E2E Security
11 December 2019
Rob Bosman
Overview
- Encryption - basic concept
- Secure data transport
- Certificates
- End-to-end encryption (briefly)
- Workshop
access servers via HTTP and HTTPS
with one and two way authentication
from Java
Basic concepts
- Plain text
- Encoded
- Minified / Obfuscated
- Compressed
- Hashed
- Encrypted
Encoded
-
Character encoding
-
URL encoding
-
Base64
| Character |
Unicode |
|---|---|
| e | U+0065 |
| é | U+00E9 |
| π | U+03C0 |
| ℝ | U+211D |
"π ∈ ℝ" ↔ '%CF%80%20%E2%88%88%20%E2%84%9D'
"π ∈ ℝ" ↔ z4Ag4oiIIOKEnQ==
| ASCII (00 - 7F) |
ISO-8859-1 (Latin-1) |
UTF8 |
|---|---|---|
| 0x65 | 0x65 | 65 |
| - | 0xE9 | C3 A9 |
| - | - | CF 80 |
| - | - | E2 84 9D |
Minified / Obfuscated
var _0x10d9=['#msg','html','log','Hello\x20world!'];(function(_0x5c4d6e,_0x1aa57b){var _0xe6bb66=function(_0x36c08b){while(--_0x36c08b){_0x5c4d6e['push'](_0x5c4d6e['shift']());}};_0xe6bb66(++_0x1aa57b);}(_0x10d9,0x83));var _0x42a6=function(_0x2deb60,_0x33e65c){_0x2deb60=_0x2deb60-0x0;var _0x4fd15f=_0x10d9[_0x2deb60];return _0x4fd15f;};const m={'t':_0x42a6('0x0')};$(_0x42a6('0x1'))[_0x42a6('0x2')](m['t']);console[_0x42a6('0x3')](m);
// My message:
const message = {
text: 'Hello world!',
}
$('#msg').html(message.text);
console.log(message);Javascript
Minified
Obfuscated
const message={text:"Hello world!"};$("#msg").html(message.text),console.log(message);Compressed
- Lossless
ZIP, BMP, PNG, WAV
- Lossy
JPEG, MP3, MP4, H-264
algorithms
Hashed
- One-way 'projection'
- Indexing collections, e.g. Java HashSet
-
Algorithms: MD5, SHA-2, SHA-3
-
Fingerprint, thumbprint
- Error or tamper detection
- Message Authentication Code (MAC)
Hashed
MD5("Valori E2E Security")
= 28:1B:76:E8:DB:40:21:6B:DF:7A:CE:F1:2F:A2:FC:88
MD5("Valori E2E Security ")
= DC:D5:D1:1A:06:33:38:D1:8B:E8:58:94:61:32:C0:FA
MD5("Walori E2E Security")
= 39:D7:50:CD:C3:46:DF:F5:46:26:5D:1E:02:B2:73:72
MD5("Valori E2E Security", "secret")
= BC:E8:20:63:FC:1D:CA:71:67:FF:B4:99:7B:55:C1:63
MD5("secret", "Valori E2E Security")
= 71:40:CA:02:C1:0E:83:40:EA:01:7A:63:79:E8:4F:F4
ENCRYPTED
- Hash algorithm
-
