Networking
Layer 3 - Networking Layer
What is a "Packet"?
- A frame is a chunk of data at layer 2.
- A packet is a chunk of data at layer 3.
- Frames only care about point-to-point. Packets can move multiple hops to final destination.
Layer 3 Built From Layer 2

Packets vs. Frames

What is a "Packet"?
- A frame has a payload that contains data we want to move.
- Ethernet frame can have 1500 bytes of payload, 1522 bytes total.
- Packets can be bigger than one frame, being split between multiple frames.
ACK
- If packet arrives at destination OK, we send back an acknowledgement packet (ACK)
- If the packet gets corrupted or lost, we sent back a negative acknowledgement (NACK)
- A datagram doesn't require an ACK or NACK. Technically, this it isn't a packet, but often still called one anyway.
Layer 3 Standard / Protocol
- A LOT of protocols fought to be used for layer 3
- TCP/IP is by far, the most popular now. 3 parts:
- IP
- TCP (part of TCP/IP also covers much of layer 4)
- UDP
- How did TCP/IP become the networking standard everyone uses?
Request For Comments (RFC)
- Early in the life of the networking, Jon Postel managed a list of items called "Request For Comments".
- First RFC was in 1969.
- Now RFCs are management by the Internet Society (ISOC) and Internet Engineering Task Force (IETF)
- First RFC was in 1969.
- Open standards. Anyone can follow. Allowed computers to interconnect.


Request For Comments (RFC)
- You can see all RFCs at:
- https://tools.ietf.org/rfc/index
- TCP/IP for Layer 3 that we use is covered by:
- RFC 790, 791, 2460
- You can even do TCP/IP via carrier pigeon (RFC 1149)
- Willingness to make an open standard fostered a level playing field
RFC INDEX
---------
RFC1 Host Software. S. Crocker. April 1969. (Format: TXT, HTML) (Status:
UNKNOWN) (DOI: 10.17487/RFC0001)
RFC2 Host software. B. Duvall. April 1969. (Format: TXT, PDF, HTML)
(Status: UNKNOWN) (DOI: 10.17487/RFC0002)
RFC3 Documentation conventions. S.D. Crocker. April 1969. (Format: TXT,
HTML) (Obsoleted by RFC0010) (Status: UNKNOWN) (DOI:
10.17487/RFC0003)
RFC4 Network timetable. E.B. Shapiro. March 1969. (Format: TXT, HTML)
(Status: UNKNOWN) (DOI: 10.17487/RFC0004)
RFC5 Decode Encode Language (DEL). J. Rulifson. June 1969. (Format: TXT,
HTML) (Status: UNKNOWN) (DOI: 10.17487/RFC0005)
RFC6 Conversation with Bob Kahn. S.D. Crocker. April 1969. (Format: TXT,
HTML) (Status: UNKNOWN) (DOI: 10.17487/RFC0006)
RFC7 Host-IMP interface. G. Deloche. May 1969. (Format: TXT, HTML)
(Status: UNKNOWN) (DOI: 10.17487/RFC0007)
RFC8 ARPA Network Functional Specifications. G. Deloche. May 1969.
(Format: PDF, HTML) (Status: UNKNOWN) (DOI: 10.17487/RFC0008)
RFC9 Host Software. G. Deloche. May 1969. (Format: PDF, HTML) (Status:
UNKNOWN) (DOI: 10.17487/RFC0009)
RFC10 Documentation conventions. S.D. Crocker. July 1969. (Format: TXT,
HTML) (Obsoletes RFC0003) (Obsoleted by RFC0016) (Updated by
RFC0024, RFC0027, RFC0030) (Status: UNKNOWN) (DOI: 10.17487/RFC0010)
RFC11 Implementation of the Host - Host Software Procedures in GORDO. G.
Deloche. August 1969. (Format: TXT, PDF, HTML) (Obsoleted by
RFC0033) (Status: UNKNOWN) (DOI: 10.17487/RFC0011)
RFC12 IMP-Host interface flow diagrams. M. Wingfield. August 1969.
