NASA Lab -
ARP Spoofing
by Arvin Liu
Recap - ARP
Task: 87 msg to 88
140.112.31.87
140.112.31.88
Switch cannot look ip.
So we needs 88's MAC to let switch forward.
src: 140.112.31.87
dst: 140.112.31.88
dst MAC: ???
87:87:87:87:87:87
88:88:88:88:88:88
<3
ARP Request & Reply
140.112.31.87
140.112.31.88
ARP Request
who has 140.112.31.88 ?
87:87:87:87:87:87
88:88:88:88:88:88
ARP Reply
140.112.31.88 is at
88:88:88:88:88:88
src ip: 140.112.31.87 src MAC: 87:87:87:87:87:87
dst ip: 140.112.31.88 dst MAC: 88:88:88:88:88:88

ARP Spoofing
ARP Spoofing
140.112.31.87
140.112.31.88
I know 140.112.31.88 => 88:88:88:88:88:88
87:87:87:87:87:87
88:88:88:88:88:88
ARP Reply
140.112.31.88 is at 89:89:89:89:89:89

140.112.31.89
89:89:89:89:89:89
89:89:89:89:89:89
What can ARP Spoofing do?
-
Spoofing only one side
- DoS Attack (know two side IP)
- pretend fake server
-
Spoofing both two sides
- Packet Sniffing
- MitM attack
Alice
Bob
Eve
Lab -
DoS by APR Spoofing
Network Topology
eth0 (Your net card)
VM 1
(victim)
VM 2
(attacker)
bridge
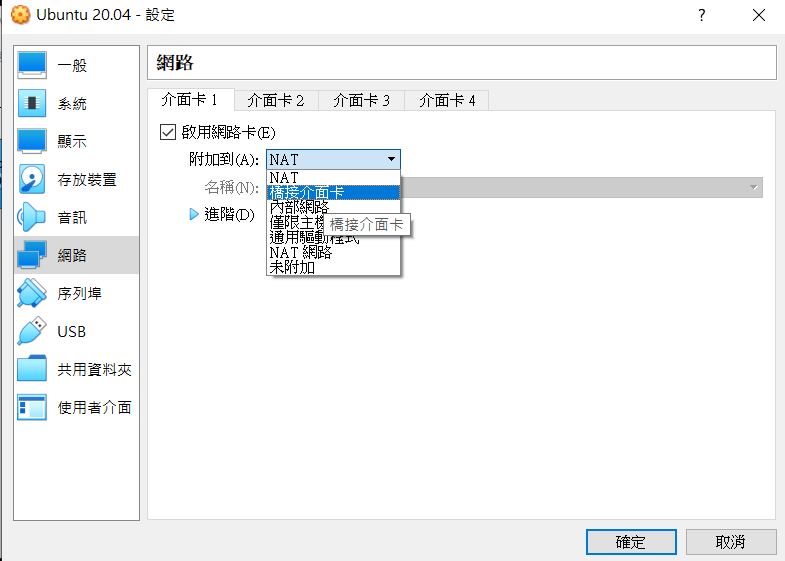
How 2 bridge?
Your Mission

VM1 (victim)
ping 8.8.8.8


VM2 (attacker)
ARP spoofing
Redirect

Router
It is kind of race condition.

VM1 (victim)

VM2 (attacker)

Router
Gateway:
192.168.0.1
192.168.0.1
192.168.0.2
192.168.0.1 is at bb:b..
bb:bb:bb:bb:bb:bb
aa:aa:aa:aa:aa:aa
192.168.0.1 is at aa:a..
Useful Tools
You can choose not to use these tools, though.
Scapy

