for education

&

presents
Ethical Hacking Workshop

BY
RISHABH SINHA
Founder & CEO at TecHacks
rishabh.info
Basics of Hacking
First thing first...
What is a hack?
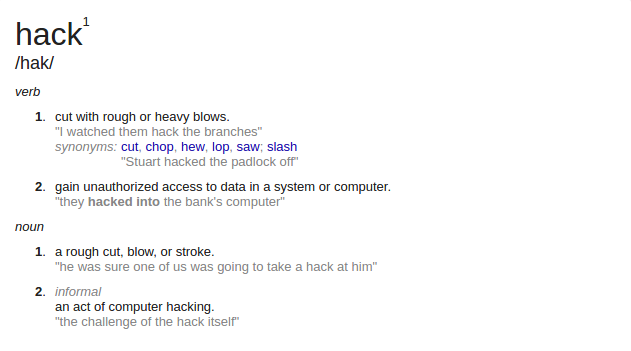
Unconventional way of hacking
Computer hacking
Unconventional Hacking
The way hacking should be looked at
Let's consider some examples
Did you ever break into your fridge?
And connected it from the internet?
that's an unconventional way of hacking!
Computer Hacking
The way hacking is looked at
Did you ever break into a computer system?
And took control on it?
That's computer hacking!
Basics of Ethical Hacking
What is security?
- Resistance or Protection from harm.
- Being free from threat/danger.
Security v/s Protection
- Extremely similar concept but not the same.
- Measures adopted to increase protection is security.
- Type of protection against threats is security.
Hackers v/s Crackers
Hacker
The person who hacks.
Cracker
The person who destroys the system.
Hackers v/s Ethical Hackers
Hackers
- Breaks laws
- Gain access without authorization
Ethical Hackers
-
Does the same stuff with permission/authorization
-
Employed by companies/agencies to perform tests.
Types of Hackers
White Hat Hackers
- Experts who fight against black-hats.
- Use their skills/talent for legal purposes only

Black Hat Hackers
- Use their skills for malicious/harmful intents.
- Threaten people with their confidential data like credit card details, etc.

Grey Hat Hackers
- A combo of white-hats & black-hats.
- They use their skills/talents for national security but through illegal ways.

Some hackers you should know about...
Pranav Mistry
Pranav Mistry is a research assistant at MIT Media Labs and the famous developer of 6th Sense Technology.

Koushik Dutta
Koushit Dutta is the man behind Clockworkmod & ROM Manager for Android.

Hari Prasad
A renowned security researcher, and winner of EFF Pioneer Award.
Found significant vulnerabilities in EVMs (Electronic Voting Machines)

Jayant Krishnamurthy
He is one of the researchers who are behind designing MD6 algorithm (yeah you heard it right, the evolution of MD5). He is a top level computer theorist and researcher.

That's it.
Visit slides.com/rishabhsinha for more.
Follow me on twitter:
@risiofficial
Basics of Hacking
By Rishabh Sinha
Basics of Hacking
Rishabh Sinha introduces the basics of Hacking, Cyber Security/Ethical Hacking, & Types of Hackers.
- 537



