Network Layer
Dr. Alexios Louridas
What are we going to see?
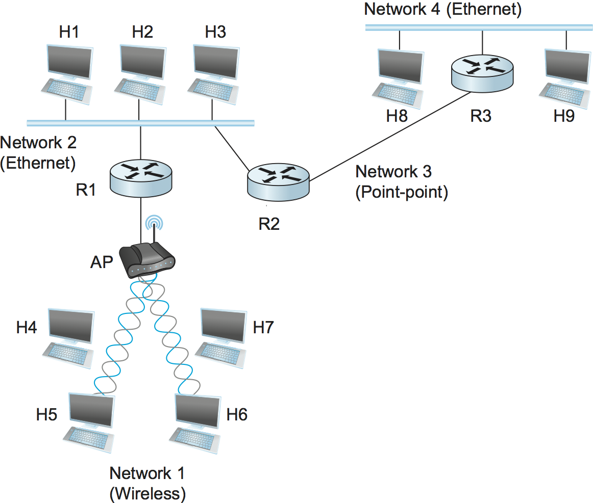
Internetworking
A collection of networks to provide data delivery of host-to-host.
H# are hosts
R# are routers
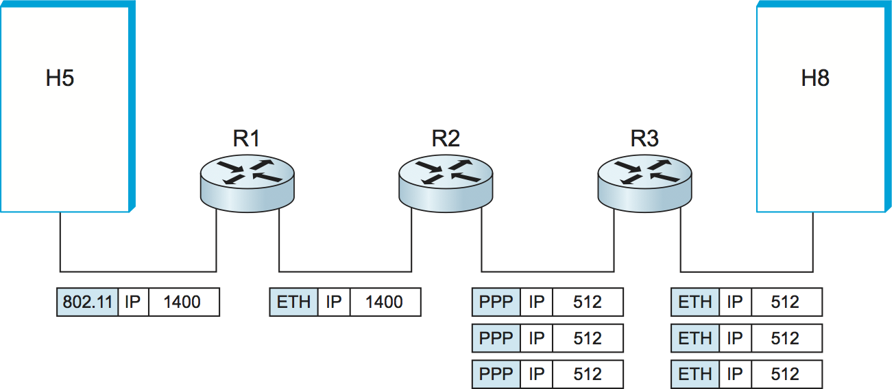
IP and Routing
Internet Protocol (IP)
Governs the transmission of data over the internet.
Responsible for Routing data packets.
-
Sender
-
Encapsulates segments into datagrams and sends them from the sending host to the receiving host
-
-
Receiver
-
Datagrams are delivered to the transport layer
-
-
Every host and router
-
Network layer protocols that operate at the network, data link, and physical layers
-
-
A router examines the header fields in all IP datagrams that pass through it
Network Layer
Encapsulation
Message
Message
Message
Message
H_t
H_t
H_t
H_n
H_n
H_l
segment
datagram
frame
-
Routing Protocols
-
RIP, OSPF, BGP
-
-
IP Protocol
-
Address
-
Datagram Format
-
Packet handling
-
-
ICMP Protocol
-
Error reports
-
Router Signals
-
-
Forwarding Table
Internet network Layer (disassembled)

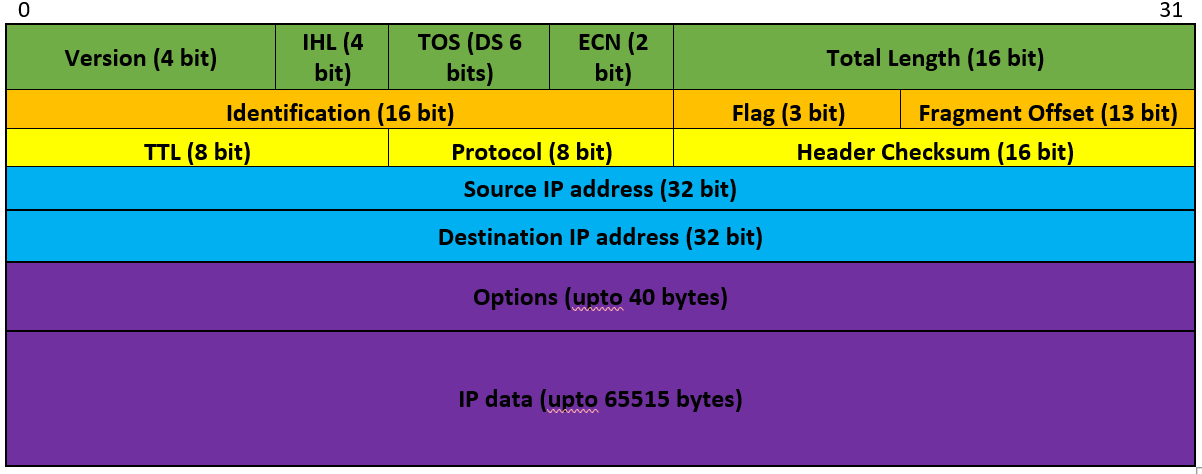
IP Datagram Format

Network layer
Forwarding
Connects one network to another network
Routing
Determines the best route to the destination before forwarding traffic to the next router along the path
Routers
Responsible for routing traffic between network
Efficient path
Routing table used to determine the most efficient path to reach the destination
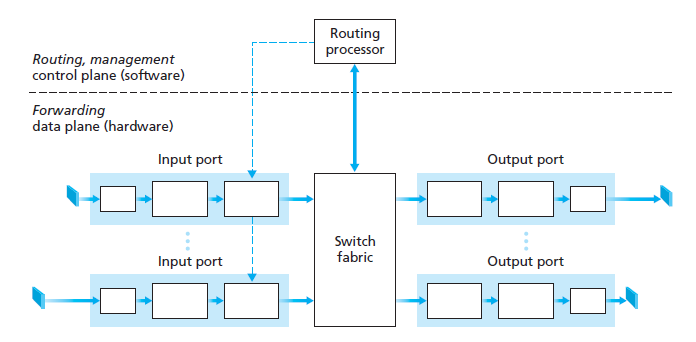
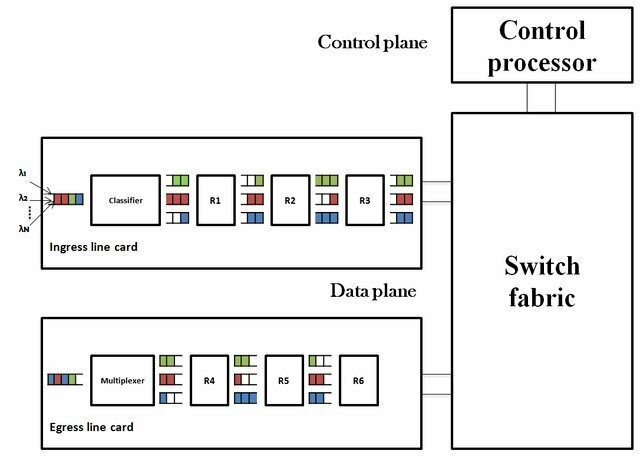

Router Architecture
datagrams journey
Buffering
Routers use buffers to temporarily store packets when the receiving interface is busy or congested. The buffer allows the router to hold onto packets until it can forward them to the next hop on the network. Without buffering, packets could be lost or dropped, resulting in data loss or network congestion.
Classifier
When a router receives a packet, it needs to determine which output interface to send the packet to. To make this determination, the router uses a classifier to examine the packet header and match it against predefined rules. The classifier can identify the source and destination addresses, protocol type, and other attributes of the packet to make the routing decision.
