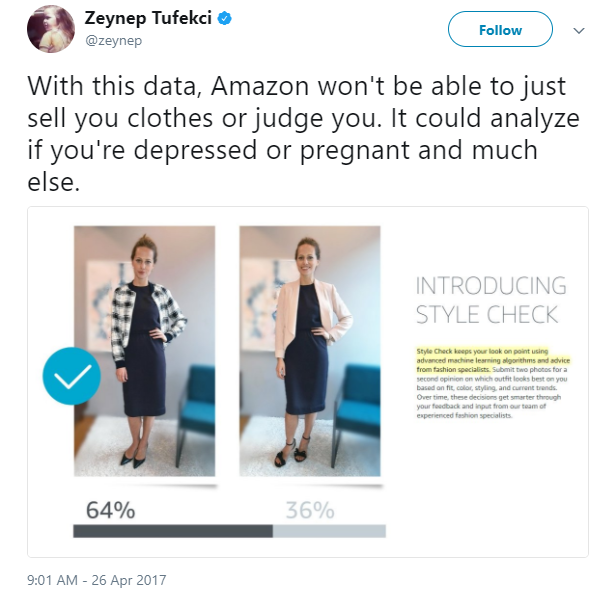
J0NJ4RV1S|SAINTCON2017

TH4NK Y0U!
This new form of
information capitalism
aims to predict and modify
human behavior as a means to
produce revenue and market control.
Shoshana Zuboff 2015
Google has seen 30 trillion URLs, crawls over 20 billion of those a day and answers 100 billion search queries a month.
Hal Varian 2014
We have had to develop new types of databases that can store data in massive tables spread across thousands of machines and can process queries on more than a trillion records in a few seconds.
Amit Singhal 2012
Data is becoming everything.
This so-called big data is actually plucked from our lives without our knowledge and without our informed consent.
All of us no longer exist to be employed and served. We exist to be harvested, harvested for behavioral data.
Shoshana Zuboff 2014
The economic basis of the Internet
is surveillance.
Every interaction with a computing device leaves a data trail, and whole industries exist to consume this data.
Maciej Cegłowski 2017
The one thing [Google and Facebook] share is an insatiable appetite for data.
They want to know where their users are, what they’re viewing, where their eyes are on the page, who they’re with, what they’re discussing, their purchasing habits, major life events (like moving or pregnancy), and anything else they can discover.
Maciej Cegłowski 2017
Together, these companies control some 65% of the online ad market, which in 2015 was estimated at $60B.
There are two interlocking motives for this data hunger: to target online advertising, and to train machine learning algorithms.
Maciej Cegłowski 2017
Prior versions of "perform mass data collection in order to understand the behavior of people":
- 1870s - The origin of Credit Bureaus
- 1988 - Roger Clarke: Dataveillance
- 2002 - DoD: Total Information Awareness
- 2005 - Christopher Slobogin: lack of
regulation over Transaction Surveillance - 2013 - Edward Snowden: details of the
NSA's global surveillance programs
How is this different?
Magnitude
Motivation
Methods
Privacy = Secrecy
vs.
Privacy = Control
“I’ve Got Nothing to Hide” and Other Misunderstandings of Privacy
- Daniel Solove [PDF]
When you say ‘privacy is dead,’ if what you mean by that is secrecy and hiding away and not being connected to the world around you, I may agree with you.
However, privacy as a functional definition of how we define ourselves, how we live in a culture, what we can expect in terms of morality, ethics, respect and security —
it’s alive and well, baby, alive and well.
Privacy is about control.
We may not mind sharing our personal lives and thoughts, but we want to control how, where and with whom.
A privacy failure is a control failure.
Privacy is the right to consent.
Privacy is the right to withdraw consent, to only provide information to the people you want to provide it to, when you want to provide it.
Privacy is evolving
Privacy is about control
Privacy is the right to consent
Privacy is a battleground


"Not to protect herself from the sun's glare, but rather from the media glare.
In other words, she is misusing the visor rather effectively."
PoC at BSidesSLC 2017



