AWS Architecture Design
Topics
What is/Why AWS?
How AWS?
The Challenges
Q&A
30m
30m
What is/Why AWS
Easy to use
Flexible
Cost-Effective
Reliable
Scalable
high-performance
Secure
The Challenges
| Scalability |
| High Availability |
| Fault Tolerant |
| High Performance DB Provisioning |
| Low Latency Content Delivery |
| Archival Inactive Objects |
| Security of Data at rest and in Transit |
| Secured Environment Access |
| Replicate Multiple Environments |
How AWS
Scalability



1 to N
Proxy & Heath Check
Elastic Load Balancing
EC2 Instance
EC2 Instances
Proxy & Heath Check
Automatic Scale



Min to Max
Elastic Load Balancing
EC2 Instance
EC2 Instances
Auto Scaling Group
Max to Min
Proxy & Heath Check
Proxy & Heath Check
High Availability


Elastic Load Balancing
EC2 Instances
ASG

EC2 Instances
ASG
Proxy & Heath Check
Proxy & Heath Check
Availability Zone
Region
Fault Tolerant


Elastic Load Balancing
EC2 Instances
ASG

EC2 Instances
ASG
Proxy & Heath Check
Proxy & Heath Check
Availability Zone
Region

Alert
Notify
Automatic Fault Tolerant (DB)

EC2 Instances
Availability Zone
Region

ASG
RDS

Master
Stand By
DNS Lookup
Data Sync

Alert
Notify
High Performance DB Provisioning
Availability Zone
Region

RDS

Master
Read-Only
Binary Log
Replication
Provisioned IOPS

EC2 Instances
ASG
Write
Read

Low Latency Content Delivery
US
AU
CN
JP
CA

CloudFront

S3



Static Objects
Buckets
Archival Inactive Objects
US
AU
CN
JP
CA

CloudFront

S3



Buckets

Glacier
Up to 3 - 5 hours
After 6 months
Download
Up to 3 - 5 hours
Security of Data in Transit (Internet)
HTTPs


S3
CloudFront

ELB
HTTPs Requests

EC2
HTTP/HTTPs Proxy
TLS v1.1 / 1.2
TLS Cert Installation
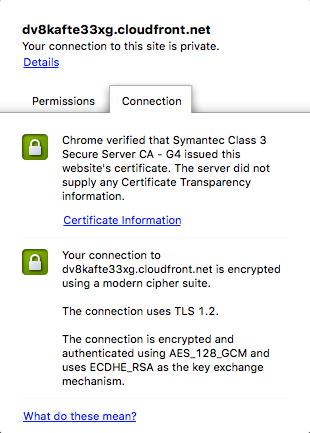
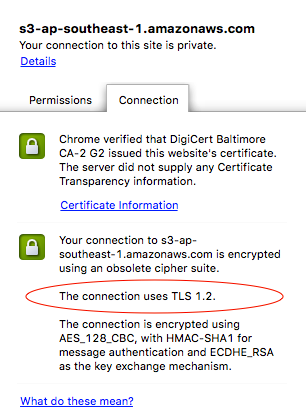
Security of Data in Transit (Internet)
Security of Data in Transit (Network)

ELB

EC2

RDS
Security Group
VPC
Security of Data at rest
Shutdown unnecessary services on your OS
Enable iptable rules to prevent external attacks on your OS
Prevent XSS and SQL injection in your code
Enable device-mapper crypt(dm-crypt) on your linux kernel
Cryptsetup tool is highly recommended
Secured Environment Access

EC2

RDS

S3

CloudFront

CloudWatch

IAM Policies

Glacier
Replicate Multiple Environments

EC2 Instances

EC2 AMIs

EC2 Instance
Create
Create
RDS Instance

Snapshot

RDS Instance
Create
Create

Introducing Elastic Beanstalk

EC2 Instances
ASG
Beanstalk

Beanstalk Application
Java
Node.js
Go
PHP
.Net
Python
Ruby

RDS

Git/Upload

EC2 Instances
ASG

RDS
Env Development
Env Production
Version Management
Introducing OpsWorks
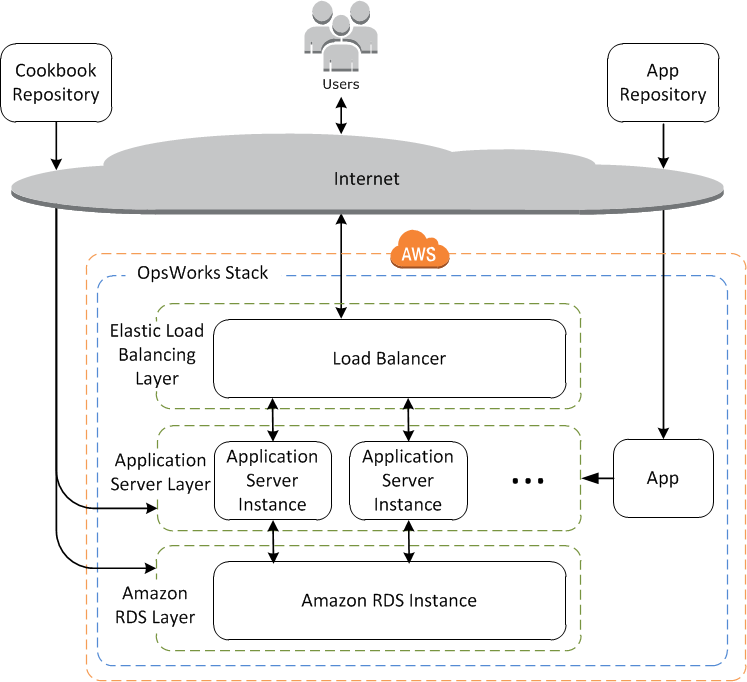
Introducing Ansible

AMI Management
Autoscaling Groups
CloudFormation
CloudTrail
CloudWatch
DynamoDB
ElastiCache
Elastic Block Store (EBS)
Elastic Cloud Compute (EC2)
Elastic IPs (EIP)
Elastic Load Balancers (ELB)
Identity Access Manager (IAM)
Relational Database Service
Route53
Security Groups
Security Token Service
Simple Storage Service (S3)
Virtual Private Cloud (VPC)



ELB
EC2
S3
AWS
Q&A
AWS Architecture Design
By Leon Li
AWS Architecture Design
A quick architecture solution for AWS platform
- 1,167
