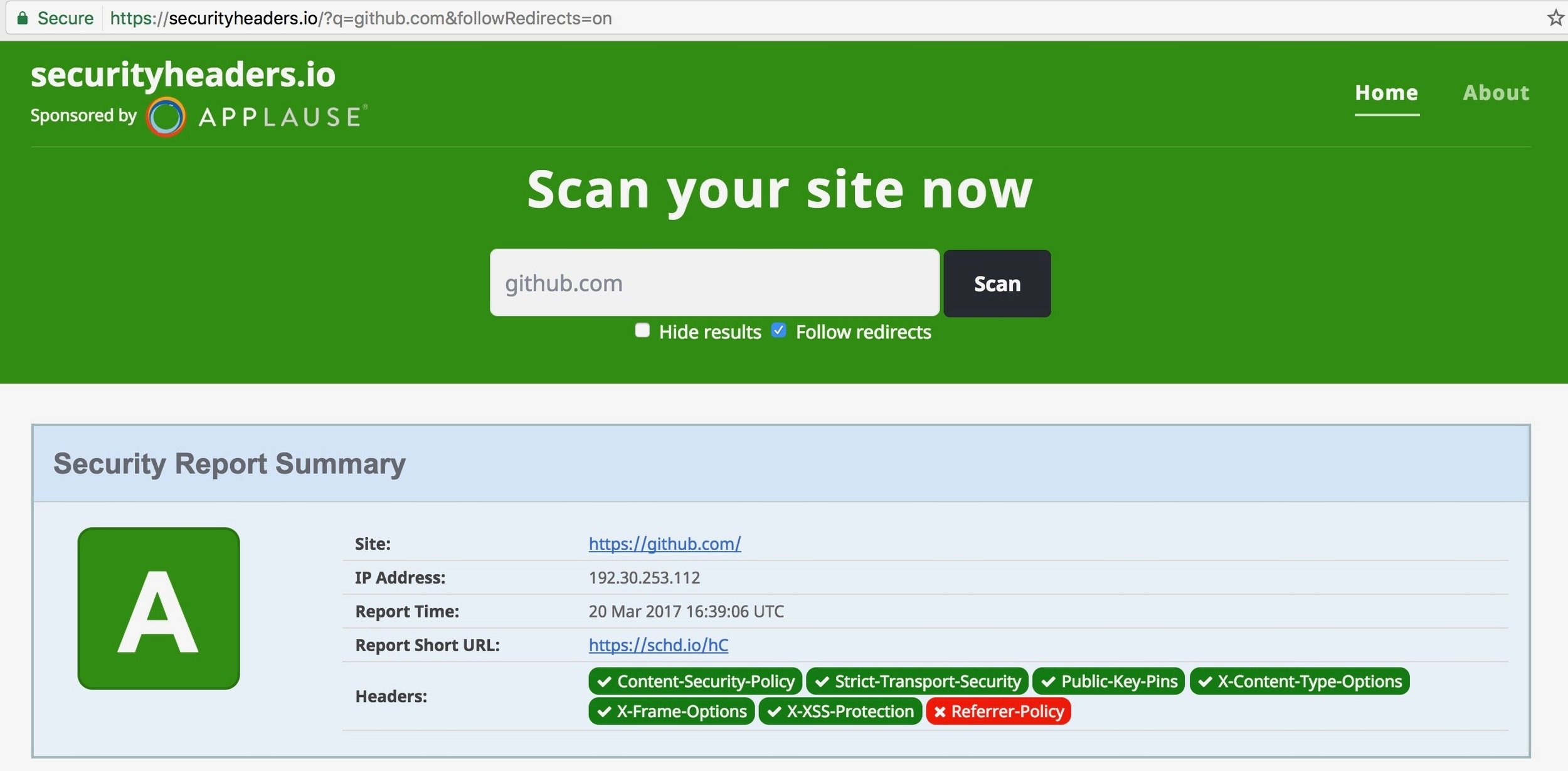
Security Headers
Content-Security-Policy:
default-src 'none';
base-uri 'self';
block-all-mixed-content;
child-src render.githubusercontent.com;
connect-src 'self' uploads.github.com status.github.com;
font-src assets-cdn.github.com;
form-action 'self' github.com gist.github.com;
frame-ancestors 'none';
img-src 'self' data: assets-cdn.github.com *.githubusercontent.com;
media-src 'none';
script-src assets-cdn.github.com;
style-src 'unsafe-inline' assets-cdn.github.comContent-Security-Policy:
object-src 'none';
script-src 'nonce-$random' 'strict-dynamic'
'unsafe-inline' 'unsafe-eval' https: http:;
report-uri https://yourreportingendpoint;Content-Security Policy
Strict-Transport-Security: max-age=31536000; includeSubdomains; preloadHTTP Strict Transport Security
- Serve a valid certificate.
- Redirect from HTTP to HTTPS on the same host, if you are listening on port 80.
-
Serve all subdomains over HTTPS.
- In particular, you must support HTTPS for the www subdomain if a DNS record for that subdomain exists.
-
Serve an HSTS header on the base domain for HTTPS requests:
- The max-age must be at least eighteen weeks (10886400 seconds).
- The includeSubDomains directive must be specified.
- The preload directive must be specified.
- If you are serving an additional redirect from your HTTPS site, that redirect must still have the HSTS header (rather than the page it redirects to).
Public-Key-Pins:
pin-sha256='X3pGTSOuJeEVw989IJ/cEtXUEmy52zs1TZQrU06KUKg=';
pin-sha256='MHJYVThihUrJcxW6wcqyOISTXIsInsdj3xK8QrZbHec=';
pin-sha256='isi41AizREkLvvft0IRW4u3XMFR2Yg7bvrF7padyCJg=';
includeSubdomains;
max-age=2592000HTTP Public Key Pinning
X-Content-Type-Options: nosniffX-Content-Type-Options
X-Frame-Options: SAMEORIGINX-Frame-Options
X-Xss-Protection: 1; mode=blockX-XSS-Protection
Referrer-Policy: Referrer-Policy: origin-when-cross-originReferrer Policy
SRI
References
- https://www.owasp.org/index.php/Top_10_2013-Top_10
- https://securityheaders.com
- https://report-uri.io/home/tools/
- https://www.troyhunt.com/owasp-top-10-for-net-developers-part-2/
- https://robinlinus.github.io/socialmedia-leak/
- https://www.troyhunt.com/clickjack-attack-hidden-threat-right-in/
- http://twig.sensiolabs.org/doc/2.x/filters/escape.html
- https://www.websec.be/blog/cspstrictdynamic/
- https://www.troyhunt.com/introducing-you-to-browser-security/
- https://scotthelme.co.uk/hardening-your-http-response-headers/
- https://scotthelme.co.uk/hsts-preloading/
- https://scotthelme.co.uk/hpkp-http-public-key-pinning/
- https://scotthelme.co.uk/a-new-security-header-referrer-policy/
- https://www.troyhunt.com/protecting-your-embedded-content-with-subresource-integrity-sri/
- https://githubengineering.com/githubs-post-csp-journey/
Web Security "Course" I.
By Máté Kocsis
Web Security "Course" I.
- 1,117