Threats, Bad Ideas,
& Causes for Concern
- Instant facial recognition & correlation at scale
- Geofenced content delivery & user identification
- Unblockable device & browser fingerprinting
- Cross-device tracking & ultrasound beaconing
- Retailer & municipal location tracking
- Inescapable data brokers
- Biometrics, IoT, and more...
Facial Recognition & Correlation


Facial Recognition & Correlation
Facial Recognition & Correlation
Facial Recognition & Correlation
Law Enforcement
- 2014: FBI wants a database of >52 million photos
- 2016: 1 of 2 American adults is in an LE FR network
- 2016: California DoJ spent over $2M on FR
- 2017: British police scan every face at football final
- 2017: Taser wants to live-stream body cams this year, add live FR by 2018, and use its data “to anticipate criminal activity” and “predict future events”
Facial Recognition & Correlation
-
2017: FR is a part of daily life in China
- Publicly shame jaywalkers
- Offer customized meals at KFC
- Replace cards and PINs at ATMs
- Stop runners from taking shortcuts
- Stop toilet paper theft at public parks
- Demo'd police-controlled drones with FR
- Track people inside buildings to control access
- "To influence behavior and identify lawbreakers"
Facial Recognition & Correlation
- Don't have a social media profile
- Don't ever get arrested
- Don't travel by plane
- Don't live in China
- Don't go in public
- Wear a mask - unless you live in one of these 13 states or in these countries, in which case it might be restricted or illegal to cover your face in public areas.
Defense?
North Carolina Penal Code §14-12.8.
Wearing of masks, hoods, etc., on public property.
No person or persons shall in this State, while wearing any mask, hood or device whereby the person, face or voice is disguised so as to conceal the identity of the wearer, enter, or appear upon or within the public property of any municipality or county of the State, or of the State of North Carolina.
No Masks




Untested possibilities




Untested possibilities

Untested possibilities

Untested possibilities


Geofenced Content Delivery
& User Identification
'90s-'00s: Location-based device tracking, via GPS or cell towers, for monitoring vehicle fleets or sending out emergency notifications
2002: Geofencing as a method to identify mobile device users and send them custom content
2010-12: Geofencing as an enhancement feature - apps do something extra; businesses focus their marketing; investors find better real estate leads
Anti-Abortion Groups Use Smartphone Surveillance to Target ‘Abortion-Minded Women’ During Clinic Visits
An advertiser's technology allowed anti-abortion groups to send propaganda directly to a woman’s phone while she is in a clinic waiting room.
Legal, but ethically questionable. "It is a violation of one of a woman’s most private moments, tapping into information about her health and medical history in order to sell her on an ideology."
Update: The Attorney General of Massachusetts announced a settlement agreement with the Boston-based firm to prevent their activity in Massachusetts.
“Consumers are entitled to privacy in their medical decisions and conditions. This settlement will help ensure that consumers in Massachusetts do not have to worry about being targeted by advertisers when they seek medical care.”
Anti-Abortion Groups Use Smartphone Surveillance to Target ‘Abortion-Minded Women’ During Clinic Visits
How Uber Deceives the
Authorities Worldwide
City regulator identification techniques include:
- geofencing government offices
- matching the credit card to city organizations
- matching locally-available inexpensive cell phone models to the devices of Uber installs
- scraping social media profiles and other public online information sources
Malicious Potential:
Spear-fencing / Geophishing
- Purposely deceive or mislead a vulnerable person
- Benign ads lead to malicious or phishing websites
- User de-anonymization leads to physical tracking
-
Location targeting: polling station, medical offices, rehab centers, domestic abuse shelter, church
- Job targeting: journalists, law enforcement, business executives, legislators, banking, utilities
- Disable location services when not needed
- Don't install 'free' apps that display ads
- Restrict permissions of installed apps
- Install an ad-blocker: uBlock Origin
- Situational awareness
Defense?
Unblockable Device Fingerprinting
Device fingerprinting: identifying a device by identifying, collecting and correlating its unique hardware, software, or connection characteristics.
Primary use is to prevent fraud by identifying when the same device is repeatedly used to commit fraudulent actions.
Client-based (installed app collects data) vs. Server-based (analyze connection info & data sent)
Unblockable Browser Fingerprinting
Canvas fingerprinting: a website uses HTML5 to instruct the browser to draw an image. Variations in a device's GPU and graphics driver cause variations in the rendered image.
Cross-browser fingerprinting: get the browsers to perform a variety of tasks that draw on operating-system and hardware resources—including graphics cards, multiple CPU cores, audio cards, and installed fonts—that are slightly different for each computer.
Unblockable Browser Fingerprinting
- Extreme compartmentation - combinations of browser + VMs + VPNs or IP addresses
- Install EFF's Privacy Badger, but it only blocks 3rd-party fingerprinting
- Install an ad-blocker: uBlock Origin
- Block JavaScript from running
- Use the Tor browser
- Visit and support your local public library
Defense?
Cross-Device User Tracking &
Ultrasound Beaconing
Cross-Device Tracking: IDing the same user across devices - phone, laptop, TV, camera
Probablistic: comparing large sets of data - device, IP address, browser fingerprint, location
Deterministic: logging in; using the same email address across services; signing in across devices
Cross-Device User Tracking &
Ultrasound Beaconing
Ultrasound beaconing: a device (TV) emits an ultrasonic audio signal that is detected by software on another device (phone or laptop)
uBeacSec.org: security and privacy research into the ultrasound tracking ecosystem
2017: FTC reports that tracking often takes place without consumers’ knowledge; consumers have limited choices to control tracking; and collection can result in caches of more - and more sensitive - data that needs to be protected
How much is your consent worth? $5-$12 / mo
Cross-Device User Tracking &
Ultrasound Beaconing
- Install an ad-blocker: uBlock Origin
- Add background audio noise to your life
- Hope that phone manufactures enable filtering of ultrasonic frequencies
- Plug in earbuds with a disabled mic

