Matrix Intern Orientation
October 10, 2025

501c3 university non-profit initiative with seed funding from Weitz Innovation and Excellence Fund
Father, Dog Father, Husband, Software Engineer, CyberSecurity PractiTIoner, Teacher, Department Chair, STEM Evangelist, Researcher, Web Developer, Board Gamer, Philosopher, Artist
(roughly in that order)


A little about me...
Matt Hale, Ph.D. (mlhale@unomaha.edu)
Program Director, MATRIX
Associate Professor
Director, School of Interdisciplinary Informatics





Today
-
Welcome and Introductions (9-9:20)
-
Mission and Vision (9:20-9:40)
-
Getting started (9:40-10:10)
-
Rules & Conduct (10:10-10:20)
-
Break (10 mins), SOC Tasking (10:30-11)
-
Problem Resolution (11-11:20)
-
Curriculum (11:20-11:40), Q/A (11:40-12)
Welcome and
Introductions


- Name
- Background
- Something unique about you
- What you hope to learn during your time with MATRIX


Welcome and Introductions
Invent 1 gloriously useless product. Your product must focus on one of the problem areas, solve it for one target audience, and use any materials.

ICEBreaker: Collective Design
Problem Areas
-
Forgetting why you walked into a room
-
Dropping your phone on your face while lying down
-
Heating food and forgetting it in the microwave
-
Sitting down right before realizing you need something
-
Untangling headphones
-
Forgetting names 3 seconds after being introduced
Target Audience
-
Serial snooze button hitters
-
Parents of young children
-
Chronic overthinkers
-
Professional button mashers (“skip ad,” “remind me later”)
-
Reluctant morning participants
-
Frequent Googlers of “symptoms of…”
-
Gifted procrastinators
-
Dramatic sigh specialists
-
Overly confident DIY fixers (“Yeah, I can probably do that”)
Materials
-
Bubble wrap
-
Whiteboard markers
-
LED lights
-
Duct tape
-
Leftover pizza
-
3D printed plastic
-
Dorm mattress foam
-
Campus ID card scanners
-
Bluetooth speakers
-
Coffee cups
-
Extension cords
Example:
The Intent Reminder Helmet™
Helping people currently running on caffeine and hope to remember why they walked into a room using LED Strips, dorm mattress foam, and a bluetooth speaker.

