Interactive Client Portfolio
Solution Grid
|


Press > to continue
ALPS curates a B2B Marketplace of innovative solutions for industry verticals

Press > to continue
|



ALPS receiving the 2022 BDO Alliance Innovation award in Las Vegas

|

ALPS industry verticals
Press > to continue
This interactive presentation overviews the premiere solutions in the ALPS Portfolio:
Click on Solution, or press > to continue

|

Press ⋁ to learn more
or press > to continue

Sollensys
Immutable Data Archives for Ransomware Protection

|

Problem:
Ransomware is rampant
Solution:
Sollensys - The most secure way to store an archive of your data via blockchain technology


|

Any company that has immutable access to a copy of their data, would not need to pay a ransom.


|

With $18B in ransoms paid out globally in 2020, companies are either:
1. Not successfully backing up their data, or
2. Getting their backups encrypted


|

The question to ask is:
If someone had the password to your backup, could they delete your data?
Unfortunately, for most people, the answer is 'Yes'.


|

The answer is often Immutability with an (*)
When companies say your data is immutable, it typically comes with an *asterisk. It may be time based deletion permissions, or it may be air-gapped and mirrored, but ultimately, they all rely on software read/write permissions.


|

Sollensys' answer is: Immutability via physics
When Sollensys offers immutability, they offer a true, undeletable archive of your data on the blockchain.
Thousands of nodes across a distributed ledger of multiple networks across multiple geofenced locations ensure that your data is completely indestructible.


|

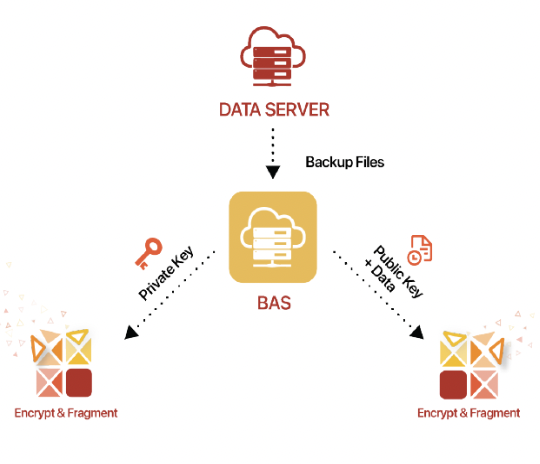
Dual Blockchain Architecture
Keeping your encrypted data on a separate network from your unencryption key assures your data is completely unreadable until the recovery process is started.


|

Cost Effective
Sollensys offers a cost effective solution to prevent your data from ever being deleted, scaling from small businesses to large enterprises.


|

Learn More
Download the whitepaper to learn more about Sollensys' Data Assurance solution


|

Digital Immunity
Zero Day Defense via In Memory Runtime Protection
Press ↓ to learn more
or press → to continue

|


Problem:
Manufacturing cybersecurity faces a unique challenge due to complex Operational Technology (OT) infrastructure
Solution:
Digital Immunity hardens the OT layer using a zero trust model

|


All OT environments which are unable to apply timely cybersecurity patches operates with an exposed environment subject to debilitating cybersecurity attacks.

|


In Memory Runtime Protection prevents all malicious code, including Zero Day Attacks and Fileless Attacks, on both modern and legacy, unpatchable systems.

|



How it Works
Digital Immunity (DI)'s Zero Trust model requires all applications to be pre-authorized using proprietary DI tool that scans unique memory signature.

|


DI is a self contained protection mechanism, no updates are required.
"Set it and forget it" -Pfizer CISO

|


DI stops cybersecurity threats in their tracks, without disruption.

|



|



Pfizer conducted a competitive review of the leading OT Cyber Manufacturing solutions.
DI was the ONLY solution to prevent ALL penetration testing attacks.

|



Pfizer now utilizes DI across their global manufacturing network.

