LocalRoot++
Making LocalRoot the Default
ICANN84 - Dublin, IE - 2025-10 V0.1
Disclaimers:
- Joint work with Wes Hardaker, David Conrad, Geoff Huston, Jim Reid, but input from many many others.

# PRESENTING CODE
A refresher on how resolution works...
Webserver
How do I reach
www.a-random-domain.net?
www.a-random-domain.net
# PRESENTING CODE
A refresher on how resolution works...
ISP Resolver
www.a-random-domain.net
Webserver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.a-random-domain.net?
www.a-random-domain.net
Webserver
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net
Webserver
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Resolver
Root
.net
1.1.1.1
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net?
www.a-random-domain.net
Webserver
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
.net
1.1.1.1
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net?
Ask ns1.foo.net, at 2.2.2.2
www.a-random-domain.net
Webserver
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
.net
1.1.1.1
ns1.foo.net
2.2.2.2
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net?
Ask ns1.foo.net, at 2.2.2.2
www.a-random-domain.net?
www.a-random-domain.net
Webserver
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
.net
1.1.1.1
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net?
Ask ns1.foo.net, at 2.2.2.2
www.a-random-domain.net is 193.151.173.16
www.a-random-domain.net
Webserver
ns1.foo.net
2.2.2.2
www.a-random-domain.net?
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Root
.net
1.1.1.1
www.a-random-domain.net?
Ask .net, at 1.1.1.1
www.a-random-domain.net?
Ask ns1.foo.net, at 2.2.2.2
Webpage please...
193.151.173.16
www.a-random-domain.net
Webserver
www.a-random-domain.net is 193.151.173.16
ns1.foo.net
2.2.2.2
www.a-random-domain.net?
ISP Resolver
How do I reach
www.a-random-domain.net?
# PRESENTING CODE
A refresher on how resolution works...
Webserver
www.example.com
ISP Resolver
How do I reach
www.example.com?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.com?
Webserver
www.example.com
ISP Resolver
How do I reach
www.example.com?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.com?
Ask .com, at 2.2.2.2
www.example.com
Webserver
ISP Resolver
How do I reach
www.example.com?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.com?
Ask .com, at 2.2.2.2
www.example.com
Webserver
ISP Resolver
How do I reach
www.example.com?

# PRESENTING CODE
A refresher on how resolution works...
Webserver
www.example.org
ISP Resolver
How do I reach
www.example.org?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.org?
Webserver
www.example.org
ISP Resolver
How do I reach
www.example.org?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.org?
Ask .org, at 3.3.3.3
www.example.org
Webserver
ISP Resolver
How do I reach
www.example.org?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.org?
Ask .org, at 3.3.3.3
www.example.org
Webserver
ISP Resolver
How do I reach
www.example.org?

# PRESENTING CODE
A refresher on how resolution works...
Webserver
www.example.ie
ISP Resolver
How do I reach
www.example.ie?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.ie?
www.example.ie
Webserver
ISP Resolver
How do I reach
www.example.ie?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.ie?
Ask .ie, at 3.3.3.3
www.example.ie
Webserver
ISP Resolver
How do I reach
www.example.ie?
# PRESENTING CODE
A refresher on how resolution works...
Root
www.example.ie?
Ask .ie, at 3.3.3.3
www.example.ie
Webserver
ISP Resolver
How do I reach
www.example.ie?


Wouldn't it be nice...

# CHAPTER 2
- Published in 2020, updates RFC7706 from 2015.
- Basically: Fetch the root zone and cache it.
- Benefits:
- Increased reliability
- Increased performance
- Improved privacy
- DoS Mitigation
# PRESENTING CODE
Benefits
- Increased performance
- If you don't need to send a packet, the RTT is zero
- If you don't need to send a packet, the RTT is zero
- Increased reliability
- If you don't need to reach the root, you don't need to be able to reach the root
- If you don't need to reach the root, you don't need to be able to reach the root
- Improved privacy
- www.alcoholics-anonymous.org
- www.alcoholics-anonymous.orf
- DoS Mitigation
- Enumeration attacks
Yes, I'm aware of RFC7816 - "DNS Query Name Minimisation to Improve Privacy" and RFC8198 - "Aggressive Use of DNSSEC-Validated Cache" (I'm an author)
# CHAPTER 2
How?