(Format: TXT, PS, PDF, HTML) (Status: UNKNOWN) (DOI:
10.17487/RFC0012)
RFC13 Zero Text Length EOF Message. V. Cerf. August 1969. (Format: TXT,
HTML) (Status: UNKNOWN) (DOI: 10.17487/RFC0013)
TCP/IP
- TCP/IP stands for Transmission Control Protocol / Internet Protocol
- There's also a User Datagram Protocol (UDP) that is made
TCP/IP Allowed Anyone to Network
- Developed by Vint Cerf and Bob Kahn in early 1970s
- Funded by Defense Advanced Research Projects Agency DARPA
- Created ARPANET - US funded military network
- Expanded to include academia and large companies like IBM, AT&T and DEC
- Operating systems like UNIX and OS/2 adopted it

TCP/IP Allowed Anyone to Network
- Commercial on-line dial-up services existed:
- CompuServe (Popular in 1980s)
- AOL (Popular in 1990s)
- Non-commercial services like Gopher, Newsgroups competed
- With the web, (1990) things really took off.
- Plus, TCP/IP technology was given away
Internet Protocol Addresses
- IP address is a totally different address than MAC address. Both are needed!
- IP version 4 (IPv4) address is four bytes, written with 4 numbers, 0-255, separated by periods
- For example: 192.168.1.100
- About 2^(4*8) = 4 billion addresses
- Your MAC address stays the same. Your IP address changes when you move and data must be routed differently
Internet Protocol
- Do not need to establish a connection
- No way to send data larger than 1 packet worth (about 64k)
- If data doesn't arrive, no way to request a resend, or even know there's an error
- No way to say what program on the computer should get the data (Skype? Zoom? Firefox? League of Legends?)
- Provides a building block for more complex protocols
Time To Live (TTL)
- Multi-hop packets can get caught in a loop
- That would congest the network and waste resources
- A Time To Live (TTL ) field for each packet prevents this
- Each router reduced TTL by one.
- If it hits zero, it is discarded.

IP Fields
-
IP Version: First four bits.
- The number 4 (in binary 0100) is IPv4.
- The number 6 (in binary 0110) is used for IPv6.
-
Header Length: Length of the header - not the data
- Measured in 32 bit chunks.
- The minimum is 5, which is 5 x 32 = 160 bits / 20 bytes.
- If there are options added, this might be longer.
- Differentiated Services: Sometimes used for streaming or voice over IP. Often just filled with zeros.
- Explicit Traffic Congestion Notification: If all the intervening nodes support this, it is a flag that can prevent dropping of specific packets on congested networks. Normally just filled with zeros.
IP Fields
-
Total length of the packet including data:
- Minimum is 20 bytes (the header), max is 64k.
- Ethernet limits the data payload of a Layer 2 frame to 1500 bytes, so packets greater than this will have to be fragmented.
-
Identification: Packet to big? Have to split it up?
- A large Layer 3 packet going into a Layer 2 protocol that can’t support packets that size, the packet must be fragmented into smaller parts.
- This field helps identify which part that is.
- If the packet isn’t fragmented, the field is filled with zeros.
IP Fields
-
Flags: This three bit field states has:
- One bit dedicated whether the layer three packet can be fragmented into multiple parts by layer two. If it can’t be fragmented, and layer two doesn’t hold enough data for the packet, the packet will be dropped.
- Another bit is set if the packet is fragmented, and there are more parts coming.
- If the packet is fragmented, the next field is the fragment offset field that is used to help reassemble the packet.
IP Fields
- Time To Live (TTL): 8 bits for a maximum hop count of 256.Protocol: 8 bits for which IP protocol is being used. Common examples, 0x06 is TCP, 0x11 isUDP.
- Header Checksum: 16 bits used to see if the header is valid. Optional, can be set to zeros if not used.
- Source: IP address of the packet’s original source.
- Destination: IP address of the packet’s final destination.
- Options: Depending on the protocol used and the header length set, there may be optional information next.
Gateway / Router
- Packet isn't for a node on the local area network (LAN)?
- Gateway / Router (same thing) picks it up and forwards it to the Wide Area Network (WAN)
TCP / UDP Ports
- Multiple programs need to network
- How do we pass the right data to the right program?
