Null | OWASP
monthly meetup
12th August
Who Am I ?
Mohd Arif
Security enthusiast
Chapter leader of Null
Volunteer at OWASP chapter
Free time bug bounty hunter + VAPT
Twitter: @Zero0x00
Email: zero0x00@protonmail.com
Recon Techniques
for
bug hunters
&
pentester
Reconnaissance?
Recon (we look for)
- Any sensitive info any doc , meta data ,records
- credential like email ,pass , API keys
- info abouts domains , ip ranges
- Architecture
Domain co-relation
a
Horizontal
Vertical
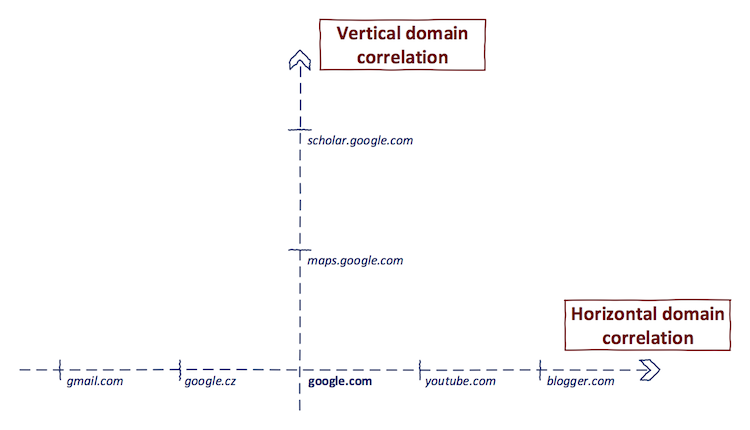
Finding Sub-Domain
Through search engine
- searching over google , bing ,online safari
- using advance operators for filtering
