Application layer (D)DoS attack and defense
13116754G
Guo Feng
www.leafonsword.org
Three Steps:
- Setup a website with CDN protected
- Launch (D)DOS attack
- Detect (D)DOS attacks
- Defend (D)DOS attacks
www.leafonsword.org

Hardware
CPU:1 core,2.3GHz
Memory:512M
DISK:4K random IOPS--5000 r/w
Bandwith:80Mbps(Download),25Mbps(Upload)
Protect by Cloudflare(or nexqcloud)
How:
Just change NS record to cloudflare(or nexqcloud)'s nameservers

Launch (D)DOS attack
With cloudflare(or nexqloud) protected

So must defeat CDN or bypass CDN's protection
bypass CDN's protection--Find real IP behind CDN(method 1)


bypass CDN's protection--Find real IP behind CDN(method 2)
By default dns resolver

bypass CDN's protection--Find real IP behind CDN(method 2)
Specified dns resolver

Find addtional information
By Whatweb

CMS:Ghost 0.4
Web Server:just node.js buildin webserver
Find Other website's information
By nmap

22 ssh
80 http
Consider attack purpose
Consuming something:
CPU
Mem
Disk
Bandwith
Consider 7 layer attack methods
- HTTP(s) Flood
- FTP
- SMTP Error DDOS
I Choose HTTP Get Flood
Types of Layer 7 DDOS web attacks
- HTTP GET
- HTTP POST
HTTP GET Flood
time-delayed HTTP headers to hold on to HTTP connections and exhaust web server threads or resources
Consider tools
Loic(loiq)
Hoic
OWASP HTTP Post Tool
SlowHTTPTest
Slowloris
Goloris
R.U.DY (R U Dead Yet?)
Example--Using loiq
- The loic clone in linux
- Three attacking ways:HTTP、TCP、UDP
- Self-define thread num and packet send speed

Before attack

Mem: 331M free
Network: <10kb/s
Disk: <100k/s
After attack
Tcpdump's output

After attack

Mem: 12.7M free
Network: >400kb/s
Disk: >2M/s
Detect (D)DOS attacks
Method one
Monitor resource consuming
CPU、Mem、Disk、Network......
DDOS => Resource consuming !
Resource consuming => DDOS ?
Method Two--Monitor connections
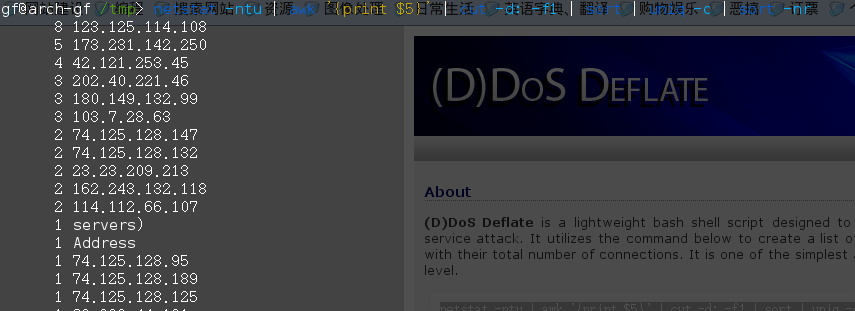
Defend (D)DOS attacks
Method One--timeout limits for HTTP headers
For Apache like web servers, waiting for the HTTP headers to complete sending is a basic and inherent behavior of web servers
So choose other web servers with timeout limits for HTTP headers,such as Nginx,IIS,lighttpd................
Apache could also use module(mod_antiloris)
Method Two--Limit Connections
Example--Nginx(ngx_http_limit_conn_module)
The ngx_http_limit_conn_module module is used to
limit the number of connections per the defined key, in
particular, the number of connections from a single IP address
http {
limit_conn_zone $binary_remote_addr zone=addr:10m;
...
server {
...
location /download/ {
limit_conn addr 1;
}
Method Three--Block Attacker
(D)DOS Deflate
- Iptables based
- maximum connections specified
- banning expiration time specified
When triggering definded connection limit:

Application layer DDoS attack and defense
By leafonsword
Application layer DDoS attack and defense
- 5,312
