Exploiting and Fixing OWASP Top 10 Vulnerabilities in RailsGoat
Own Specialization Theme
Martin Markov
What is RailsGoat?
Vulnerable Ruby on Rails Application created by OWASP for educational purposes of Rails Developers

Research Questions
How are the present vulnerabilities in the RailsGoat application exploitable and what should be done to enhance the security of the application?
- What are the current vulnerabilities in the RailsGoat Application?
- How are they exploitable?
- What can be done to secure the RailsGoat Application and patch the present vulnerabilities?




Vulnerabilities in RailsGoat
- Injections (SQL injections & Command Injections)
- Broken Authentication and Session Management
- XSS (Cross-Site Scripting)
- Insecure Direct Object Reference
- Security Misconfiguration
- Sensitive Data Exposure
Missing Function Level Access Control
CSRF (Cross-Site Request Forgery)
Unvalidated Redirects and Forwards
SQL Injection
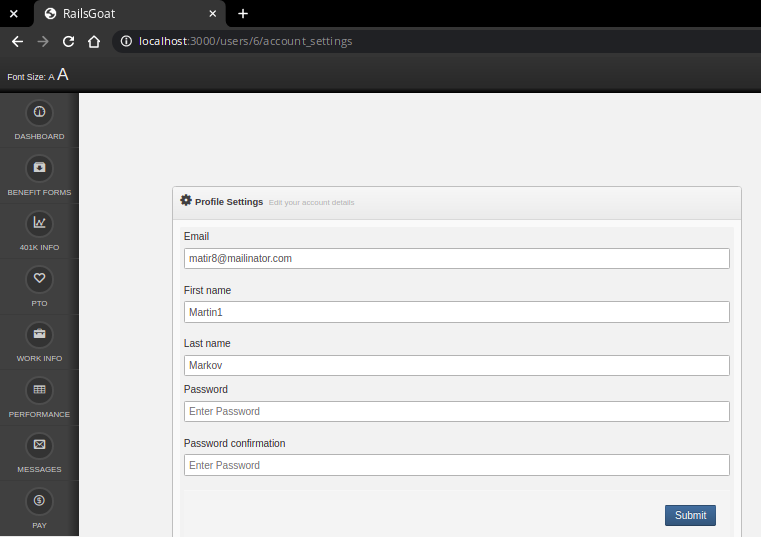
SQL Injection
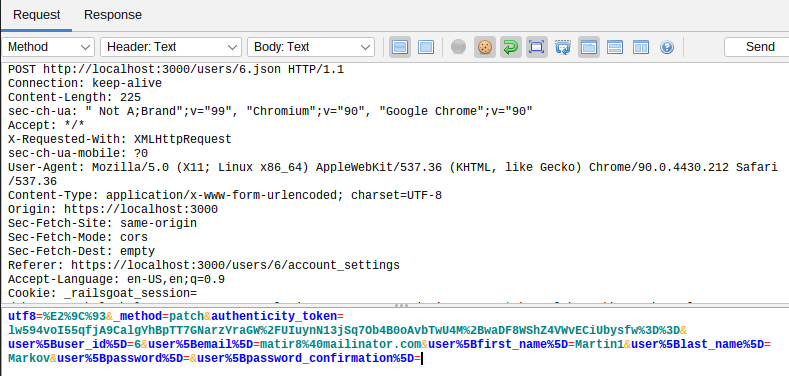
SQL Injection
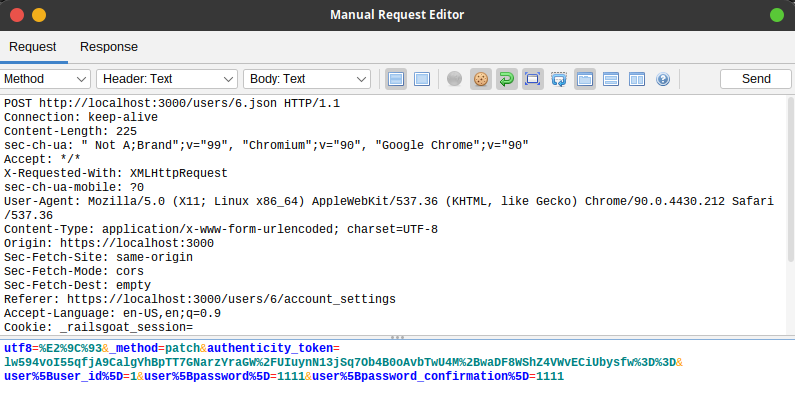
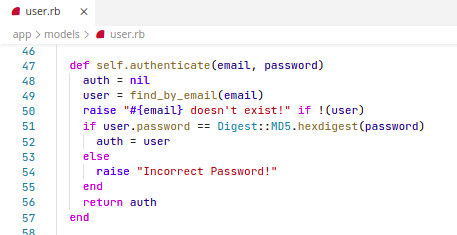
Setting the password of User with ID 1
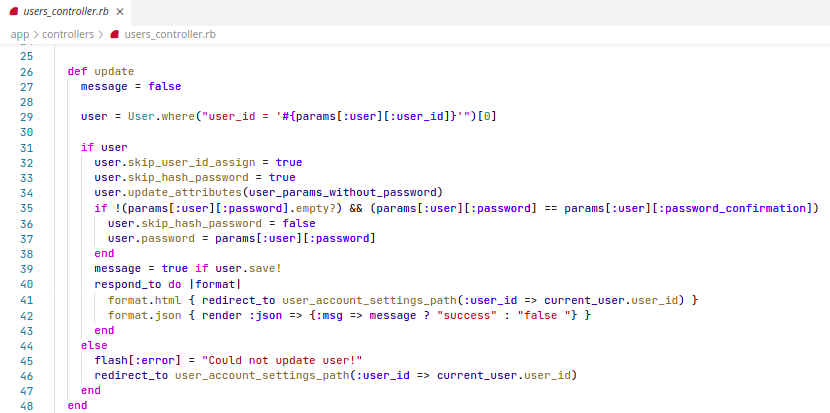
Problem
Solution
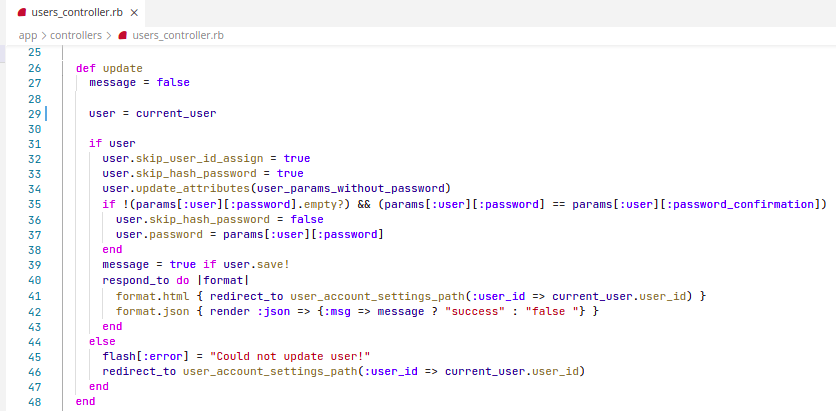