- Use "ports" - A two-byte number 0 - 65,535
- Standardize incoming port numbers for certain services
Common Destination Ports
- 25 - SMTP (mail)
- 53 –Domain Name System
- 80 –Unencrypted web (http)
- 443 –Encrypted web (https)
- 636 –Encrypted LDAP
Ephemeral Ports
- The client initiates from a random port
- Random unoccupied port 49152-65535
- Web Examples:
Server 216.58.192.206:443
Client 192.168.1.101:51010
User Datagram Protocol (UDP)
- Do not need to establish a connection
- No way to send data larger than 1 packet worth (about 64k)
- If data doesn't arrive, no way to request a resend, or even know there's an error
- Uses ports to decide what program on the computer should get the data (Skype? Zoom? Firefox? League of Legends?)
- Adds 8 bytes to the 20 bytes IP header
Transmission Control Protocol (TCP)
- Do need to establish a connection
- Can break large data into smaller parts
- If data doesn't arrive, can request a resend
- Uses ports to decide what program on the computer should get the data
- A lot of these features are Layer 4
- Will table TCP discussion for Layer 4
TCP/IP
- IP - Basic routing of packets - Layer 3
- UDP - Adds ports - Layer 3
- TCP - Adds connections, longer data, retrying failed packets, other layer 4 stuff
Special IP Address
- 127.0.0.1 always points to your own computer
- Also called 'localhost'
- Called a local loop-back link

Special IP Addresses
- Reserved Local Addresses
- 10.0.0.0 - 10.255.255.255
- 172.16.0.0 - 172.31.255.255
- 192.168.0.0 - 192.168.255.255
- No network at all?
- 160.254.0.0 - 169.254.255.255
- Multi-cast Address
- 224.0.0.0 - 239.255.255.255
- Broadcast Address
- Any address ending in 255
IPv4 vs. IPv6
- IPv4 uses 4 byte addresses:
- 192.168.1.1
- IPv6 uses 16 byte addresses:
-
2a04:4e42:0400:0000:0000:0000:0000:0323
-
You can drop leading zeros, and numbers with all four digits as zero
-
2a04:4e42:400::323
-
Enough addresses each atom on Earth can have its own
-
IPv6 Adoption
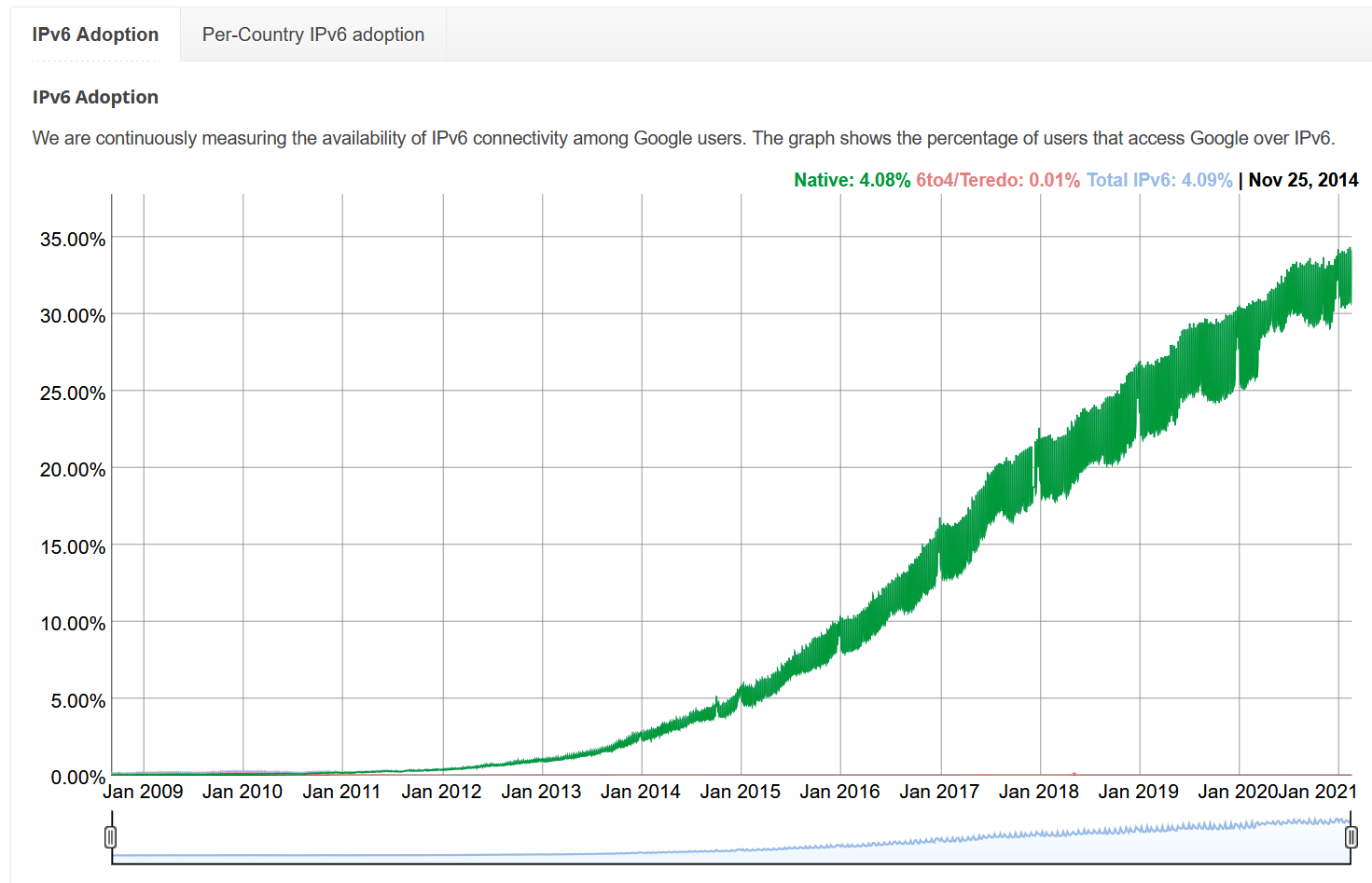
Network Address Translation

NAT
- Allowed 4 byte addresses to last longer
- Simpson can be run behind 1 or 2 IP addresses (check)
- Requires ranges of IP addresses that DON'T exist on the Internet, and that we can assume are local.
NAT
- Try it, type "what is my ip" into Google search
- Compare it with your neighbors, or phone
