Configuring serverless applications with secret values
Serverless
flat key-value pairs:
- env/dev.yml
- env/test.yml
- env/prod.yml
- env/local.yml
accessible via:
process.env.VAR_NAME
Heroku
app config variables
.env - local development
accessible via: process.env.VAR_NAME
Serverless
flat key-value pairs:
- env/dev.yml
- env/test.yml
- env/prod.yml
- env/local.yml
accessible via:
process.env.VAR_NAME
CDK
structured (possibly different for each lambda):
- env/dev.yml
- env/test.yml
- env/prod.yml
flat key-value pairs
(running locally via serverless-offline):
- env/local.yml
sg2-reports-api prod.yml (in Git)
REGION: eu-west-1
DYNAMODB_URI: dynamodb.eu-west-1.amazonaws.com
DYNAMODB_TABLE: ${self:service}-prod-reportStatus
SQS_URL: https://sqs.eu-west-1.amazonaws.com/193743439270/${self:service}-prod-reportQueue
SQS_QUEUE: ${self:service}-prod-reportQueue
S3_BUCKET: ${self:service}-prod-report-storage
REPORT_CONFIG_PATH: config/config_paths_sg2_heroku_prod.json
AUTH_URL: http://apps.solargis.com/api/auth/login
SG2_API_URL: http://apps.solargis.com/api/
CORS: '*'
MONGODB_URI: mongodb+srv://sg2-client:eL6chahg7rohlae3@prod-mq4cm.mongodb.net/test?retryWrites=true
MONGODB_DATABASE: sg2
COMPANY_JWT_SECRET: EheiLo3OhPah0phooG4eich0iey7uuquoo0ooli4Oongo9iew9EvuotahPoh3aiw0fa6ba8eeDiebaexaecai0weekoh1chu2gaid3othaivusooB2oph0wu
METADATA_YEAR_TO: 2018
