Image Fingerprinting System Using Perceptual Hash
Overview
Digital fingerprints are perceptual features of a multimedia object encoded in fixed size bits.
Perceptual Hash vs Cryptographic Hash
The system map an arbitrary length of information into a small and fixed size of bits. The resulting fingerprint then can be compared of similarity.
Procedures of the system
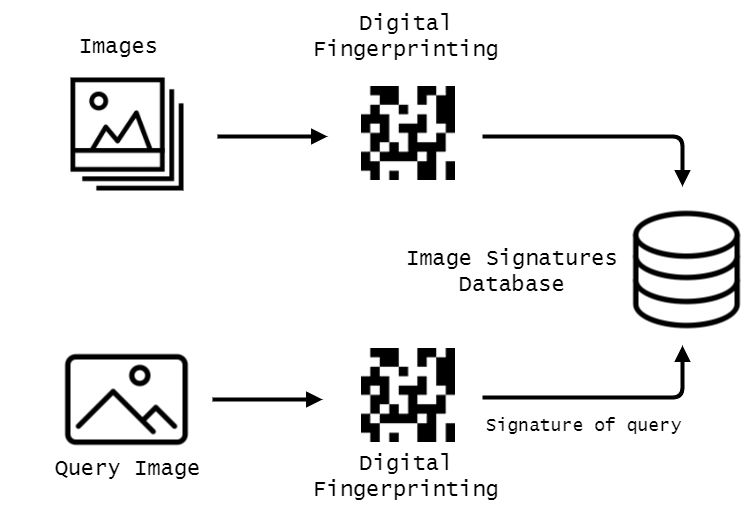
Existing images are indexed into signature hash and store as a key in database. Query image hash can be retrieved using hamming distance search with multi-index hashing.
Fingerprinting Process
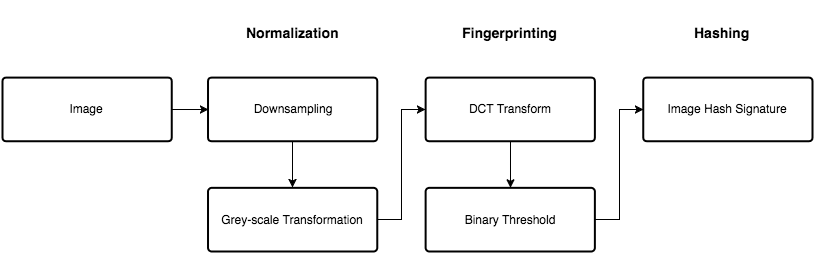
Process of fingerprint construction consists of the following stages:
An image is normalized by two step processes: downsampling and gray-scale transformation.
After the normalization, the DCT coefficient of the image is calculated to formulate a fingerprint block. The fingerprint block can be encoded into bits.
1.Downsampling
In order to reduce high frequency details of an image while preserving structural information of the image, the image is resize down to a 32 x 32 pixels lower resolution image


2.Greyscale transformation
To transform the color based on RGB color model to a greyscale representation, the luminance channel of an image is calculated, which is given by
3.Discrete Cosine Transform
The discrete cosine transform, abbreviated (DCT) represents an image as a sum of sinusoids of varying frequency and magnitudes.
3.Discrete Cosine Transform

DCT Energy Compaction Property
Most of the visually significant information is concentrated in just a few lower coefficients of the DCT. For this reason, DCT is ideal to construct the digital fingerprint.
The property is also useful for image and audio lossy compression.
3.Discrete Cosine Transform
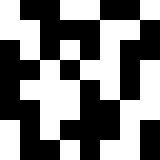

4.Fingerprint Block Construction
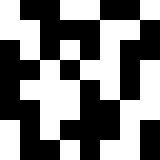
Truncate the DCT coefficient to 8 x 8
Compute average of Alternate Coefficient
Apply Binary threshold using the average value
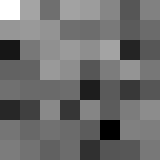
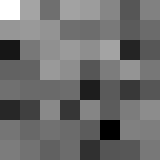
4.Fingerprint Block Construction
5.Fingerprint Matching
Images are considered as matched if the Hamming distance (Bit Errors) between the fingerprints is below a certain input threshold.
Experimental Results


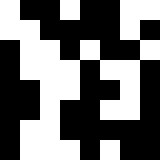

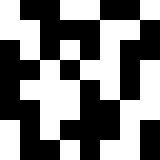
Experimental Results


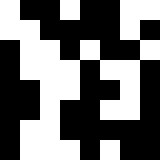
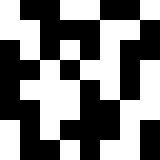
PHASH
By nxxcxx
PHASH
- 495