Install Scapy in Ubuntu
Ubuntu 20.04 already has python3.
Install pip (python package manager)
sudo apt install python3-pipInstall scapy
sudo pip install scapy==2.4.0
# or
sudo python3 -m pip install scapy==2.4.0Start Packet Crafting
import all you can use.
from scapy.all import *craft any protocol packet you want
pkt = IP(dst="127.0.0.1")
print(bytes(pkt))
# b'E\x00\x00\x14\x00\x ...
# Which is packet's raw bytesusing "/" to concat
udp_pkt = IP(dst="127.0.0.1") / UDP(dport=80, sport=65001)send it!
send(udp_pkt)Examples
UDP data "AAA"
udp_pkt = IP(dst="127.0.0.1") / UDP(dport=777, sport=8888) / b"AAA"
send(udp_pkt)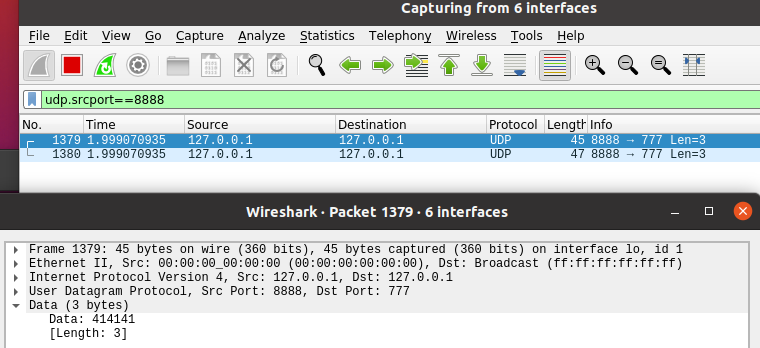
Examples
fake ARP Request
arp_pkt = ARP(op=ARP.who_has, psrc="1.1.1.1", pdst="8.8.8.8")
send(arp_pkt)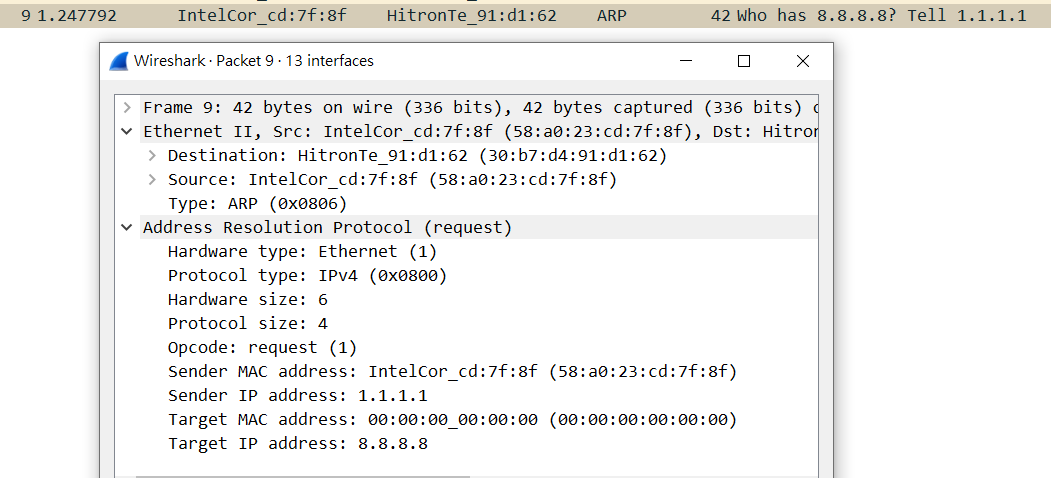
ARP Parmeters
op : ARP.who_has (ARP request) /
ARP.is_at (ARP response)
psrc : ip source (e.g. "127.0.0.1")
pdst : ip destination
hwsrc : MAC source (e.g. "08:00:27:1e:0f:88")
hwdst : MAC destination
These maybe helpful in lab ...
How 2 look ARP Table?
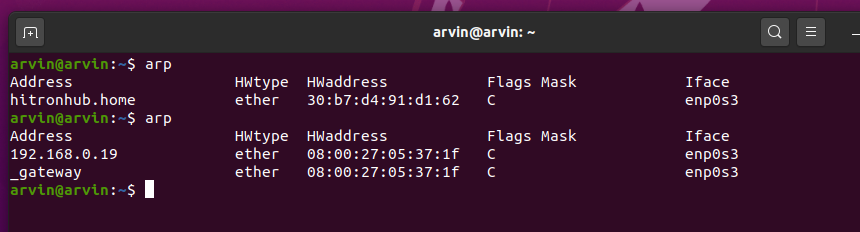
Type command "arp".
How 2 Get Score?
Your Mission