The center of the "star" topology
- A hub (layer 1) repeats any incoming traffic to everyone else.
- A switch (layer 2) knows what node(s) are connected to what port. It relays traffic to the nodes it was intended for.
- A router (layer 3) can figure out how to route a packet across multiple hops, in any topology.

Subnets
- Quick way to group IP addresses together
- Example
- 192.168.1.1 to 192.168.1.254 are in one subnet
- 192.168.1.54 is in
- 192.168.2.10 is out
- 192.168.1.0 is the network address
- 192.168.1.255 is the broadcast address
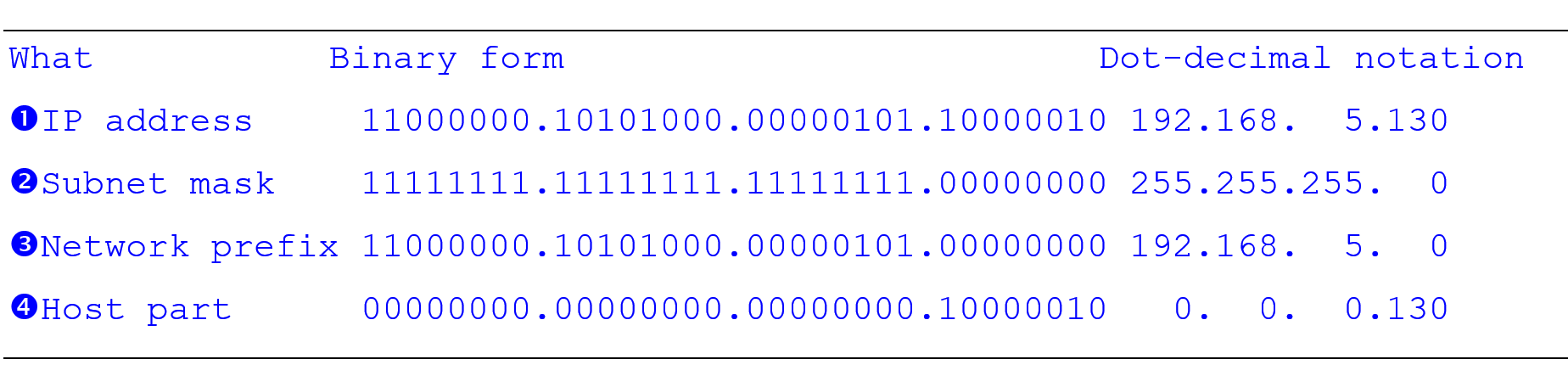
Netmask
- Quick way to figure if an address is in the local subnet
- Just takes one CPU cycle
- Uses bitwise 'and'
Netmask
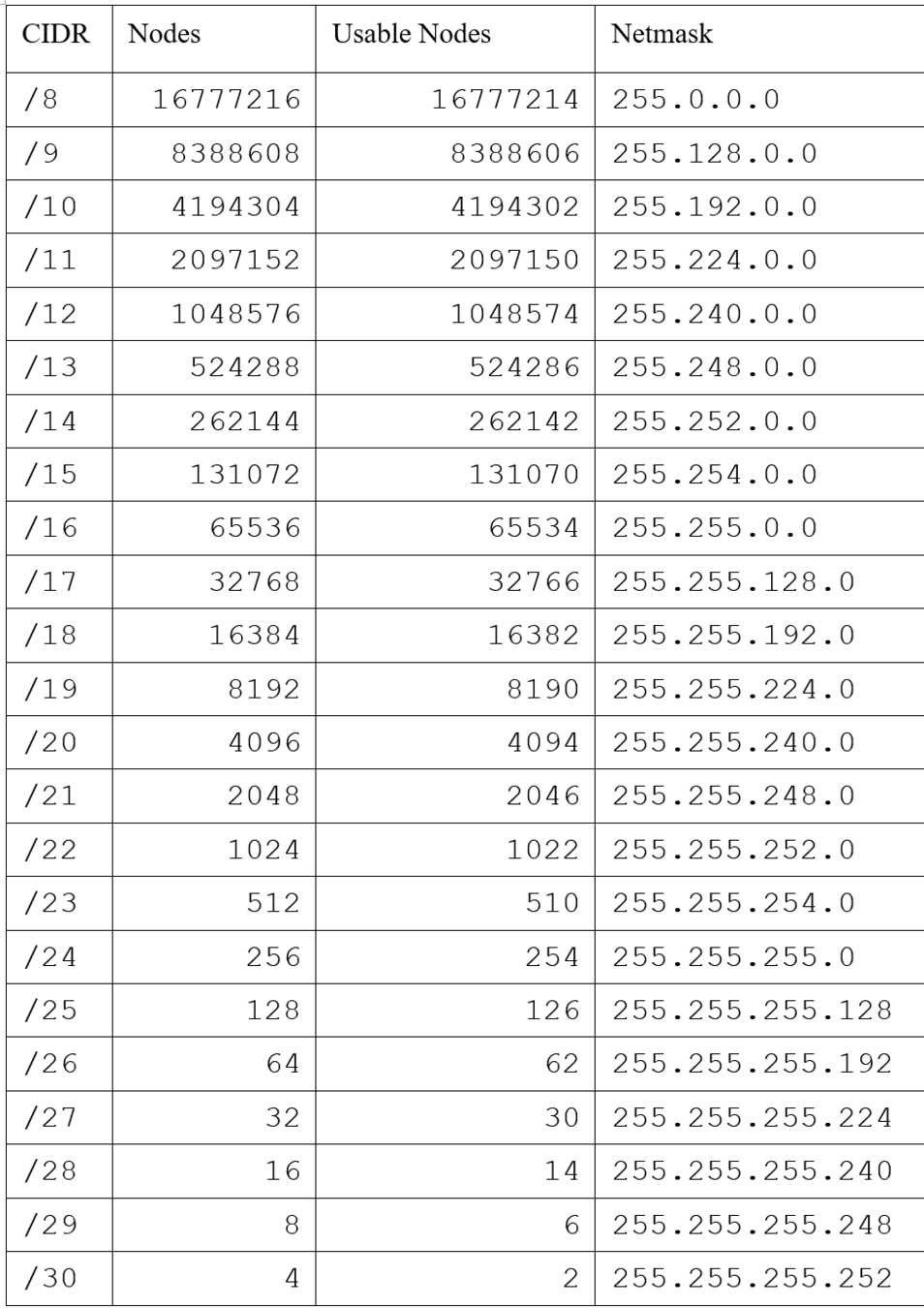
CIDR
- Classless Inter-Domain Routing
- Example
- 192.168.5.0/24
- Means 24 ones for the mask
- Followed by 32 - 24 = 8 zeros
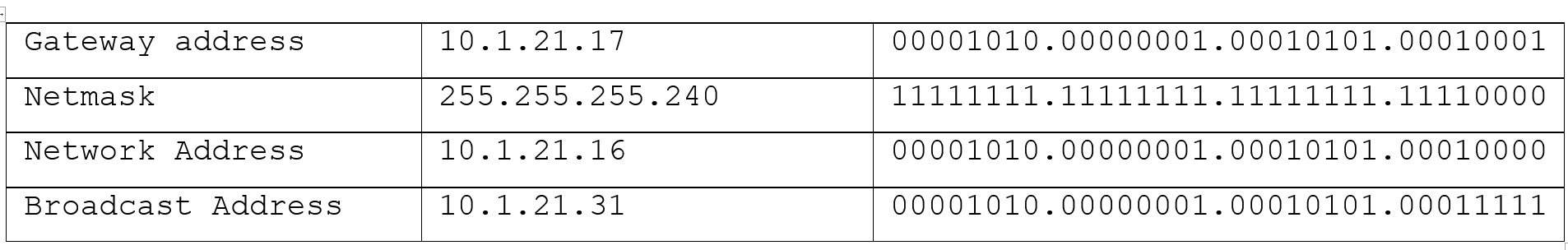
What IP address can I set my computer?
- Must be in your subnet
Broadcast Address
- Sent to everyone
- Useful, like if you add a printer to your network and the printer wants to announce itself
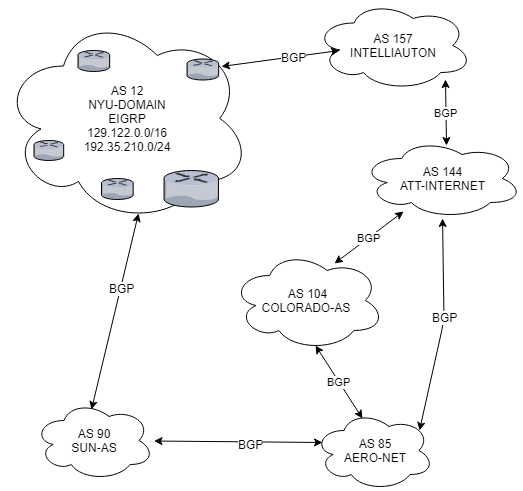
How does routing work?
- Internet is divided into multiple Autonomous Systems (AS)
- An AS is a collection of routers controlled by an administrative entity (ASN)
- You can download a big text file with all of them:
ftp://ftp.arin.net/info/asn.txt -
Each ASN controls a 'block' of IP addresses
-
Look up who owns a block:
https://mxtoolbox.com/arin.aspx
How does routing work?
- The Exterior Gateway Protocol is the type of protocol that routes packets between ASs.
- The name of the current EGP is Border Gateway Protocol (BGP) v4
- Inside an AS, packets are routed with an Interior Gateway Protocol.
- IS-IS (most popular)
- EIGRP
- OSPF
- RIP
Routing Protocol Categories
- Distance-vector routing protocol
- Periodically sends info about known routes to neighbors
- Slow to react to changes, but robust
- Link-state routing protocol
- Sends info about state of links to every other router
- Fast, but assumes everyone is well-behaved
- IS-IS
- Path-vector routing protocol
- Like distance-vector, but for exterior routing.
- BGP
Internet Provider Tiers
- Tier 1 - Top level. AT&T. Century Link. Verizon. They have so much routing capacity and cable they don't pay other companies to move data, others pay them.
