

Steve Borosh

@424f424f
github.com/rvrsh3ll
medium.com/@rvrsh3ll
https://enterpriseattack.futuresec.io/
https://slides.com/rvrsh3ll/azure-console
Black Hills Information Security

-
Azure Cloud Shell
- Capabilities
- Demo: SSH Tunnel to access cloud database.
-
Dynamic Device Code phishing
- Overview
-
Phishing Direct Send
- Overview
- Unban a burned IP
- Demo: Dynamic Device Code
-
Offensive Azure Command and Control
- C2 redirection
- Demo: C2 Redirection
-
Payload Hosting
- Demo: Serve IPFS Payload
- Yammer Phishing
- Overview
Talking Points
Disclaimer:
Beware of the terms of service. Microsoft may suspend and ban your subscription for violations such as hosting malware and domain fronting.

Operator Setup
- Windows 10/11 VM
- WSL
- Azure tenant
- Microsoft 365 business account
- Wireguard
- DBeaver
- SSH Tunnel
Azure Cloud Shell

Azure Cloud Shell Overview
- Requires a subscription to Microsoft Azure (trial/pay-as-you-go)
- PowerShell or Bash hosted by Microsoft
- portal.azure.com
- shell.azure.com
- Windows Terminal
https://learn.microsoft.com/en-us/azure/cloud-shell/overview
Key Concepts
- Cloud Shell runs on a temporary host provided on a per-session, per-user basis
- Cloud Shell times out after 20 minutes without interactive activity
- Cloud Shell requires an Azure file share to be mounted
- Cloud Shell uses the same Azure file share for both Bash and PowerShell
- Cloud Shell is assigned one machine per user account
- Cloud Shell persists $HOME using a 5-GB image held in your file share
- Permissions are set as a regular Linux user in Bash
- IPv4 (Currently)
Deploying a VM
az group create --name myResourceGroup --location eastus
az vm create -n MyVm -g MyResourceGroup --image UbuntuLTS --generate-ssh-keys --public-ip-sku Standard

Setup SSH Tunnel

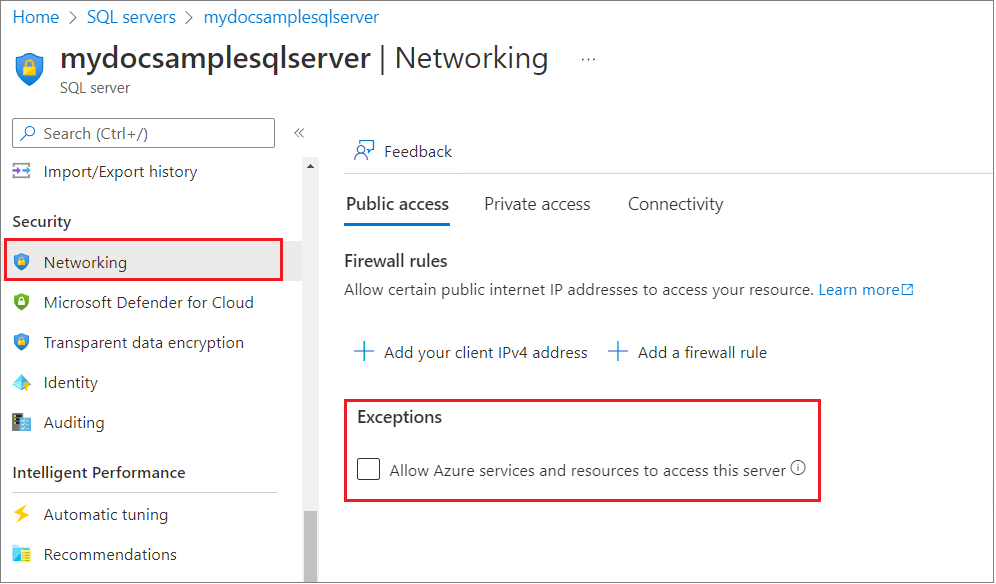
Azure Databases
*.database.windows.net
Allow Azure Resources
Query