site: (vertical domain)
ip: (horizotal domain) if target is shared hosting
inurl:
Using 3rd party services
Virus total (run own passive DNS)
viewdns.info
pentest-tools.com
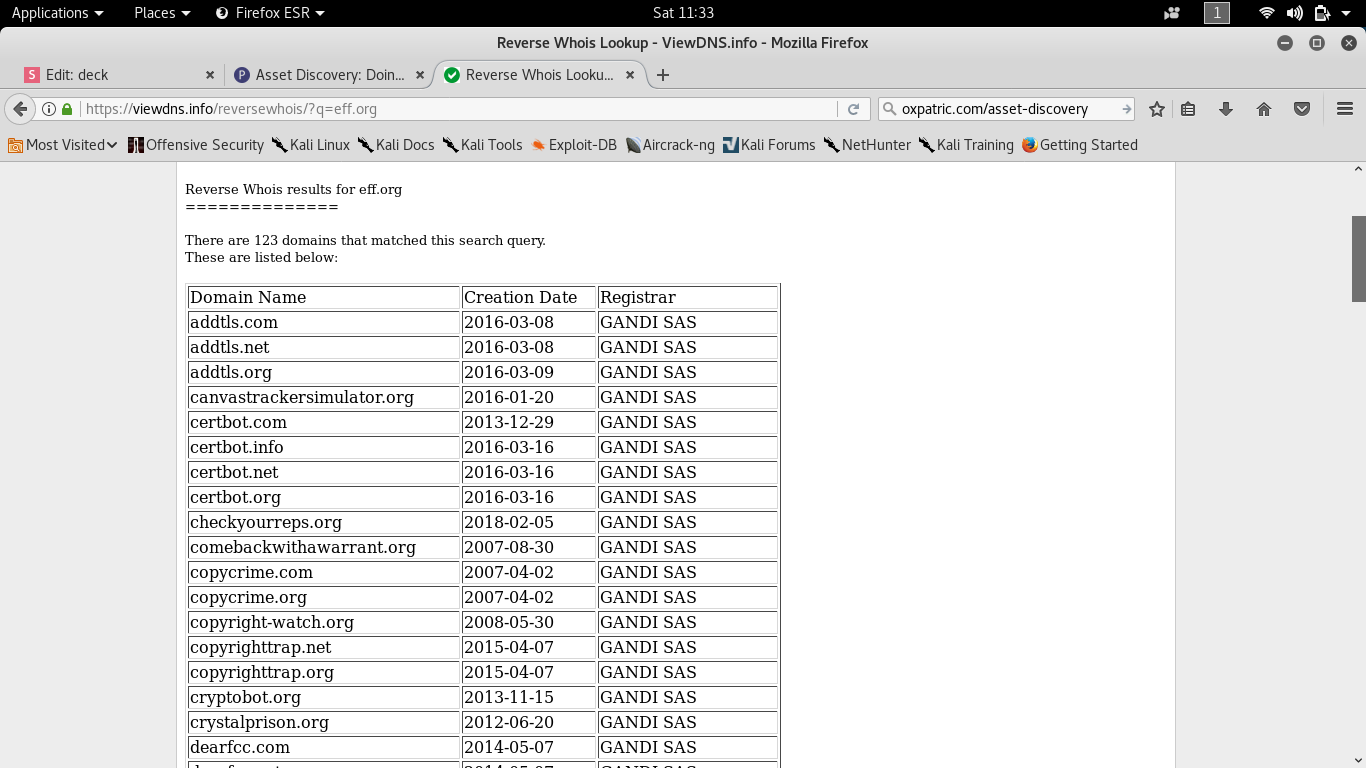
How helpful is Certificate Transparency
CT in short is meant to log, audit, and monitor certificates that Certificate Authorities (CA) issue
Any one can look through the CT logs ad find certificates issued for domain
An SSL/TLS certificate usually contains domain names, sub-domain names and email addresses. This makes them a treasure trove of information for attackers.
