Public Key Cryptography

© 2018 Morgan C. Benton code4your.life
ShHHHHhh!
It's a secret!
Humans invented ways to send secret messages to one another over 4000 years ago (ca 1900BCE). Since then, we have not stopped trying to come up with better and better ways to keep our communications private and/or ways to ensure that things, once written down, can't be altered by anyone.
Why do you think that is?

© 2018 Morgan C. Benton code4your.life


"Slave power crushes freedom of speech and of opinion. Slave power degrades labor. Slave power is arrogant, is jealous and intrusive, is cruel, is despotic, not only over the slave but over the community, the state."
Elizabeth Van Lew
Spy and Anti-Slavery Activist
Code has been around... even before computers...
© 2018 Morgan C. Benton code4your.life

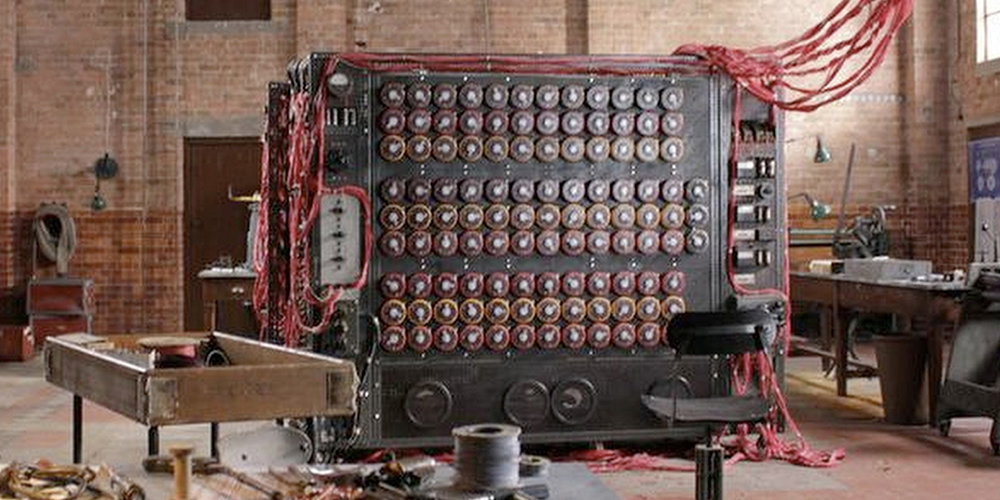

Code-breaking was even the inspiration and motivation behind the creation of one of the very first working computers...
© 2018 Morgan C. Benton code4your.life
TRUST
Why is it necessary?

© 2018 Morgan C. Benton code4your.life




CRYPTOGRAPHY
Temple of Blockchain
DANGER!!!
A flawed implementation of an Android random number generator allowed hackers access to several bitcoin wallets in early 2013!
In 2010, a group of hackers calling themselves failOverflow figured out how to get the PlayStation 3 private key based on a similar security flaw.
It's important to understand this stuff if you are implementing the tech!!!
BRIEF HIstory of Cryptography
- Writing
(Mesopotamia, circa 3500 BCE) - Ciphertext
(Egypt, circa 1900 BCE) - Cryptanalysis
(Muslims, circa 800 CE) - Electromechanical ciphers
(circa 1917) - Mathematical cryptography (Shannon, 1949~)

© 2018 Morgan C. Benton code4your.life
Early
- DES (1974)
- Diffie-Hellman key exchange
(1977) - RSA Algorithm
(1977) - Elliptic Curve Algorithms
(1985) - MD5 (1992), SHA-0 (1993)
- SHA-1 (1995)
- AES replaces DES (2001)
- SHA-2 (2004)
MOdern
Ciphertext
- The most ancient method of encrypting a message
- ALL cryptography up until the early 20th century was more or less some form of ciphertext
- Essentially involves some scheme where every letter of a message is replaced with some other letter or symbol; Recipient must have a "key" to decipher it