Scheduling
Once a router has classified a packet and determined the output interface, it needs to schedule the packet for transmission. The scheduling algorithm determines the order in which packets are sent, based on factors such as packet priority, available bandwidth, and network congestion. Scheduling algorithms can help ensure that high-priority packets are sent first, while still maintaining overall network performance
The concept of net neutrality is based on the idea that the internet should be an open and level playing field, where all users have equal access to information and online resources, regardless of their location, financial resources, or the type of device they use to access the internet.
If network neutrality is not enforced, ISPs could prioritize or block certain types of internet traffic, including specific websites, applications, or services. This could have significant implications for how routers function and how data is transmitted over the internet.
https://www.youtube.com/watch?v=fpbOEoRrHyU
https://worldpopulationreview.com/country-rankings/countries-without-net-neutrality
Network Neutrality
-
Buffering, classification, and scheduling
-
Help routers efficiently manage network traffic, ensure data integrity, and optimize network performance.
-
-
Throughput
-
Maximising throughput within the whole network.
-
-
Delay
-
Minimizing the mean packet to send traffic through the network effectively.
-
Routing

-
Routing decisions are done on the fly
-
Routing reflect changes in the topology, and sometimes changes in the traffic as well.
-
Also called Dynamic Routing
Adaptive
-
Routing decisions happens offline
-
Routing is preloaded in router before the network is booted
-
Also called Static Routing
Non-Adaptive
Routing algorithms
-
Routers know physically connected neighbours, link costs to neighbours
-
Iterative process of computation, exchange of info with neighbours
-
Bellman-Ford - Routing Information Protocol (RIP)
distance Vector
-
All router have complete topology, link cost information.