The current_user method
Command Injection
Command Injection
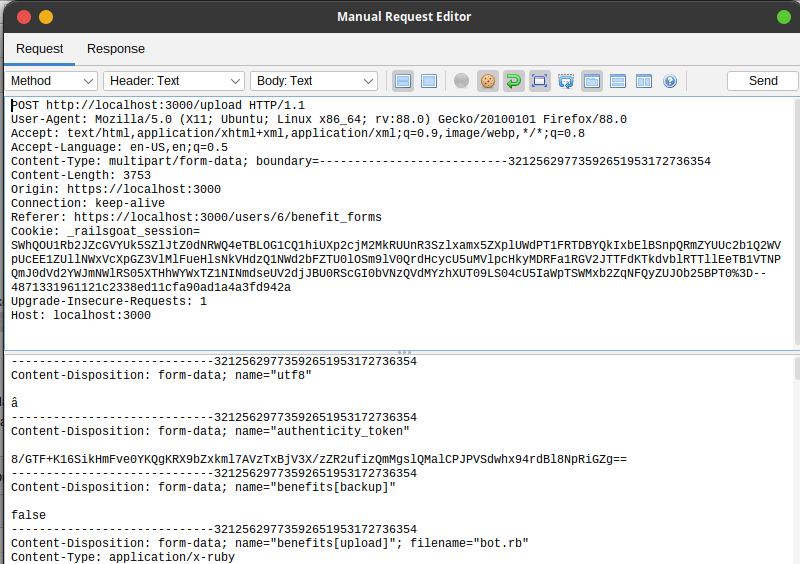
Command Injection
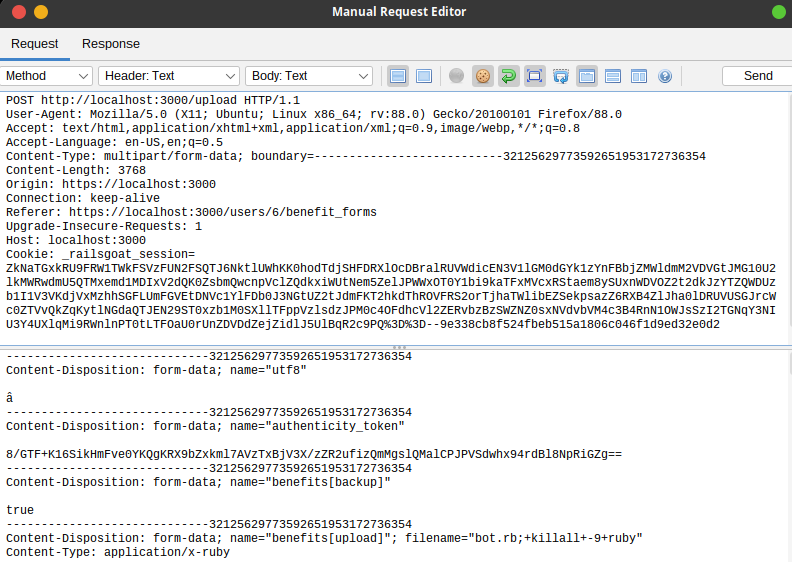
Command Injection
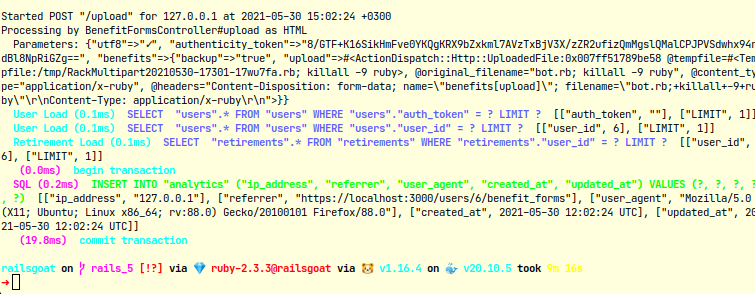
The application stopped because of execution of commands in file name
Problem
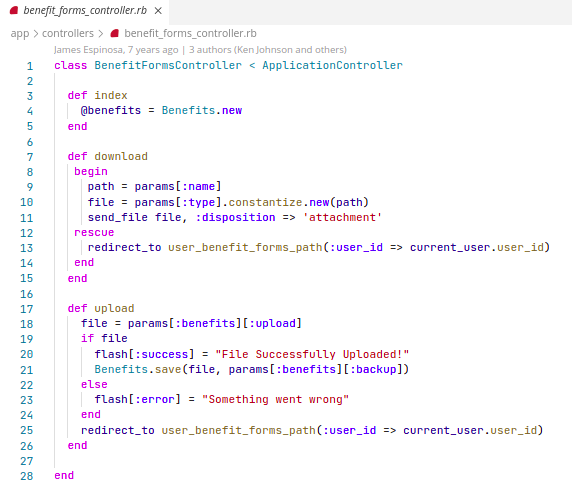
Problem
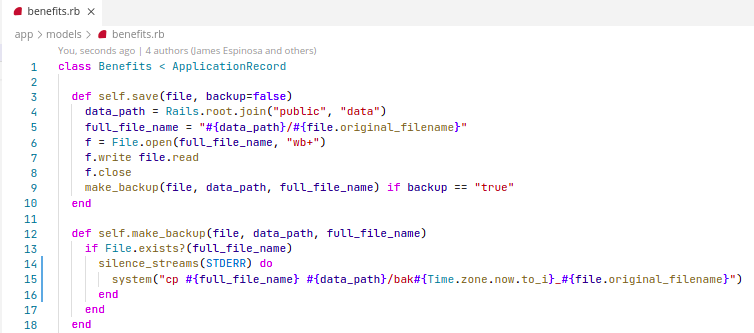
Solution
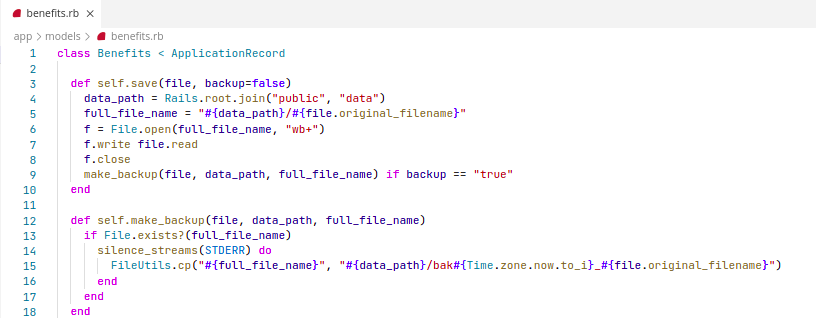
Using the safe FileUtils.cp() instead of directly executing system commands with user input
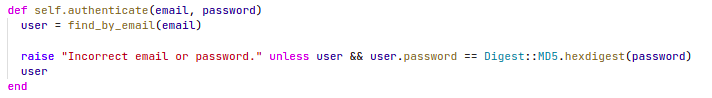
Broken Authentication and Session Management