© 2018 Morgan C. Benton code4your.life
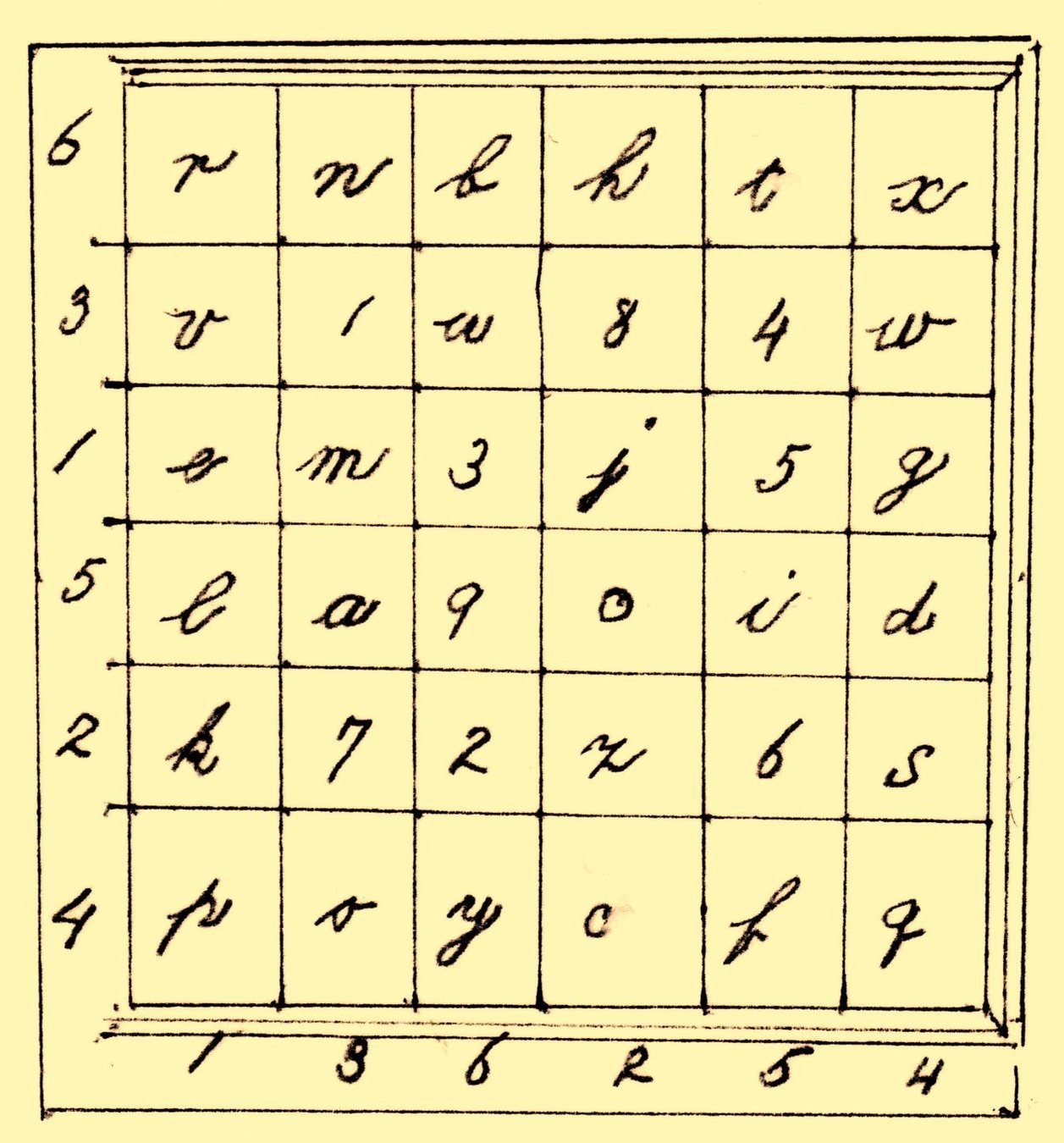
PROblem
- For ciphertext to work, both sender and recipient must have the key
- Sending the key across a public network (i.e. the internet) defeats the purpose since it could be intercepted at any point along the way
- Secure communication via the web required a new solution → asymmetric cryptography, aka public key cryptography

© 2018 Morgan C. Benton code4your.life
Trapdoor Algorithms

An IMportant Step Forward:
Trapdoor Algorithms
are like...




INteger Factorization
It turns out that while it's very easy to multiply two numbers together, it's VERY HARD to discover their prime factors.
The RSA algorithm is widely used, but some fear it might be vulnerable to quantum computing.
RSA-1024 is a 309-digit number that is the sum of two large prime numbers. Even using ALL of the computing power on earth, it could take over 1000 years to discover these factors.
/cdn.vox-cdn.com/uploads/chorus_image/image/55358555/693472226.0.jpg)

Elliptic
Curve
Cryptography
Currently, one of the more popular families of trapdoor function being used in public key encryption.
Allows smaller (faster) keys to be used for the same level of security as RSA.
How RSA Works:
To generate keys:
- Pick 2 large prime numbers p and q that differ in length by a few digits
- Compute n = pq
- Calculate the totient
φ(n) = (p -1)(q - 1) - Pick a number
e such that
1 < e < φ(n) and e and φ(n) are coprime - Use the extended Euclidean algorithm to calculate
d, the modular multiplicative inverse,
d = e-1 mod φ(n) -
e is the public key
d is the private key
To encrypt a value:
- The encrypted value c of message m is: c = me mod n
To decrypt a value:
- The decrypted message m given c is:
m = cd mod n
Public Key Encryption

© 2018 Morgan C. Benton code4your.life

photo credit: US Naval Academy https://www.usna.edu/CyberDept/sy110/lec/cryptDig/img/bobaliceAsymmetric.png
How does Public Key Encryption work?

© 2018 Morgan C. Benton code4your.life
STep 1: Generate a Private Key

© 2018 Morgan C. Benton code4your.life
A private key is just a random number, but it is generated from a HUGE, COLOSSAL, GI-NORMOUS number of possibilities, so the chances two people will have the same key, or that someone might guess your key are infinitesimally small
Example
bitcoin private key space = 2 256 ≈ 1077
number of atoms in visible universe ≈ 1080
STep 2: Generate a
PUBLIC Key

© 2018 Morgan C. Benton code4your.life
A public key is calculated from your private key using a one-way hashing function
knot metaphor
dictionary metaphor
Public Key Cryptography
By Morgan Benton
Public Key Cryptography
Introduction to the basic concepts associated with public key cryptography. This presentation is targeted at people who may have no background in math or computing, but are able to follow a mathematical argument.
- 1,439