-
Open Shortest Path First (OSPF)
link-state
Routing algorithms for internet
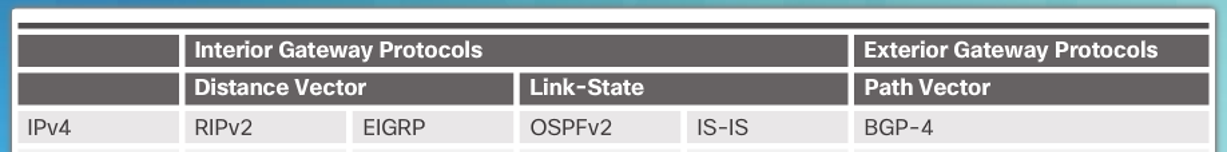
Dynamic Routing Protocol Overview
RIP protocol was updated to RIPv2 to accommodate growth in the network environment
RIPv2 does not scale to current larger network implementations
Routing Protocols developed to meet the need of larger networks include:
Open Shortest Path First (OSPF)
Intermediate System-to-Intermediate System (IS-IS).
Enhanced IGRP (EIGRP)
Border Gateway Protocol (BGP) is used between Internet service providers (ISPs)
-
Each node constructs a one-dimensional array (a vector) containing the "distances" (costs) to all other nodes and distributes that vector to its immediate neighbours.
-
The starting assumption for distance-vector routing is that each node knows the cost of the link to each of its directly connected neighbours.
-
These costs may be provided when the router is configured by a network manager. A link that is down is assigned an infinite cost.
RIP (Routing Information Protocol)
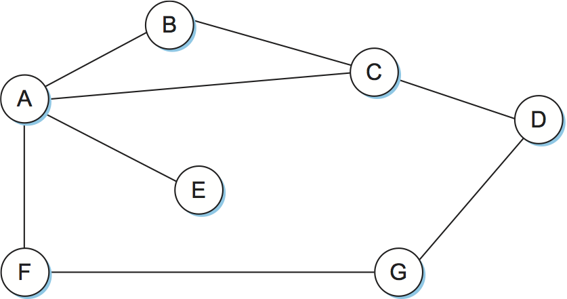
-
Routers send their advertisements every 30 seconds;
-
A router also sends an update message whenever an update from another router causes it to change its routing table.
-
One point of interest is that it supports multiple address families, not just IP. RIP version 2 (RIPv2) also introduced the subnet masks, whereas RIP version 1 worked with the old classful addresses of IP.
-
All link costs are equal to 1, just as in our example. Thus, it always tries to find the minimum hop route. Valid distances are 1 through 15, with 16 representing infinity. This also limits RIP to running on fairly small networks—those with no paths longer than 15 hops.
RIP (Routing Information Protocol)

-
Starting Assumptions
-
Each node is assumed to be capable of finding out the state of the link to its neighbours and the cost of each link.
-
-
Aim
-
Each node to know the least-cost path to any destination.
-
-
Mechanism 1
-
A solid and reliable way to provide link-state information to all nodes in the network.
-
-
Mechanism 2
-
To be able to calculate the routes from the sum of all the accumulated link-state knowledge.
-
OUR SERVICES
Reliable Flooding
Store most recent LSP from each node
Forward LSP to all nodes but one that sent it
Generate new LSP periodically (timer); increment SEQNO
Start SEQNO at 0 when reboot
Decrement TTL of each stored LSP; discard when TTL=0
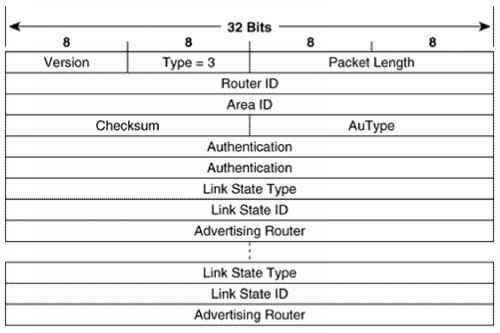
Link State Routing (Routing Table)
Link State Packet (LSP)
ID of the node that created the LSP
Cost of link to each directly connected neighbour
Sequence number (SEQNO)
Time-to-live (TTL) for this packet
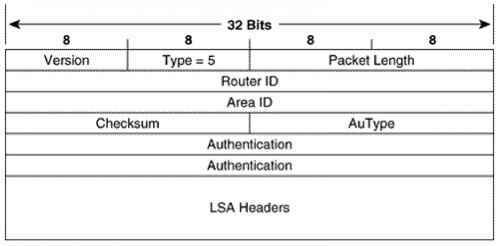
Link State Request Packet
Link State Acknowledgement Packet
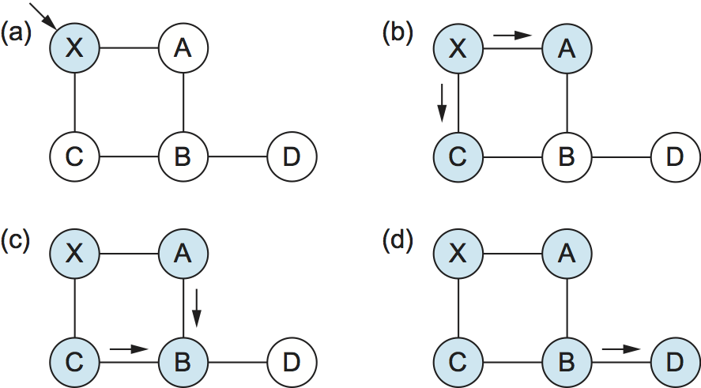
Reliable Flooding
Flooding of link-state packets.
