Kong
What
Kong is an API gateway.
Text
Features of an API Gateway
- Routing: Sending requests to different destinations depending on the context or message content.
- Transformation: Components responsible for transforming or masking data.
- Inbound and outbound traffic monitoring and logging.
- Safety policies that add authentication, authorization, and encryption to APIs.
Why
Monolithic Architecture → Microservice Architecture
Monolithic vs. microservice projects
Pros of Monolith Architecture -
- Simplicity, for small codebases
- Faster early development speed
- Easy testing
Cons of Monolith Architecture -
- Not Ideal for growing codebases
- Slowing Iterations in the long term
- Harder to Innovate
- Steep code learning curve
Monolithic vs. microservice projects
Pros of Microservice Architecture -
- Better Architecture for large applications
- Better agility in the long term
- Microservices : easy to learn
- Isolation for scalability and damage control
Cons of Microservice Architecture -
- More moving parts
- Complex infrastructure requirements
- Consistency and Availability
- Harder to test

How
Kong is suite of software that utilizes OpenResty to dynamically configure NGINX and process HTTP requests.
Text
- NGINX provides protocol implementations and worker process management,
- OpenResty provides Lua integration and hooks into NGINX’s request processing phases, and
- Kong itself utilizes those hooks to route and transform requests.

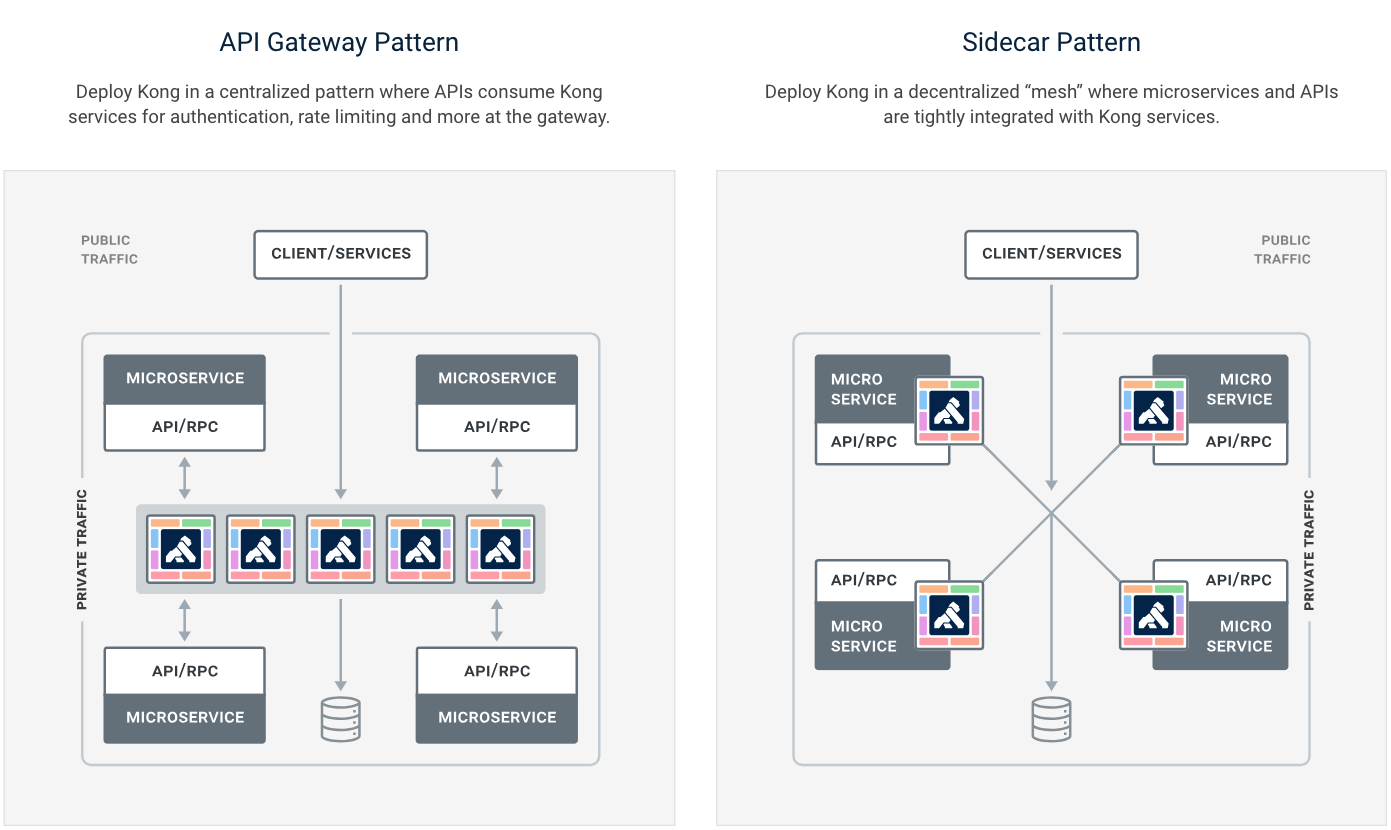
How
Demo
Entities
-
Service entities are abstractions of each of your own upstream APIs and microservices.
-
Route entities define rules to match client requests. Every request matching a given Route will be proxied to its associated Service.
-
Each Route is associated with a Service, and a single Service can have many Routes.
-
Plugins allow you to easily add new features to your API or make your API easier to manage.
-
Consumers are associated to individuals or applications using your API. They can be used for tracking, access management, and more.
Plugins
-
Key-Auth. 服务端之间的相互调用。
-
ACL. 不同的用户组配置不同的访问权限。
-
JWT. 客户端及第三方调用。
JWT使用流程
-
Kong上面针对服务或路由启用JWT插件。
-
JWT插件上配置consumer和credential。
-
客户端调用登录接口,服务端验证用户身份后从Kong上面获取JWT的秘钥,然后生成JWT的令牌,返回给用户。
-
客户端将令牌保存到本地,用于后续接口的调用。
Kong
By Liu Junfeng
Kong
- 625