There are various search engines that collect the CT logs. We can easily search through them just like how we can Google anything.
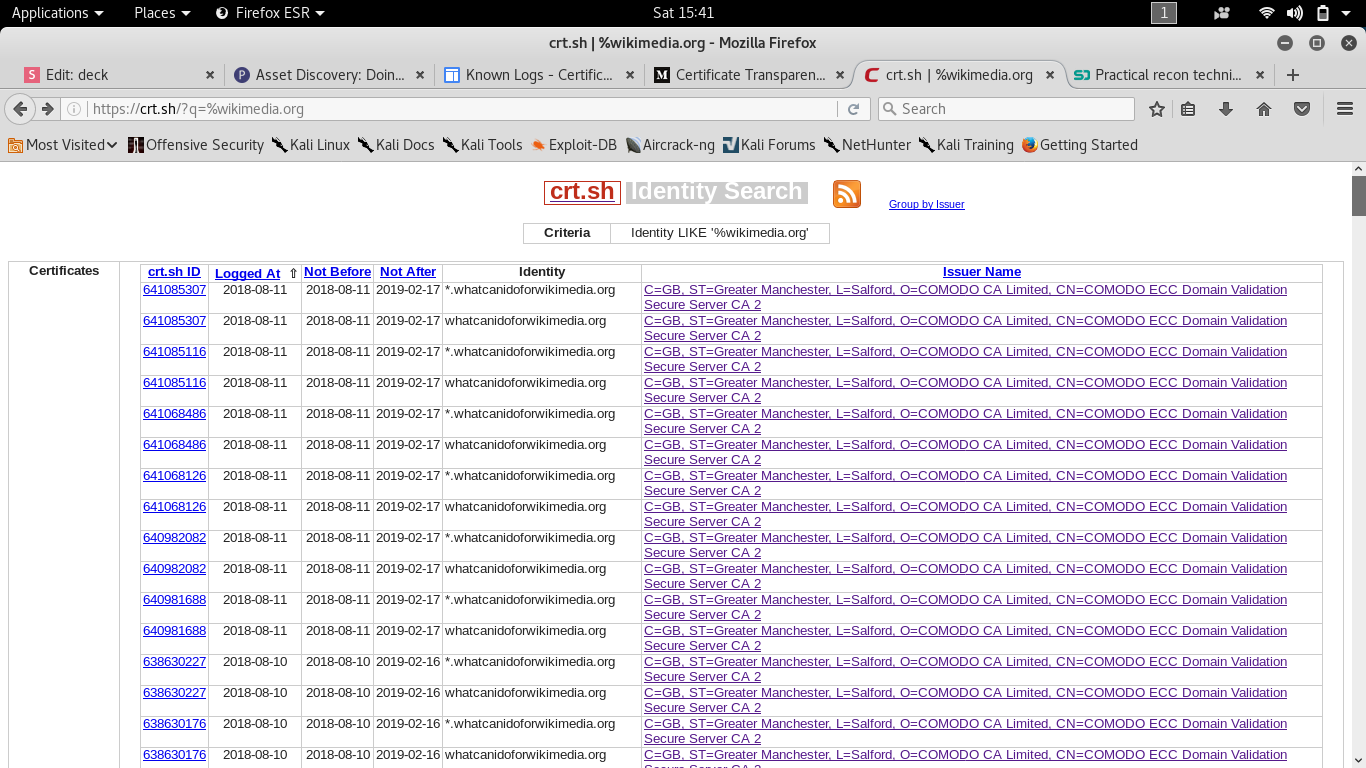
Bad side of CT
for
Recon
- Once it is up , there is no way to delete it
- At CT log the domain name found might be not exit any more but they can't be removed
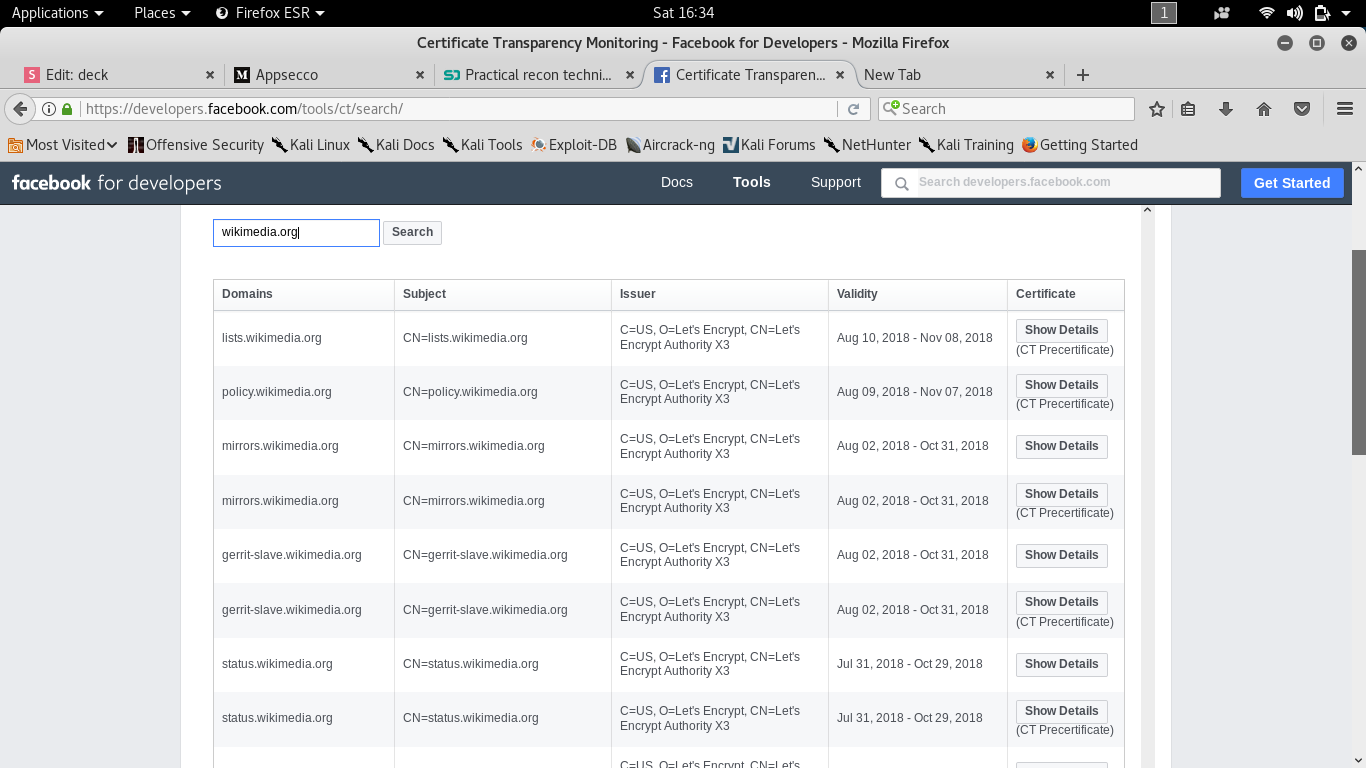
As we see these give some domain as non resolved
so we use CT log and massdns combine
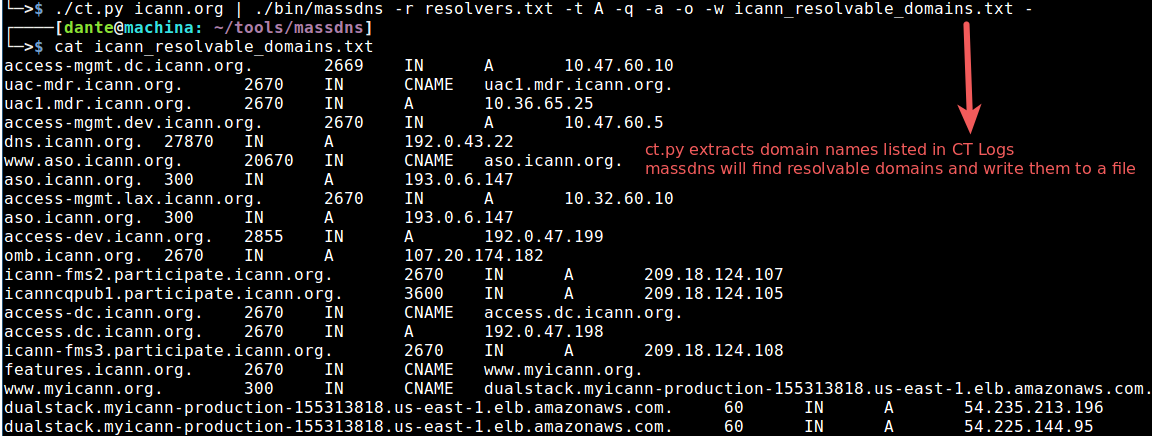
USING CETSPOTER
this service not only provide vertical but also give horizontal co-relation
CERTDB.COM
Certdb is based on the scanning the IPv4 segments,domain and "finding & analyzing" all the certificate