- Overly explicit error messages give attackers feedback when trying to perform a brute-force attack
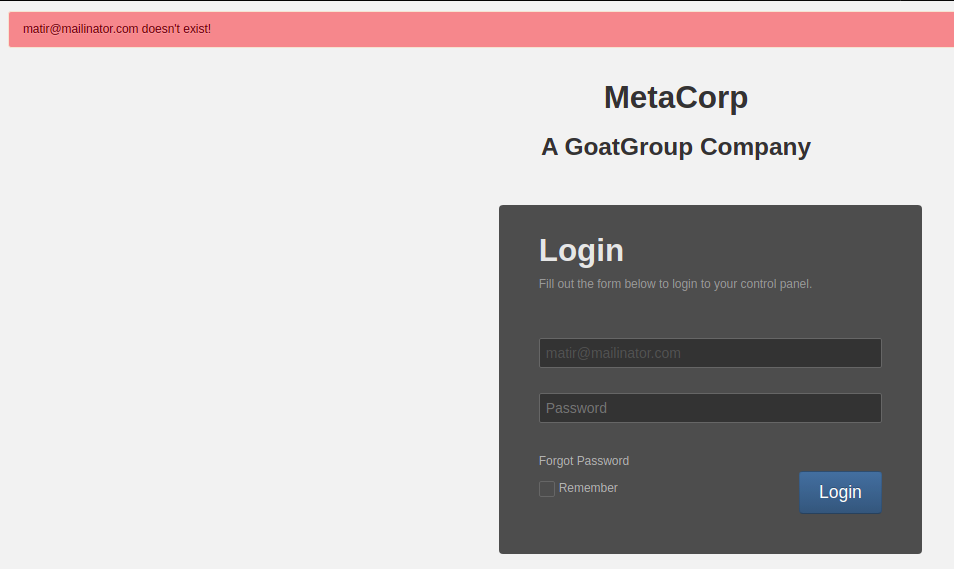
Broken Authentication and Session Management
- Overly explicit error messages give attackers feedback when trying to perform a brute-force attack
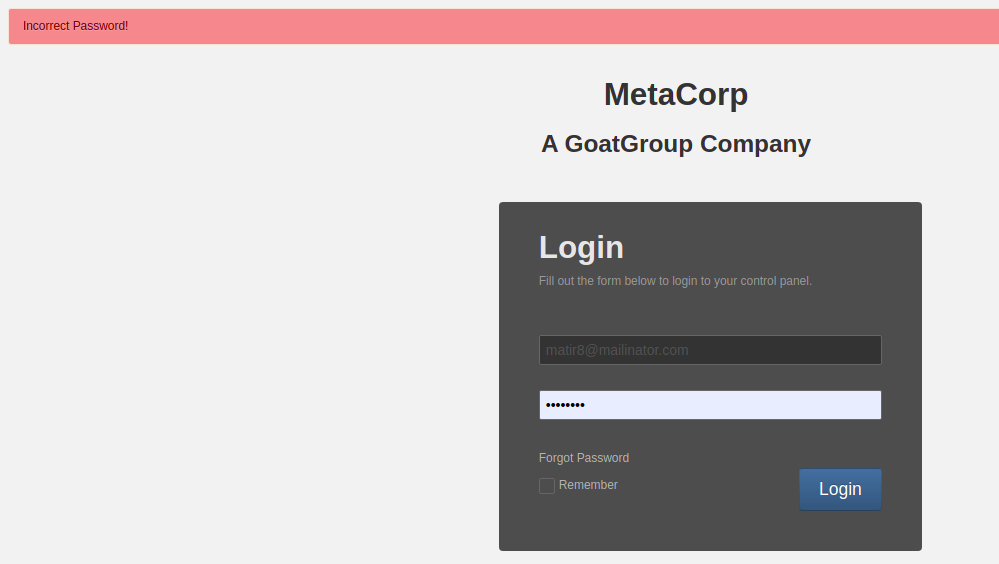
Problem
Concrete error messages for the authentication flow are a bad practice
Solution
If the authentication is not successful display a generic error message
XSS Attack
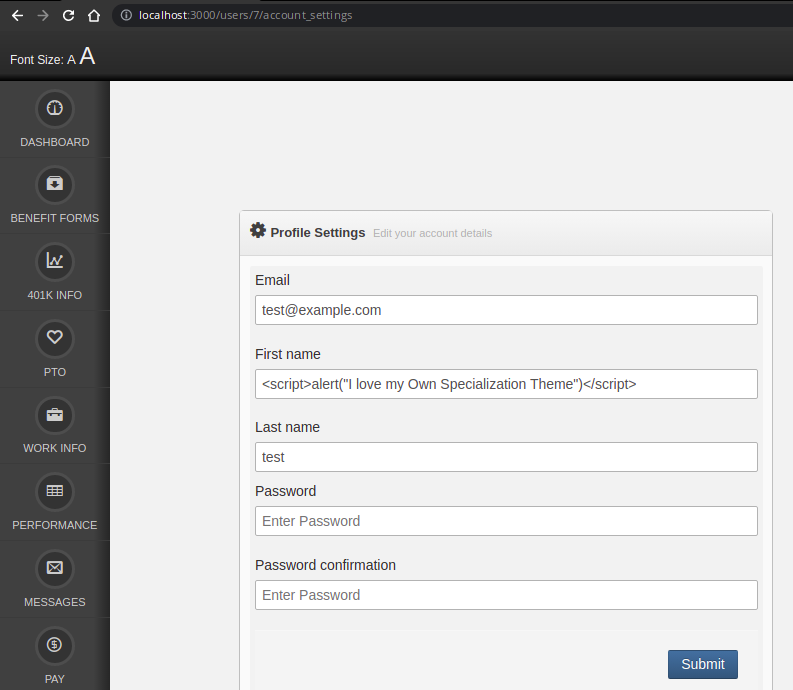
XSS Attack
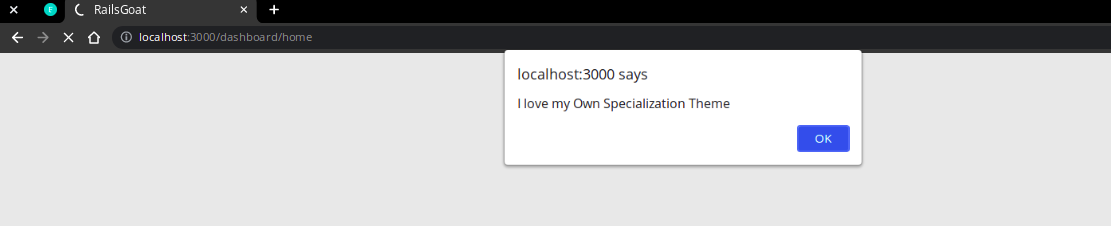
Problem
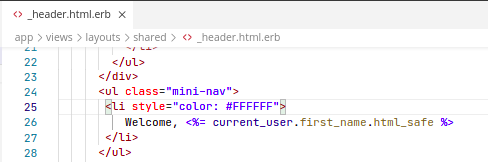
