Digital Security
3 main
motivators


Last year, >1 ETH
stolen from me/Subvisual

Questions to ask yourself
If I lose my phone right now, how fucked am I?
What about my laptop?
Is my company fucked, or "just" me?
Which services am I trusting with my secrets?
Types of attacks
- Malware / Ransomware / etc
- Phishing
- Evil maid
- Brute-force
- Man-in-the-middle
- Denial of Service
- Social Engineering
- Zero-day
- ...
My previous
(lack of) best practices
Too many things in LastPass
- some mnemonics
- 2fa recovery codes
Too much Metamask
Too little Ledger
Phone was a big
single-point-of-failure
Both for potential attacks,
or just the hassle of losing/breaking it
Laptop was encrypted though
thankfully
The new
shiny stuff

it's not about
can they leak my passwords?
but rather
is the browser extension well maintained?
will they still be online next week?

❯ gpg --list-keys
/home/naps62/.gnupg/pubring.kbx
-------------------------------
Miguel Palhas (arrakis) <mpalhas@gmail.com>
Miguel Palhas (solaria) <mpalhas@gmail.com>
Miguel Palhas (Pixel) <mpalhas@gmail.com>
Miguel Palhas (giskard) <mpalhas@gmail.com>
❯ pass
Password Store
├── 2fa
│ ├── binance
│ ├── github
│ └── google
│ ├── miguel.palhas@lightshift.capital
│ ├── miguel@subvisual.co
│ └── mpalhas@gmail.com
├── crypto
│ ├── argent-x.json
│ ├── elrond
│ ├── forta
│ │ ├── password
│ │ └── wallet
│ ├── metamask
...Go ahead and hack me
Syncthing
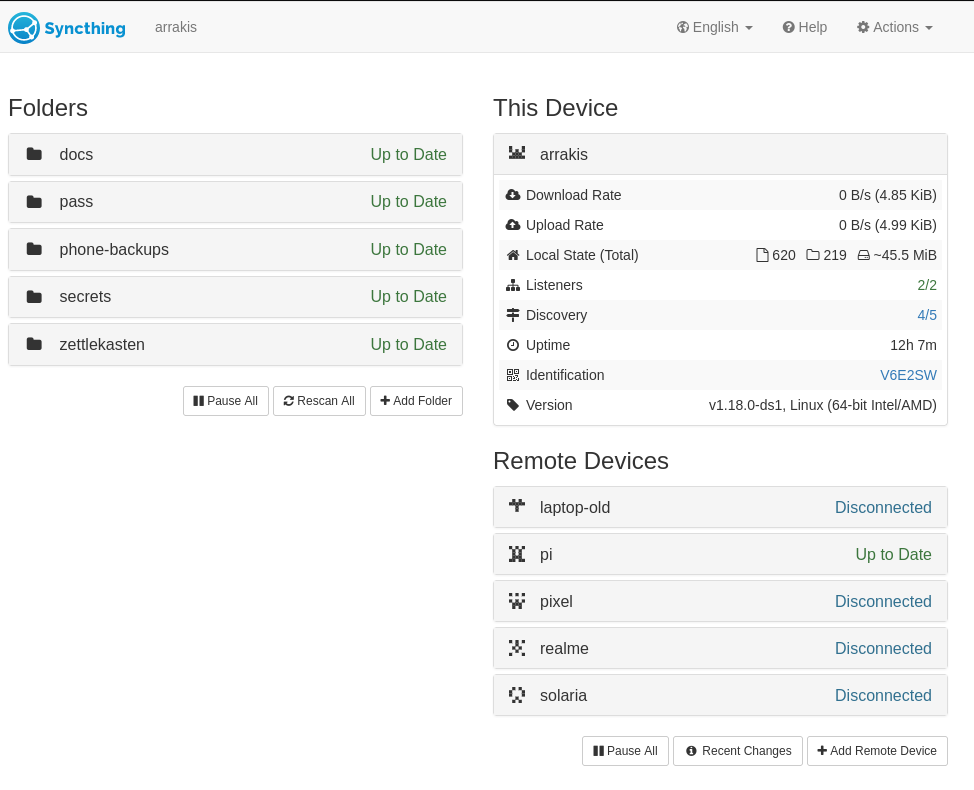
Redundancy
Redundancy
Redundancy
2nd phone
More Specifically, a Google Pixel 5
because GrapheneOS
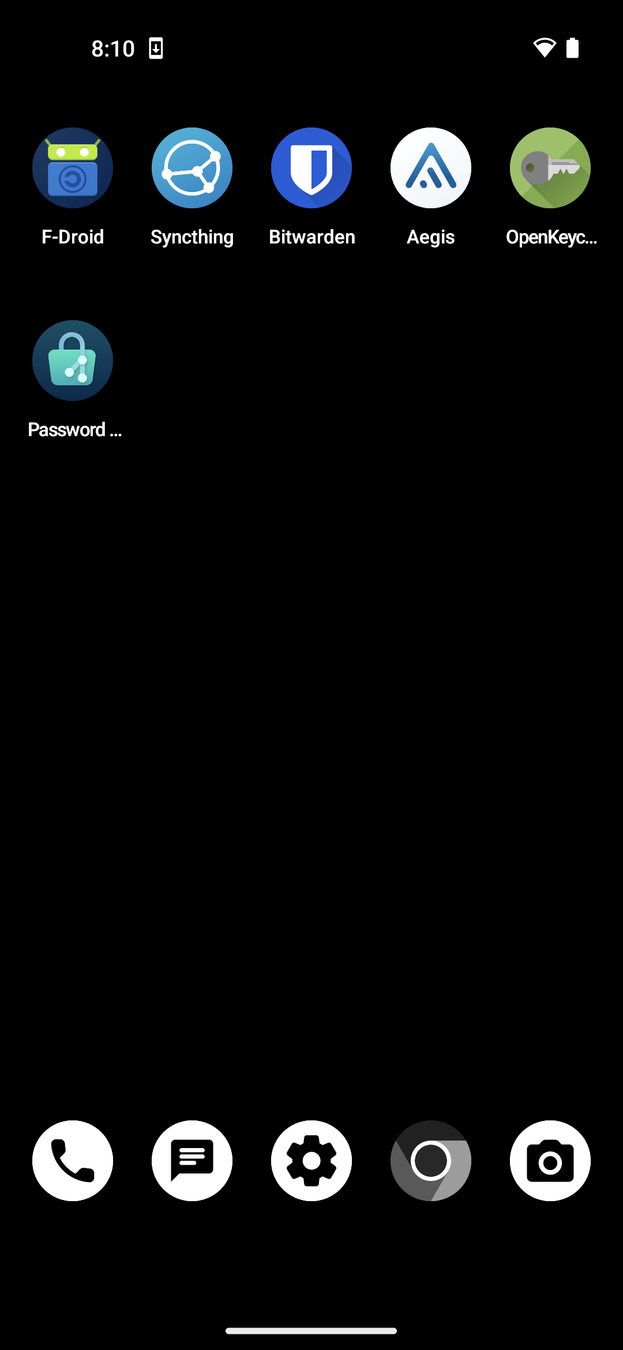
What it has:
- F-Droid
- Syncthing
- Bitwarden
- 2FA app
- GPG
- Pass
- All GrapheneOS's security goodness
What it doesn't have:
- Google services
- Biometrics
- Untrusted Wifi networks
- Vacations
Yubikey*
Because redundancy and convenience
*not set up yet. Amazon messed up, only arrived yesterday. Don't hack me yet pls

Future work
How to create a dead-man-switch?
(seriously, ideas welcome)
Digital Security
By Miguel Palhas
Digital Security
- 316