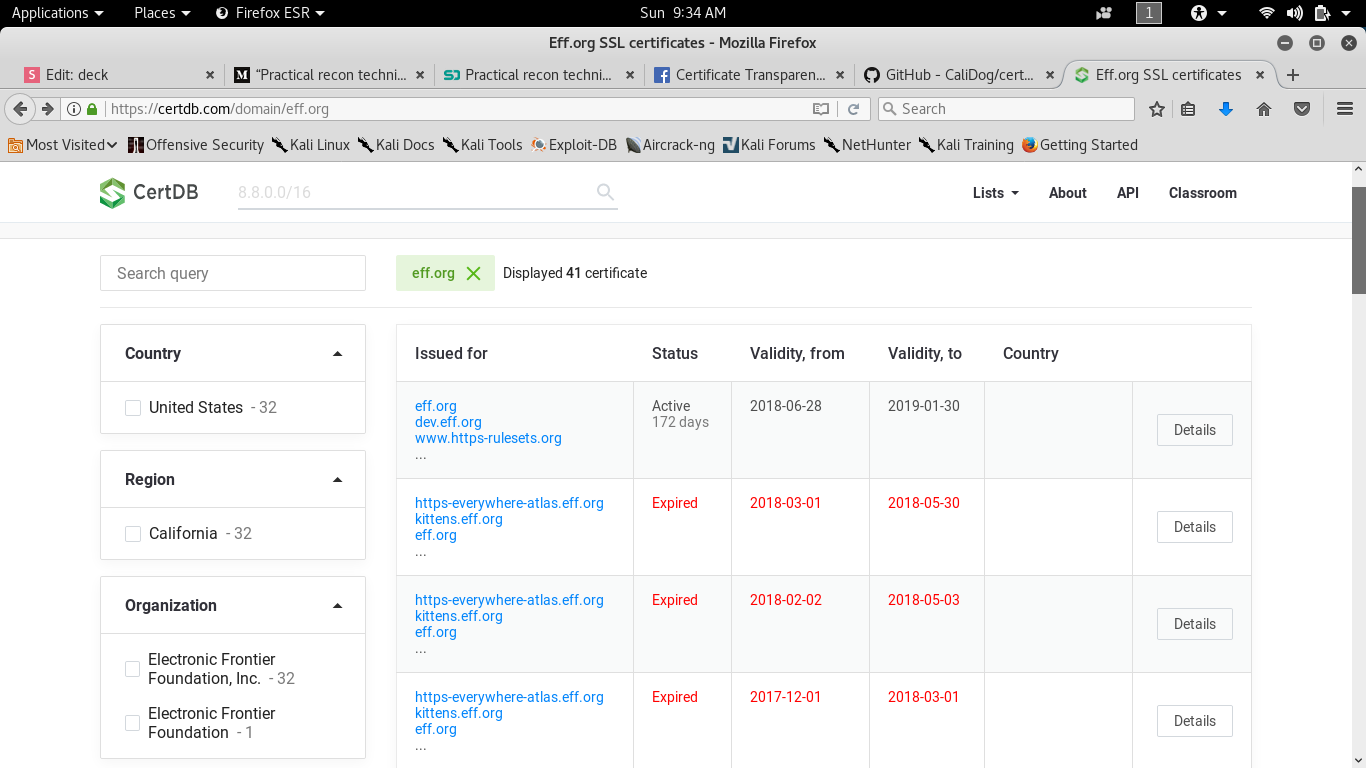
Text
Zone Transfer
dig @ns.example.com example=.com AXFR
The best practice advises administrators to allow AXFR requests only from authorized DNS servers, so the above technique will probably not work. But if it does, you have found a goldmine
Text
Text
Sublist3r
One of the most popular open source tools for subdomain enumeration, is called Sublist3r. It aggregates output from many different sources, including: google,crt.sh,virustotall etc
- It doesnot validate the give domain exit or not
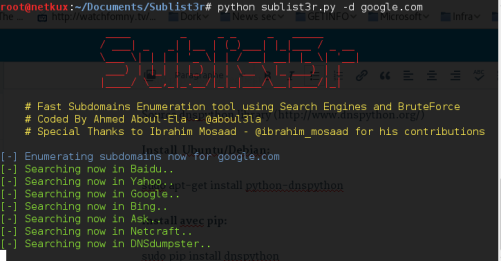
command-
python sublist3r.py -d example.com
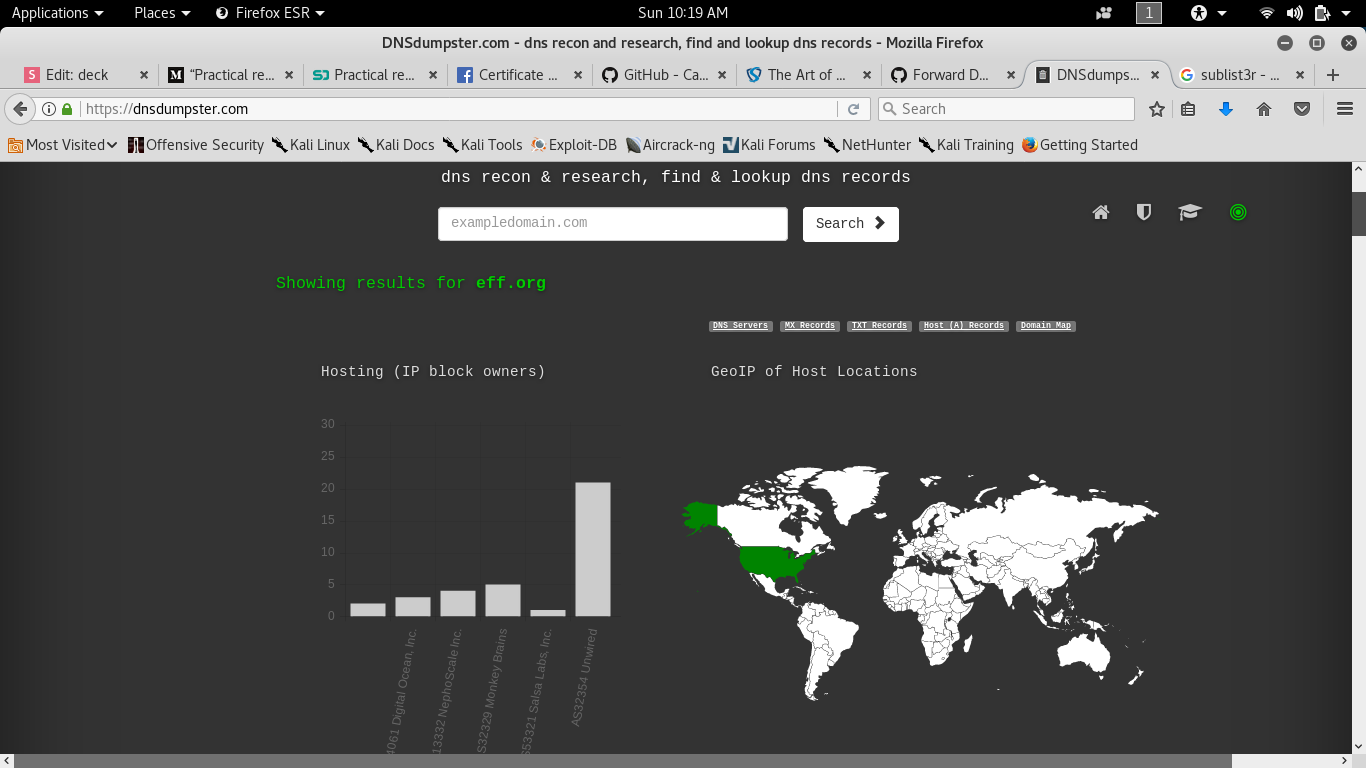
DNSDumpster
publicly provides its Forward DNS study/dataset on scans.io repository. The DNS dataset aims to discover all domains found on the Internet
Content Management System
searching Vulnerable cms
setting up cms like joomla , silverstripe , cushy etc there is a window of time where the installer has no form of authentication
- If you use HTTPS it will end up o CT log
- Attacker find such web application without authentication while searching through CT log , he can take over the server
This attack demo by Hanno Bock at defcon 25
CESYS.IO
- Same service as certdb
- SSL Certificate
- Good source of domain & email address

Cloud Storage
- AWS s3 bucket
- Digital ocen spaces
- It contains large amount of data , which probably any attacker want
- user store eve there password in plain txt on 3rd party services
Attacker search for open/publicly available s3 bucket
- each bucket get a unique URL
google dork
-site: s3.amazoaws.com file:pdf
we ca also do dictory based attack by tools like AwsBucket Dump ,Slurp
GITHUB
Popular VC (Version Control)
Code repo
Github section
+ Repo
+ code
+ Commits
+Issue
Look for
- API ad Keys
- Token
- Secret
- vulerable
- http://
Recon Techniques for bug hunters & pentester
By Mohd Arif
Recon Techniques for bug hunters & pentester
- 1,039



