We Can (Not) Secure
Introduction to SecDevOps!
This talk is dedicated to
Segment-your-network Woman
and Patch-your-shit Man!
Infracode loves Security
This talk is heavily focused on the buzzy wuzzy cloudy wowdy
AWS Cloudformation kind of environments, but similar patterns can be used in similar "Cloud Orchestrator" Tools*.
My loose interpretation of "DevOps" is the idea of
source control, testing, deployment and code reuse ;)
Infracode is quicker and easier than maintaining different technical silos.... Pulling in infracode PR from a developer to open a Port on the firewall
*HarshiCorp Terraform, OpenStack Heat, Atlas and others.
- CloudFormation: IaaS Templates
- Elastic Compute Cloud "EC2": Xen based Virtual Machines
- Elastic Block Store (EBS): Block level storage
- Simple Storage Service (S3): Networked Storage
- Route 53: DNS (Public and Private Zones)
- Virtual Private Cloud (VPC): isolated networks
- Elastic Load Balancing (ELB): TCP Frontend
- Relational Database Service (RDS): MySQL
- CloudWatch: Monitoring log streams
- CloudTrail: Monitoring AWS API
- Identity and Access Management (IAM): Least privledge
- Simple Queue Service (SQS): One way messaging
Good Buzzwords
- Defense in depth
- Isolation/Seperation/segmentation
- Principle of least privilege (ACL)
- Cattle, not pets
1) Source Control
Maintain a solid git repository for as much as possible: Application Source/infracode/Jenkins/enviromental data.
For the following examples - Assume the following:
- SOE-RHEL72 Repo
- Shared Infracode Repo (Cloudformation & Jenkins)
- Environment Non-Production Repo
- Environment Production Repo
- Microservice (Java) Repo
Each of these Repos are accessible from inside the VPN
to people in the correct LDAP security groups.
+ Read-only access is given as required.
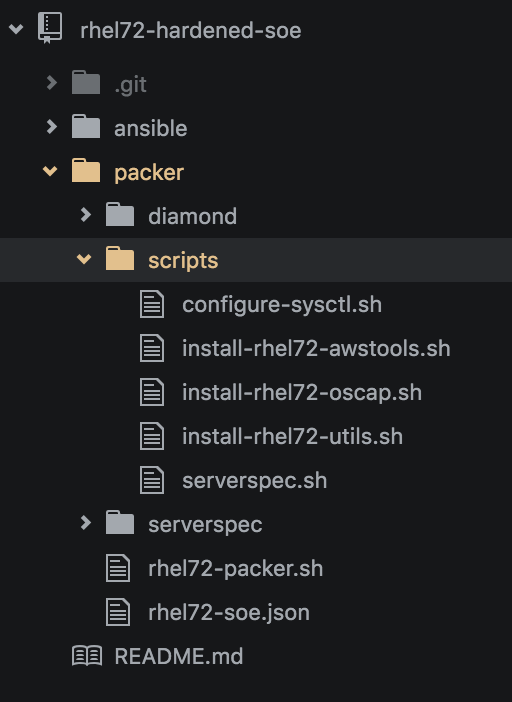
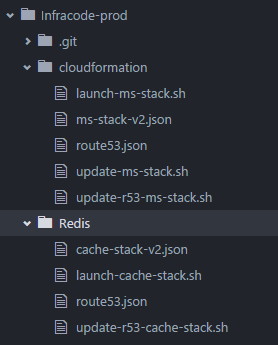
2) One SOE to build them all
The "Hardened" SOE is the sidekick of "patch your shit man"
All of my AWS environment servers are based on a single AMI.
1) Harden single RHEL 7.2 gold release and
utilise in Dev,Test,Pre-Prod and Production.
2) Build AWS launch configuration userdata scripts to maintained to your freerange bespoke machines, but always built on the SOE.