METADATA_VERSION: 2.5.0
Secrets in AWS
System Manager - Parameter Store (SSM)
Text
Secrets in AWS
System Manager - Parameter Store (SSM)
Supported values:
- String
- ListString
- SecureString
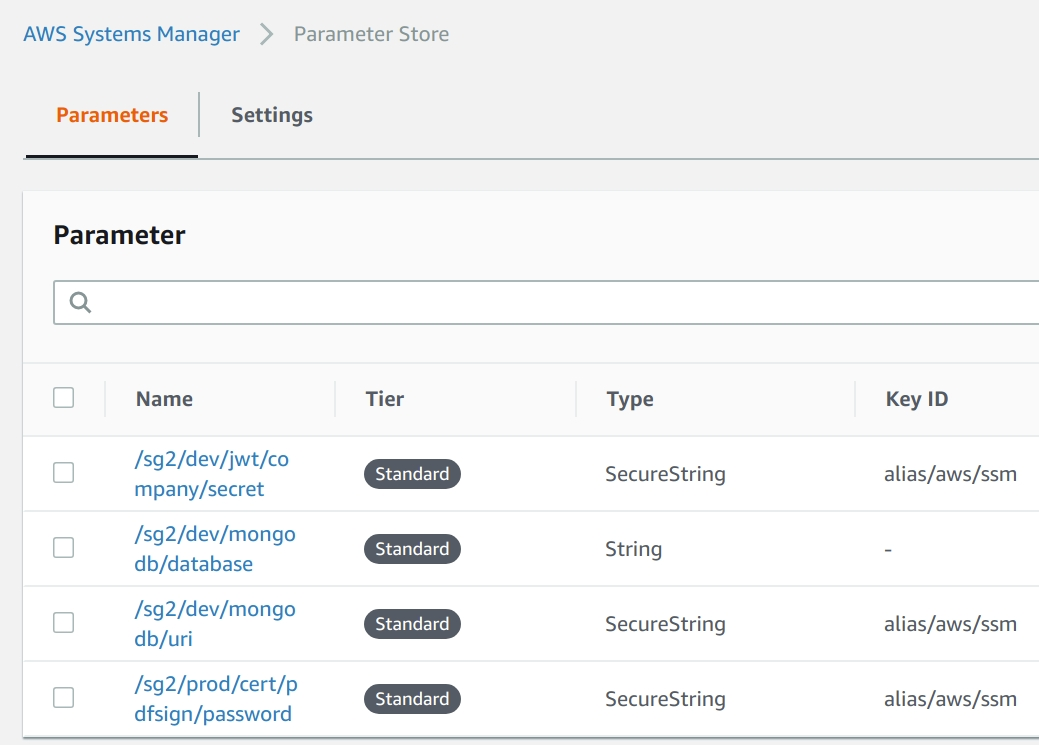
Name pattern:
/{namespace}/{environment}/{component}/{variable}
e.g: /sg2/dev/mongodb/uri
Secrets in AWS
System Manager - Parameter Store (SSM)
Supported in:
- Serverless:
- ${ssm:PARAM_NAME~true}
-
${ssm:/sg2/dev/mongodb/uri~true} -
${ssm:/sg2/dev/mongodb/database}
- CDK env file (no SecretString - CF limitation):
{{resolve:ssm:/sg2/dev/mongodb/database:1}} - CDK constructs
- AWS-SDK - at runtime or in scripts
Secrets in AWS
Secrets Manager
Text
Secrets in AWS
Secrets Manager
Text
Secrets in AWS
Secrets Manager
Supported values:
- JSON key-value pairs
- String
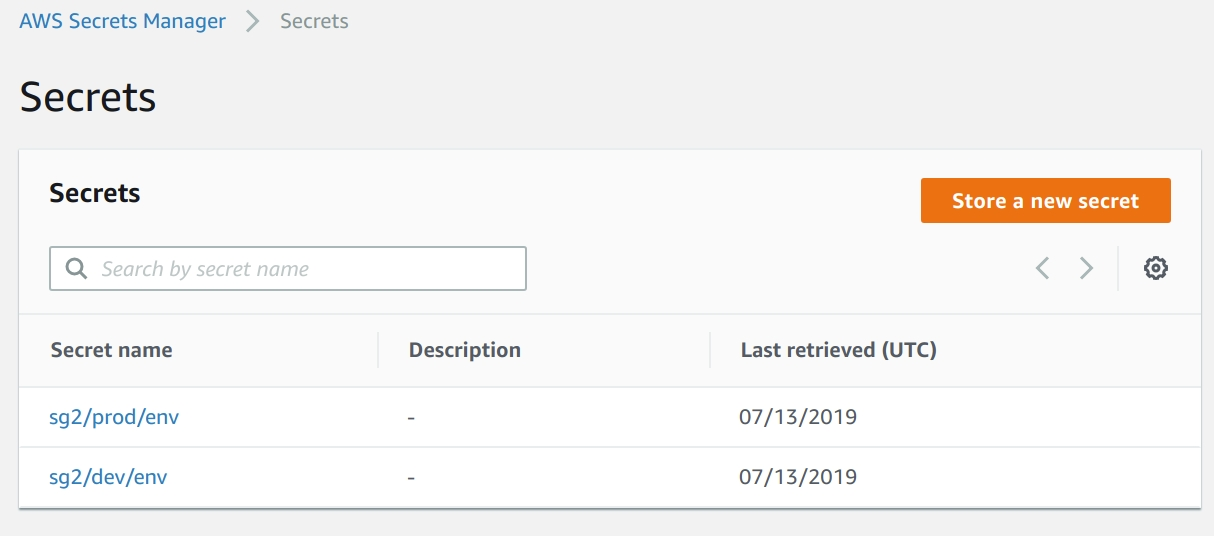
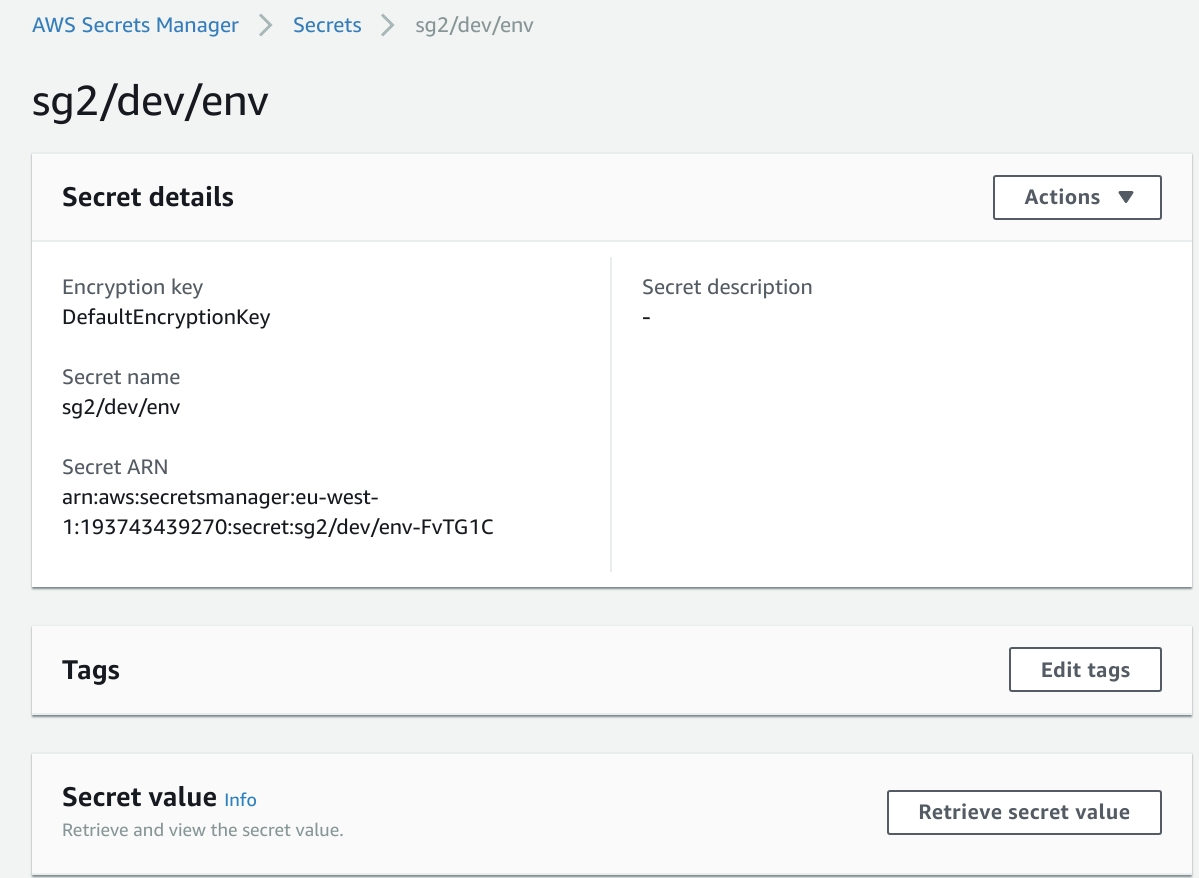
Secret name pattern:
{namespace}/{environment}/{secretName}
e.g.: sg2/dev/env
Secrets in AWS
Secrets Manager
Supported is:
- Serverless
- String secrets:
${ssm:/aws/reference/secretsmanager/secret_ID_in_Secrets_Manager~true} - JSON secrets: set to self.custom.secrets, then use key from self.custom.secrets
- String secrets:
- CDK env file:
-
{{resolve:secretsmanager:sg2/dev/env:SecretString:MONGODB_URI}}
-
- AWS-SDK - at runtime or in scripts
REGION: eu-west-1