ICEBreaker: Collective Design
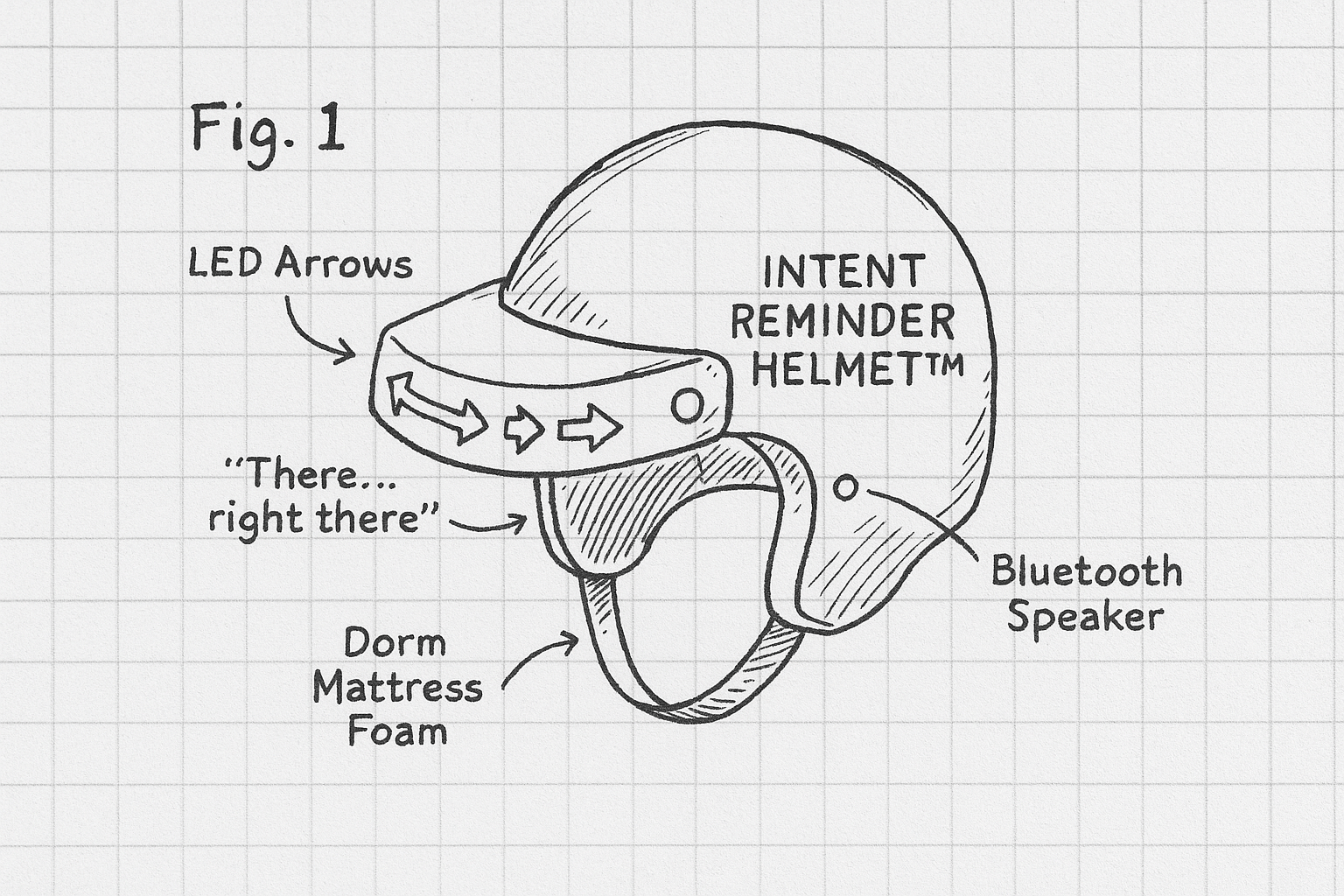
The user declares what they want into the bluetooth speaker/mic. When a user walks into the room, the visor drops down and shows an augmented reality arrow pointing to the object if it is detected. The speaker says "there right there" until the user says "got it". The dorm mattress foam prevents brain damage when the user bumps into things while using the visor.

ICEBreaker: Collective Design
Now find a partner, combine your gloriously useless products. Your new product must solve both problem areas at the same time for both of your target audiences, using all of your original materials.

ICEBreaker: Collective Design
Now integrate all of your designs together.

ICEBreaker: Collective Design
You get the idea...cohesive vision and clear design guidance are needed when working on a team.
Mission
and Vision