AWS RHEL Packer Serverspec SOE






- Bastion
- Frontend
- Backend
- Build
Tools: Packer by Hashicorp
Tweaking /etc/sysctl.cfg, confirming timezone, installing bastion keys (revoking older keys), run openscap-scanner
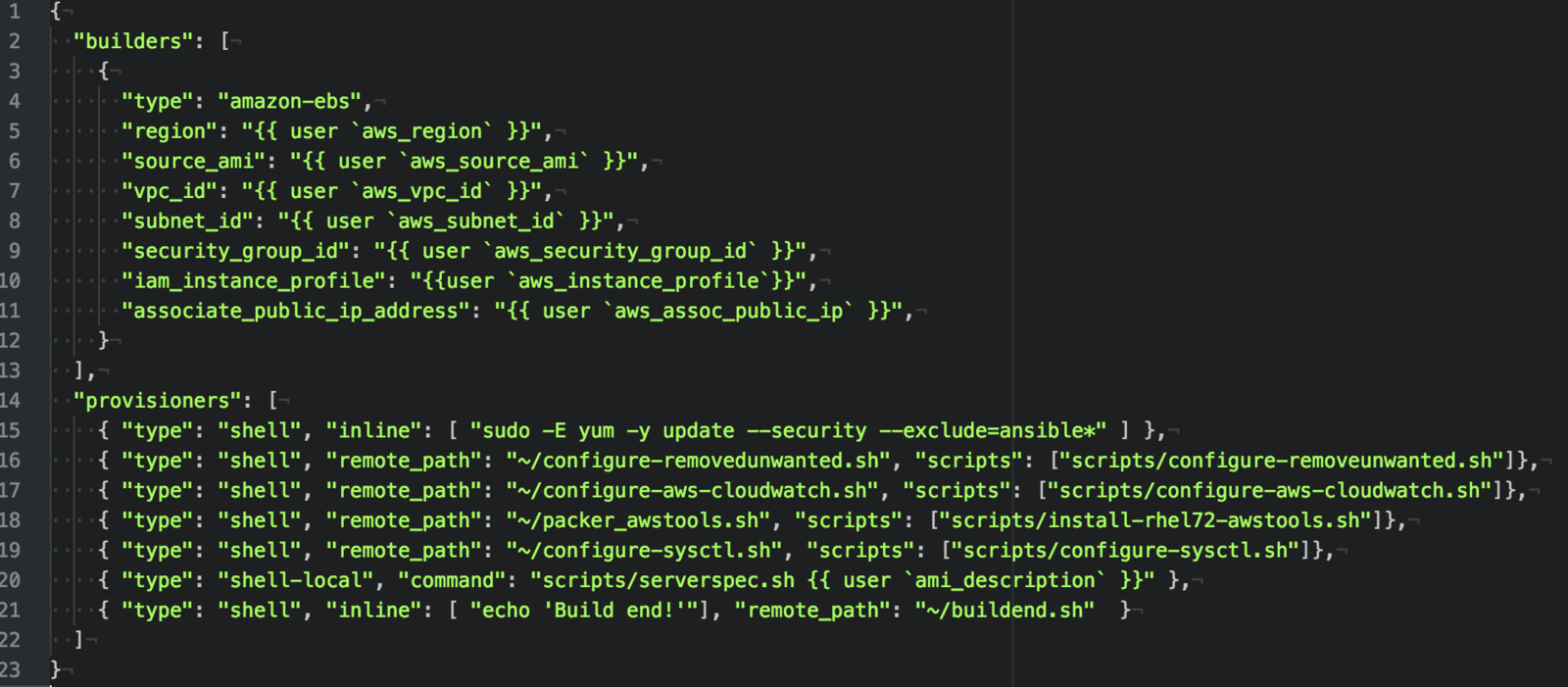
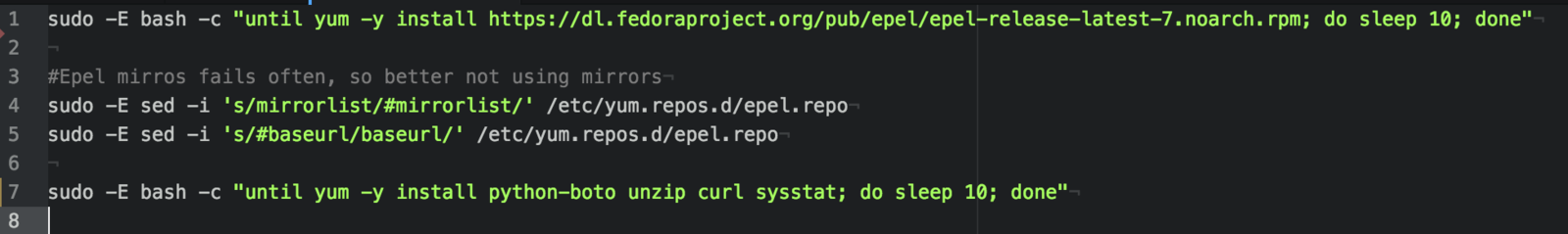
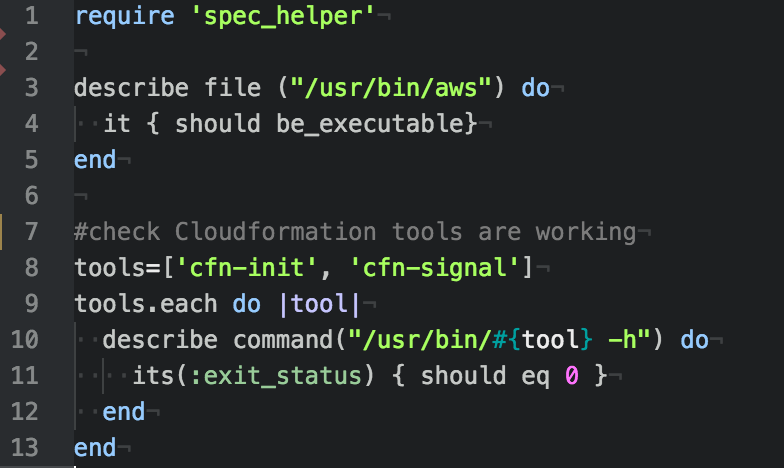
Tools: ServerSpec