Secret key
- (Pseudo)random numbers
- Exclusive OR (XOR)
XOR
0 |
0 |
1 |
1 |
0 |
0 |
1 |
1 |
|---|
0 |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
|---|
same?
then 0
different?then 1
| 0 | 1 |
|---|
| 0 |
|---|
| 0 | 1 | 1 | 0 | 0 | 0 | 0 | 1 |
|---|
ENCRYPTED
0 |
0 |
1 |
1 |
0 |
0 |
1 |
1 |
|---|
0 |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
|---|
0 |
1 |
1 |
0 |
0 |
0 |
0 |
1 |
|---|
plain text
cipher text
0 |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
|---|
0 |
0 |
1 |
1 |
0 |
0 |
1 |
1 |
|---|
secret key
0 |
1 |
1 |
0 |
0 |
0 |
0 |
1 |
|---|
0 |
0 |
1 |
1 |
0 |
0 |
1 |
1 |
|---|
0 |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
|---|
Block cipher
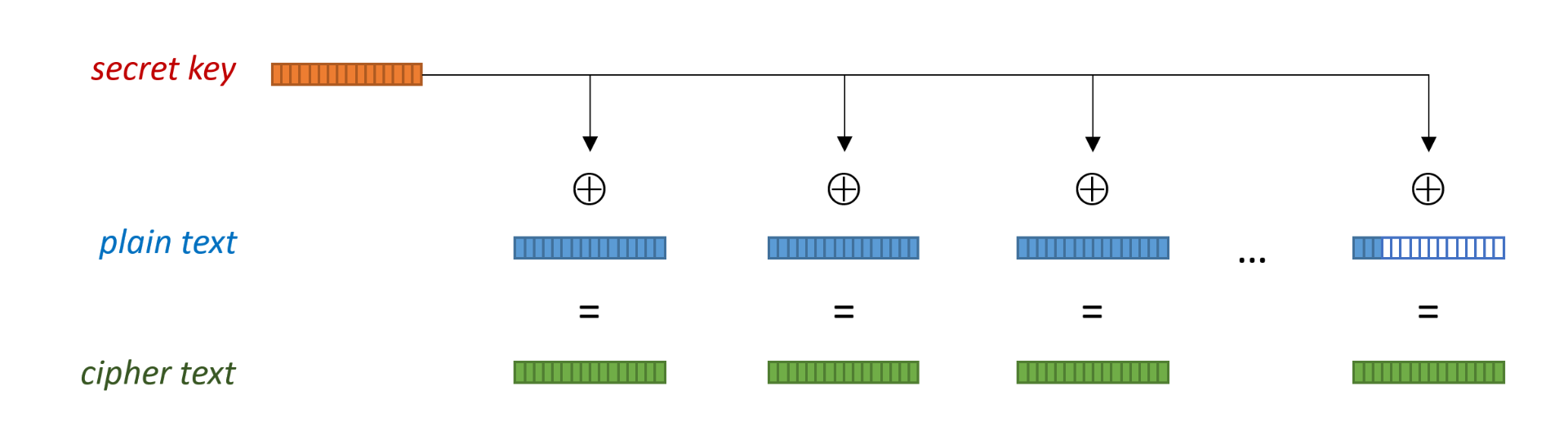
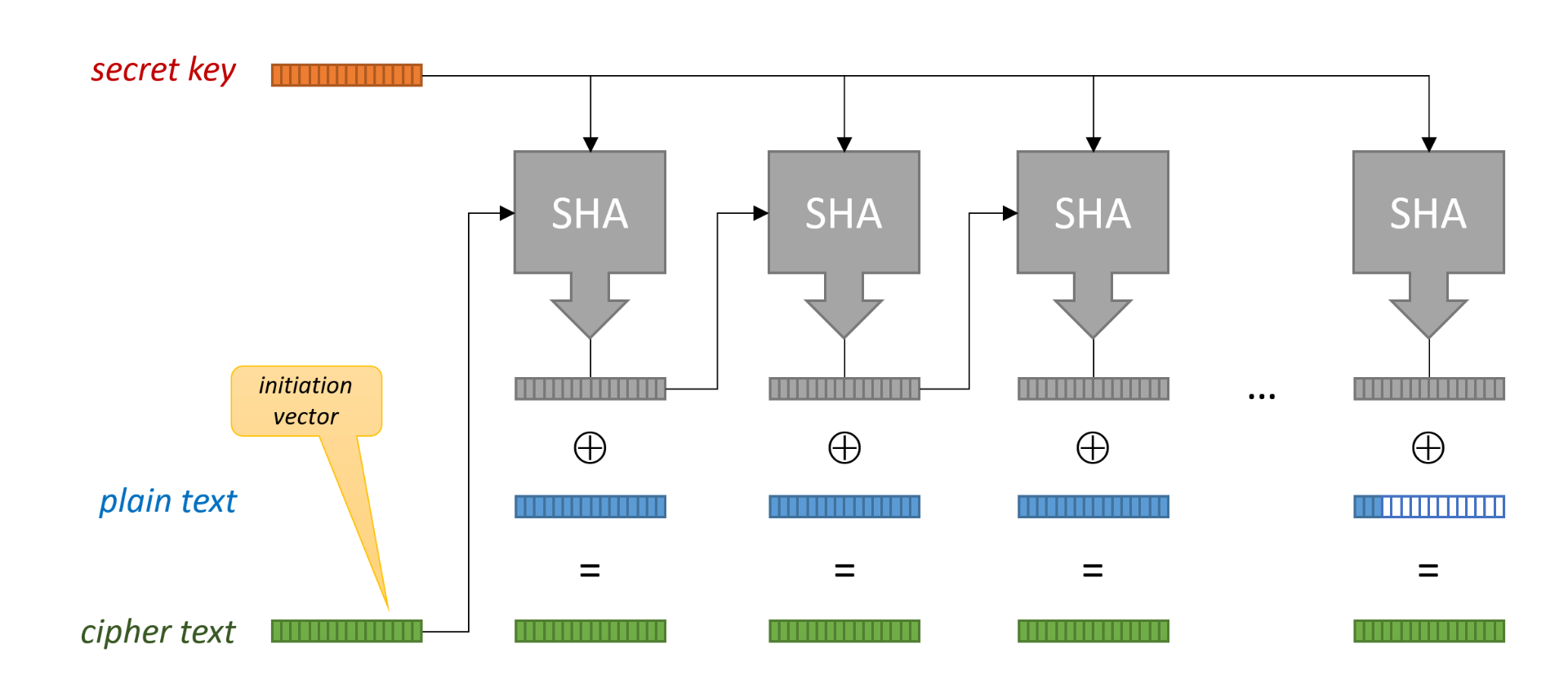
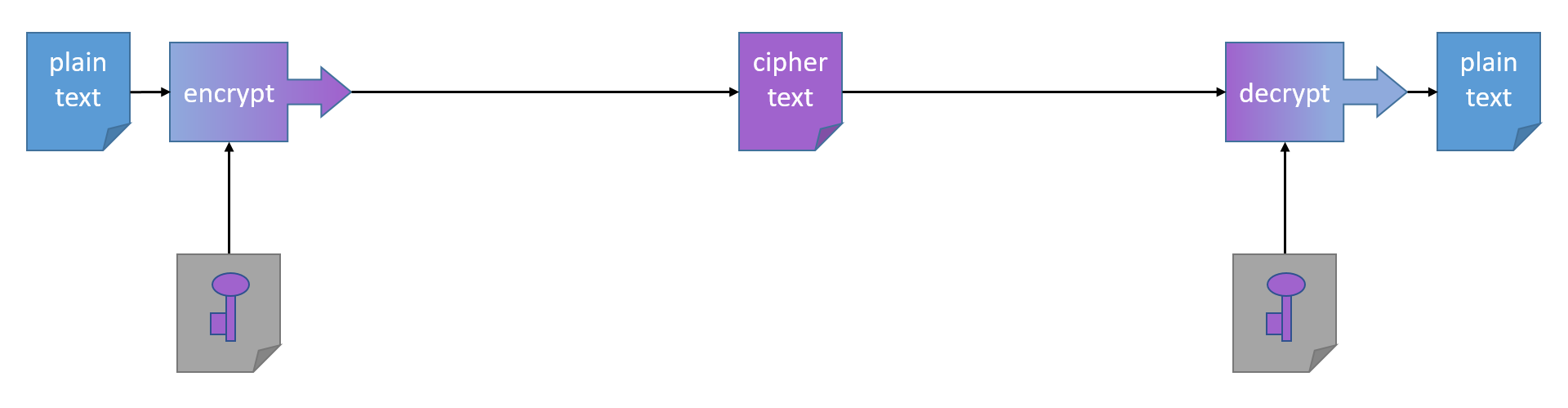
Secure data transport
Secure data transport
- Shared info: key + algorithm
- Symmetric encryption
- Key exchange
- Authentication
- PKI + RSA
- SSL + TLS
Symmetric Encryption




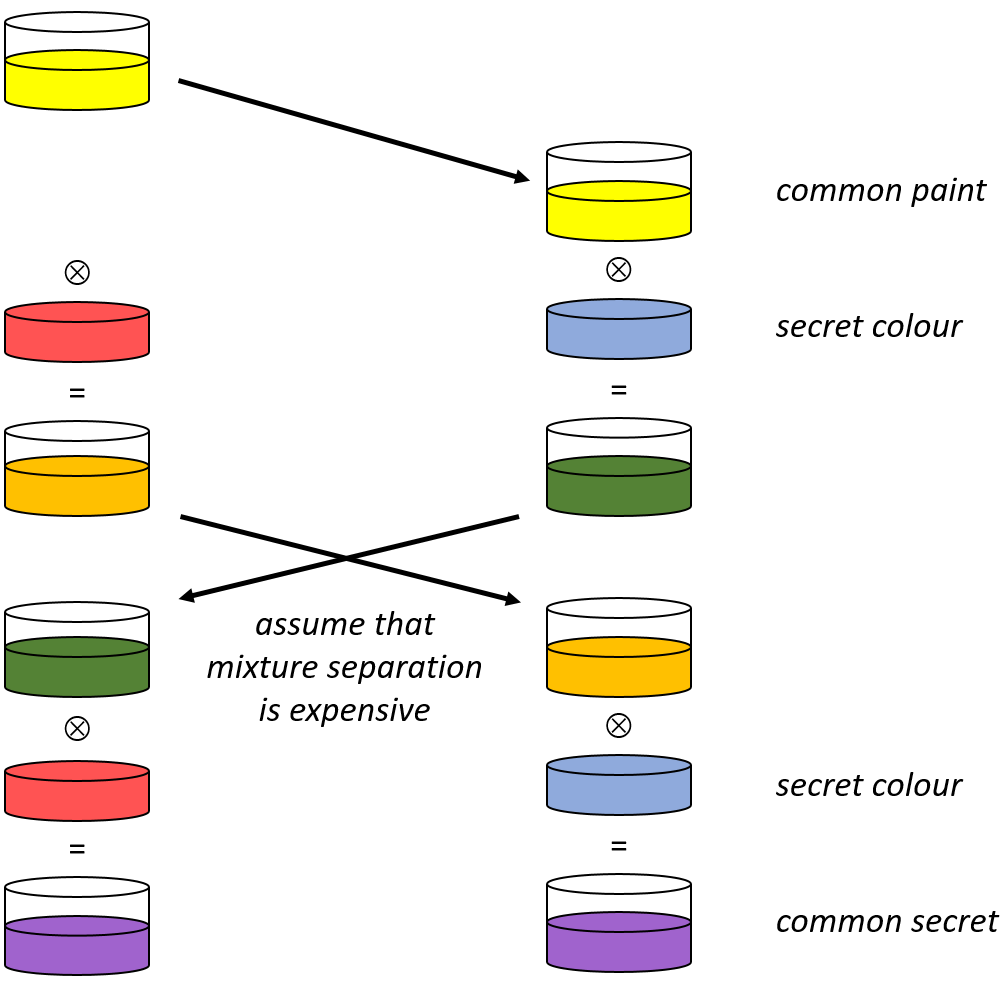