Upskilling Challenges and Opportunities


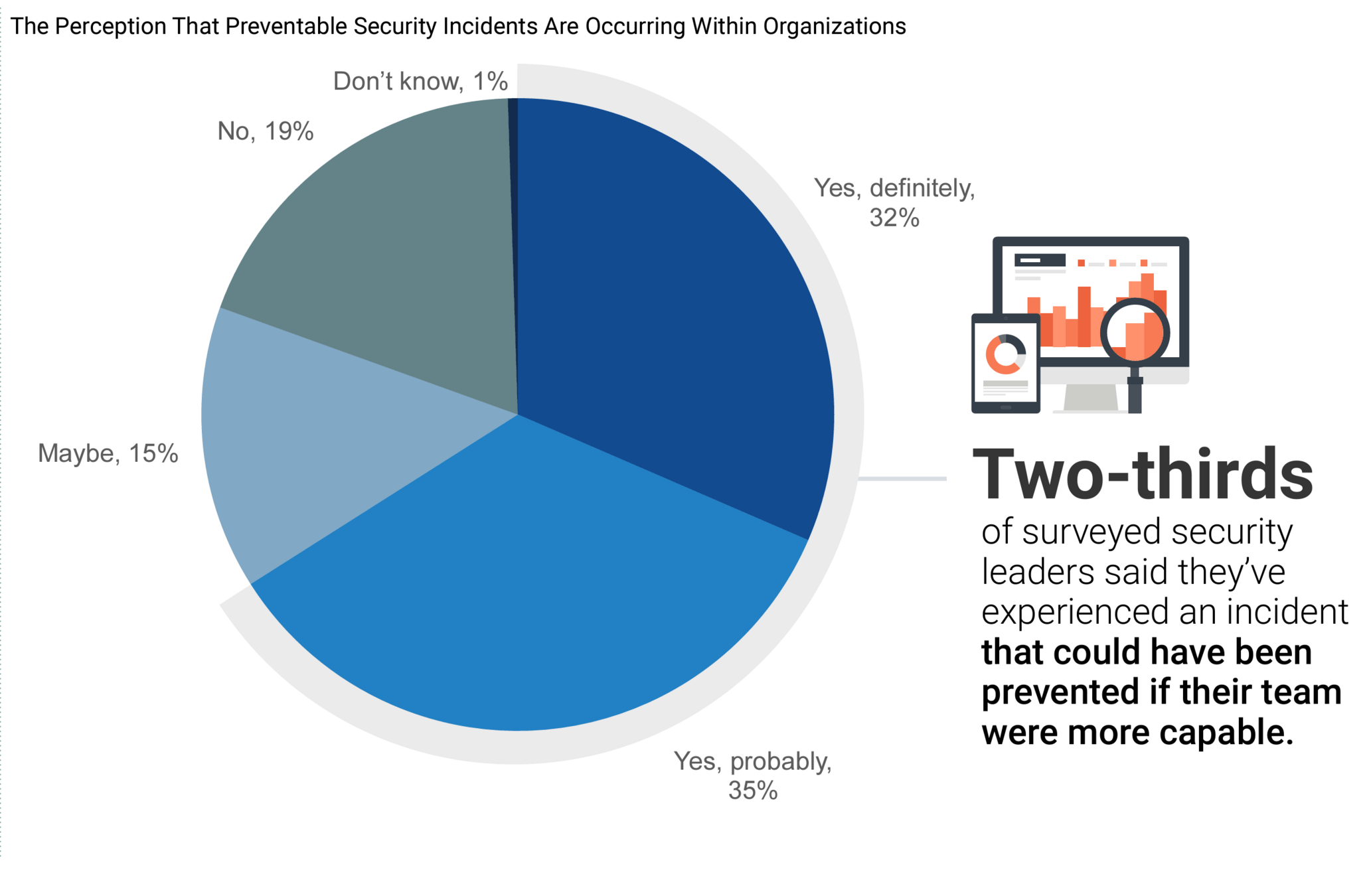
The challenge


Figure (c) 2023 Tech Target, Inc commissioned by Splunk
The Opportunity:
Upskilling and Workforce Development

-> Why Cant Companies close
the skill gap?