Test suites meant to be run against machines

3) AWS Account isolation
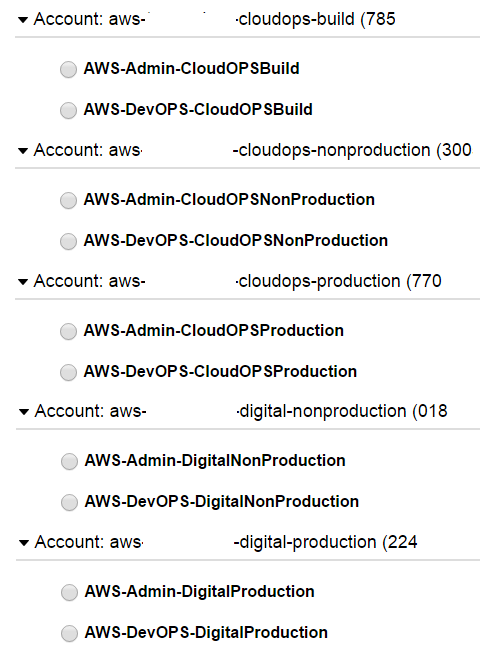
Seperate the business functions
into different accounts inside AWS.
- CloudOPS-Build for AMI/SOE
- CloudOPS for Management (Jenkins)
- Digital for Deployment
Seperate roles in each account to protect against stolen sessions!
Restrict functionality as required.