DYNAMODB_URI: dynamodb.eu-west-1.amazonaws.com
DYNAMODB_TABLE: ${self:service}-prod-reportStatus
SQS_URL: https://sqs.eu-west-1.amazonaws.com/193743439270/${self:service}-prod-reportQueue
SQS_QUEUE: ${self:service}-prod-reportQueue
S3_BUCKET: ${self:service}-prod-report-storage
REPORT_CONFIG_PATH: config/config_paths_sg2_heroku_prod.json
AUTH_URL: http://apps.solargis.com/api/auth/login
SG2_API_URL: http://apps.solargis.com/api/
CORS: '*'
MONGODB_URI: ${ssm:/sg2/dev/mongodb/uri~true}
MONGODB_DATABASE: ${ssm:/sg2/dev/mongodb/database}
COMPANY_JWT_SECRET: ${ssm:/sg2/dev/jwt/company/secret~true}
METADATA_YEAR_TO: 2018
METADATA_VERSION: 2.5.0
SOLUTION for sg2-reports-api prod.yml
api:
project:
domain:
name: api-dev.solargis.com
mapping: /project
layers:
jwt: 'arn:aws:lambda:eu-west-1:193743439270:layer:jwt_layer:1'
environment:
COMPANY_JWT_SECRET: '{{resolve:secretsmanager:sg2/dev/env:SecretString:COMPANY_JWT_SECRET}}'
MONGODB_URI: '{{resolve:secretsmanager:sg2/dev/env:SecretString:MONGODB_URI}}'
MONGODB_DATABASE: '{{resolve:secretsmanager:sg2/dev/env:SecretString:MONGODB_DATABASE}}'
# MONGODB_DATABASE: '{{resolve:ssm:/sg2/dev/mongodb/database:1}}'
REPORT_CONFIG_PATH: 'config/config_paths_sg2_heroku.json'
SOLUTION for CDK env file
TODO
- resolve patterns with AWS-SDK to use env files in local scripts
- use it ;)
Secrets in AWS
By Michal Moravcik
Secrets in AWS
- 53