Unfortunately
-> Training IN CYBER Is HARD

- highly technical skills
- numerous tools
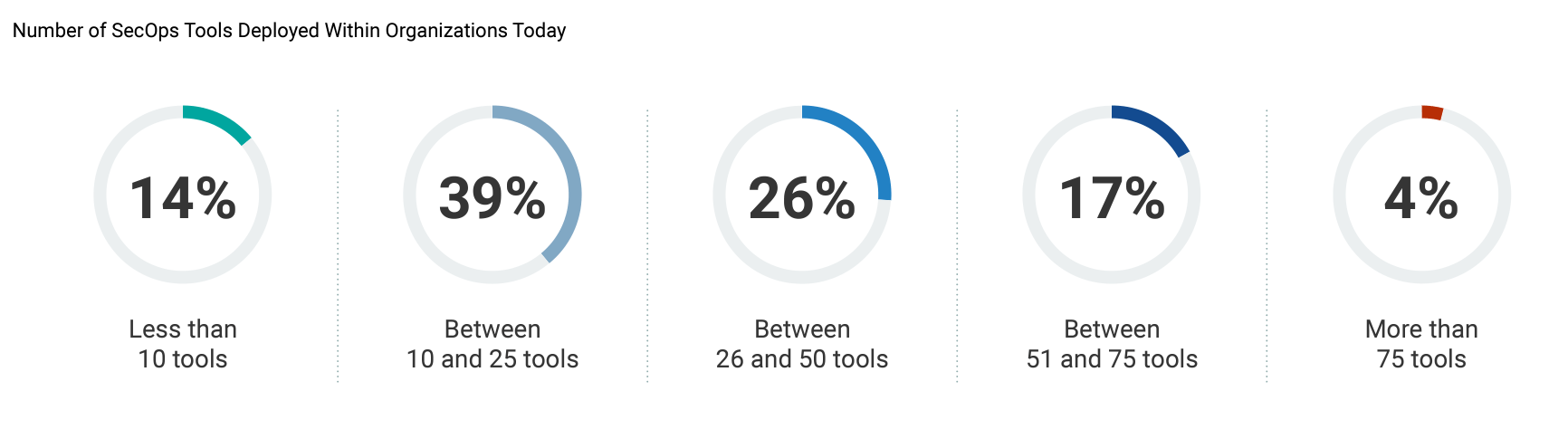

Figure (c) 2023 Tech Target, Inc commissioned by Splunk
Training in Cyber is Hard
- highly technical skills
- numerous tools
Training in Cyber is Hard


- highly technical skills
- numerous tools
Training in Cyber is Hard


- highly technical skills
- numerous tools

Training in Cyber is Hard


- highly technical skills
- numerous tools


Training in Cyber is Hard


- highly technical skills
- numerous tools



Training in Cyber is Hard

What we are doing about it


Novice
Expert
Companies want folks to be here
Folks start here
Skills in cybersecurity
Moving up the skill gradient requires knowledge and practice
Current CYBER workforce development Model
Novice
Current CYBER workforce development Model
Expert
Lanes of skill advancement
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Skills in cybersecurity
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Current CYBER workforce development Model
Novice
Expert
Skills in cybersecurity
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
Current CYBER workforce development Model
Novice
Expert
Skills in cybersecurity
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
Current CYBER workforce development Model
Novice
Expert
Skills in cybersecurity
CYBER workforce development Model (observations)
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
siloed, not mutually exclusive
requires hands on experiences for attack/defend skills
Novice
Expert
Skills in cybersecurity
workforce development Model (observations)
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
+ works with real data
+ highest skill ceiling
- can take a long time
- prone to groupthink
- hard to generalize
+ recognized credential
+ general knowledge
+ less groupthink
+ pedagogy expertise
+ expert mentorship
- opportunity cost barrier
- 4-6 years of time
- less modular
- "book" vs "real world"
learning
+ flexible and modular
+ deliverable online
+ short time commitment
+ industry credentials
- hard to generalize
- lowest skill ceiling
- lacks depth
Novice
Expert
Skills in cybersecurity
But what if...

...We want all of this
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
+ works with real data
+ highest skill ceiling
- can take a long time
- prone to groupthink
- hard to generalize
+ recognized credential
+ general knowledge
+ less groupthink
+ pedagogy expertise
+ expert mentorship
- opportunity cost barrier
- 4-6 years of time
- less modular
- "book" vs "real world"
learning
+ flexible and modular
+ deliverable online
+ short time commitment
+ industry credentials
- hard to generalize
- lowest skill ceiling
- lacks depth
Novice
Expert
Skills in cybersecurity
This brings us to the
NebraskaCYBER MATRIX Project
and our Learning Platform (VECTR)