@dagrz loves popping AWS

4) VPC/Network Isolation
Cloudformation allows for the creation of new VPC and Subnets inside these VPCs easily.
Public subnets can be accessible from internet facing addresses
Private subnets can be accessible from public devices
Restricted can ONLY be accessed by private services with the correct security groups!
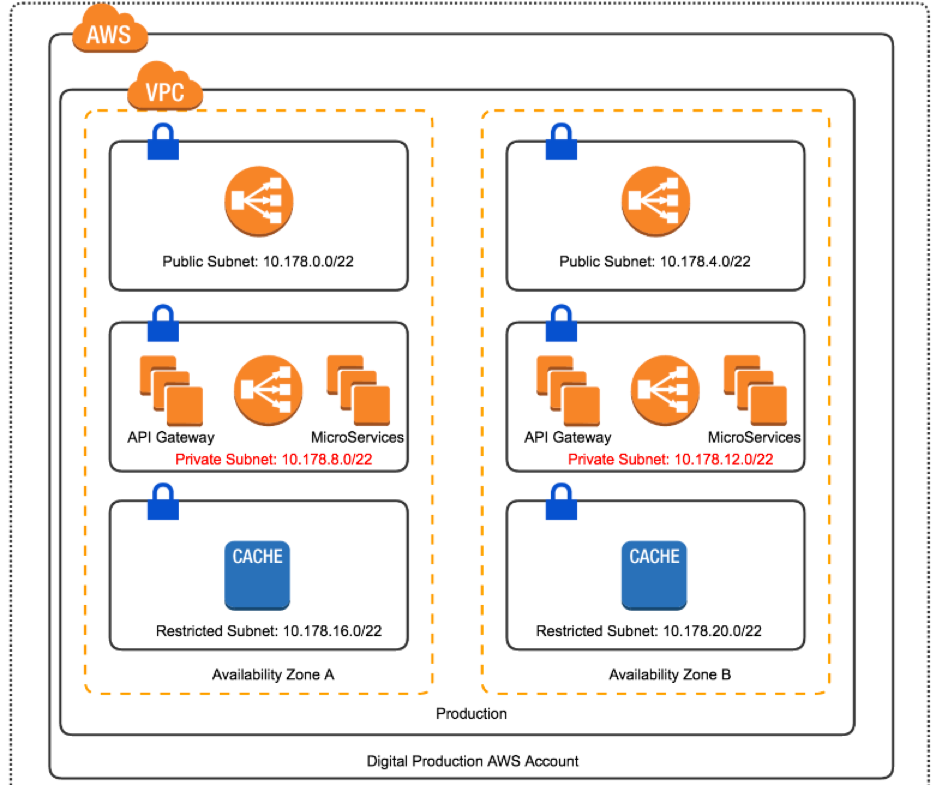