# CHAPTER 2
Getting the root zone
https://www.internic.net/domain/root.zone
# CHAPTER 2
How?

Fetching using curl / wget
$ wget https://www.internic.net/domain/root.zone
--2025-10-17 11:37:51-- https://www.internic.net/domain/root.zone
Resolving www.internic.net (www.internic.net)... 192.0.46.9
Connecting to www.internic.net (www.internic.net)|192.0.46.9|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2246592 (2.1M) [text/plain]
Saving to: ‘root.zone’
root.zone 100%[==============>] 2.14M 2.28MB/s in 0.9s
2025-10-17 11:37:53 (2.28 MB/s) - ‘root.zone’ saved [2246592/2246592]# PRESENTING CODE
Fetching using AXFR
$ dig axfr . @b.root-servers.net
; <<>> DiG 9.10.6 <<>> axfr . @b.root-servers.net
;; global options: +cmd
. 86400 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2025101700 1800 900 604800 86400
. 518400 IN NS a.root-servers.net.
. 518400 IN NS b.root-servers.net.
. 518400 IN NS c.root-servers.net.
. 518400 IN NS d.root-servers.net.
. 518400 IN NS e.root-servers.net.
. 518400 IN NS f.root-servers.net.
...
...
ns1zim.telone.co.zw. 172800 IN A 41.220.30.81
ns1zim.telone.co.zw. 172800 IN AAAA 2c0f:f758:0:a::81
ns2zim.telone.co.zw. 172800 IN A 41.220.30.82
ns2zim.telone.co.zw. 172800 IN AAAA 2c0f:f758:0:a::82
. 86400 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2025101700 1800 900 604800 86400
;; Query time: 172 msec
;; SERVER: 170.247.170.2#53(170.247.170.2)
;; WHEN: Fri Oct 17 11:30:52 EDT 2025
;; XFR size: 24904 records (messages 86, bytes 1422842)# PRESENTING CODE
Can fetch from: [b, c, d, f, g].root-servers.net
Fetching using AXFR
# PRESENTING CODE
Stats from b.root-servers.net
Gratuitous cat
# PRESENTING CODE

ISC BIND 9.14 (and above)
zone "." {
type mirror;
};# PRESENTING CODE
Example configuration using a BIND "mirror" zone:
root zone
Knot Resolver
modules.load('prefill')
prefill.config({
['.'] = {
url = 'https://www.internic.net/domain/root.zone',
interval = 86400 -- seconds
ca_file = '/etc/pki/tls/certs/ca-bundle.crt', -- optional
}
})# PRESENTING CODE
Source: Knot Resolver Cache prefilling
Example configuration to prefill cache with root zone using HTTPS:
HTTP(s)
Optional TLS
zone
Unbound 1.9 (and above)
auth-zone:
name: "."
url: "https://www.internic.net/domain/root.zone"
zonefile: "root.zone"
fallback-enabled: yes
for-downstream: no
for-upstream: yes
zonefile: "root.zone"
prefetch: yes
# PRESENTING CODE
Source: Unbound Authority Zone Options
Unbound Auth Zones example:
HTTP(s)
root zone
# PRESENTING CODE
So, how much data is this?!

sudo ipset destroy root_servers
sudo ipset -N root_servers iphash
sudo ipset -A root_servers 198.41.0.4
sudo ipset -A root_servers 170.247.170.2
...
sudo iptables -A INPUT -m set --match-set root_servers src -j ACCEPT
sudo unbound-control flush_zone .
sudo iptables -L -Z -v
[ Query each TLD]
sudo iptables -L -vv
sudo iptables -L -vvv
ip filter INPUT 8
[ match name set rev 4 ]
[ counter pkts 1537 bytes 1127567 ]
[ immediate reg 0 accept ]
Chain INPUT (policy ACCEPT 21512 packets, 5564K bytes)
pkts bytes target prot opt in out source destination
1537 1128K ACCEPT all -- any any anywhere anywhere match-set root_servers src
0 0 ACCEPT all -- any any anywhere anywhere match-set root_servers dst
# PRESENTING CODE
Individual queries
1.1MB
# PRESENTING CODE
AXFR
Bytes: 1,602,476 (2719 packets)
dig axfr . @b.root-servers.net
# PRESENTING CODE
HTTP
Bytes: 2,379,902
wget https://www.internic.net/domain/root.zoneBytes: 990,949
wget https://www.owl-stretching-time.com/root.zoneHTTPS
HTTPS with nginx - gzip
# PRESENTING CODE
CDNs - Content Delivery Network
- Specifically designed to distribute web objects
- Basically every webpage and video is served from a CDN
- Designed for high scalability, geographic distribution
- Examples:
- Akamai
- Amazon CloudFront
- Cloudflare
- Fastly
- Leaseweb, OVHcloud CDN, Tencent Cloud, etc.
# PRESENTING CODE
Trust...

