Introducing and securing service meshes
with Istio and Kiali
@xeviknal
@kialiProject



Xavier Canal
@xeviknal
@kialiProject


Agenda
-
Why are we here?
-
Istio architecture
-
Istio concepts
-
Routing Features
-
Security features
-
Q&A
@xeviknal
@kialiProject

Monolith to Microservices


@xeviknal
@kialiProject

Microservices
@xeviknal
@kialiProject


Service Mesh
TO THE RESCUE
@xeviknal
@kialiProject

SERVICE MESH?
@xeviknal
@kialiProject

service mesh provides a transparent and language-independent way to flexibly and easily automate application network functions
Microservices to Service Mesh
@xeviknal
@kialiProject


HOW?
@xeviknal
@kialiProject


Istio features
- Load Balancing (HTTP, TCP, gRPC...)
- Traffic control (routing roules, retries, timeouts, fault injection, mirroring)
- Secure service-to-service communication
- Access controls (authorization)
- Metrics and traces for traffic
@xeviknal
@kialiProject

Istio objects
- Gateway
- Virtual Service
- Destination Rule
- Service Entry
- etc.
@xeviknal
@kialiProject

Gateway
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: mesh-arena-gateway
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "*"Expose Service Mesh to external traffic
VirtualService
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: ball-vs
spec:
hosts:
- ball
http:
- route:
- destination:
host: ball
subset: ball-v1Routing rules to apply when a host is addressed (match, rewrite, weight)
DestinationRule
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: ball-dr
spec:
host: ball
subsets:
- name: ball-v1
labels:
version: v1
- name: ball-v2
labels:
version: v2Policies defined for a service after routing has been defined (load balancing, circuit breaking)
Mesh Arena Demo
@xeviknal
@kialiProject


Football simulation, only AI players
Each item, one microservice
Let's build the match...
STEP by STEP
@xeviknal
@kialiProject

NEW SECURITY CONCERNS
NEW PARADIGM
@xeviknal
@kialiProject

Target discovery
@xeviknal
@kialiProject

Lots of services to protect
Services are dynamic
Multiple workloads per service

Few components to protect
Pieces are very well-known
Almost static architecture

Impersonation
@xeviknal
@kialiProject

One point per service
Higher network usage

Few points to impersonate

Data protection
@xeviknal
@kialiProject

Each service receives and sends data
Higher network usage

Few components to protect

Access Control
@xeviknal
@kialiProject

Each service has at least one endpoint
Consumers need to be identified
Multiple workloads to protect


Few public points
Consumers are unknown
Audit
@xeviknal
@kialiProject

Each service may have unauthorized access

Few access points to log

ISTIO
PROTECTING
THE SERVICE MESH
@xeviknal
@kialiProject

WITH
SECURITY BY DEFAULT
No changes needed for application code and infrastructure
@xeviknal
@kialiProject

DEFENSE IN DEPTH
Integrate with existing security systems to provide multiple layers of defense
@xeviknal
@kialiProject

ZERO-TRUST NETWORK
Build security solutions on untrusted networks
@xeviknal
@kialiProject

Auto-discovery
- Discover all the pieces you have to protect
- Almost real time discovery
- Detect unexpected connections between services
@xeviknal
@kialiProject

SERVICE MESH

Demo
Strong Identity
- Provide identity to each workload
- Necessary for:
- mTLS
- RBAC
- Secure naming
@xeviknal
@kialiProject

SPIFFE
- Secure Production Identity Framework For Everyone
- Creates a universal naming convention
- How to encode that name in a X.509 file (SVID)
- How a client validates a X.509 certificate to authenticate the SPIFFE identity
@xeviknal
@kialiProject

Strong Identity - how?
cat chain-example.pem | openssl x509 -noout -text
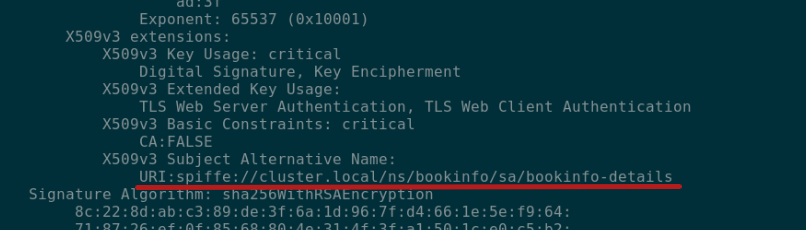

@xeviknal
@kialiProject

Mutual TLS Authentication
@xeviknal
@kialiProject

Are you who you say you are?
Mutual TLS Authentication
- Ensure both ends of communications are legit
- Encrypt service-to-service communications
- Envoy and Pilot involved (secure naming)
@xeviknal
@kialiProject


Demo
Enabling mTLS
apiVersion: "networking.istio.io/v1alpha3"
kind: "DestinationRule"
metadata:
name: "ball-enable-mtls"
spec:
host: ball
trafficPolicy:
tls:
mode: ISTIO_MUTUALAuthentication methods accepted on workload(s)
apiVersion: "authentication.istio.io/v1alpha1"
kind: "Policy"
metadata:
name: "default"
spec:
peers:
- mtls:
mode: PERMISSIVERules applied on client-side after routing
@xeviknal
@kialiProject

Policy
DestinationRule
@xeviknal
@kialiProject

Can ServiceA perform Action on ServiceB?
RBAC system
RBAC system
- Fine-grained access policy
- Consistent and homogeneous across the mesh
- Talks about services and versions
instead of pods, deployments - Strong identities needed
@xeviknal
@kialiProject


Demo
ServiceRole
apiVersion: "rbac.istio.io/v1alpha1"
kind: ServiceRole
metadata:
name: details-reviews-viewer
namespace: bookinfo
spec:
rules:
- services:
- "details.bookinfo.svc.cluster.local"
- "reviews.bookinfo.svc.cluster.local"
methods: ["GET"]
constraints:
- key: "destination.labels[version]"
values: ["v1"]
List of permissions:
- Object: Service
- Action: method + Path
@xeviknal
@kialiProject

ServiceRole
Binding
apiVersion: "rbac.istio.io/v1alpha1"
kind: ServiceRoleBinding
metadata:
name: bind-details-reviews
namespace: bookinfo
spec:
subjects:
- user: "cluster.local/ns/bookinfo/sa/bookinfo-productpage"
roleRef:
kind: ServiceRole
name: "details-reviews-viewer"List of subjects attached to a role:
- Authenticated SVC
- Authenticated end-user
@xeviknal
@kialiProject

Auditing
- Distributed traces
- Logging
@xeviknal
@kialiProject

THE SERVICE MESH

Demo
Useful Links
- Mesh Arena - github.com/jotak/demo-mesh-arena
- Slides - xavier.canal.cat/devopskathmandu
- Kiali links
@xeviknal
@kialiProject

THANKS
@xeviknal
@kialiProject



Introduction to Service Meshes with Istio and Kiali
By Xavier Canal Masjuan
Introduction to Service Meshes with Istio and Kiali
Industry is moving into microservices architectures from monolith ones. Hence, security concerns are changing due to this paradigm change. Let's see what Istio and Kiali provide to address those security issues.
- 42