Preprod Production
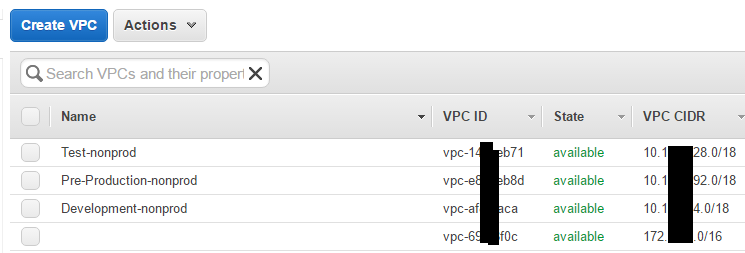
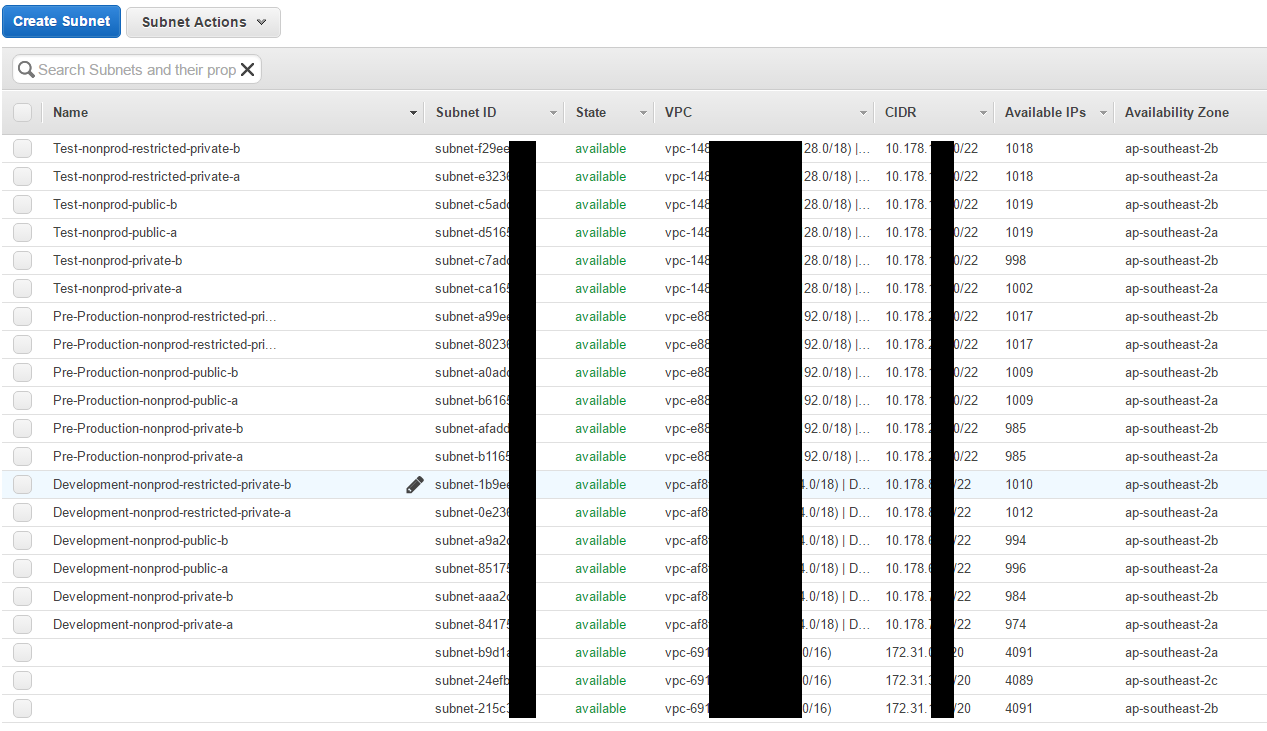
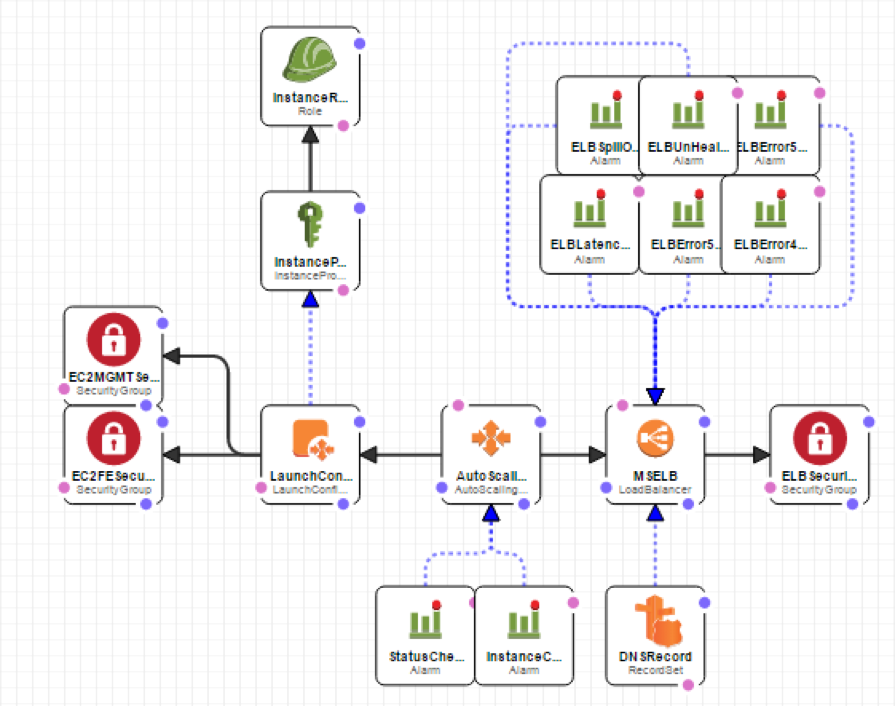
5) Immutable infrastructure
CloudFormation is my home boy
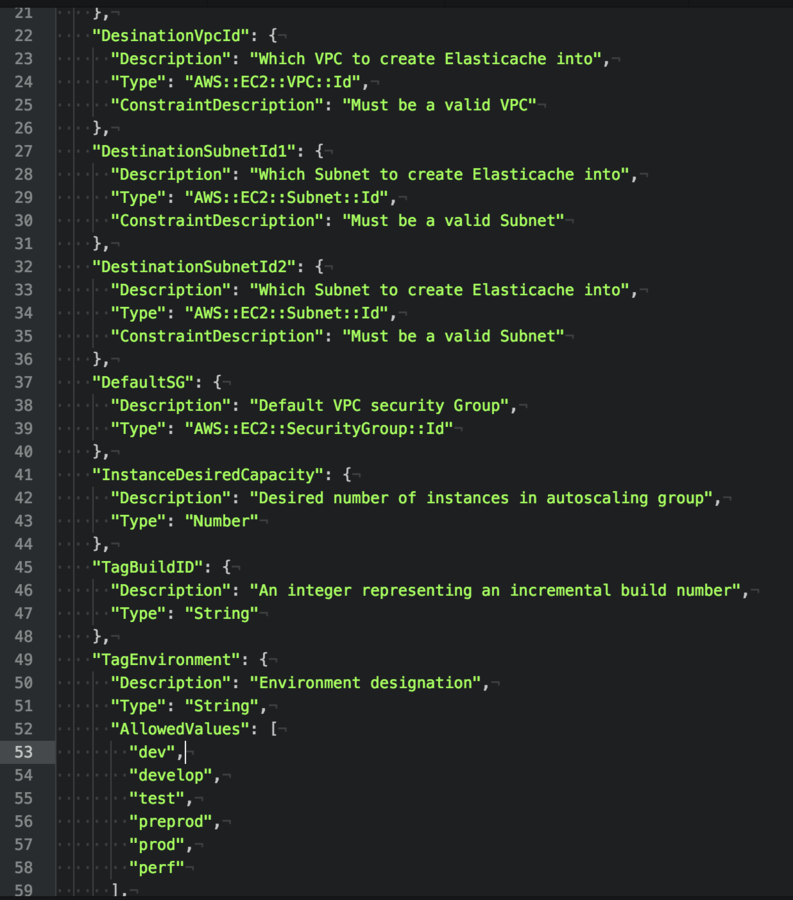
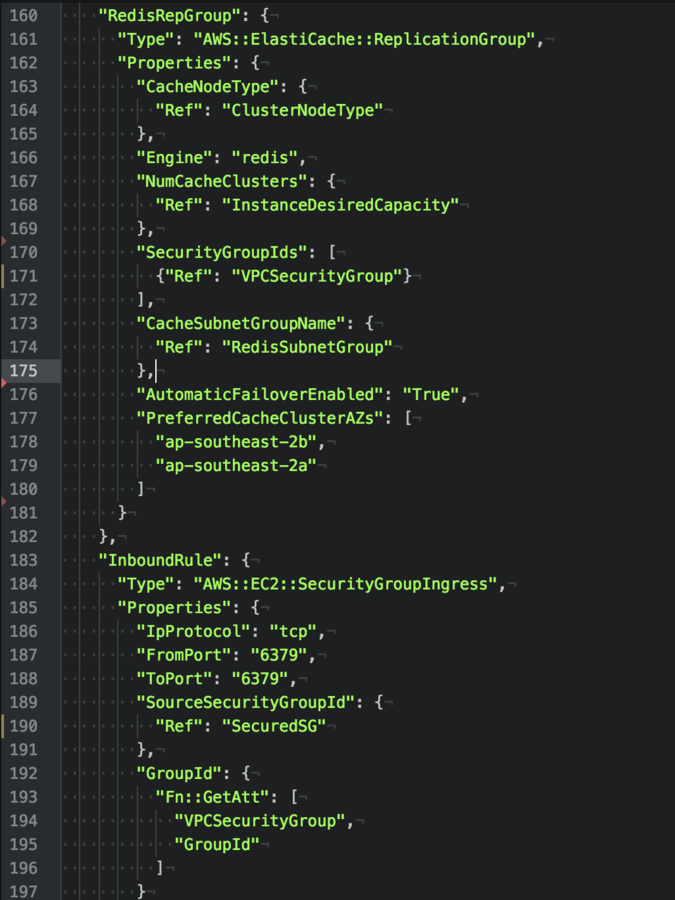
6) Jenkins: Low Hanging Fruit
I love Jenkins, but it's a
perfect place to get persistence.