# PRESENTING CODE
- "... an RR type that provides a cryptographic message digest of the data in a zone."
- Also known as "ZONEMD"
- DNSSEC signature over the entire zone file
$ dig zonemd .
; <<>> DiG 9.18.39-0ubuntu0.24.04.2-Ubuntu <<>> zonemd .
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9730
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;. IN ZONEMD
;; ANSWER SECTION:
. 86400 IN ZONEMD 2025102400 1 1 9679D824471ED710F3C6332217D1A70A96757F564DD83F7C12F4C886 BBB744A51168E86E1932D59524A14B10956759C6
;; Query time: 22 msec# PRESENTING CODE
1. promotes the behavior in [RFC8806] to be a Best Current Practice.
2. RECOMMENDS that resolver implementations provide a simple configuration option to enable or disable functionality, and
3. RECOMMENDS that resolver implementations enable this behavior by default, and
4. REQUIRES that [RFC8976] be used to validate the zone information before loading it.- Still needs text added on retries, fallback and fetching by IP...
Questions?

Backup slides
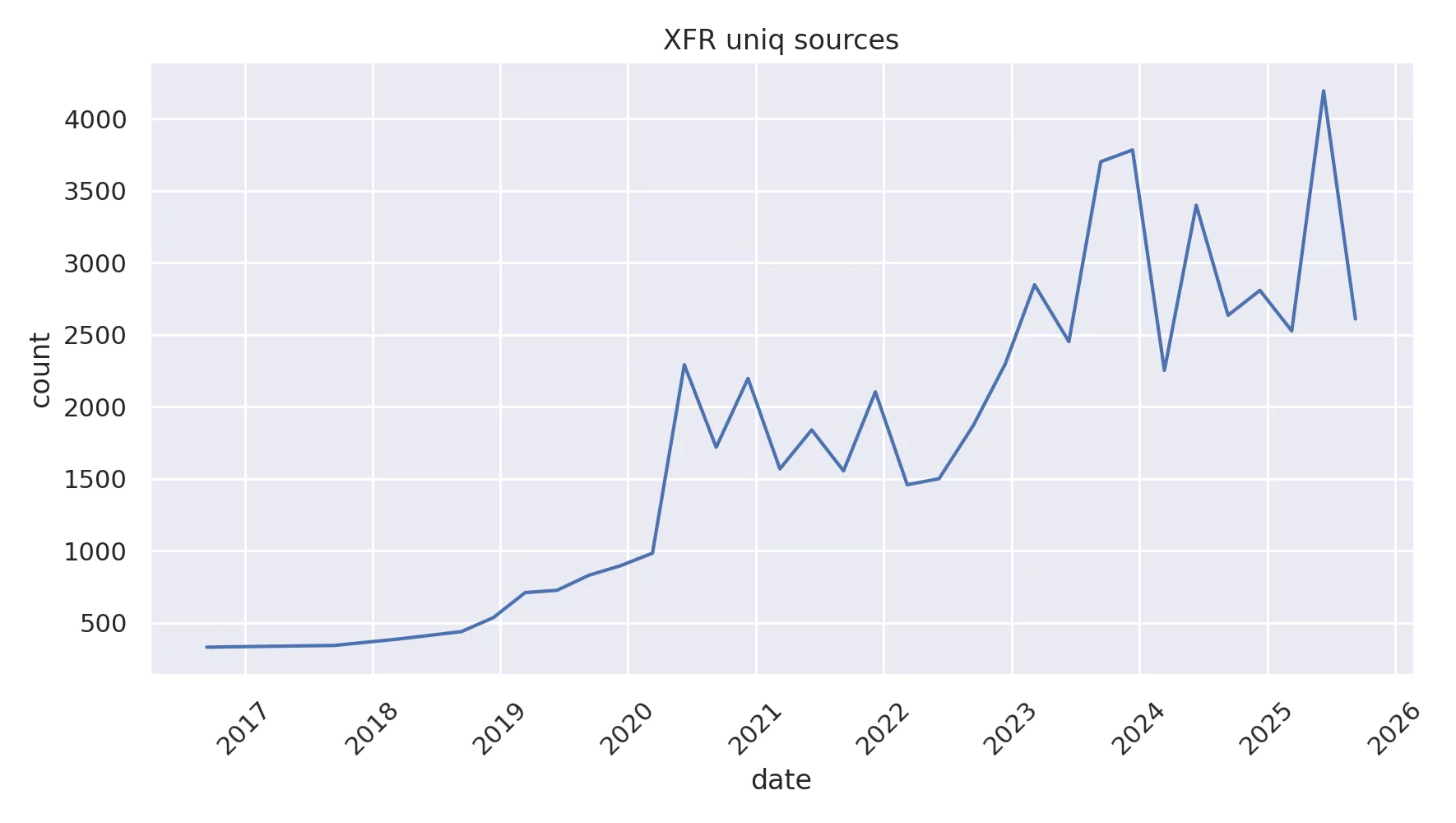
Capacity
- Comparison to current root-server system
- One CDN states 405Tbps
- Current RSS: 1999 instances (2025-10-19)
- That means each instance would need 202Gbps to match
Cloudflare
Capacity