|


MORE VALUE FROM LEGACY DEVICES
Protection for Un-Patched and Un-Patchable systems: Extending usability of Legacy Systems and Software
REDUCE SECURITY OVERLOAD
Stops File-less, File-based, Known or Unknown (e.g. Zero-Days) attacks while replacing 4+ security tools
NEGLIGIBLE PERFORMANCE IMPACT ON HOST
< 1% CPU 40MB RAM
Operational Attributes

|


Learn More
Download the Datasheet to learn more about Digital Immunities Endpoint Protection Solution
Fuse Analytics
Secure Compliance Warehousing & Data Retirement


|

Press ↓ to learn more
or press → to continue


|

Problem:
Storing and maintaining Sensitive data is complex due to Security and Shifting Data Compliance legislation.
Solution:
Fuse Analytics provides a cloud based legacy data warehouse solution with dynamic retention policies.


|

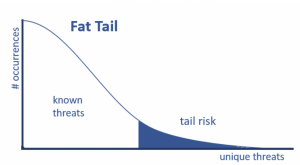
PII (Personally Identifiable Information) contains a long tail risk


|

Storing PII shorter than needed causes compliance issues, and longer than needed causes security and unnecessary legal exposure


|

Fuse Analytics provides a secure, managed interface to access to your data for analytics and audits.


|

Fuse Analytics provides a secure, managed interface to access to your data for analytics and audits.


|

Watch a demo:


|

Learn More
Download the Strategies for HR & Payroll Archiving whitepaper
INVOKE
Premiere Robotic Process & Intelligent Automation
Press ↓ to learn more
or press → to continue


|



|

"Companies with advanced automation programs will obliterate - not merely beat - the competition"
Forrester Research


|

Intelligent Automation (IA) technologies are the fastest
approach to business innovation.


|

Digital transformation is easier said than done.
Legacy Systems lack ability to integrate
Manual tasks hinder operational efficiency
AI models don't typically account for security


|

INVOKE has the tools, experience and credibility to guide you on your automation journey.


|

"Automation is our business, that's why we've invested resources into automating our own processes, so customers can benefit from the tools we've created to manage their own automations"
-Johnny Ramondino, President
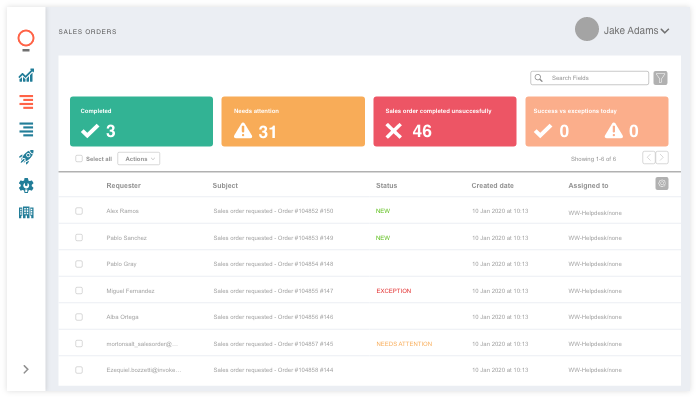
ARIA is designed to manage processes, handle exceptions, schedule automations, and provide reporting


|

"The good thing about automation is that it can do anything. The bad thing about automation is that it can do, well, anything"
-Johnny Ramondino, President
DISCOVER is designed to effectively find areas ripe for automation. This six week monitoring process identifies the exact processes that your employees are
INVOKE provides a process to know exactly where to start in your automation journey, and how much efficiency you're leaving on the table.


|

Premiere Partner of Blue Prism & UI Path
Allows for As-a-Service use of Digital Workers to scale cost effectively




|

INVOKE's satisfied customers



|

OPERATIONAL INSIGHTS
TRAINING AND ONBOARDING
PROCESS IMPROVEMENT
COMPLIANCE
Let INVOKE guide your automation journey
EMPLOYEE ENGAGEMENT
PROCESS DOCUMENTATION
AUDITS


|

Book a time here

Learn More
Book a call with Johnny Ramondino, INVOKE President
Thank you!
Joe Gatto, Sam Peret
joe.gatto@acadialps.com
samuel.peret@acadialps.com

Acadia Leadership Partners Inc.
ALPS | Premiere Solutions
By Samuel Peret
ALPS | Premiere Solutions
- 272