MATRIX: ML, AI, and Threat Response Initiative
for Cyber eXcellence in Nebraska
VECTR: Virtual Education for Cybersecurity, Threats, and Risk
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
Novice
Expert
Skills in cybersecurity
Reimagining workforce development in CYBER
Lanes of skill advancement
Class1
Class2
Class3
ClassN
undergrad degree
Class1
ClassM
graduate degree
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Workshops / exercises
paired mentorship
experience
stackable modules
credential (e.g. CISSP)
Novice
Expert
Skills in cybersecurity
Reimagining workforce development in CYBER
Lanes of skill advancement
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Novice
Expert
Skills in cybersecurity
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Novice
Expert
Skills in cybersecurity
Lanes of skill advancement
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
a new skill advancement enabler
#NebraskaCYBER MATRIX
Novice
Expert
Skills in cybersecurity
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
a new skill advancement enabler
#NebraskaCYBER MATRIX
Breaking silos and serving all cyber training audiences
Novice
Expert
Skills in cybersecurity
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
a new skill advancement enabler
Novice
Expert
Skills in cybersecurity





How can we serve everyone, regardless of their incoming ability levels?
Reimagining workforce development in CYBER
Higher education (academic degrees)
On the job training / Internships
Certificates and micro-credentials
a new skill advancement enabler
Novice
Expert
Skills in cybersecurity
Baseline cyber competency threshold
#NebraskaCYBER MATRIX
Security Competency Platform
(Codenamed VECTR)
a new skill advancement enabler
Novice
Expert
Skills in cybersecurity
Baseline cyber competency threshold
Reimagining workforce development in CYBER
#NebraskaCYBER MATRIX
Security Competency Platform
(Codenamed VECTR)
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
a new skill advancement enabler
Novice
Expert
Skills in cybersecurity
Baseline cyber competency threshold
Reimagining workforce development in CYBER
#NebraskaCYBER MATRIX
Security Operations Center (SOC)
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
#NebraskaCYBER MATRIX
Security Competency Platform
(Codenamed VECTR)
a new skill advancement enabler
Novice
Expert
Baseline cyber competency threshold
Reimagining workforce development in CYBER
#NebraskaCYBER MATRIX
Security Operations Center (SOC)
(Student Intern Academy)
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
Nano
module
#NebraskaCYBER MATRIX
Security Competency Platform
(Codenamed VECTR)
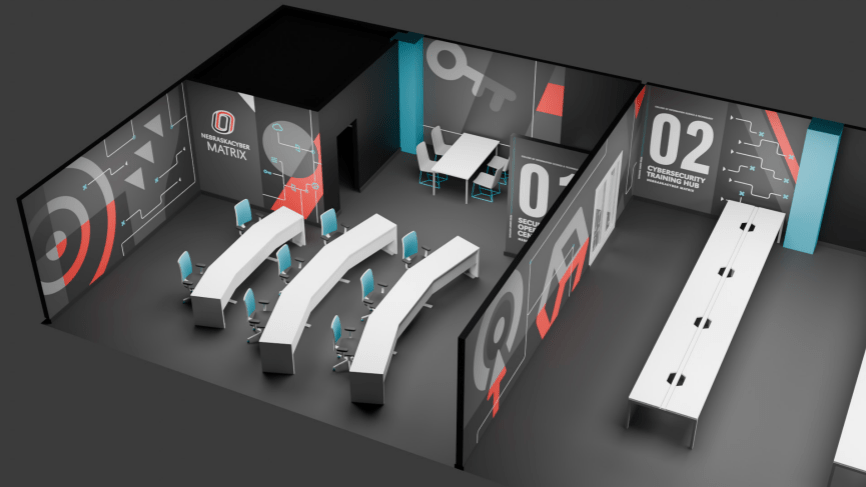
Skills in cybersecurity

(Oct'24-Jan.) Facility planning and Design
(Jun.) Facility Renovations started
(Apr.) Cyberengineer role filled
development/infrastructure setup began
(Sep. 19th): Facility renovations completed
(Oct. 6) First analyst intern cohort
(Aug.): VECTR beta test started
(Nov.) Grand opening and VECTR Launch