Instead of escaping the string, the html_safe method marks it as trusted and safe
Solution
- By default trying to render the string in rails would treat it as suspicious and escape it.
- However, if you want to render an HTML string, you can use the sanitize method with a list of trusted tags only
Insecure Direct Object Reference
Accessing sensitive information about another user because of trusting paramentrs sent to the server
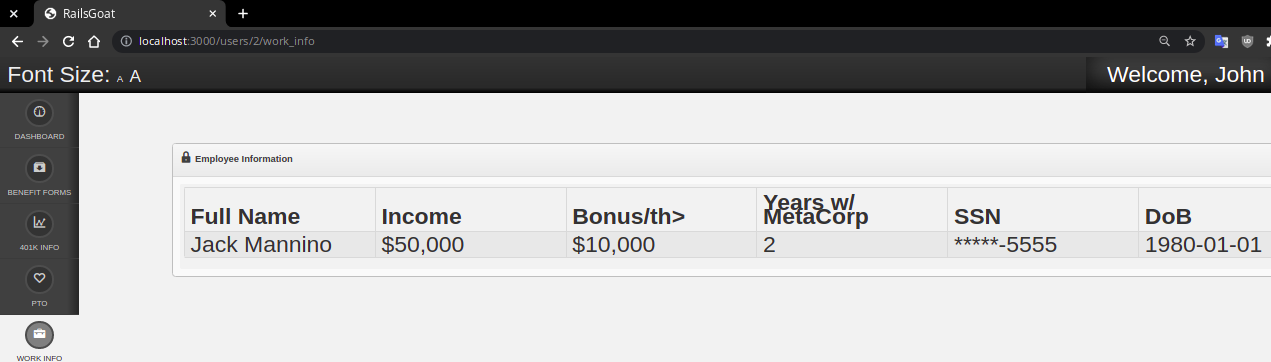
Problem
On line 3 the user_id is fetched from the params object. There's no check if this is the current_user's id
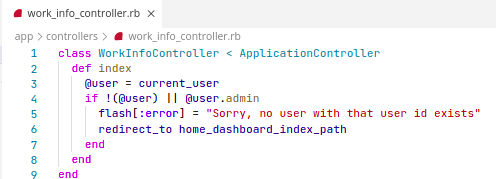
