Intro to Reverse Engineering
Reverse Engineering
- Figuring out what a binary does
- Usually don't have access to source code
- Can (almost) always get disassembly
Why?
- Bypass copyright protection
- Accessing undocumented OS APIs
- Malware analysis
- Exploit development
- Jailbreaking/Figuring out how jailbreaks work
Whirlwind tour of x86 Assembly
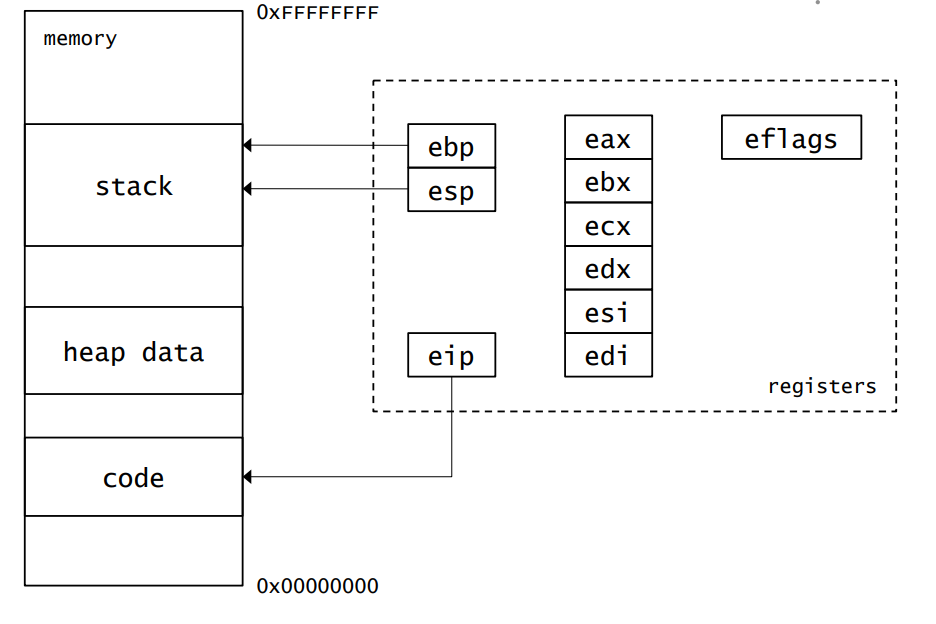
CPU Architecture
Graphic from https://github.com/isislab/Hack-Night/blob/master/2014-Fall/slides/sotirov-re-fall2011.pdf
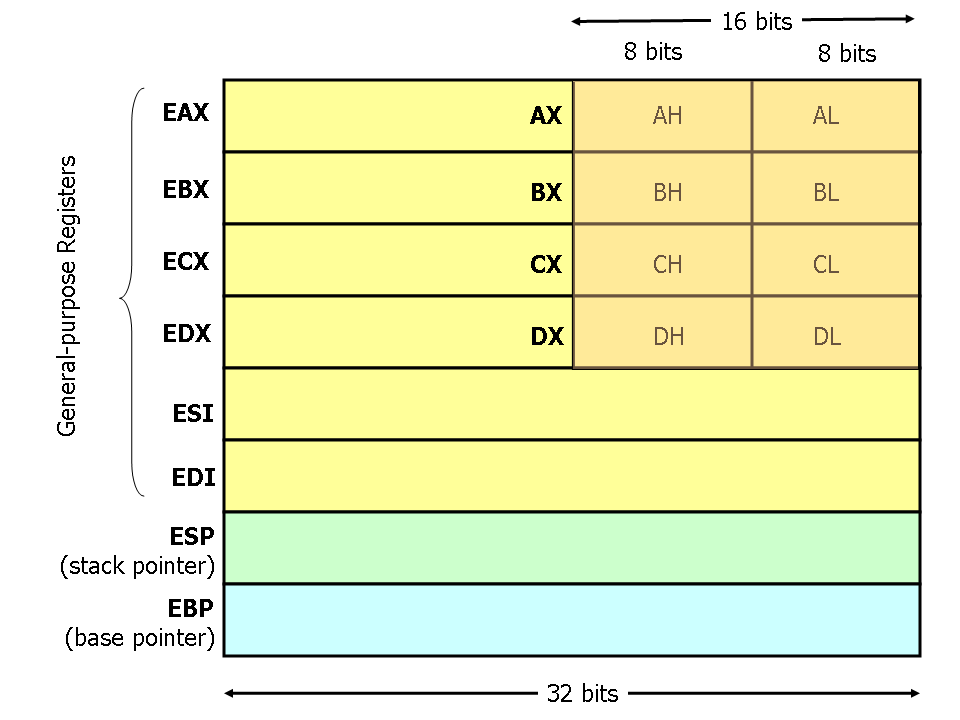
Moving Data
mov eax, ebx
mov byte ptr [var], 5push eax
push [var]pop edi
pop [ebx]lea edi, [ebx+4*esi]
lea eax, [var]mov
push
pop
lea
Arithmetic/Logic
add eax, 10
add BYTE PTR [var], 10add
sub al, ah
sub eax, 216sub
dec eax
inc DWORD PTR [var]inc/dec
imul eax, [var]
imul esi, edi, 25imul
idiv ebx
idiv DWORD PTR [var]idiv
and eax, 0fH
xor edx, edxand/or/xor
shl eax, 1
shr ebx, clshl/shr
not BYTE PTR [var]
neg eaxnot/neg
Addressing Memory
mov eax, [ebx]
