Securing Trino data Access
- Authorize service access with JWT
- External centralizaed authorization service
- JWT generation requires OTP
Goals/Requirements
- Client application should not change the database driver, only credentials change
- Client application should authenticate OTP to generate token
Goals/Requirements
Solution parts
- Trino proxy server
- Authorization service for token generation/validation
- OTP generator client (embedded in application)
- Log/Event collector
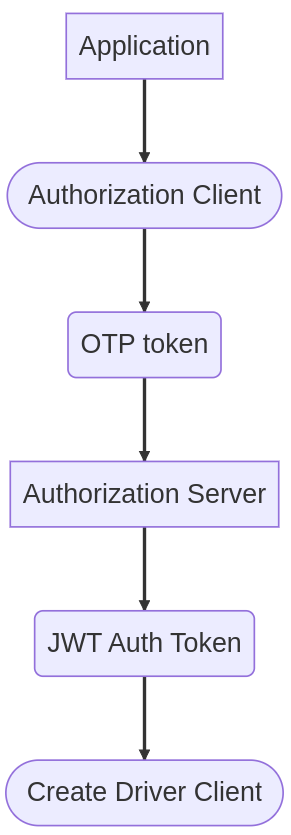
Trino Proxy Server
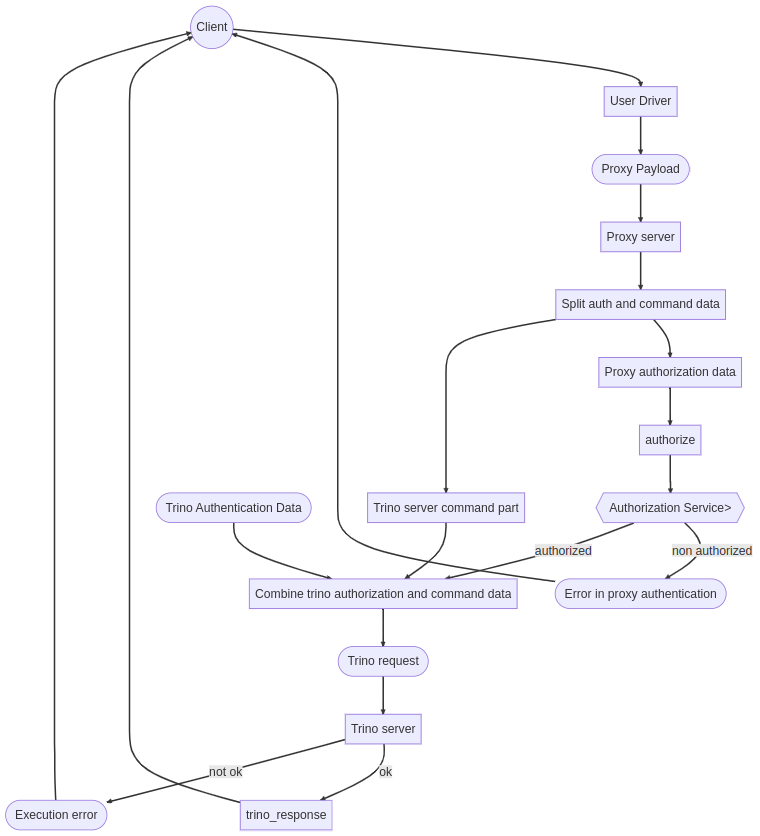
Request to execution flow consists of decoding user data, validating and encoding with new credentials.
Data exports
Each proxy request generate an event, exported for event server
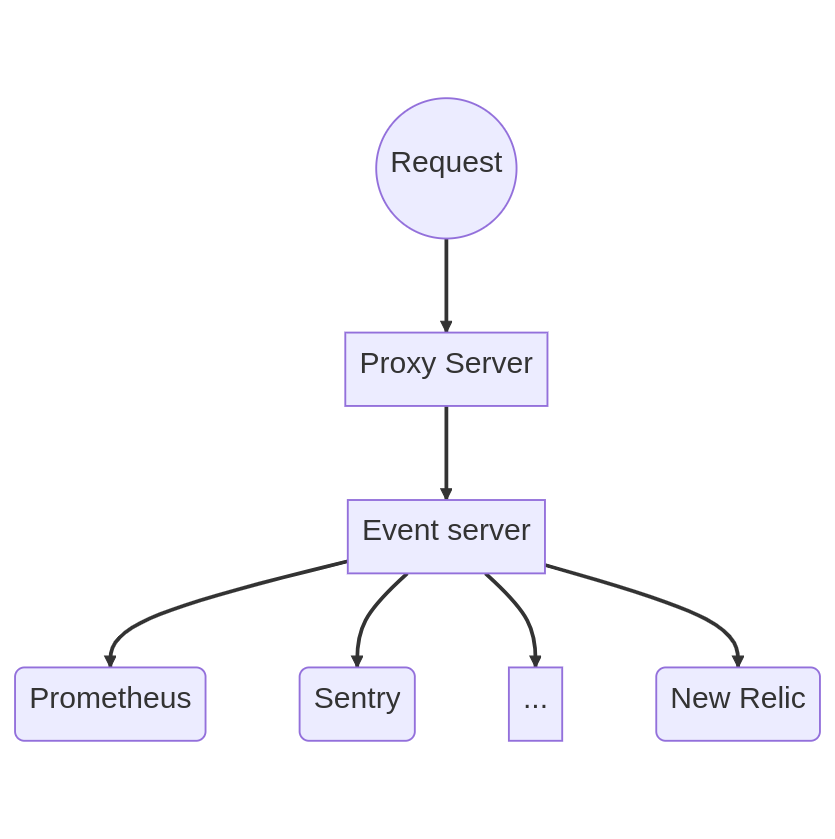



Event server can persist or export to one of many monitoring services
Bonus
ML fraud detector
Fraud Detector
Metrics from event server are feed into fraud detector service, a ML service for risk management and notification.
Lessons Plan
1. Auth
- Create authorization service
- Create a rust OTP generator client
- Create generator client binds for Python and JS
2. Event server
- GRPC server to receive events
- Persist events on database
- Create exporters plugin engine
- Create prometheus exporter
- Create new relic exporter
- Create sentry exporter
3. Proxy Server #1
- Proxy TCP server
- Safe concurrency patterns
- Decode and reconstruct request data
- Check authorization
- Run on trino and return
3. Proxy server #2
- Integrate with event server
- Integrate to Fraud Detection service
4. Proxy server #3
- Parent worker arquitecture
- Ditribute execution over workers
Securing data Acess for Trino with a Proxy
By André Claudino
Securing data Acess for Trino with a Proxy
- 77