Solution
Directly using the current_user instead of fetching the user with the id sent in the request parameters
Security Misconfiguration
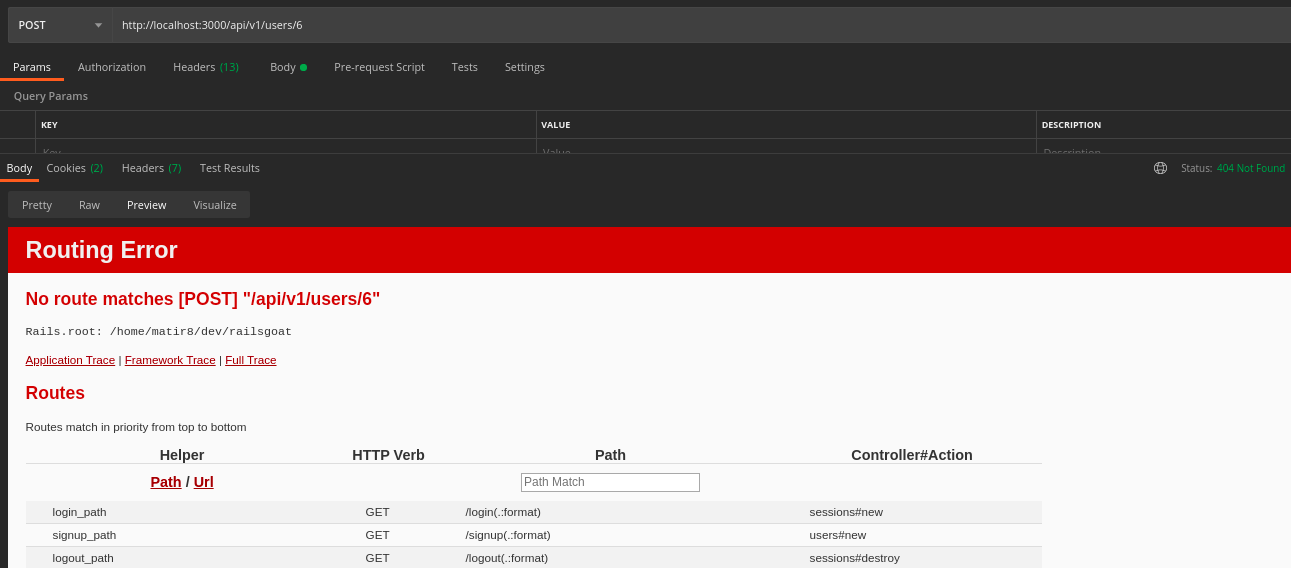
Exposing all available routes on 404 error
Problem
By following the default running instructions in the Readme file the application is running in the development environment which exposes all available routes on 404 routes
Solution
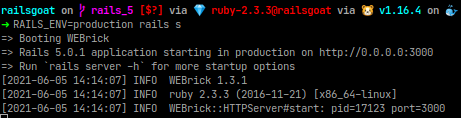
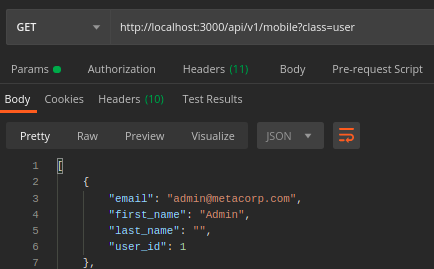
Sensitive Data Exposure
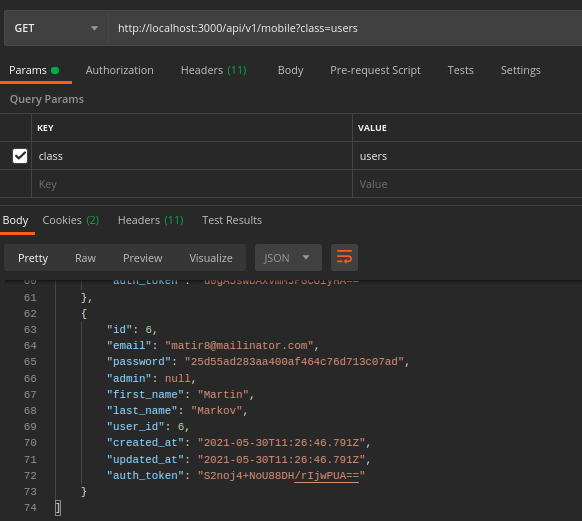
Problem
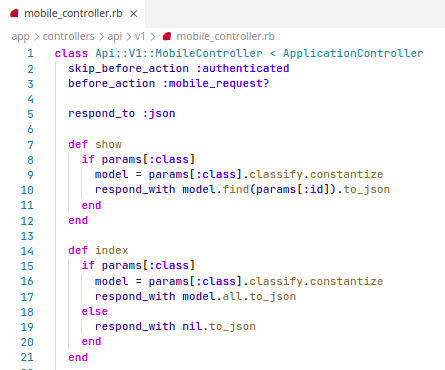
Solution