VM1 (victim)
ping 8.8.8.8


VM2 (attacker)
ARP spoofing
Redirect

Router
Screenshot 1 : before atk
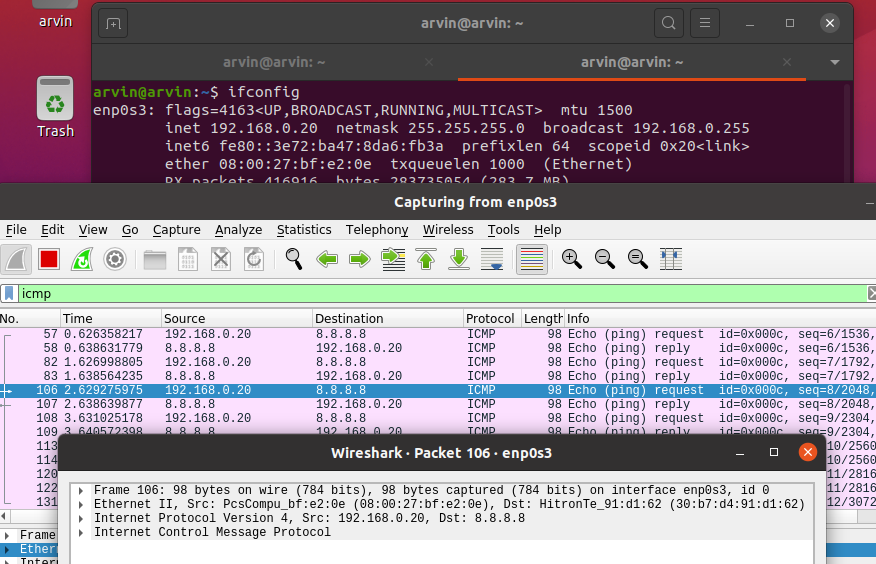
ping 8.8.8.8 and highlight
1. ICMP request's Ethernet Src & Dst
2. victim's ip & MAC
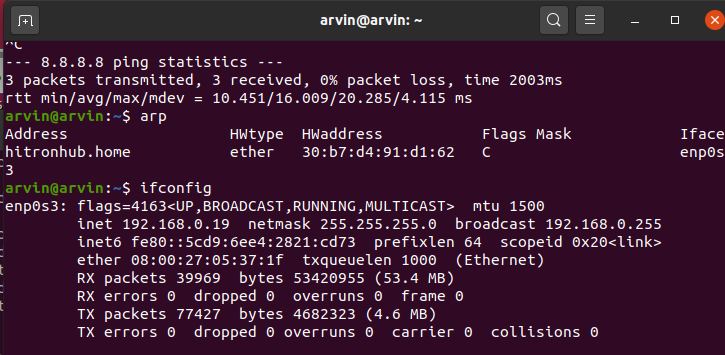
Screenshot 2 : atk's info
highlight attackers ip & mac
Screenshot 3 : after atk
ping 8.8.8.8 and highlight
ICMP request's Ethernet Src & Dst
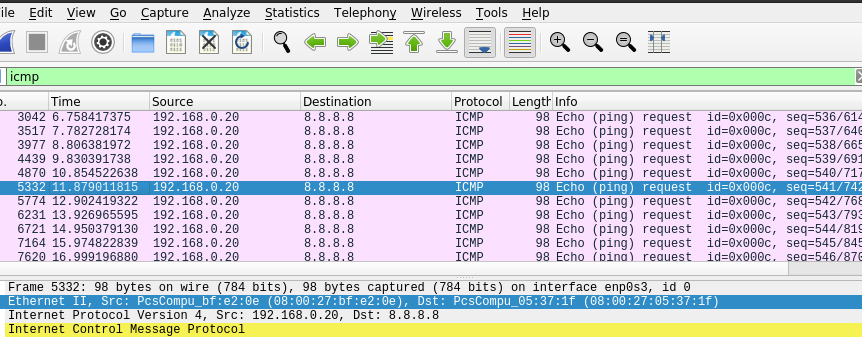
Ether Dst must be equal to Attacker's MAC,
And these ICMP may not respond in a row.
Submit these 3 pics You'll get full scores!
Or you can webcast it :).
How to Prevent?
-
DAI (Dynamic ARP Inspection)
- Bind ip & mac
Prevent ARP Spoofing
Another Net Setting
(If you cannot use bridge mode to ping 8.8.8.8, like you're using dorm's networks)
Network Topology Comp
mode Bridge
Host
VM1
mode NAT