Defense?
Retailer & Municipal
Location Tracking
Wi-Fi tracking: Sensors are spread across a physical area to record the broadcasted MAC address and signal strength of WiFi radios, mapping a device's movement and location
Retailer & Municipal
Location Tracking
-
2016: London's subway authority tracked people at 54 locations to map how they moved through and used the stations
-
2016: Grocery store light bulbs flicker codes intended for the store's app on customers' smart phones
- 2017: "The Aisles Have Eyes" - stores track and profile customers to provide them custom pricing and service
Defense?
- Turn off your Wi-Fi & Bluetooth
- Turn off your camera
- Don't connect to a store's 'free' WiFi
- MAC randomization is broken
- Wear a hat or disguise
- Don't return to the same store
- Don't even go in
Inescapable Data Brokers,
Collection, & Analysis
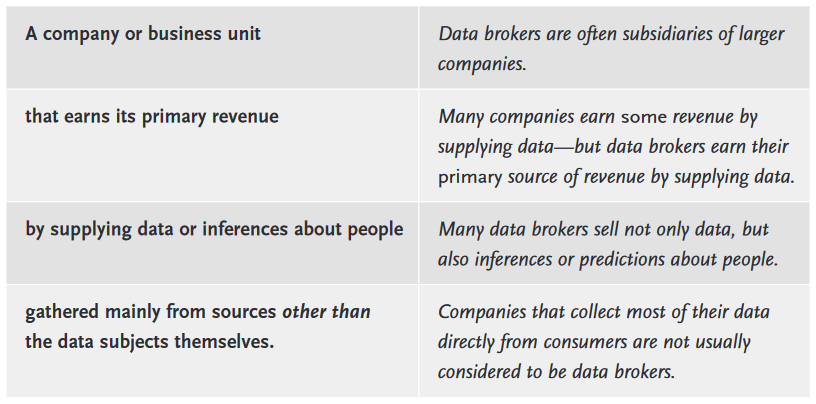
The marketing industry is attempting to profile and classify us all, so that advertising can be customized and targeted as precisely as possible.
Google, Facebook, Apple and thousands of lesser-known companies are making it their policy and business to profile us in detail, all in the hopes of crafting better sales pitches.
Inescapable Data Brokers,
Collection, & Analysis
2012: Target, 2002: 'If we wanted to figure out if a customer is pregnant, even if she didn’t want us to know, can you do that?'
2017: Snapchat advertisers have access to "data from offline purchases—like stats from a loyalty card program—that will be used to target consumers with relevant ads."
Inescapable Data Brokers,
Collection, & Analysis
2017: Freedom of the Press Foundation "specifically targeted EPA and NOAA employees in the Washington, D.C. area, urging them to leak newsworthy documents to one of the dozens of news organizations that use SecureDrop."
2016: Gizmodo bought Facebook ads targeted to federal employees requesting them to submit leaks about Trump
Inescapable Data Brokers,
Collection, & Analysis
2017: Why Build a Muslim Registry When You Can Buy It?
"For the price of $138,380, the website offers a database file containing more than 1.8 million individual names, addresses, cities, states and ZIP codes. Just 7.5 cents per person.
ExactData.com boasts a total database of 200 million US contacts, which can be filtered by 450 terms. These include categories such as “Religion” and “Ethnicity”, as well as personal information such as “Household Income” and “Vehicle Make”.
Inescapable Data Brokers,
Collection, & Analysis
Inescapable Data Brokers,
Collection, & Analysis
- Don't install 'free' apps that display ads
- Restrict permissions of installed apps
- Restrict apps from connecting out
- Install an ad-blocker: uBlock Origin
- Buy everything with cash
- Don't install apps
- Burn your phone
- Live in a cave
- Accept it
Defense?
Oh, the Humanity!