- Tier 2 - Have their own cable and routing systems. Like Mahaska Communications Group. They pay Tier 1s to route data outside their network.
- Tier 3 - These own no cable or routers. They rent it, and just provide customer service.
Popular Layer 3 Protocols
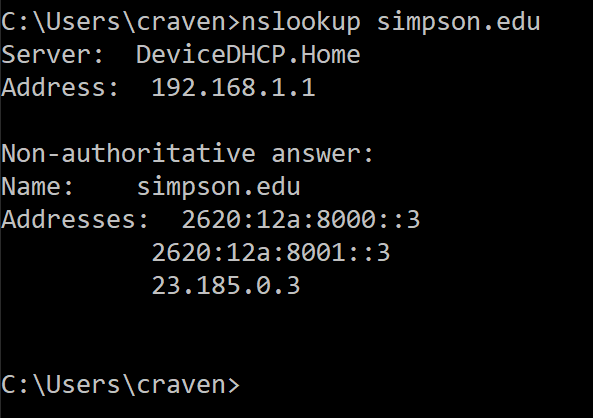
- Domain Name System
- Change simpson.edu to IP address
- ICMP
- Response if packet can't get to destination
- ARP
- Match MAC address to an IP address
- DHCP
- Auto-set IP address, netmask, and DNS servers
- Firewalls
Want More
Internet History?
- Look at start of
https://www.vox.com/a/internet-maps - Watch Nerds 2.0.1: A Brief History of the Internet
https://www.youtube.com/watch?v=a4OWIA1Eh1w
Domain Name System
- mail.my-domain.example => 192.168.1.100
www.my-domain.example => 192.168.1.101
sam.my-domain.example => 192.168.1.102
Domain Name System
- Top Level Domain
- my-domain.example
- Root Servers
-
https://www.iana.org/domains/root/servers
-
IP Addresses for domain servers
-
DNS Lookup
- The local computer requests the IP address for the computer from the router.
- The router asks for the IP address from the ISP.
- The ISP asks the root server for TLD name servers. (Who owns .example?)
- The ISP asks the TLD servers who owns the domain. (Who owns my-domain.example?)
- The ISP asks the domain name server for the IP of the computer in the domain. (What IP is www.my-domain.example?)
- The ISP passes the address back to the router.
- The router passes the address back to the local computer.
- Now the local computer has the IP address.
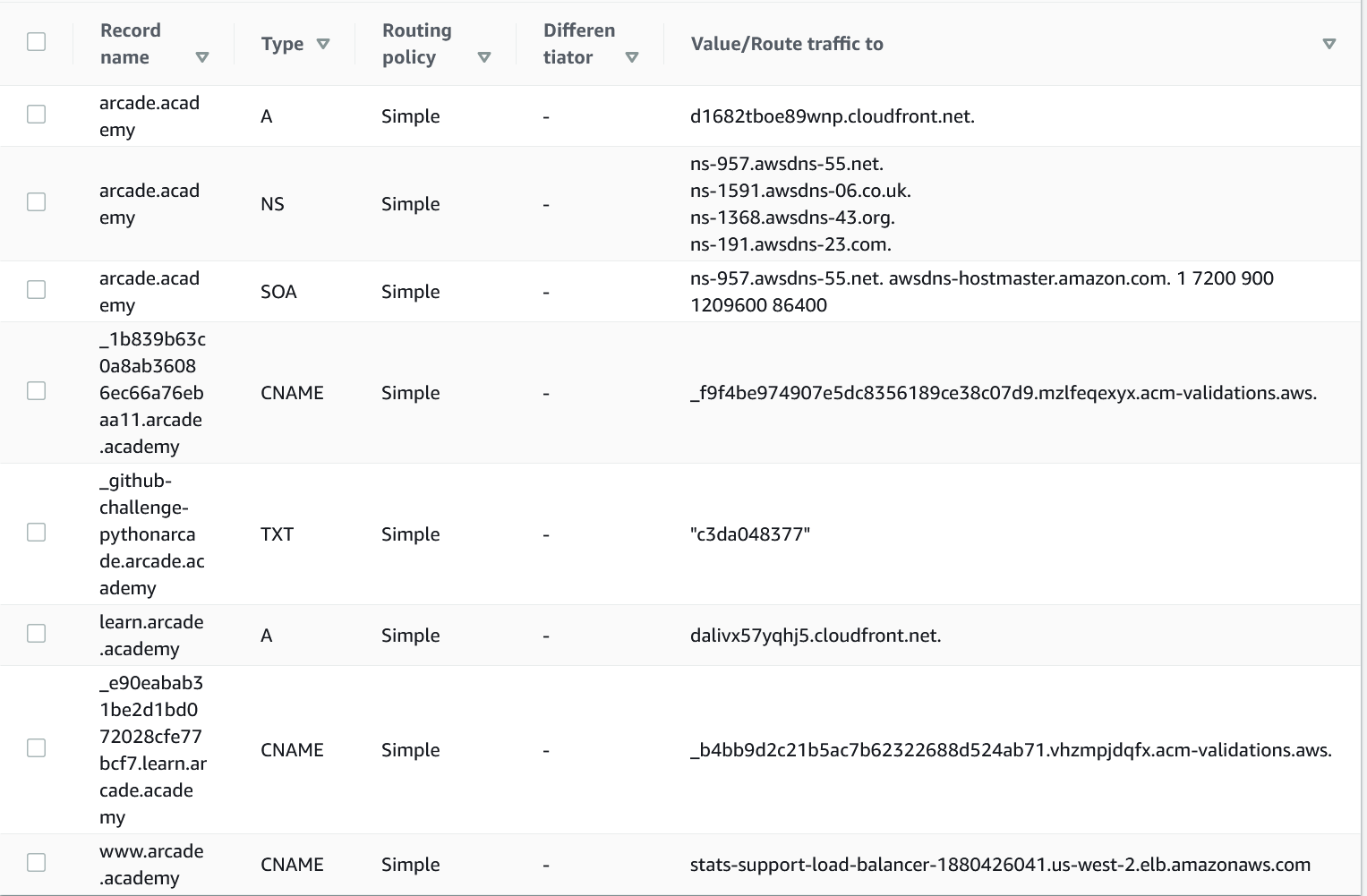
Name Server Record Types
- SOA – Start of Authority record. It holds the primary name server for the domain, an e-mail address of the person responsible for the domain, and how long each record should be cached
-