Router

Router
Host
VM1
VM2
VM2
NAT
(+virtual router)
Network Topology Comp
mode Bridge
mode NAT
- Host & VMs are in same LAN
- Host can connect to VMs
- VMs can connect to Host
- Host & VMs are not in same LAN
- VMs can connect to Host
- Host cannot connect to VMs
- VMs connect Internet by NAT mechanism in host.
NAT Network Setting
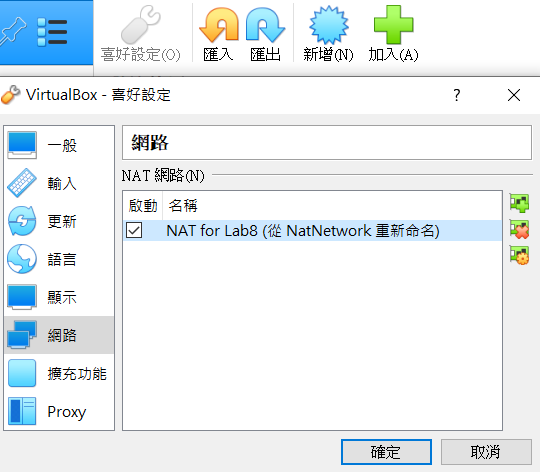
Step 1 : Create NAT Env
NAT Network Setting
Step 2 : VM's Net Setting
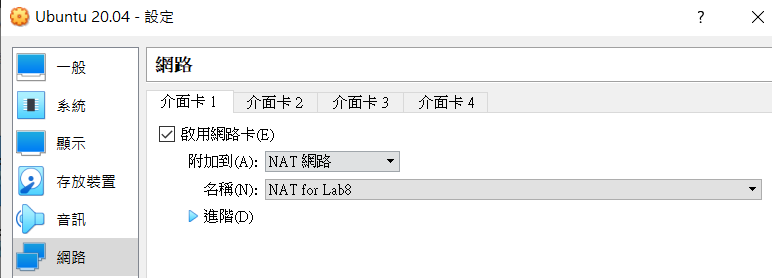
It should be "NAT Networks", not NAT.
if using NAT, your VMs cannot connect to each others.
NAT Network Setting
Step 3 : Check Your VM
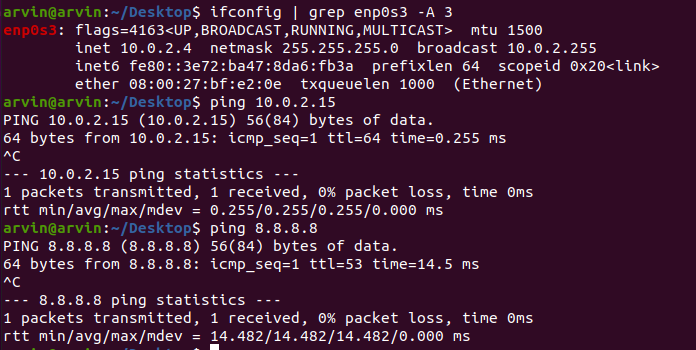
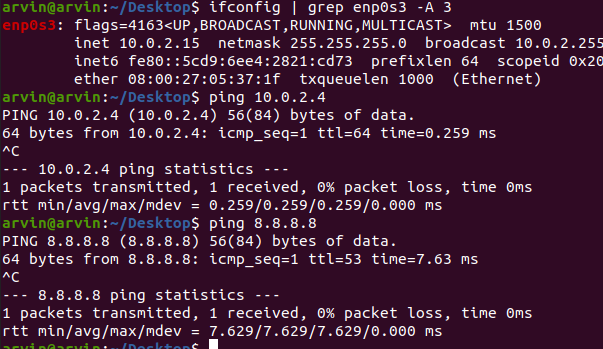
VM 1
VM 2
1. They should have different IP & MAC
2. Can ping each others.
3. Can ping 8.8.8.8
NAT Network Setting
Step 4 : Enjoy your attack!
NASA Lab
By Arvin Liu
NASA Lab
NASA Lab - DoS by ARP Spoofing
- 1,727