VECTR (beta) DEMO
https://nebraskamatrix.com/vectr/
Getting Started



- Machine access
- Tool access (slack, Github, shared drive, project mgmt board on Github)
- Logging your hours
- Identifying your work times and being present in the lab
Getting Started
Rules, Code of Conduct,
& Ethical Standards



MATRIX Student Employee Agreement
- Who: All MATRIX staff/student workers
- What: Confidentiality, responsible technology use, professional conduct, facility security
- Scope: facilities, systems, data, curriculum, and research activities
- Agreement document (internal)

1. Confidentiality & Non-Disclosure
- Use Confidential Information only for official MATRIX job duties.
- No sharing with third parties without written consent from the Program Director (Dr. Hale).
- Safeguard data with care; report suspected incidents immediately.
- Obligations survive employment unless released in writing.

1.1 Definition of Confidential Information
-
“Confidential Information” includes, without limitation:
-
Any data, datasets, data artifacts, or derivative outputs, regardless of format;
-
Any curricular modules, instructional content, training materials, or other educational resources developed under the MATRIX project;
-
Any details related to the VECTR architecture, infrastructure, or software code (including components, configurations, scripts, or deployment practices);
-
Any internal reports, communications, or documentation relating to investigations, assessments, prototypes, red-team findings, or threat intelligence;
-
Any research concepts, methodologies, intellectual property, or partner information disclosed or made available through MATRIX.
-

1.1 Definition of Confidential Information
-
Confidential Information does not include information that:
becomes publicly available through no breach by the Student;
was already lawfully known to the Student without restriction; or
independently developed by the Student without using or referencing MATRIX resources or Confidential Information.

1.2 Use & Protection
-
The Student shall:
-
Use Confidential Information solely for purposes of fulfilling their official MATRIX job duties;
-
Not disclose, share, transmit, or describe Confidential Information to any third party, including peers, friends, family members, faculty, or external entities, without prior written consent from Dr. Matt Hale (Program Director);
-
Exercise no less than reasonable care in safeguarding Confidential Information, equal to or greater than the care used to protect their own confidential materials;
-
Immediately report any suspected or actual unauthorized disclosure or access to the Program Director.
-

1.3 Survival
The confidentiality obligations in this Agreement survive termination or conclusion of employment indefinitely, unless explicitly released in writing by UNO/MATRIX.

2. Responsible Use of Technology & AI
2.1 Approved Tools Only
-
Public-facing AI tools, including ChatGPT (free/personal account), Gemini, Claude, Copilot (personal edition), or similar public LLM services, are strictly prohibited for any MATRIX-related work.
-
The only permitted AI tools are those explicitly licensed and provisioned by UNO/MATRIX, such as the GPT Enterprise license issued by UNO. All use must comply with internal logging and policy constraints.

2.2 Prohibted Behavior
The Student shall not:
-
Upload or paste any MATRIX-related data, content, notes, or code into any public or non-approved AI system;
-
Install any unauthorized software, extensions, plugins, or executables on MATRIX machines or networks;
-
Use MATRIX computing, networking, or storage systems for personal projects, academic coursework, entertainment, or unrelated experimentation.

2.3 Workstation and Device Security
The Student is responsible for maintaining the physical and digital security of all MATRIX-issued or MATRIX-accessed systems. Accordingly:
-
All workstations, laptops, virtual environments, terminals, and remote sessions must be locked or logged out whenever left unattended, even briefly.
-
Auto-lock timers shall not be disabled or extended beyond approved security policy limits.
-
No credentials may be stored in unsecured plaintext locations (e.g., sticky notes, unencrypted files).
-
USB drives, portable media, or external devices may not be connected unless explicitly authorized.
-
Wireless connections must be made only through approved, secure MATRIX or UNO networks—no tethering, hotspots, or unsecured Wi-Fi.

3 Professionalism, Conduct, & Safety
-
The Student shall conduct themselves with professionalism and ethical responsibility at all times — especially when reviewing, investigating, or responding to cyber events or real-world threat intelligence.
-
Under no circumstances may the Student test, probe, or access external systems without explicit written authorization.
-
The Student shall not discuss or speculate publicly (including on social media or informal conversation) about any active or past MATRIX cyber event assessments or operational activities.