Oh, the Humanity!
- The Thinning Line Between Commercial and Gov't Surveillance
- The World's Most Valuable Resource is No Longer Oil, But Data
- Data is Giving Rise to a New Economy
- Corporate Surveillance in Everyday Life
- The Information Superhighway has become The Information-Tracking Superhighway
- The Surprising Things Algorithms Glean About You From Photos
- Here's a Chilling Glimpse of the Privacy-Free Future
- Big Data is so Powerful, Nation States Will Fight Over It
- Real-time Location Data is Moving Marketing
- Patents Reveal How Facebook Wants To Capture Your Emotions, Facial Expressions And Mood
In The Future, Everyone Will Have
15 Minutes of Privacy
It's Not Entirely Bad, I Guess...
2015: Syrian refugees get auditable and verified access to UN relief funds via iris scans at ATMs
2016: Using facial recognition and deep learning to hide your screen when your boss is approaching
2017: Dutch pranksters want to make a toaster that burns your toast if your online reputation is bad
2017: IBM's Watson AI mines public profiles of attendees to craft a rave that everyone likes
Are Collection & Misuse Inevitable?
Privacy by Design: build privacy into the product
Privacy Tech: an emerging market sector
Data Ethics: roles, rights, and responsibilities of collecting and analyzing data
Data Protection: laws and regulations controlling how your data and data about you is used
Data Avoidance: don't even collect it
Adversarial Input
Adversarial examples are inputs to machine learning models that an attacker has intentionally designed to cause the model to make a mistake; they're like optical illusions for machines.
-
Genderless Nipples Thwart Instagram's Filter
-
Introduction to Adversarial Machine Learning
- Attacking AI-based Digital Assistants


Omnipresent Surveillance: What We Fear

Omnipresent Surveillance: What We Fear

Omnipresent Surveillance: What We Fear
Omnipresent Surveillance: What We Want
The online world forces individuals to make daily irrevocable decisions about their online footprint.
The surveillance economy works on such information asymmetry: Data-mining companies know everything about us, but we know very little about what they know.
Omnipresent Surveillance: Where We Are
"The only way for an individual to ensure he or she is not subject to collection of biometric information when traveling internationally is to refrain from traveling."
Omnipresent Surveillance: What's Next
Omnipresent Surveillance: What's Next
TH4NK Y0U!
#privatizedselfie



The Surveillance Capitalism Will Continue Until Morale Improves
By J0NJ4RV1S
The Surveillance Capitalism Will Continue Until Morale Improves
- 3,395