DevOps Plan of Attack
Prioritizing change in a DevOps context
Lansing DevOps Meetup
Sponsored by A2 Hosting
DevOps Plan of Attack
Prioritizing change in a DevOps context

Maslow's Hierarchy of Needs
https://www.simplypsychology.org/maslow.html
Development Needs
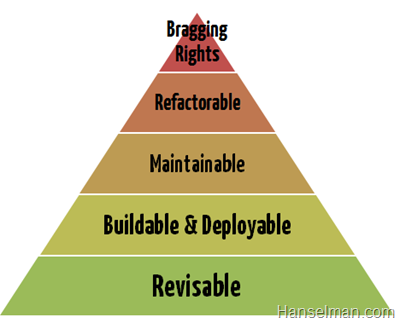
https://www.hanselman.com/blog/MaslowsHierarchyOfNeedsOfSoftwareDevelopment.aspx
Service Level Needs

https://landing.google.com/sre/book/chapters/part3.html
I. Codebase
One codebase tracked in revision control, many deploys
II. Dependencies
Explicitly declare and isolate dependencies
III. Config
Store config in the environment
IV. Backing services
Treat backing services as attached resources
V. Build, release, run
Strictly separate build and run stages
VI. Processes
Execute the app as one or more stateless processes
VII. Port binding
Export services via port binding
VIII. Concurrency
Scale out via the process model
IX. Disposability
Maximize robustness with fast startup and graceful shutdown
X. Dev/prod parity
Keep development, staging, and production as similar as possible
XI. Logs
Treat logs as event streams
XII. Admin processes
Run admin/management tasks as one-off processes
https://12factor.net/

Other Considerations
- Capabilities/Maturity
- Risks/Legal Responsibilities
- Tolerance/Flexibility
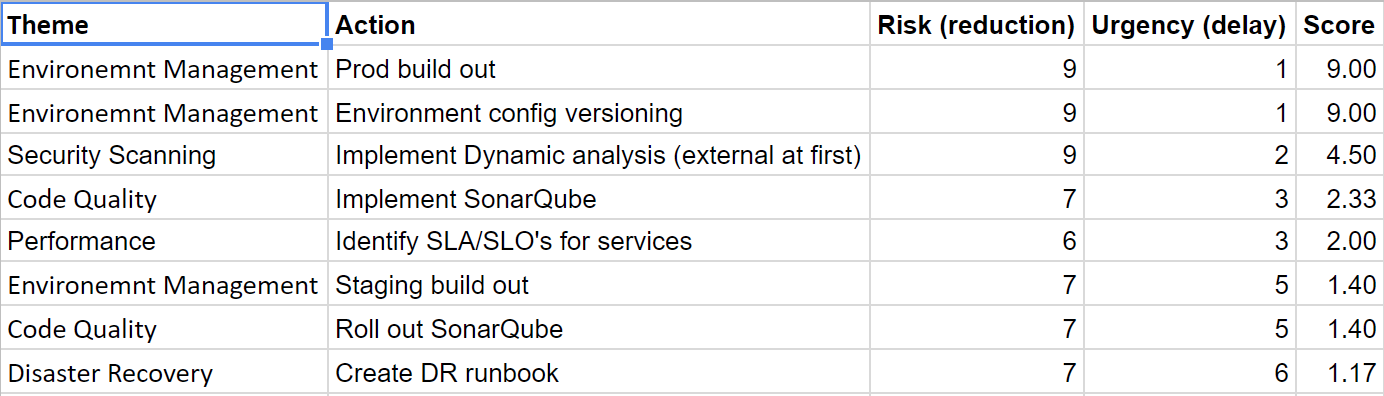
The Magic Formula
- Make a list of all the things to do
- Give each item a value of 1-10 for risk reduction
- Give each item a value of 1-10 for how much you can procrastinate (can you mitigate the risk?)
- Divide the first number by the second number
Ever Evolving
DevOps Plan of Attack
By Brendon Thiede
DevOps Plan of Attack
Prioritizing change in a DevOps context
- 319