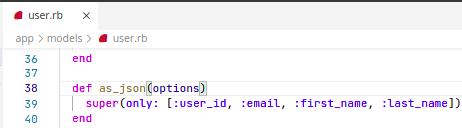
Overriding the default ActiveRecord as_json to only serialize the attributes needed
Missing Function Level Access Control
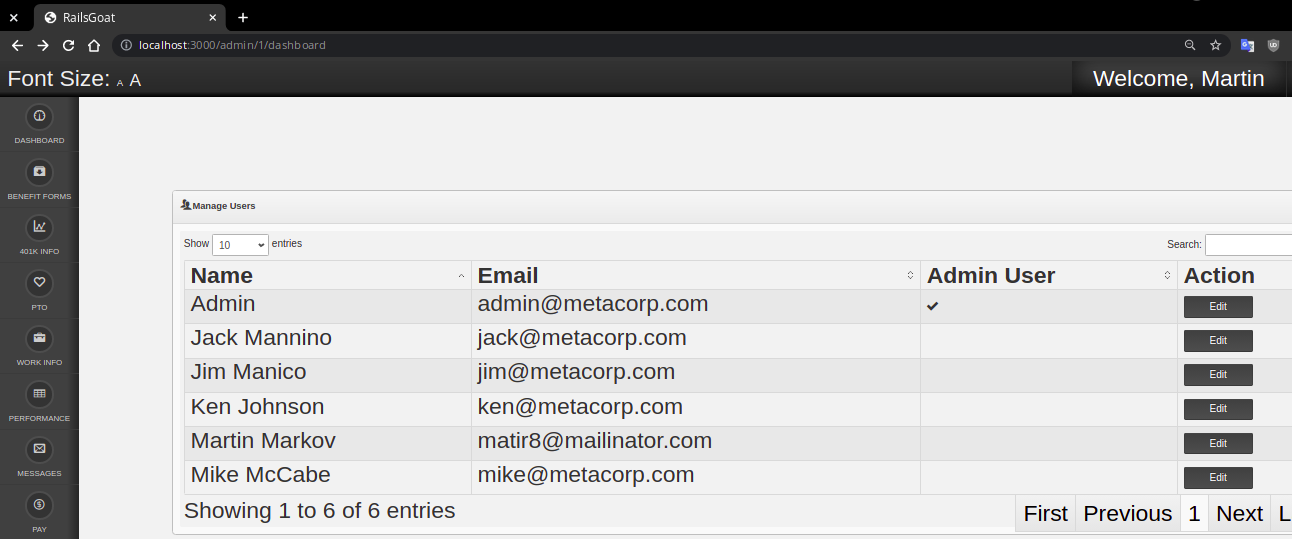
Problem
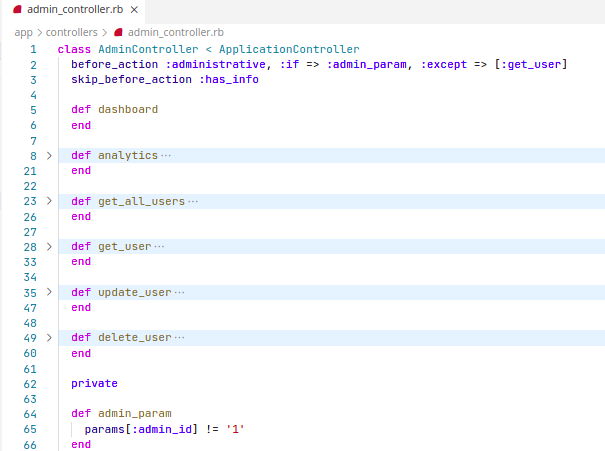
Solution
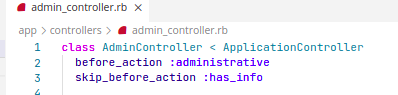
Apply the administrative guard function before every admin action to be sure that the admin endpoints are accessed only by users with the admin role
Cross-Site Request Forgery
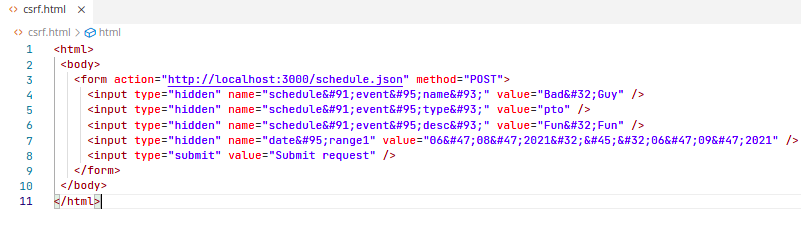
What if the target user is logged in to the RailsGoat Application, opens a page with this HTML and clicks the button?