DBeaver

SSH Tunnel to AzureSQL

Dynamic Device Code Phishing
Access_tokens FTW
Device Codes
- Login to your device from your computer
- Code or QR code
- Netflix, Discord, Slack as examples
- Provides remote access to services
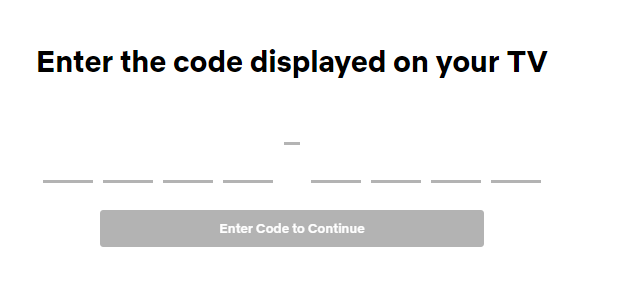
Microsoft

microsoft.com/devicelogin
TokenTactics
-
Receive access and refresh tokens from device logins
-
RefreshTo-OtherServices
-
Read / Send Email
-
Read / Send Teams
-
Enumerate AzureAD
https://github.com/rvrsh3ll/TokenTactics
Co-Developer @0xBoku
Important Info
- 15 Minute expiration from code generation
- 1 hr access_token expiration
- 90 day refresh_token expiration
- Adheres to conditional access
Example Request

Example Request

Example Request Sign-in LOg

Dynamic Codes
- Hosted on VPS and Azurewebsites
- Azurewebsite requests code from the VPS and displays to visitor
- 15 minutes from time of website visit
Azure-App-Tools
-
Assortment of Azure apps
-
Easily deployable with Az
-
Phishing sites*
-
Drive-by downloads*
-
C2 redirection*
-
*.azurewebsites.net
-
Dynamic Device Codes
* Subject to Microsoft Terms of Use
https://github.com/rvrsh3ll/Azure-App-Tools
How it works
Azure Log - Source IP


How it works v2
Azure Log - Source IP

BLog
https://www.blackhillsinfosec.com/dynamic-device-code-phishing/
Phishing Direct Send
Direct Send
- company-com.mail.protection.outlook.com
- Unauthenticated SMTP !!
- External -> Internal
- Internal -> Internal
- https://www.blackhillsinfosec.com/spoofing-microsoft-365-like-its-1995/
Send-MailMessage -SmtpServer company-com.mail.protection.outlook.com -From company@service-now.com
-To administrator@company.com -Subject "Ticket for upgrade" -Message "Totally legit" -Attachment .\ClickMe.rdpUnban IP Address
https://sender.office.com/

Dynamic Device Code PHISHING

I have a code, Now what?
- Check your access token https://jwt.io/ (client-side)
Token Audience


User and Permissions
RefreshTo-
2. Switch Audience

Browse
POST /owa/ HTTP/2
Host: outlook.office.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 2703
Referer: https://login.microsoftonline.com/
Origin: https://login.microsoftonline.com
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Te: trailers
code=0.A&id_token=ey
https://github.com/rvrsh3ll/TokenTactics/blob/main/resources/example_requests/owa_request_v2.txt
https://www.trustedsec.com/blog/hacking-your-cloud-tokens-edition-2-0/

post-access tooling
https://github.com/dirkjanm/ROADtools
https://github.com/BloodHoundAD/BARK
https://github.com/BloodHoundAD/AzureHound
https://github.com/Flangvik/TeamFiltration
- RoadRecon
- BARK
- AzureHound
- TeamsFiltration

Offensive Azure Command and Control
C2 Redirection
- Azure CDN
- https://medium.com/@rvrsh3ll/hardening-your-azure-domain-front-7423b5ab4f64
- Azure Apps
- https://github.com/rvrsh3ll/Azure-App-Tools/tree/master/IIS-Redirector
- Azure Service Bus
- https://github.com/Flangvik/CobaltBus
C2 Redirector Protection
- "Magic Header"
- X-ASPNet-Version: 1.5
- CDN-level
- web.config for Azure Websites
IIS redirector

Mythic settings

AZ Website settings






Azure C2 Redirection

Payload Hosting
File sharing
- SharePoint
- OneNote
- Yammer
- Azurewebsites.net
azure websites file hosting
- Trusted domain/IP ranges
- Easy deployment via Az cli "az webapp up"
- Web.config for Mime Types

One Two Punch
- Azurewebsites.net
- IPFS


Payload Hosting

Yammer phishing
Yammer Community

Yammer Community invite received

Attach Files

Share Directly


steve@blackhillsinfosec.com
https://futuresec.io


Hack Miami X
By rvrsh3ll
Hack Miami X
- 1,345