A – This associates an address like www.mydomain.example to 192.168.1.100
-
AAAA – This is just like an A-record, but for IPv6
-
CNAME – Domain name alias. It allows you to point a computer like www.mydomain.example to a different domain like www2.myotherdomain.example.
-
MX – Mail exchange record. What computer handles mail at that domain?
-
NS – Name Server record. This identifies the computers that will manage all the name server records for the domain.
Addresses Can Be Hardcoded
- Linux: /etc/hosts
- C:\Windows\System32\Drivers\etc\hosts
Public DNS
- Google
- 8.8.8.8
- 8.8.4.4
Reverse Lookup
It’s also possible to find a domain name record with an IP address, which is called a reverse look-up.
If you do a Wireshark packet trace during one of these lookups, the request will look weird. For example, a reverse lookup on 192.168.1.100 gives a lookup request for 192.168.1.100.in-addr.arpa. ARPA is a special top level domain used for reverse lookups and a few other items. It is a left-over from the original ARPANET that predated the Internet.
ICMP
- Internet Control Message Protocol
- Sends message back to computer if router can't forward packet to destination
- Used in creating a 'trace route' for how our data gets to the final destination
Address Resolution Protocol (ARP)
- Each node keeps table of IP to MAC mappings
- Want to see what your computer has? Type "arp"
- Don't know the IP address for a destination?
- Node sends ARP probe. Who has 192.168.1.1?
- Broadcast ARP packet with IP filled in and MAC with zeros
DHCP
- Dynamic Host Configuration Protocol
- Figures how to set computer's IP address, DNS servers, gateway, and netmask
- Before, we used to have to type this in manually
- Routers usually have these servers built-in
Networking: Layer 3 Networking Layer
By Paul Craven
Networking: Layer 3 Networking Layer
- 1,252