Cross-Site Request Forgery
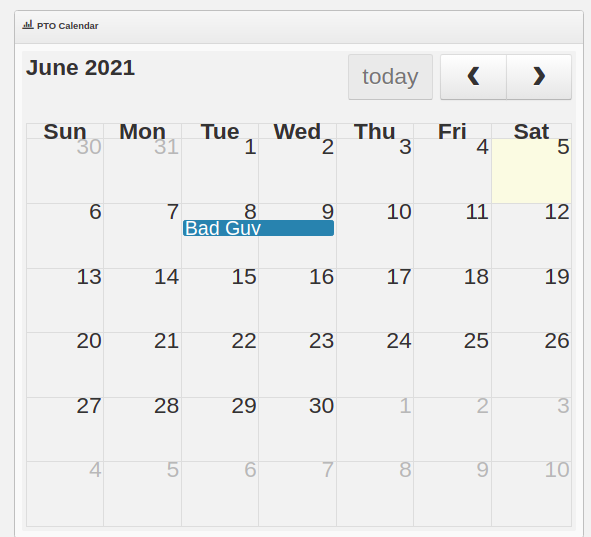
Problem
The application does not check for foregery requests
Solution
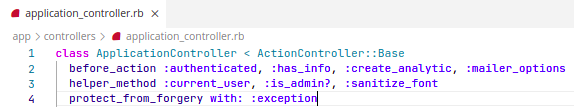
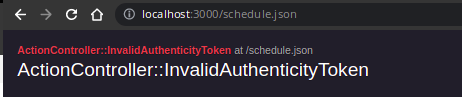
If we try the CSRF Attack again we'd get:
Unvalidated Redirects and Forwards
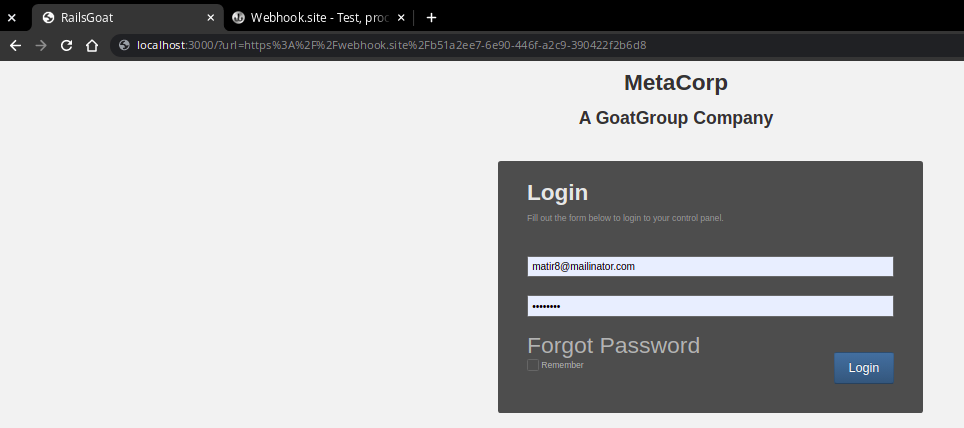
Problem
On successful login, the user will be redirected to the URL specified as a parameter (if there is one), no matter if it is in the same app or not
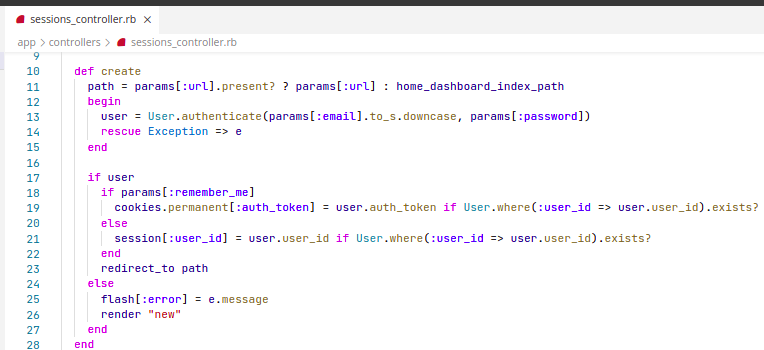
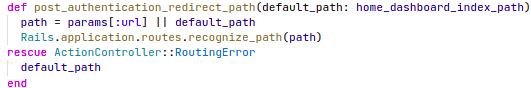
Solution
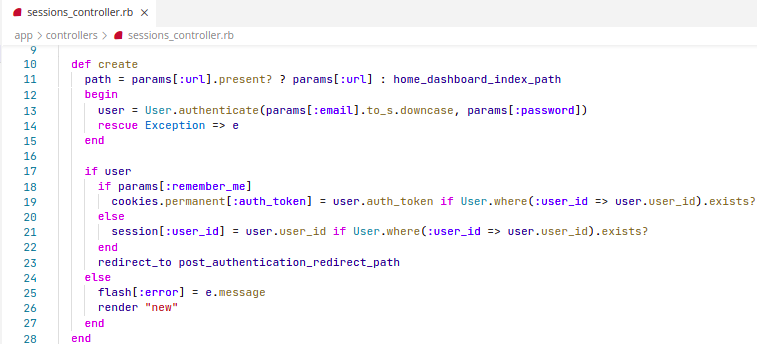
Reflection



Own Specialization Theme
By Martin Markov
Own Specialization Theme
- 21