3.1 Authorization before Action
-
No scanning, probing, testing, packet capture, credential harvesting, OSINT targeting, or exploitation—of any system—may occur without explicit authorization from the MATRIX Program Director or designated supervisor.
-
Assumptions such as “it’s publicly accessible” or “it’s for research” do not constitute permission.
-
Authorization must identify the system, approved tools, scope of interaction, and permitted level of intrusion.

3.2 Scope Discipline ("DO No Harm")
-
Testing must never exceed the explicitly defined scope.
-
Discovery of vulnerabilities or access beyond expectation must be immediately reported—not explored further.
-
No lateral movement, privilege escalation, data exfiltration, or backdoor placement is permitted unless expressly part of an approved engagement.

3.3 No Real-World Impact Testing without Clearance
-
Denial-of-service testing, phishing simulations, social engineering attempts, or physical intrusion techniques are strictly prohibited unless formally approved and coordinated.
-
Third-party systems, personal accounts, or university services are entirely off limits unless they are part of a written testing scope.

3.4 Data Handling
-
If sensitive or unexpected data is encountered during authorized work:
-
Do not open, analyze, or retain it beyond what is required to confirm existence.
-
Immediately report the discovery to your supervisor
-
-
Never download, share, or archive discovered information for personal use, demonstration, or academic curiosity.

3.5 Public disclosure & External Communication
-
The Student shall not disclose vulnerabilities, screenshots, indicators, write-ups, or lessons learned publicly or privately unless given explicit clearance to do so.
-
No publishing on GitHub, Reddit, LinkedIn, Discord, conference talks, CTF writeups, or other publishing venues without written approval.

3.6 Intent Matters - But Outcomes Matter More
-
Even if the Student believes an action is educational, harmless, or beneficial, unauthorized security testing is treated as an incident—not an experiment.
“If you don’t have written permission, you don’t have permission.”

4 Facility Security and Clean Room Expectations
-
MATRIX facilities are restricted-access environments.
Students shall not allow any individual to tailgate or enter without badging.
Any visitor or guest must be pre-approved by MATRIX administration. -
Workstations and desks must be kept clean, orderly, and free of sensitive documents when unattended.
-
No physical materials, screenshots, or printed data may be removed from the MATRIX space unless explicitly authorized.
-
Students are welcome to leave small personal items on their desk, but students are responsible for safeguarding their own valuables, don’t leave them on your desk, use a locker.

5 Return or Destruction of Materials
Upon separation from MATRIX employment or upon request, the Student shall:
-
Return or permanently delete all Confidential Information in their possession; and
-
Certify in writing that no unauthorized copies remain.

6 Acknowledgement of Accountability
Violation of this Agreement may result in:
-
Immediate termination of MATRIX employment;
-
Referral to the UNO Office of Student Conduct and/or IT Security;
-
Potential legal action, where applicable under federal, state, or university policy.
Discussion: Scenarios


Friend wants to hang out with you, do homework, while you work


While Testing, you find a vulnerability in a Web app that allows you to fetch and use an Admin Session


Looking over network traffic, you notice what appears to be a plaintext username and password going to a service you're familiar with


Someone knocks on the door. They are with the Networking team and need to fix a port on the wall


Per-Person SOC Tasking
WorkPlan Roadmap
(JOSH)


PRoblem REsolution and Tasking Workflow


- Work with peer first
- Create a ticket
- Contact staff during office hours (see schedule)
- Emergency/time-critical issue -> alert immediately
Curriculum Development
(Derek)


Open Q/A
Matt Hale, PHD
Program Director, MATRIX
Associate Professor, Cybersecurity
Director, School of Interdisciplinary Informatics
Director, NebraskaCYBER
mlhale@unomaha.edu
©2025 Matt Hale / MATRIX / UNO

nebraskamatrix.com
MATRIX Orientation
By Matt Hale
MATRIX Orientation
MATRIX Orientation
- 83



