Angular
Security Culture

Stepan Suvorov
CTO @ Studytube

Masters in Information Security

Philippe de Ryck
Thank you for the inspiration!
XSS
XSS
Post Data with malicious code
Store
Fetch
Open App
Get malicious code
Check
DOM-based XSS
Follow link
Response
Make user to follow a link
var url = new URL(location.gref).searchParams.get("user");
$('#form').append('<input type="hidden" value="' + url + '">');<form id="#form">
<input type="hidden"
value="https://example.com"/><script>alert(1)</script>
</form>.../?user=something<script>alert(1)</script>...


XSS Defence
Sanitization
Content Security Policy
What does CSP do?
Inline code
API
CDN
Analytics
3rd party
Injected script
DOM Trusted Types
$('#form').append('...some STRING');el.innerHTML='...some STRING'
DOM Trusted Types
- Don't pass (HTML, URL, script URL) strings to the DOM
- Use object instead
- DOM already supports it:
- Web platform (or polyfill) provided typed objects:
- TrustedHTML
- TrustedScript
- TrustedURL
- TrustedScriptURL
- Security rules & controls are based on types
el.innerHTML = { toString: () => 'hello' }
el.innerHTML // "hello"Content-Security-Policy: trusted-types myPolicyel.innerHTML = location.hash.slice(1); //string//create via a TrustedTypes policy
el.innerHTML = aTrustedHTML;

Angular Trusted Types
Sanitization out of box:
- HTML
- Styles
- Url
- Resource Url
bypassSecurityTrust*
- Angular controls the data in the template
- Data is always escaped for the right context
- HTML-bound data is sanitized by Angular
CSRF

CSRF
login
action




bad action

done
done!
eBay : The password cannot be updated by using this method.


eBay CSRF Story


: However, the information that’s needed to reset the password can.

facebook CSRF
2019 reward
- Jan 26, 2019 — Report Sent
- Jan 26, 2019— Acknowledged by Facebook
- Jan 28, 2019 — More details sent
- Jan 31, 2019— Fixed by Facebook
- Feb 12, 2019 — 25K bounty Awarded by Facebook
What to do against CSRF?
CSRF Tokens
login
action




bad action

done
Token:





==

Token: ...
NO ACCESS!

!= ...


Angular CSRF
HttpClientXsrfModule.withOptions({
cookieName: 'My-Xsrf-Cookie',
headerName: 'My-Xsrf-Header'
}),
Dependencies
Do you know all your project dependencies?



event-stream v3.3.6

right9ctrl

event-stream v4.0.0

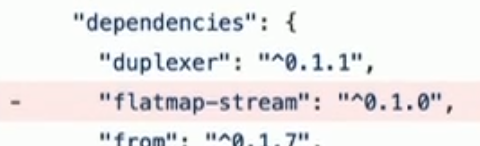
flatmap-stream v0.1.1

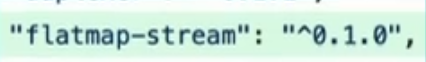
flatmap-stream v0.1.0
event-stream v3.3.5
flatmap-stream v0.1.1

require("crypto").decrypt("aes256", data, npm_package_description);copay-dash

if(!/build\:.*\-release/.test(process.arg[2])) return;npm run-script command
"build:ios-release": "run-s env:prod && ionic cordova build ios --release"inject malicious payload to steal private keys from wallet
flatmap-stream v0.1.1

45 days

event-stream
77 days
How it was found?
pure luck!
npm audit
npm install angularcli

@angular/cli


is looking for superstars!

Questions?
Angular Security Culture
By Stepan Suvorov
Angular Security Culture
- 2,162