Diffie-Hellman key exchange
MAN-IN-THE-MIDDLE (MITM)
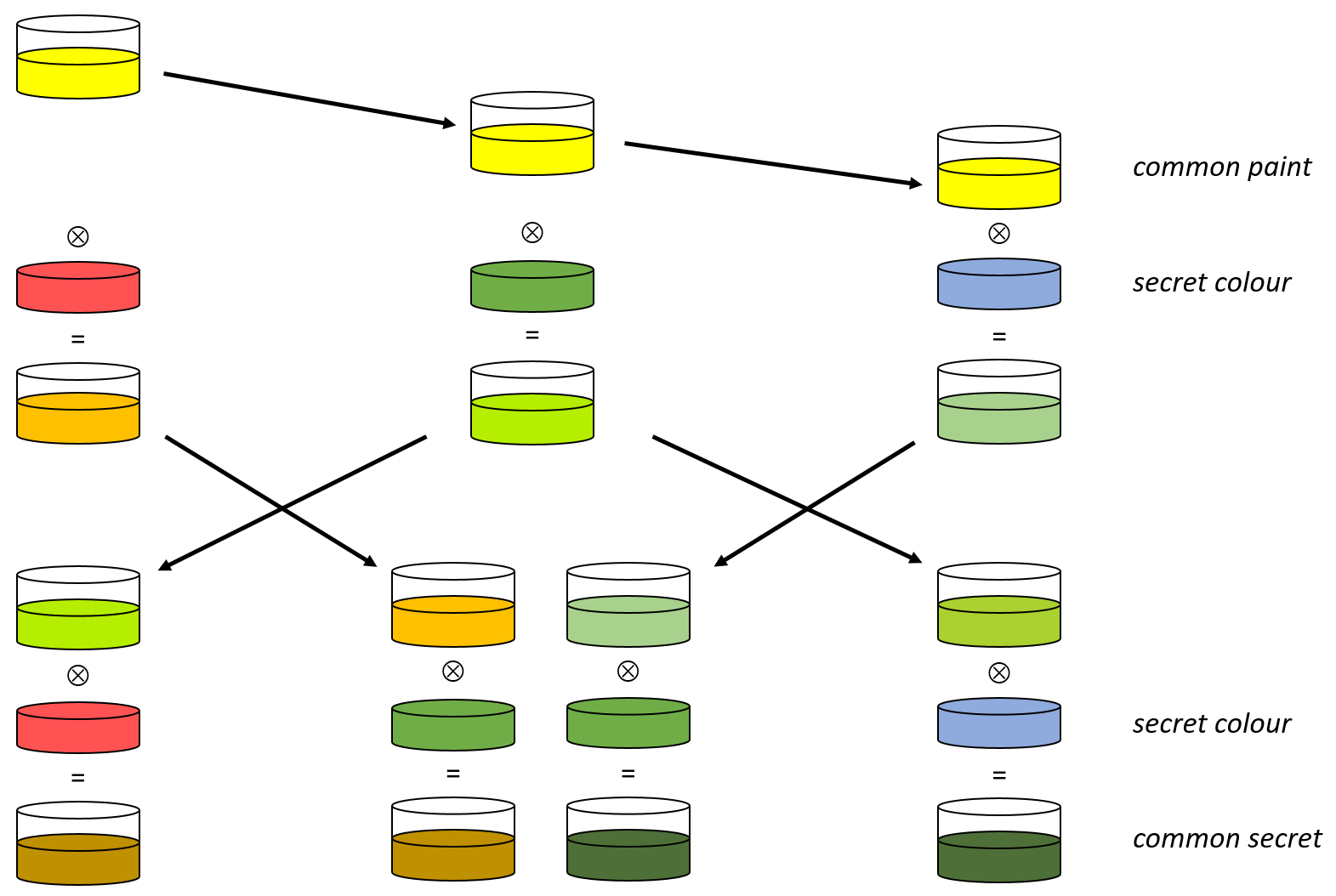
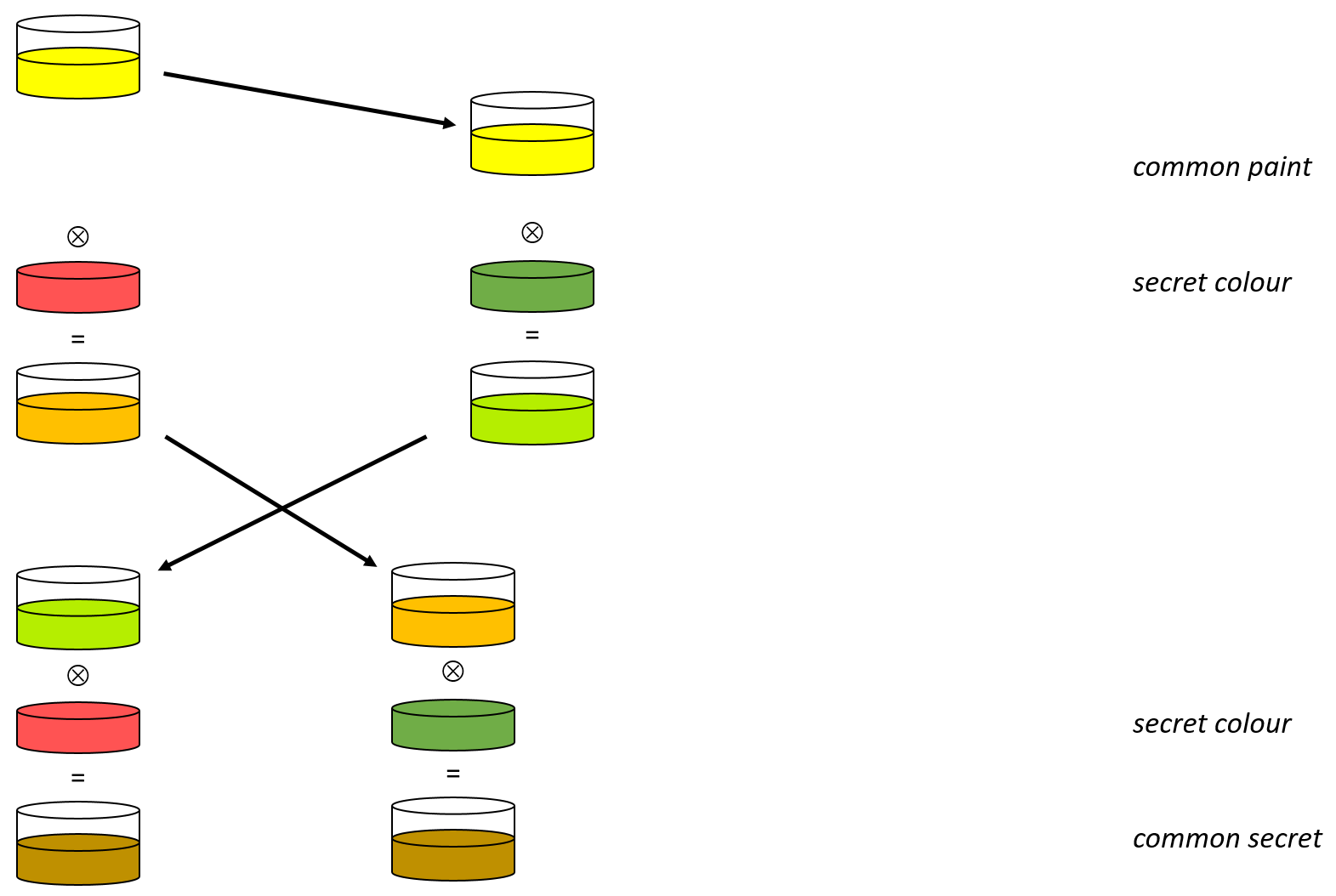
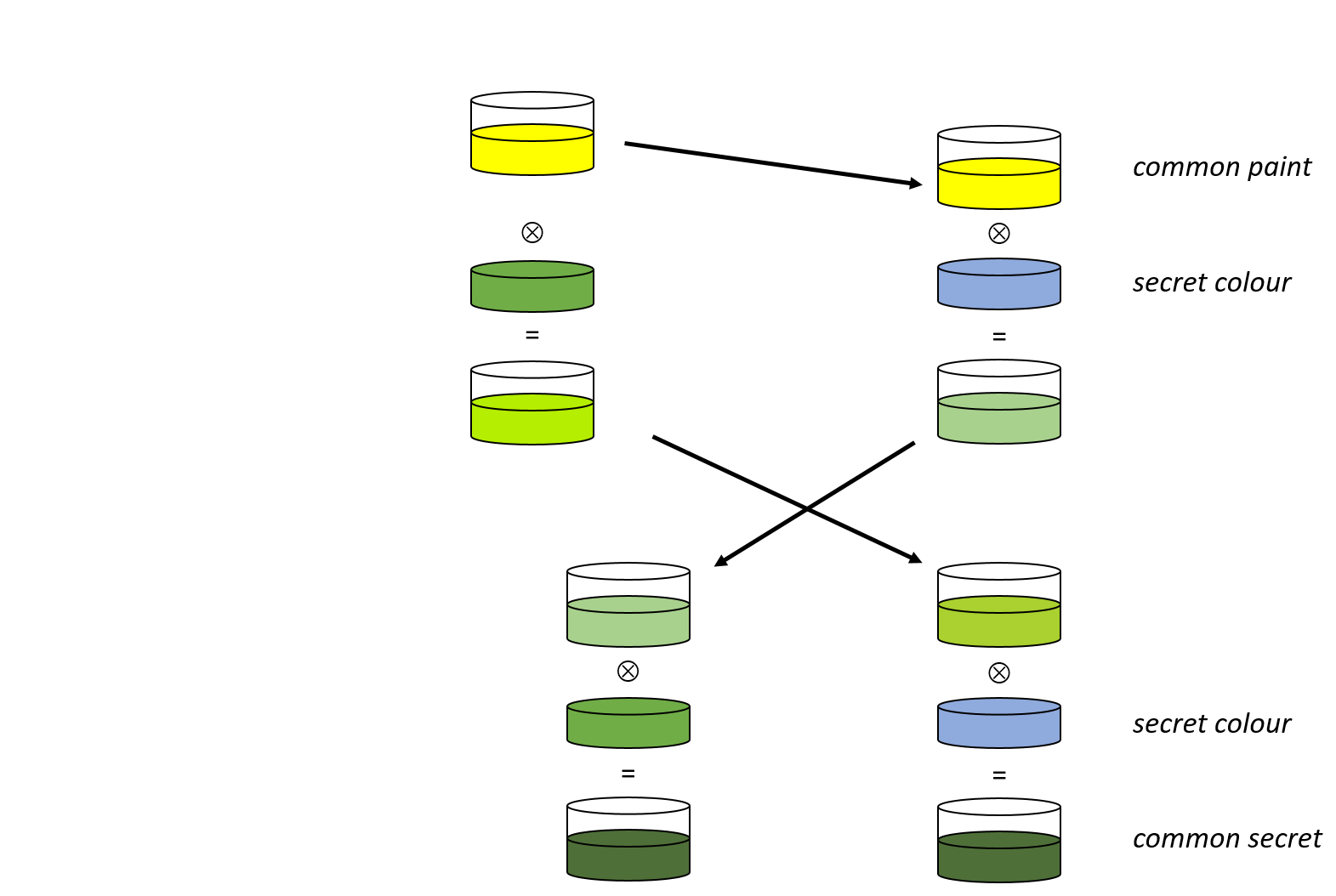
MITM Attack



Authentication
- Authentication
"Ben jij dat wel?"
- Authorisation
"Mag jij dat wel?"
Public Key Infrastructure

public
private
PKI + RSA
- PKI - Public Key Infrastructure
- RSA - Rivest, Shamir and Adleman
- Additional info, e.g. validity, purpose
- Certificate
Certificates
Certificates
- Signed public key
- Chaining
- Certificate Authority