(a) LSP arrives at node X;
(b) X floods LSP to A and C;
(c) A and C flood LSP to B (but not X);
(d) flooding is complete
| Step | Confirmed | Tentative | Comments |
|---|---|---|---|
| 1 | (D,0,--) | Since D is the only new member of the confirmed list, look at its LSP. | |
| 2 | (D,0,--) | (B,11,B) (C,2,C) | D's LSP says we can reach B through B at cost 11, which is better than anything else on either list, so put it on Tentative list; same for C. |
| 3 | (D,0,--) (C,2,C) | (B,11,B) | Put lowest-cost member of Tentative (C) onto Confirmed list. Next, examine LSP of newly confirmed member (C). |
| 4 | (D,0,--) (C,2,C) | (B,5,C) (A,12,C) | Cost to reach B through C is 5, so replace (B,11,B). C's LSP tells us that we can reach A at cost 12. |
| 5 | (D,0,--) (C,2,C) (B,5,C) | (A,12,C) | Move lowest-cost member of Tentative (B) to Confirmed, then look at its LSP. |
| 6 | (D,0,--) (C,2,C) (B,5,C) | (A,10,C) | Since we can reach A at cost 5 through B, replace the Tentative entry. |
| 7 | (D,0,--) (C,2,C) (B,5,C) (A,10,C) | Move lowest-cost member of Tentative (A) to Confirmed, and we are all done. |
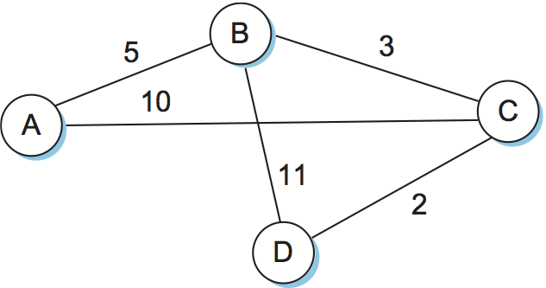
Example of Building a route table for Link State Routing
Authentication of Routing Messages
Open Shortest Path First Protocol (OSPF)
Additional Hierarchy
Load Balancing
Multiple Cost Metrics
Send information from one node to many other nodes, and the entire network can thus be impacted by bad information from one node. For this reason authenticating routing messages has become very important.
OSPF introduces another layer of hierarchy into routing by allowing a domain to be partitioned into areas. A router within a domain only needs to know how to get to the right area reducing the amount of information in the routing table.
Allows multiple routes to the same place to be assigned the same cost and will cause traffic to be distributed evenly over those routes, thus making better use of the available network throughput.
For each link, multiple cost metrics for different Types of Services (ToS) (e.g., satellite link cost (more delay involved) set low for best effort ToS; high for real-time ToS)

Summary - Comparison
-
Message Complexity
-
Link State Algorithms sent O(nE) messages.
-
Distance Vector Algorithms exchange messages only to neighbours.
-
-
Convergence
- Link State Algorithms may have some oscillations.
- Distance Vector Algorithms may have routing loops and count-to-infinity problem.
-
Link Failures in Link State Algorithms
-
Node can advertise incorrect link cost.
-
Each node computes only its own table.
-
-
Link Failures in Distance Vector Algorithms
-
Can advertise incorrect path cost.
-
Each node’s table used by others so error propagates through the network.
-
Network Layer
By Alexios Louridas
Network Layer
- 81


