(Practical) Android Malware Analysis
BSides London - 3rd June 2015
Paul AMAR / Etienne Stalmans
# who
Paul [at] SensePost [.dot.] com
@PaulWebSec / GitHub: PaulSec
Etienne [at] SensePost [.dot.] com
@kamp_staaldraad

why do we care?
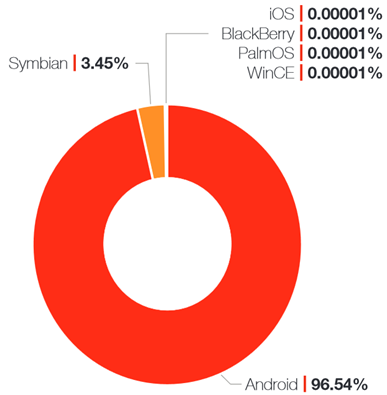
Android Growth - Fortinet results (2014 report)
What?
Static Analysis (Androguard, Dex2Jar, apktool, ...)
Dynamic Analysis (DroidBox using the emulator)
how?
Need Vmware Player:
> Create a new Machine
> Linux, Ubuntu
> Import the Hard-drive with the .vmdk
Launch it, creds: student/mobile
Tools available at ~/Tools
Samples available at ~/Desktop/samples/
VMware perf

Enable Virtualization performance
Androguard
Disassembles/Decompiles Android apps
Different tools: androlyze, androdis, androauto, ...
Androguard 101
Let's analyze the APK!
Get in the folder:
$ cd ~/Tools/androguard
Run Androlyze using shell mode:
$ python ./androlyze.py -s
Androguard 102
In the shell, load the APK:
sample = APK('/path/to/file.apk')
And start investigating:
sample.get_permissions()
sample.get_activities()
sample.show()
....
Androguard 103
Retrieves classes/methods from the loaded APKd = dvm.DalvikVMFormat(a.get_dex())
for _class in d.get_classes():
print _class.get_name()for method in _class.get_methods():
print method.get_name()
but.. apk, apk..
Has been signed, and compiled
Unzip it using:
$ unzip /path/to/file.apk
what's in there?
META-INF: meta info directory
lib: directory containing compiled code
res: resources directory
assets: application assets directory
AndroidManifest.xml: additional manifest file describing name, version, access rights and referenced library files for the app
classes.dex: the main Dalvik Executable file
resources.arsc: precompiled resources e.g. binary XML
APKtool
Disassembles/rebuilds resources to JAR/APK
Disassembles the APK$ apktool d /path/to/file.apk -o out/
$ apktool b foo/Builds foo folder into foo/dist/foo.apk file
https://ibotpeaches.github.io/Apktool/
usually, *phun* is in
*.dex files.
DEX = Dalvik EXecutable file
code that runs in the Dalvik VM
We need to convert it to a JAR archive
dex2jar
A set of tool to work with Android .dex and java .class files
Read/write the Dalvik Executable (.dex) file, Disassemble .dex to smali files, Convert .dex file to .class files (zipped as jar)
dex2jar 101
Convert .dex to a .jar
$ /path/to/d2j-dex2jar.sh /path/to/file.dex
JAR archive will be in d2j's folder.
JD-GUI
At that point, you can use any Java decompiler.
java -jar jd-gui-1.1.0.jar
TADAM!
feeling a bit lazy?

but wait, there's more..
jadx - tools to produce Java source code from Android Dex and Apk files
https://github.com/skylot/jadx
jadx 101 (RLY?)
$ jadx /path/to/file.apk
$jadx-gui /path/to/file.apk
Done.
So, now...
Got the source code, might contain hundred of classes.
Thousand lines of code.
Where/What to look for?

observations
Often..
- Using HTTP to communicate (and/or SMS)
- no SSL certificate for the panels
- IMEI used as the victim's identifier
- Encrypting using AES
- Encoding data in Base64 (still..)
Low hanging fruit
Save the source files (*.java) in:
eg. /tmp/sample_test
And search for specific terms:
$ cd /tmp/sample_test
$ grep -r -i 'cipher' .
$ grep -r -i 'http://' .
$ grep -r -i 'base64' .
....
then,
Analyze how the communication works
Retrieve encryption keys
See how the app interacts on the filesystem
Dynamic analysis
In this workshop, two ways:
- Directly from the emulator
- Using DroidBox
adb
Stands for: Android Debug Bridge
Command line tool to communicate with
emulator or connected devices
adb 101
List the devices already connected
$ adb devices
Install .APK
$ adb install /path/to/file.apk
Push/Pull file from device
$ adb push/pull <local> <remote>
Droidbox
Logs everything that happens..
.. and retrieves bunch of information:
- Incoming/outgoing network data
- File read and write operations
- Sent SMS and phone calls, ...
Droidbox
Create a new AVD (Android Virtual Device),
Nexus 4, Android version 4.2.1
$ android
Start the emulator
And install/launch the app$ ./startemu.sh <AVD name>
$ ./droidbox.sh /path/to/file.apk
burp suite setup
In order to monitor the HTTP(s) traffic
Configure a proxy on your phone:
- Wifi, Press <Network Name>
- Modify network
- Show advanced options
- Insert the proxy details
And launch the app.
pracs
The VM comes up with 5 APKs.
Check the file samples.txt and start in this order
~/Desktop/samples/samples.txt
Each prac should take around 20/30 mins.
funny samples (1/4)

Ciphered strings using AES
sha256:c0cb135eef45bb8e411d47904ce638531d53473729c7752dc43c6d55d5ed86f8
FUNNY samples (2/4)

String obfuscation - XOR
sha256:99c4d780c0143af20191d6ffb0cc206605e397330ddd6a84185df1d112c1e963
Funny samples (3/4)

Interesting persistence technique
sha256:f75500da9728d95e33e40f9a1d8bf29959d5aa89827aeabfb3aaaa02a488dd39
FUNNY SAMPLES (4/4)

recent PornDroid sample (May 2015)
sha256:d5f29750a8cb158d9b89a1e02e8addc5e410d1ddc48e660589144ade47f794c5
Last sample?
bot.apk - iBanking sample
Specially crafted for BSides London
Retrieve phone numbers, C&C URL
wrap-up
This is just an introduction.
Lot of research regarding obfuscation:
Dex Education - Practicing Safe Dex | Black Hat 2012
DEF CON 22 - Tim Strazzere and Jon Sawyer - Android Hacker Protection Level 0
how to keep informed?
VirusTotal (#android #malware)
Contagio mini-dump (+ mailing)
amtrckr.info (Android Malware Tracker)
AndroMalShare (202.117.54.231:8080)
questions?
BSides 2015 - Android Malware Analysis
By paul38
BSides 2015 - Android Malware Analysis
BSides 2015 - Android Malware AnalysisDeck
- 3,754