Using Jenkins Job Builder, I've moved on Jenkins code into the infracode repository.
Jenkins is read only and all modifications must be completed during the GIT repo.
Pull Requests preferred! :D
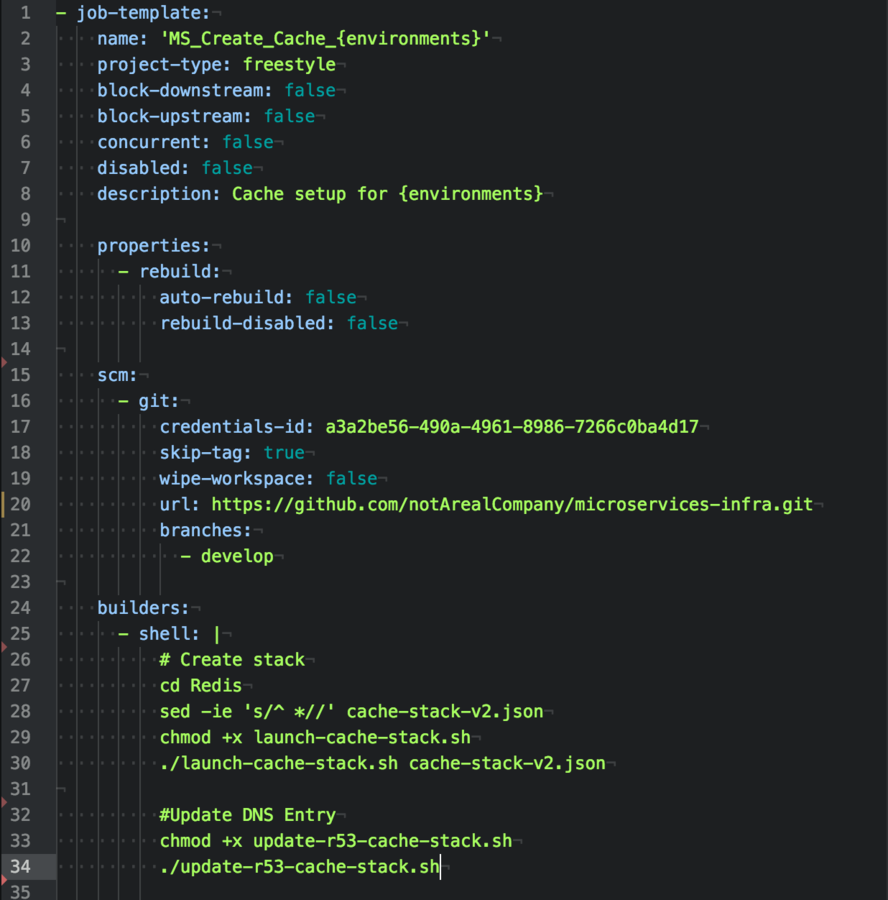
7) Untrusted Data and Docker
ImageTragick is an easy example of untrusted code running on production environments leading to RCE.


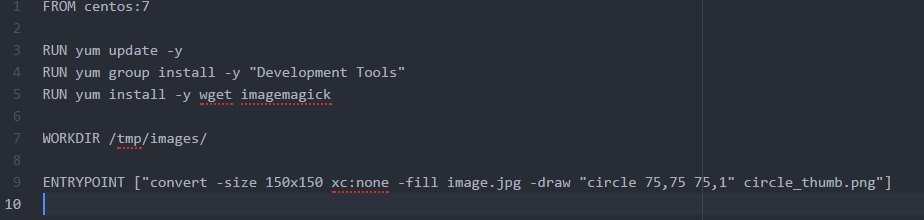
8) Secrets and AWS KMS Roles
KEEP YOUR PASSWORDS OUT OF THE SOURCE CONTROL FOR THE LOVE OF CHRIST! YOU GOD DAMN SAVAGES!