- TrustStore / KeyStore
- Server TLS certificate
- Client TLS certificate
SSL - TLS
- SSL - Secure Socket Layer
- TLS - Transport Layer Security
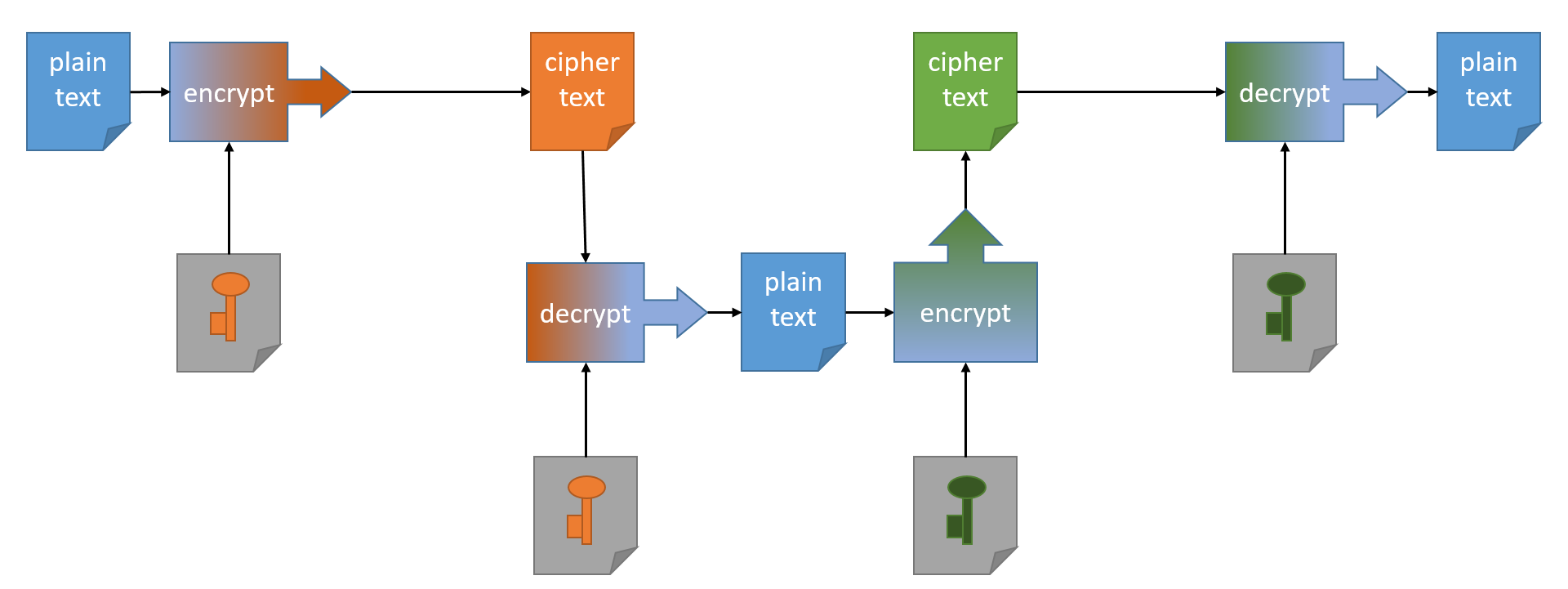
E2E ENCRYPTION
E2E Encryption
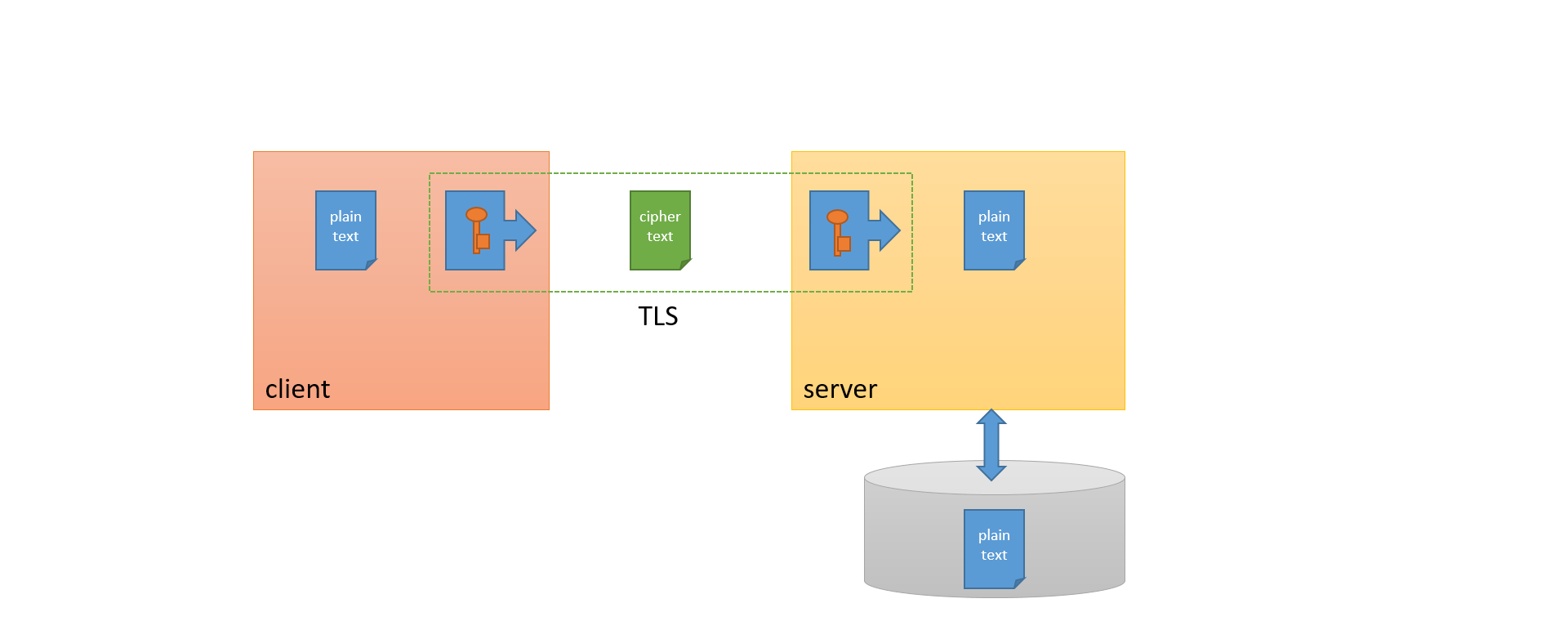
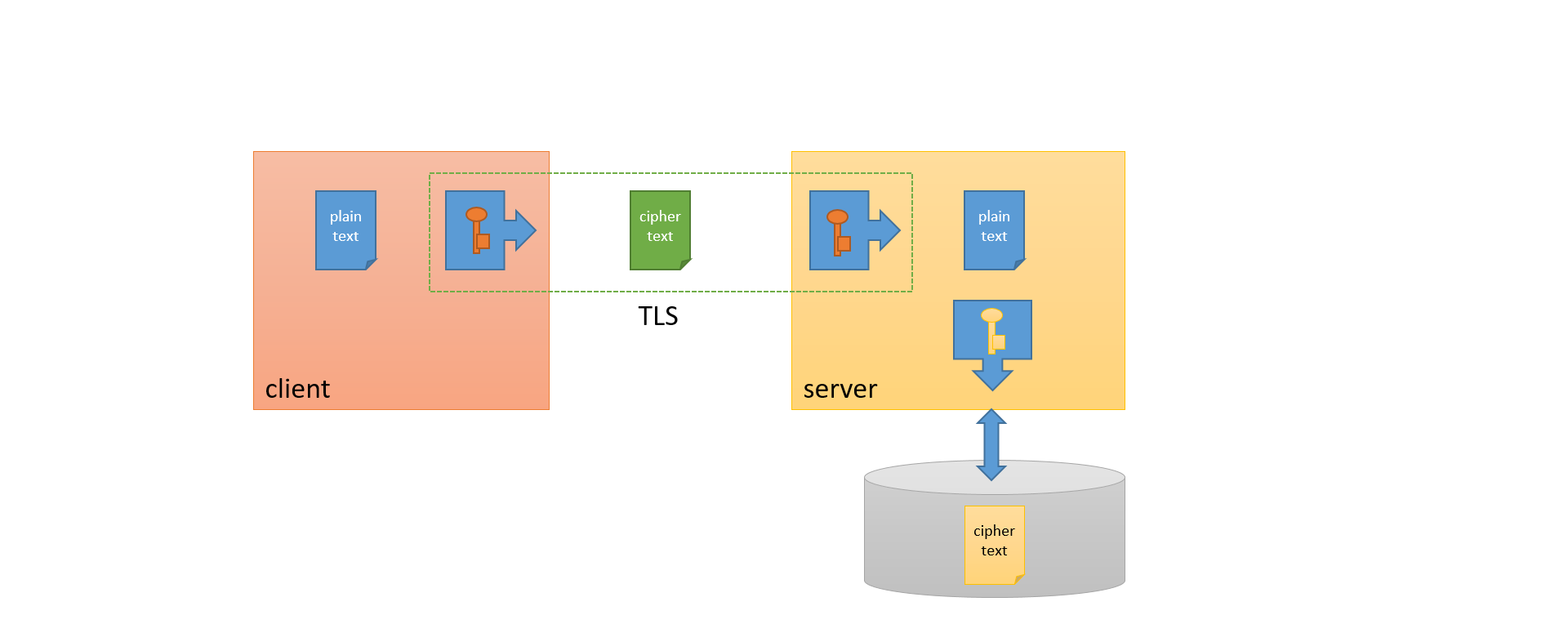
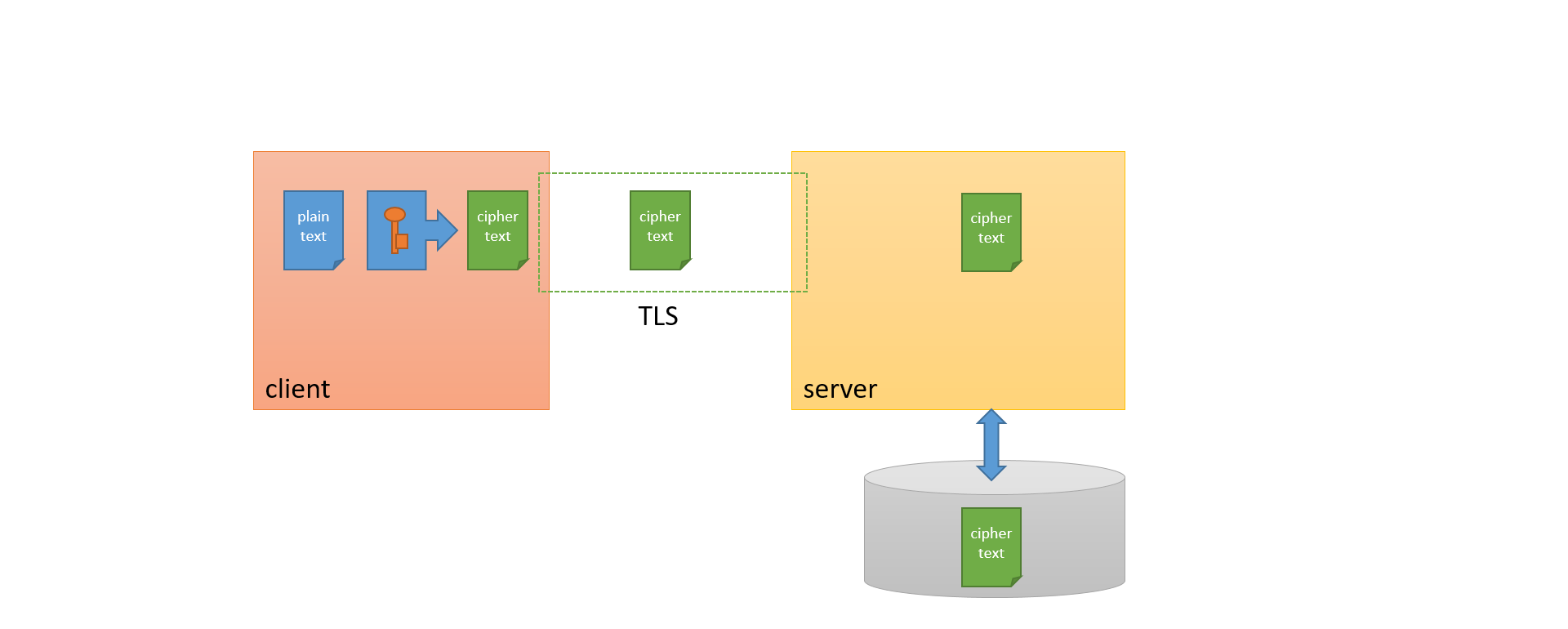
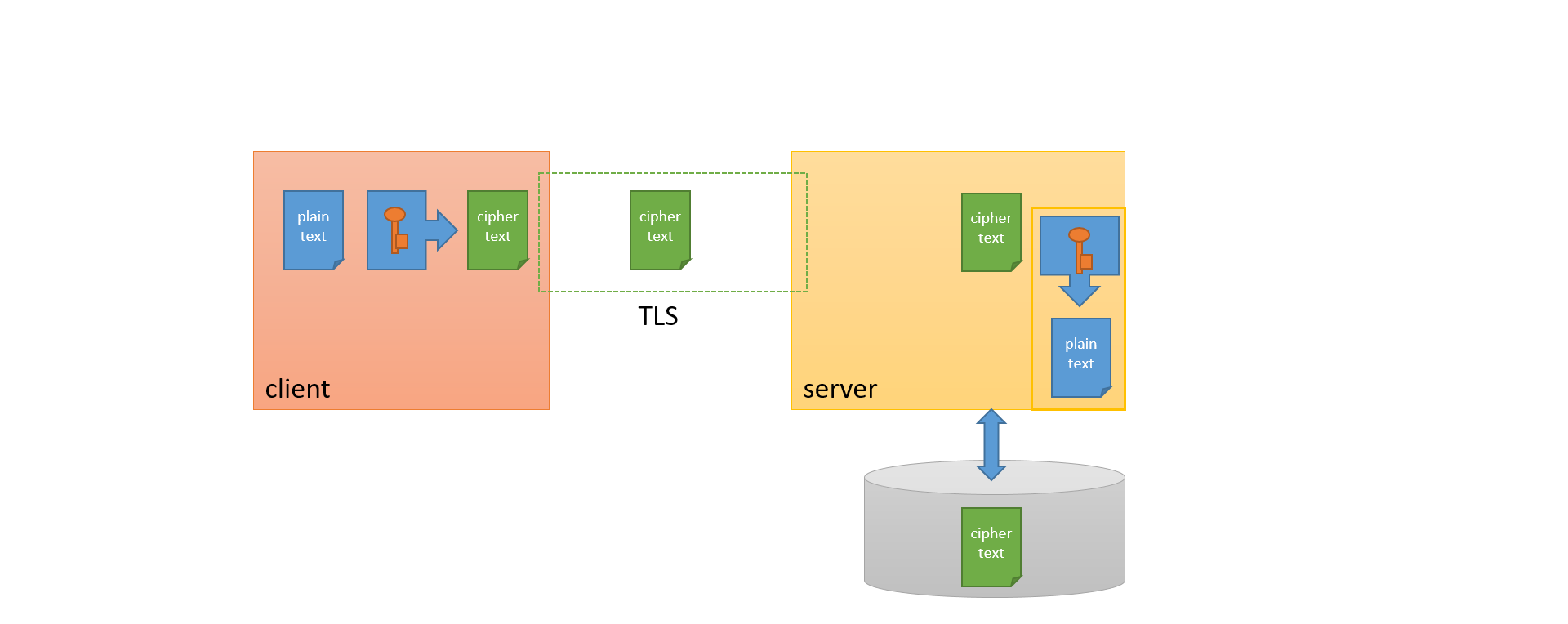
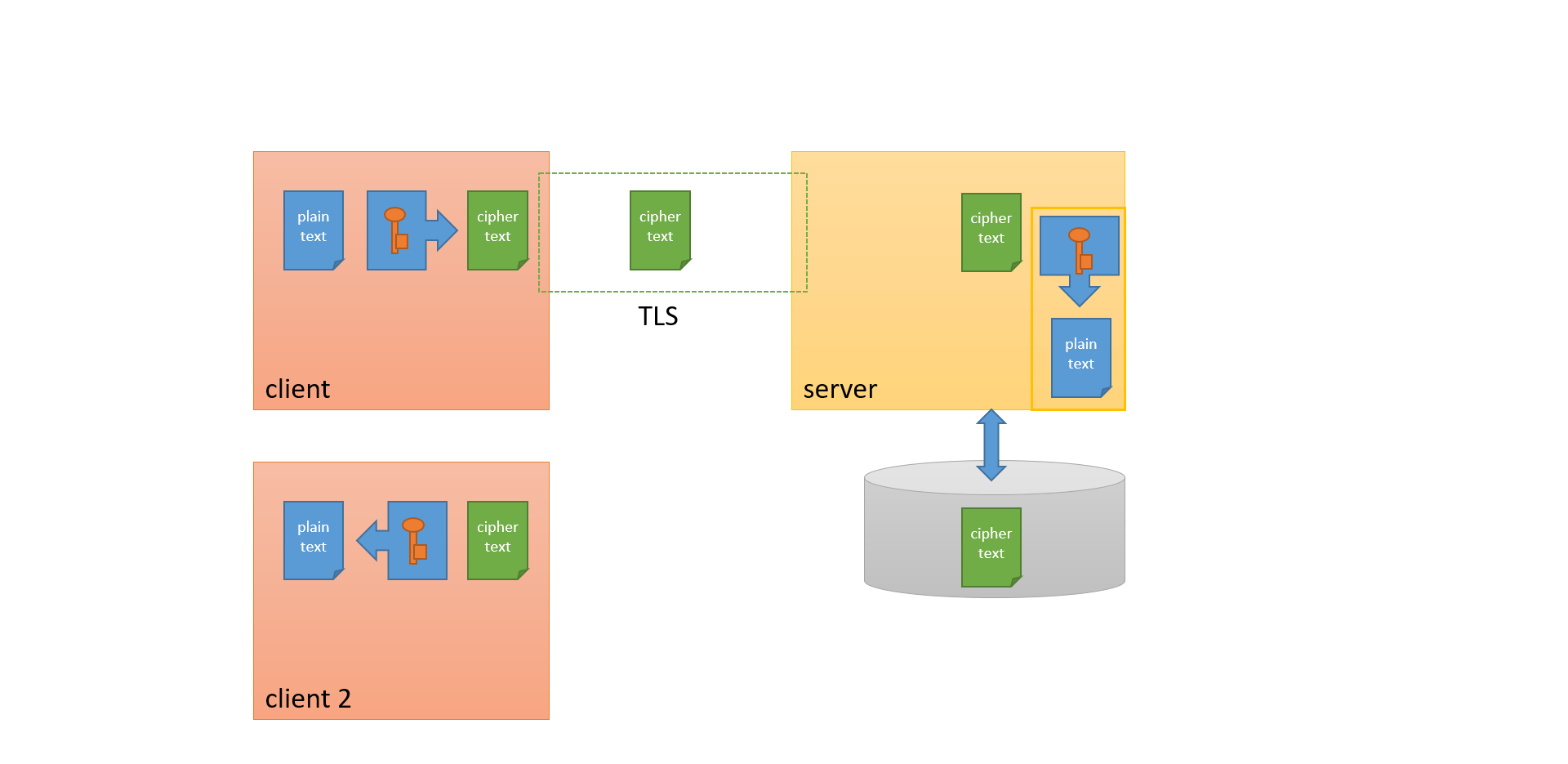
Workshop
https://github.com/RobBosman/valori.E2E-Security
E2E Security
By Rob Bosman
E2E Security
- 102