mov [var], ebx
mov eax, [esi-4]
mov edx, [esi+4*ebx]
Move 4 bytes in memory at address in ebx into eax
Move contents of ebx into the 4 bytes at memory address var
Move 4 bytes at memory address ESI-4 into eax
Move 4 bytes at memory address ESI+4*ebx into eax
Control Flow
jmp begincmp eax, ebx
jle donecmp DWORD PTR [var], 10
jeq loopcall <label>
retjmp
je/jne/jz/jg/jge/jl/jle
cmp
call/ret
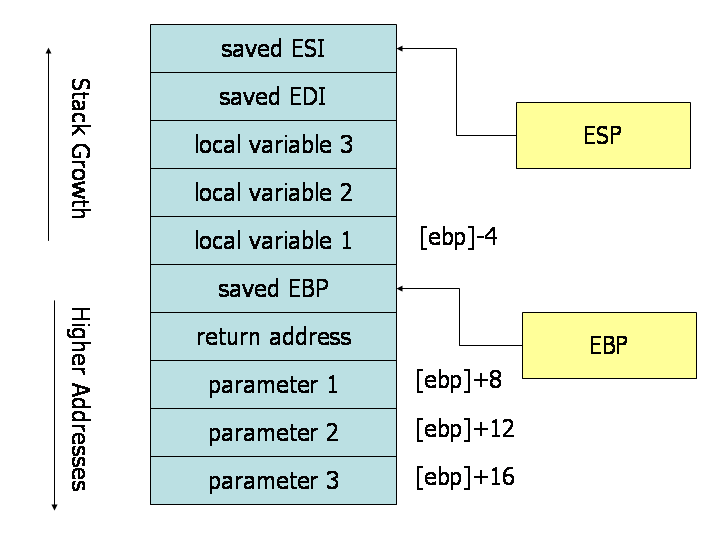
Caller Rules
- Save eax, ecx, edx
- Push parameters onto the stack, last parameter first
- Call the subroutine
Callee Rules
- Before executing the function body
- Push ebp onto the stack, copy esp into ebp
- Allocate local variables by decrementing esp appropriately
- Save ebx, edi, esi
- After executing the function body
- Save the return value in eax
- Restore ebx, edi, esi
- Deallocate local variables
- Restore ebp by popping it off the stack
- Return with ret
CMU Bomb Demo
Intro to Reverse Engineering
By Manas George
Intro to Reverse Engineering
- 715