Tools: Credstash/Unicreds
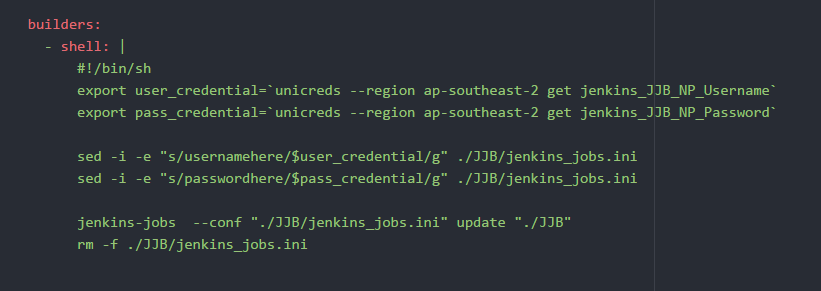
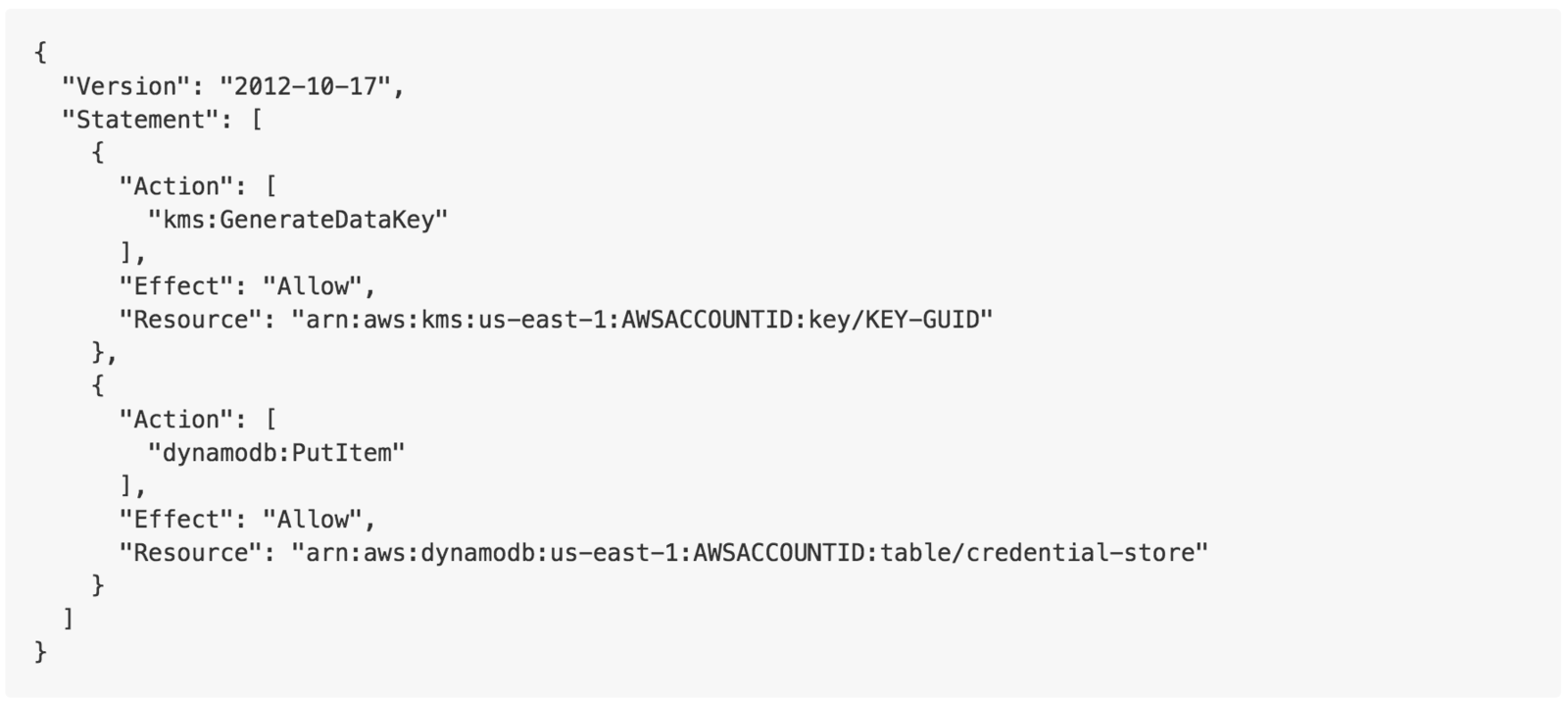
KMS and Credstore dynamodb
Limit write access to passwords
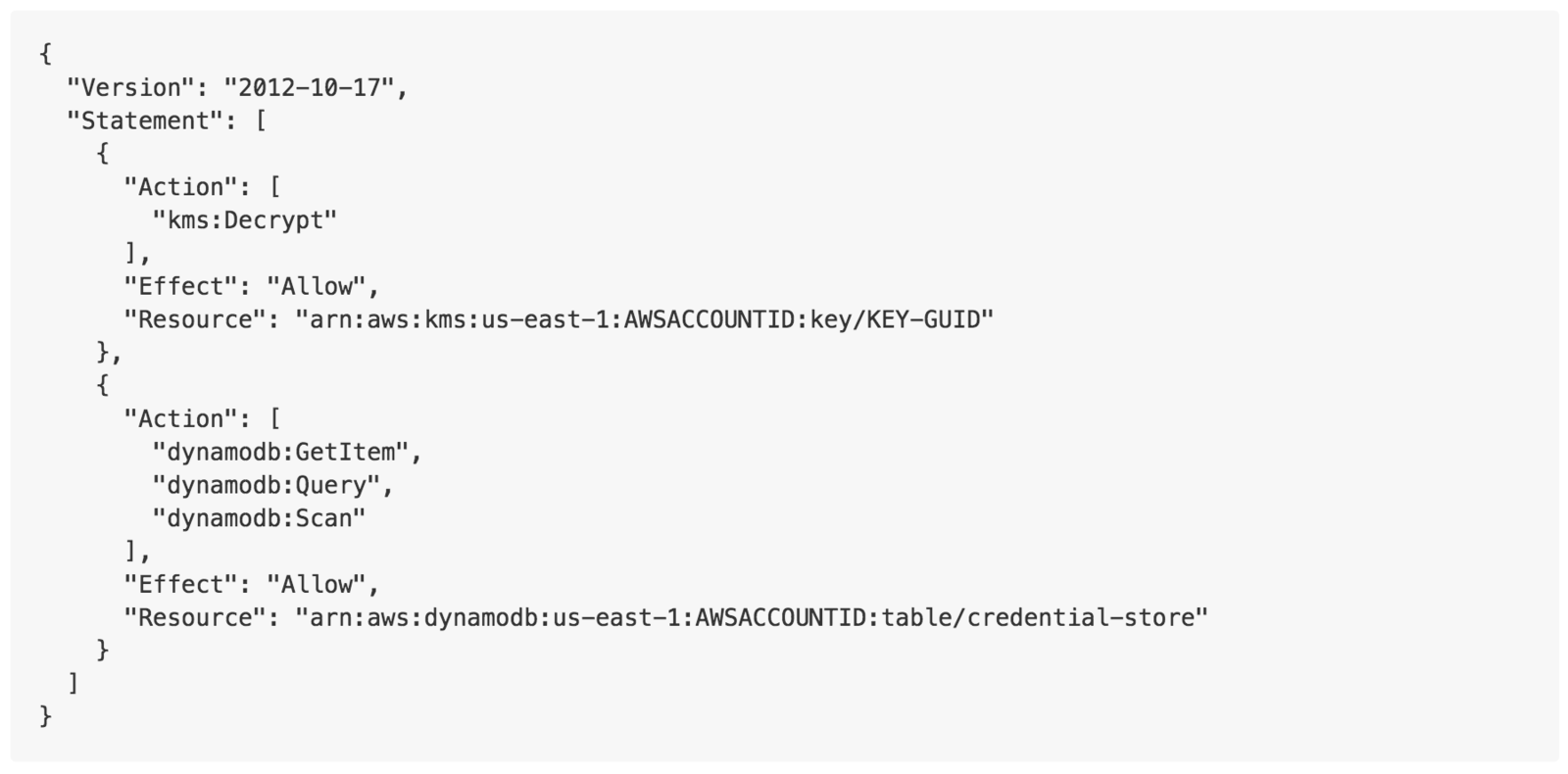
KMS and Credstore dynamodb
Limit read access to passwords
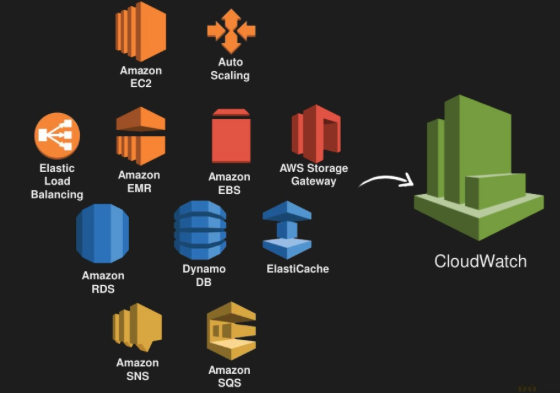
9) AWS Cloudwatch
PUT IT ALL IN THE LOGS!
10) CICD - Security scans
Gauntlt, mittn





Upright and proud
Thank you!
SecDevOps
By Shlee Paradiso
SecDevOps
- 1,296