DDoS Capacity

Source: KrebsOnSecurity
Aisuru
- 30 Tbps / 1998 instances =~ 15Gpbs / instance
Root Query
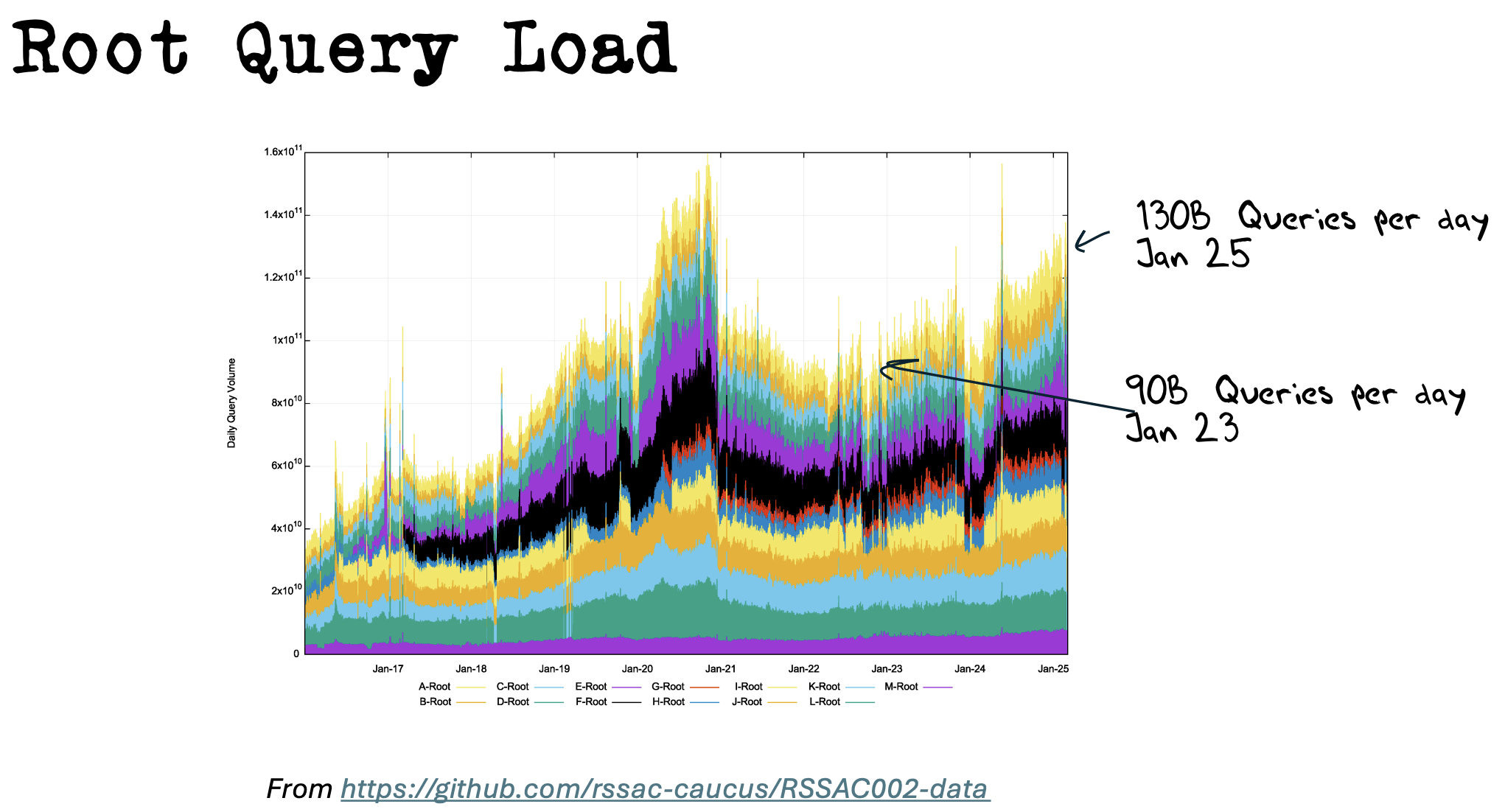
Capacity
Making LocalRoot Default
By wkumari



